Home » Implementing Zero Trust Security with Microsoft Entra » Managing Access with Microsoft Entra Roles: Best Practices
Managing Access with Microsoft Entra Roles: Best Practices
Learn best practices for implementing and managing Microsoft Entra roles, including applying the principle of least privilege and utilizing custom roles for specific needs, in complex cloud environments with increasing cyber threats.
Explore the chapters:
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
With cloud environments becoming increasingly complex and cyber threats becoming more sophisticated, organizations must implement robust security measures to protect their sensitive data and resources. One fundamental model for managing permissions is role-based access control (RBAC), which provides a structured approach to control access to resources and services within the Microsoft Cloud ecosystem.
The RBAC model allows organizations to grant specific permissions to users based on their job responsibilities. This is an approach that aligns with the principle of least privilege (PoLP), where users are given only the access they need to perform their tasks, thus reducing the potential attack surface and minimizing the risk of unauthorized access.
In Microsoft Entra ID, the RBAC model is implemented by Microsoft Entra roles, which are specifically designed for managing Microsoft Entra resources. They are a powerful tool for managing access and permissions within your organization’s cloud applications and resources.
When managing access within Microsoft Entra, proper role management is paramount for maintaining security and compliance. With several roles that grant different levels of access, it becomes important to establish clear guidelines for assigning and managing these roles. This article explores best practices for implementing and managing Microsoft Entra roles as well as practical tips and common pitfalls to avoid.
Summary of key best practices related to Microsoft Entra roles
The table below summarizes six best practices to consider when implementing Microsoft Entra roles in your organization.
Best practice | Description |
Apply the principle of least privilege | Grant admins only the permissions they need for their job functions and nothing more. |
Leverage custom roles where necessary | Create custom roles tailored to specific needs when built-in roles are too permissive. |
Enable multi factor authentication | Require additional authentication factors for all accounts. |
Implement Conditional Access policies | Implement policies that restrict access based on user behavior, location, role, or device. |
Employ automation for role management | Use automation tools to streamline role creation, assignment, and deprovisioning. |
Monitor role activities and changes | Monitor admin activity and audit role changes to detect anomalies and potential security threats. |
Apply the principle of least privilege
The principle of least privilege (PoLP) is a basic concept in cybersecurity that involves granting users or administrators only the minimum permissions necessary to perform their job functions. This approach reduces the attack surface and mitigates the potential impact of security breaches—it is one of the cornerstones of effective access management in Microsoft Entra ID.
In Microsoft Entra, PoLP can be effectively implemented through two types of role definitions: built-in and custom roles. Built-in roles—like “User Administrator,” “Application Administrator,” and “Groups Administrator”—provide predefined permissions that cover common administrative needs, helping admins quickly apply PoLP without the complexity of custom configurations. Meanwhile, custom roles allow for more tailored permissions that align with unique organizational requirements.
To further strengthen the principle of least privilege, Microsoft Entra ID allows the scoping of roles to Administrative Units (AUs), enabling fine-grained control over role permissions. When a role is assigned at this scope, its permissions are limited to resources within that particular administrative unit, reducing the risk of accidental changes to resources outside the intended scope. For example, a “User Administrator” role scoped to the Customer Support Administrative Unit can manage users in the Customer Support department without impacting users in other parts of the organization. This approach is particularly useful for organizations with complex structures, as it enables more targeted administration aligned with organizational hierarchies or operational needs.
However, implementing PoLP is not a one-time task. Effective implementation requires continuous oversight and updating to adapt to changes. When employees change roles, move departments or have their access needs evolve, privileges must be regularly reviewed and adjusted. Microsoft Entra’s Access Reviews feature aids in this process, allowing organizations to set up periodic reviews for role assignments, particularly for high-impact roles like Global Administrator.
Overprovisioning is another frequent mistake that some admins make. In this situation, administrators are granted more permissions than necessary, often in an attempt to ensure uninterrupted workflow. This can lead to “privilege creep,” where admins accumulate excessive permissions over time, potentially compromising security.
As an admin, take the following steps to avoid overprovisioning:
- Avoid assigning broad, generic roles like “Global Administrator” to users. Instead, utilize more granular roles that align with specific job functions.
- To maintain consistency and reduce complexity, utilize Microsoft Entra ID’s predefined roles before creating custom ones.
- Review role assignments regularly and revoke permissions that are no longer needed. Outdated roles can pose a security risk.
Organizations looking to simplify implementing the RBAC model and PoLP can use solutions like Cayosoft Administrator to manage user permissions and delegate roles more precisely. Cayosoft Administrator provides a unified system spanning on-premises AD and Entra ID, which allows the creation of granular, role-based permissions across hybrid environments.
