Qilin ransomware has emerged as a significant threat to organizations, particularly those relying heavily on Active Directory for managing their IT infrastructure. Qilin ransomware has adopted a new method for stealing credentials from Google Chrome browsers by leveraging Active Directory Group Policy. In this guide, we will explore how Qilin ransomware operates, the risks it poses to your organization, and how you can leverage tools like Cayosoft Guardian to detect and mitigate these threats effectively.
Understanding Qilin Ransomware
Detecting Qilin Ransomware with Cayosoft Guardian
Cayosoft Guardian customers can use a feature called Change Alerting Rules. If you are not a Cayosoft Guardian customer, you can start a free trial. In the next section we will take you step-by-step on how to create two new Change Alert Rules that will detect both scenarios.
Change Alert Rule – Group Policy with Logon Script Called logon.bat
1. In the Cayosoft Guardian web portal, expand the Change Monitoring node.
2. Click the Change History node.
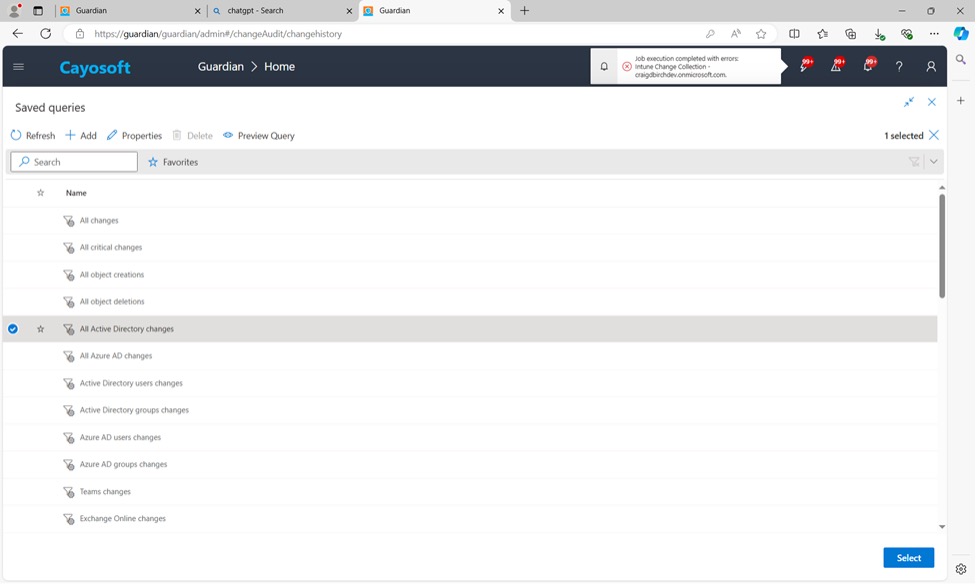
4. In this example, we use the predefined query called “All Active Directory Changes”.
5. Click Select.
6. Open the Properties Tab.
7. Click on the Advanced Tab.
(va_gpoPolicySettings_added/any(i:i/path eq ‘Computer Configuration/Policies/Windows Settings/Scripts/Startup’)) and (va_gpoPolicySettings_added/any(i:i/name eq ‘logon.bat’))
9. Click Apply.
10. Click Save As.
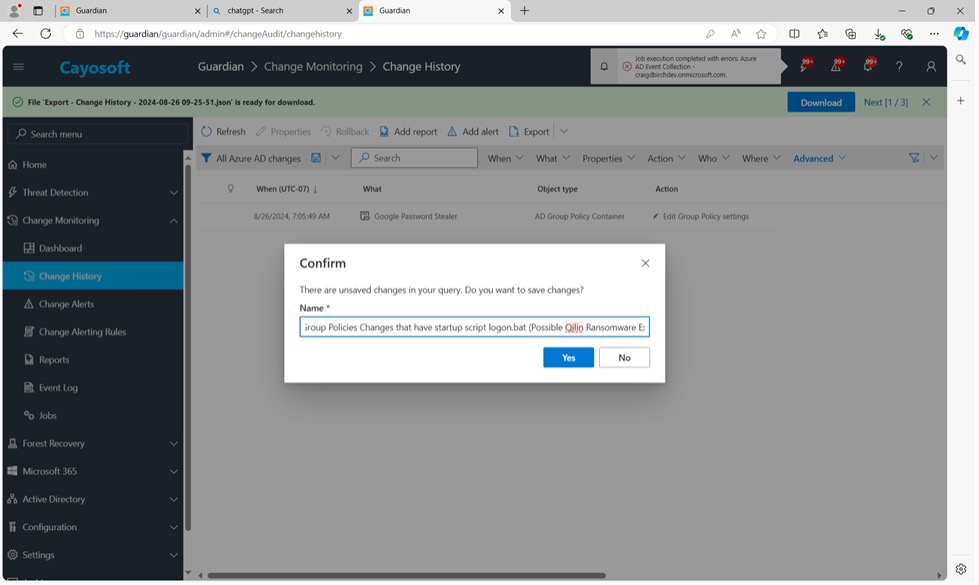
11. Input name: Detect Group Policies Changes that have startup script logon.bat (Possible Qilin Google Chrome Password Stealer Exploit).
