CVE-2024-37085 is an authentication bypass vulnerability in VMWare ESXi being currently being exploited by ransomware groups. This blog will review the background of the exploit and how to leverage Cayosoft Guardian to scan for potential indicators of compromise and proactively defend against future attacks. The short video below also provides a brief overview of the topics outlined above.
Overview of VMware Vulnerability CVE-2024-37085
Background
Threat actors are actively exploiting a vulnerability in VMWare ESXi, that can allow an attacker gain full administrative control. This VMWare ESXi authentication bypass vulnerability, CVE-2024-37085, was discovered by Microsoft researchers on June 25, 2024, and has been labeled a medium-severity security flaw.
For those running a version of VMware that is lower than version 8.0 update 31 or cloud foundation 5.2, you are susceptible to an Active Directory bypass bug. This bug grants any members of an Active Directory group named ESX Admins full administrative control over your ESX hosts. This exploit is currently being used by well-known ransomware groups like Akira and Black Basta.
VMWare has put out a patch for any customers that are running version 8 or cloud foundation 5.2, but they have yet to release a fix for older versions of their software. For more details on patches or the exploit, read the security advisory from Broadcom.
Exploit Details
According to Microsoft, security researchers identified a new post-compromise technique utilized by ransomware operators like Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest in numerous attacks. In several cases, the use of this technique has led to Akira and Black Basta ransomware deployments. The technique includes running the following commands, which results in the creation of a group named “ESX Admins” in the domain and adding a user to it:
- net group “ESX Admins” /domain /add
- net group “ESX Admins” username /domain /add
While investigating the attacks and the described behavior, Microsoft researchers discovered that the threat actors’ purpose for using this command was to utilize a vulnerability in domain-joined ESXi hypervisors that allows the threat actor to elevate their privileges to full administrative access on the ESXi hypervisor. This finding was reported as part of a vulnerability disclosure to VMware earlier this year.
Further analysis of the vulnerability revealed that VMware ESXi hypervisors joined to an Active Directory domain consider any member of a domain group named “ESX Admins” to have full administrative access by default. This group is not a built-in group in Active Directory and does not exist by default. ESXi hypervisors do not validate that such a group exists when the server is joined to a domain and still treats any members of a group with this name with full administrative access, even if the group did not originally exist. Additionally, the membership in the group is determined by name and not by security identifier (SID).
Microsoft researchers identified three methods for exploiting this vulnerability:
- Adding the “ESX Admins” group to the domain and adding a user to it – This method is actively exploited in the wild by the abovementioned threat actors. In this method, if the “ESX Admins” group doesn’t exist, any domain user with the ability to create a group can escalate privileges to full administrative access to domain-joined ESXi hypervisors by creating such a group, and then adding themselves, or other users in their control, to the group.
- Renaming any group in the domain to “ESX Admins” and adding a user to the group or use an existing group member – This method is similar to the first, but in this case the threat actor needs a user that has the capability to rename some arbitrary groups and rename one of them to “ESX Admins”. The threat actor can then add a user or use a user that already exists in the group, to escalate privileges to full administrative access. This method was not observed in the wild by Microsoft.
- ESXi hypervisor privileges refresh – Even if the network administrator assigns any other group in the domain to be the management group for the ESXi hypervisor, the full administrative privileges to members of the “ESX Admins” group are not immediately removed, and threat actors still could abuse it. This method was not observed in the wild by Microsoft.
Successful exploitation leads to full administrative access to the ESXi hypervisors, allowing threat actors to encrypt the file system of the hypervisor, which could affect the ability of the hosted servers to run and function. It also allows the threat actor to access hosted VMs and possibly to exfiltrate data or move laterally within the network.
Prevention & Detection of CVE-2024-37085 – VMWare ESXi Vulnerability
VMware plays a vital role in hosting mission-critical applications and supporting infrastructure, including Active Directory domain controllers. The Cayosoft team recognized that not all organizations can immediately upgrade to the latest version. To help those not able to upgrade to the latest version, a new threat definition has been developed and added to the Cayosoft Guardian threat library, that checks for this ESX Admin group in Active Directory.