With Cayosoft Administrator, instead of assigning broad or high-level administrative roles, which may provide unnecessary access to critical systems, organizations can enforce a least-privileged delegation model that significantly enhances security by reducing reliance on native roles for most administrative users.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Leverage custom roles where necessary
Microsoft Entra ID offers robust built-in roles to manage access and permissions, but there are scenarios where these predefined roles may not perfectly align with your organization’s specific needs. Fortunately, Microsoft Entra ID offers custom roles, which allow you to create fine-grained, tailored roles that precisely match your organization’s specific needs.
Custom roles in Microsoft Entra ID are particularly useful when:
- Combining permissions from multiple roles: If you require permissions from multiple built-in roles (such as both User Administrator and Application Administrator permissions), a custom role can consolidate these permissions into a single, efficient role.
- Restricting permissions to a subset of actions: When the default built-in roles include more permissions than necessary, a custom role allows you to limit access to just the needed subset. For example, if you only need certain permissions from the “Reports Reader” role, a custom role can be crafted to grant just those permissions.
- Scoping permissions to specific resources or applications: Custom roles are also useful when permissions need to be restricted to specific resources or applications within Microsoft Entra ID.
However, it is important to review the built-in roles to understand the relevant permissions before creating a custom role. This ensures that you fully understand the permissions required and lets you confirm that a built-in role can’t meet the need, which matters because leveraging existing built-in roles whenever possible reduces complexity and minimizes the risk of unintentional overprovisioning.
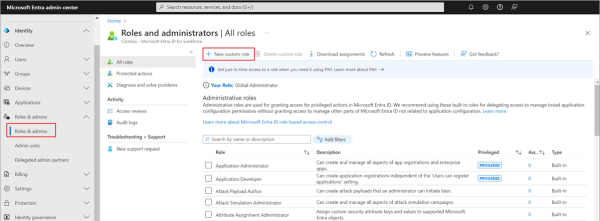
Once you determine that a custom role is necessary, you can create and assign it in Microsoft Entra ID by following these steps:
- Create the custom role: In the Microsoft Entra admin center, navigate to Identity > Roles & admins > Roles & admins. Click + New custom role.
- Define role permissions: Specify the permissions the custom role will grant. You can choose from a wide range of built-in permissions or create custom permissions if needed.
- Assign the role: Once you’ve created the custom role, you can assign it to users using the Role Assignments tab.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Enable multi factor authentication
Multi factor authentication (MFA) is a security measure that prevents unauthorized access to your data and applications by requiring a second method of verifying your identity. According to Microsoft, MFA reduces the overall risk of compromise by 99.2% and by 98.6% in cases of leaked credentials. When threat actors try to compromise organizations’ security, they most often target accounts with administrative rights.
By requiring an admin to provide a second form of verification in addition to a password, MFA dramatically reduces the risk of unauthorized access, especially when passwords are compromised. This extra verification is essential for protection against common threats, including the following:
- Credential theft and phishing: Even if an attacker gains a user’s password, they cannot access the account without the additional verification step.
- Password spray and brute-force attacks: MFA thwarts attempts to compromise accounts using common or weak passwords, protecting organizations from automated attacks.
- Social engineering attacks: MFA reduces the success rate of social engineering, but attackers may still attempt tactics like MFA fatigue.
Like the principle of least privilege, it is not enough to enforce MFA for all admin accounts; proper education is also essential to ensure that admins do not fall for social engineering attacks like MFA fatigue attacks. This is an attack pattern where threat actors, having compromised an admin’s password, repeatedly initiate multifactor authentication requests to the target victim’s registered devices. The goal is to trick and force the victim into confirming their identity via notification. This is similar to what reportedly happened in the Uber breach by Lapsus$, where an employee was spammed for over an hour before being contacted via WhatsApp and tricked into accepting the MFA request.
To prevent MFA fatigue and similar social engineering attacks:
- Educate users and admins: Inform users about the risks of MFA fatigue and instruct them to never approve unexpected authentication requests. Training helps them recognize when they are being targeted and take appropriate actions.
- Implement number matching and contextual prompts: Microsoft Entra ID offers number matching and additional context prompts in the Microsoft Authenticator app. These features require users to match numbers or confirm context (such as the originating location or app) before completing authentication, making it more difficult for attackers to succeed.
Combining the advanced features in Cayosoft’s Administrator and Guardian protects admin accounts from compromise. Guardian has an advanced threat detection feature that, among several useful threat definitions, allows admins to identify when privileged accounts have yet to register for MFA and to detect privileged user accounts susceptible to MFA fatigue attacks.
When properly configured and combined with user education, MFA remains one of the most effective tools for preventing unauthorized access and defending against modern attack techniques.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Implement Conditional Access policies
Conditional Access is a powerful feature in Microsoft Entra ID that allows organizations to enforce specific security controls based on various contextual factors. It acts as a policy engine, making real-time decisions about resource access based on signals such as user identity, device health, location, and risk level.
At its core, Conditional Access operates on an “if-then” principle: if a user wants to access a resource, the user must complete a specified action. This approach allows for granular control over access to applications and data, enhancing security without compromising user productivity.