12. Click Yes.
13. Select Add an Alert.
14. Navigate to the Workflow Steps.
15. Use the Toggle Feature to select how you wish to receive the alert.
Change Alert Rule – Group Policy with Logon Script Called run.bat
1. In the Cayosoft Guardian web portal, expand the Change Monitoring node.
2. Click the Change History node.
3. In Saved Queries, select one of the predefined queries.
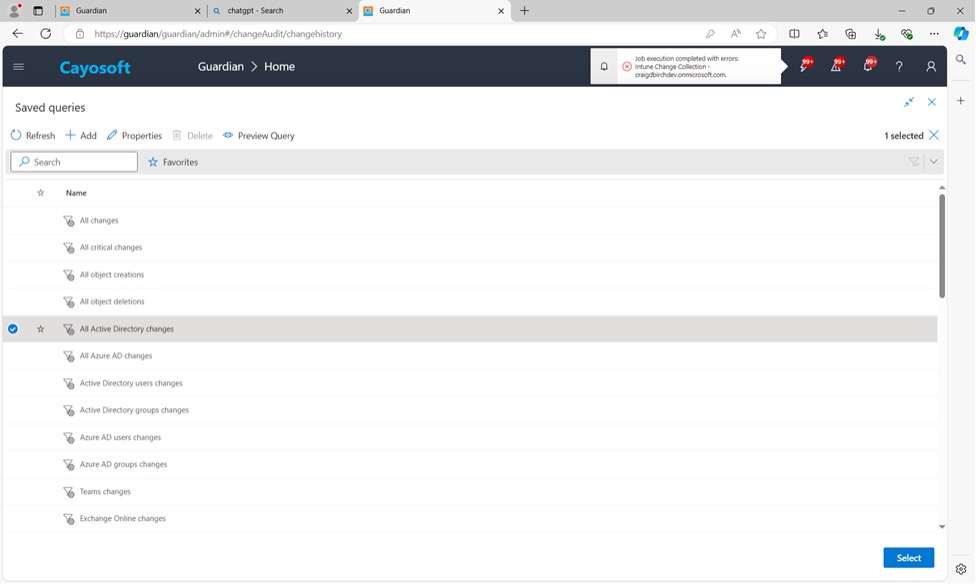
5. Click Select.
6. Open the Properties Tab.
7. Click on the Advanced Tab.
9. Click Apply.
10. Select Save As.
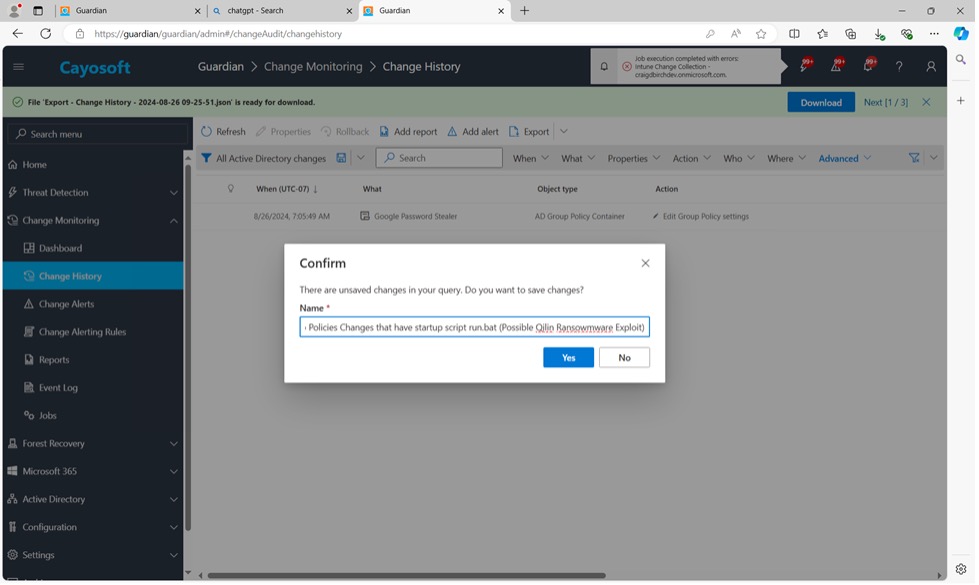
11. Input name: Detect Group Policies Changes that have startup script run.bat (Possible Qilin Ransomware Exploit).
12. Click Yes.
13. Select Add an Alert.
14. Navigate to the Workflow Steps.
15. Use the Toggle Feature to select how you wish to receive the alert.
Conclusion
Both the above are offered through the full Cayosoft Guardian solution. To see more of these features in action, be sure to request a personalized demo.
Cayosoft Guardian also offers a free version that enables threat detection and scanning capabilities. To access, download the free trial.
If you are an existing customer and would like more information on our latest threats, check out our threat library or visit our support site.
FAQs
Detecting Qilin ransomware in your network requires monitoring for suspicious changes in Active Directory, particularly in Group Policy Objects (GPOs). Tools like Cayosoft Guardian can be highly effective in this regard. By setting up Change Alert Rules, you can monitor for specific scripts like “logon.bat” or “run.bat” being added to GPOs, which are indicative of a Qilin ransomware attack. Early detection allows IT administrators to respond quickly, mitigating the potential damage caused by the ransomware.
To protect your organization from Qilin ransomware, it is essential to implement robust security measures within your Active Directory environment. This includes regularly monitoring and auditing Group Policy Objects (GPOs) for unauthorized changes, using tools like Cayosoft Guardian to set up Change Alert Rules. Additionally, ensure that VPN credentials and other access points are secured with strong, unique passwords and multi-factor authentication (MFA). Keeping your software and systems up to date with the latest security patches is also crucial in defending against potential exploits used by Qilin ransomware.
Want to Learn More About Cayosoft Guardian?
Cayosoft Guardian increases Active Directory security through advanced threat detection and recovery capabilities. Schedule a demo today!