Instructions below outline how to scan your environment for indications of the vulnerability and how to create a custom change alert with automatic rollback detection with Cayosoft Guardian. This will prevent the creation of new AD group named ESX Admins and the renaming of an existing AD group to ESX Admins, ensuring this vulnerability can not be exploited in the future.
This feature is available in the free version of Cayosoft Guardian. If you’re not a current customer you can still detect the compromise by downloading our free trial.
Detecting Potential Indicators of Compromise with Cayosoft Guardian
1. First, make sure the latest version of threat definitions have been downloaded. Steps 2-4 walk through the process.
2. In the Cayosoft Guardian web portal, expand the Threat Detection node.
3. Click the Dashboard node.
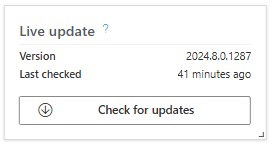
4. In the upper right corner, on the Live Updates widget, click Check for Updates. Make sure the version is 2024.8.0.1287 or higher.
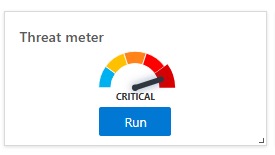
5. Once updated, start a manual scan by clicking Run on the Threat Meter widget.
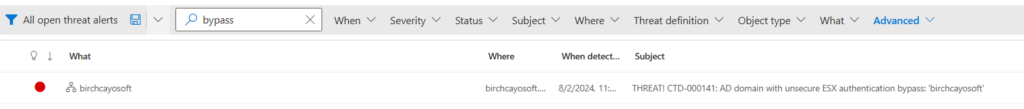
7. Click on the Threat Alerts node.
8. In the Threat Alerts panel, click on Search, type in bypass, and press Enter.
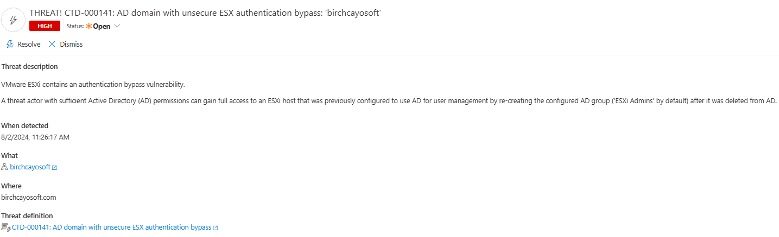
9. Open the Threat Alert, to see the details.
Preventing Future Compromise with Cayosoft Guardian
1. In the Cayosoft Guardian web portal, expand the Change Monitoring node.
2. Click the Change History node.
3. Click All Changes.
4. In Saved Queries, select one of the predefined queries.
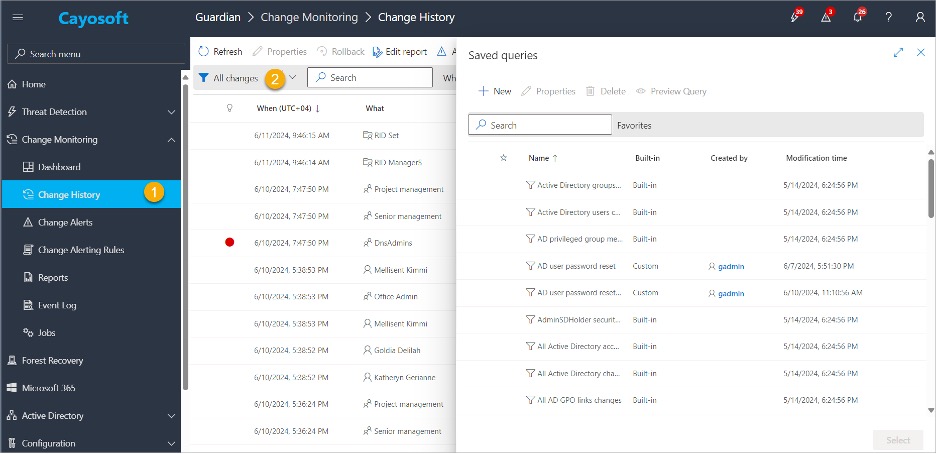
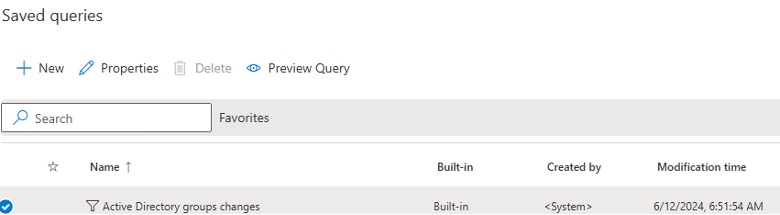
6. Click Select.
7. Open the Properties Tab.
8. In the Object Type drop down, select AD Group.
9. In the Modified Properties drop down, select Group name (pre-Windows 2000) (samAccountName)
10. Select the options for New/Added, Contains, and type in ESX Admins.
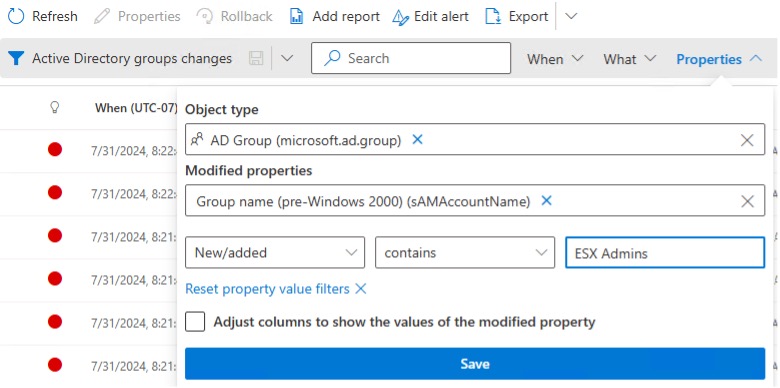
11. Click Save.
12. Click Run Query.
13. Select Save As.
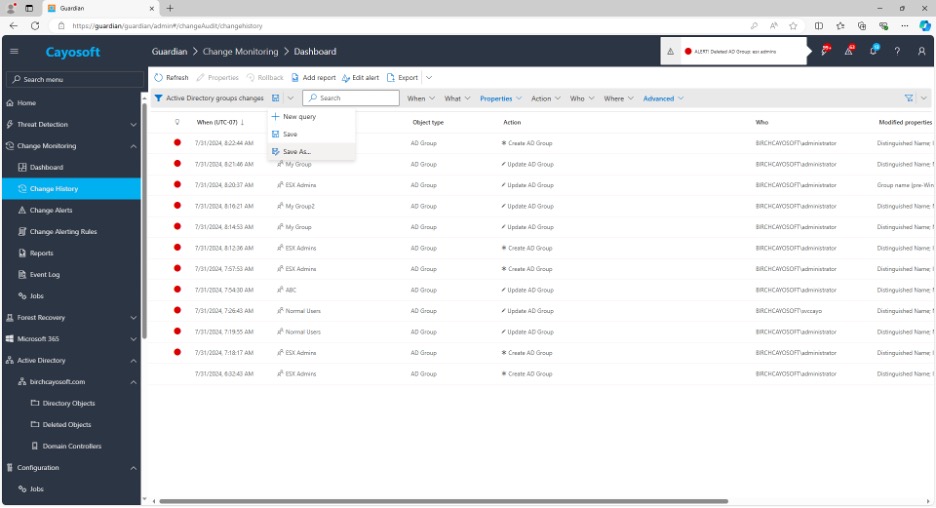
14. Input name: Mitigate VMWare Exploit Active Directory ESX Admins Takeover (CVE-2024-37085)
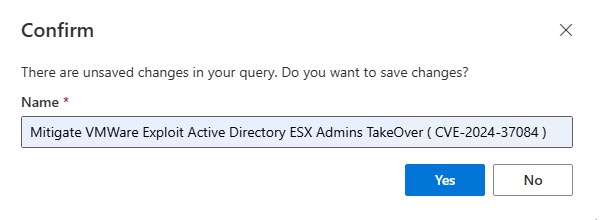
15. Click Yes.
16. Select Add an Alert.
17. Navigate to the Workflow Steps
18. Set the Toggle for Automatic Rollback to On.
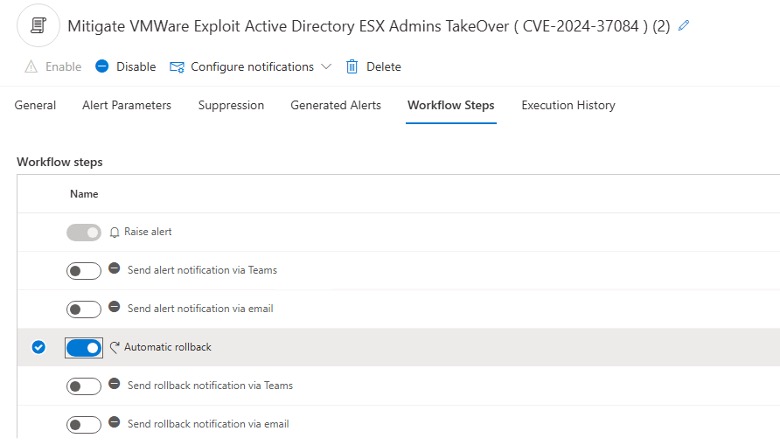
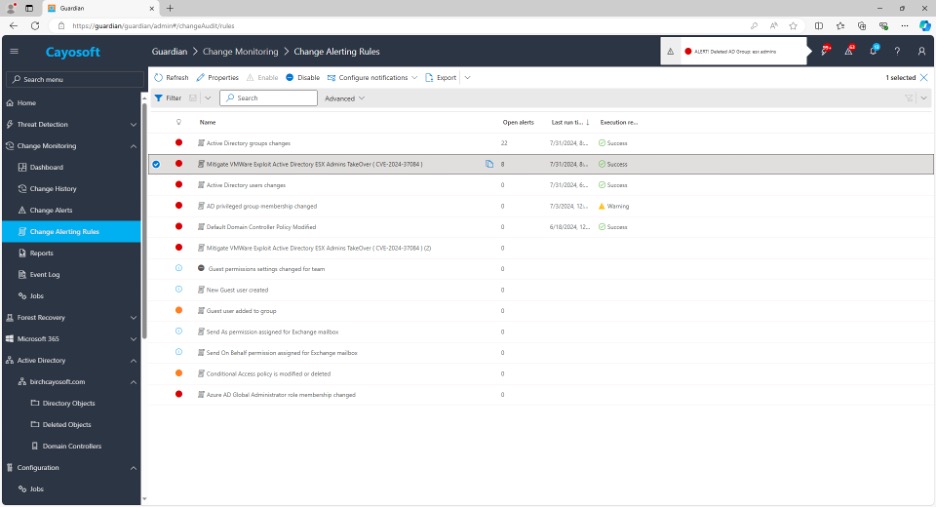
20. Navigate to the Change Alerting node.
21. Verify the new change alert called “Mitigate VMWare Exploit Active Directory ESX Admins Takeover (CVE-2024-37085)” was created.
22. Test Case Scenario 1: Create a new AD group called ESX Admins.
23. Expected Result 1: The alert will detect the new group and automatically delete the group ESX Admins from Active Directory
24. Test Case Scenario 2: Modify the name of an existing AD group to ESX Admins
25. Expected Result 2: The alert will detect the name change and automatically rollback the name to its original name
Both the above capabilities are offered through the full Cayosoft Guardian solution. To see more of these features in action, be sure to request a personalized demo.
Cayosoft Guardian also offers a free version that enables threat detection and scanning capabilities, shown in the prevention section above. To access, download the free trial.
If you are an existing customer and would like more information on our latest threats, check out our threat library or visit our support site.
Want to Learn More About Cayosoft Guardian?
Cayosoft Guardian increases Active Directory security through advanced threat detection and recovery capabilities. Schedule a demo today!