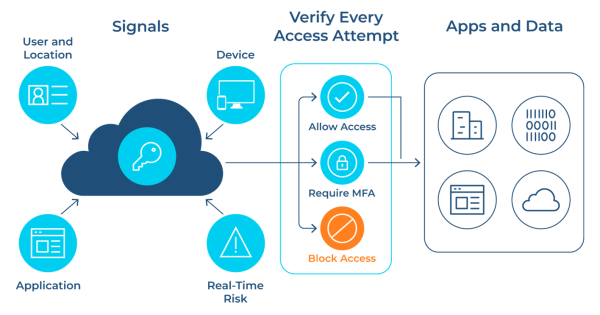
Admins can implement conditional access policies to address various security scenarios:
- Requiring MFA for administrative roles: Enforce additional verification for users accessing sensitive management portals.
- Location-based access control: Block or allow access based on the user’s geographic location or IP address range.
- Device compliance: Ensure that only managed and compliant devices can access corporate resources.
- Risk-based authentication: Prompt for additional verification when sign-in behavior is deemed risky.
- Application-specific policies: Apply different security requirements for various applications based on their sensitivity.
One of the easiest ways to enable Conditional Access for admins is to deploy the “Require MFA for administrators” Conditional Access policy template.
Conditional Access policies provide a flexible and powerful way to enhance your organization’s security posture. By carefully crafting these policies, you can significantly reduce the risk of unauthorized access while balancing security and user experience. Remember to regularly review and update your policies to adapt to evolving threats and organizational needs.
Employ automation for role management
Automating role management tasks—such as user provisioning, deprovisioning, and role assignments—streamlines the user administration lifecycle in Microsoft Entra ID. Automation minimizes manual intervention, reduces the risk of errors, enhances productivity, and significantly strengthens security by ensuring that users have only the appropriate permissions at any given time.
Microsoft Entra ID provides several built-in tools and integrations to support automated role management:
- Lifecycle Workflows: This feature automates actions based on lifecycle events, such as onboarding, role changes, or departures. For example, Lifecycle Workflows can initiate automated processes to assign or revoke roles.
- Dynamic groups and role assignment: Use dynamic groups to automatically assign users to specific roles based on criteria such as department, job title, or location. When users meet these criteria, they’re automatically added to the appropriate group and assigned relevant roles, and when they no longer meet these criteria, access is automatically revoked.
However, there are some potential downsides: Setting up and maintaining these automated workflows can require significant initial effort and expertise, particularly in complex environments. Misconfigured automation rules can lead to unintended access or delays in provisioning, which might compromise security or disrupt operations.
Solutions like Cayosoft Administrator simplify user administration automation by providing a user-friendly platform that allows organizations to efficiently create, update, and deactivate user accounts using automated workflows and custom templates. By pulling information directly from HR systems or databases, Cayosoft streamlines the user provisioning process, ensuring that new hires are set up with the correct permissions and that departing employees are swiftly deprovisioned to maintain security and compliance.
Cayosoft further enhances flexibility by allowing administrators to design complex account templates that automatically assign group memberships and roles based on predefined rules, reducing human error and manual workload. Its unique “Suspend” feature ensures that different scenarios, such as terminations or leave of absence, are managed smoothly without security gaps. This makes it a valuable tool for IT teams seeking to optimize user and group management across their environments.
While setting up automation requires initial investment and expertise, the long-term benefits in accuracy, security, and efficiency make it invaluable for managing roles at scale. Properly implemented, automated role management ensures that users maintain least-privilege access without the administrative overhead of manual interventions.
Monitor role activities and changes
Effective implementation of Microsoft Entra roles requires continuous monitoring and auditing of role activities and changes; it is especially necessary to maintain a secure environment and detect potential threats or misuse of privileged access. By closely tracking role assignments, modifications, and usage, organizations can quickly identify anomalies and respond to security incidents before they escalate.
Adequate monitoring helps identify when admins gain access to privileges they shouldn’t have, potentially indicating a security breach. It can also reveal suspicious patterns indicating insider threats or compromised accounts. In addition, many regulatory standards require organizations to track and audit access to sensitive data and systems.
Microsoft Entra has impressive native monitoring methods to track changes, but configuring it is often a problem for administrators, leaving them blind to malicious events happening in the environment. Cayosoft Guardian solves this problem by combining threat detection, monitoring, and recovery into one comprehensive product. With Guardian’s impressive monitoring and auditing capabilities, IT administrators can protect roles from being changed and can proactively identify unwanted changes, whether malicious or by mistake, and respond to them. Guardian also offers an instant rollback feature that allows administrators to quickly find and fix unwanted changes, including changes to roles and other important policies like conditional access.
With Guardian, administrators can:
- Continuously monitor changes across on-premises AD, hybrid AD, Entra ID, and Office 365, providing a unified view of all directory activities
- Be notified of suspicious activities, such as unusual role assignments or changes to privileged groups
- Immediately roll back unwanted modifications in case misuse or unauthorized changes are detected
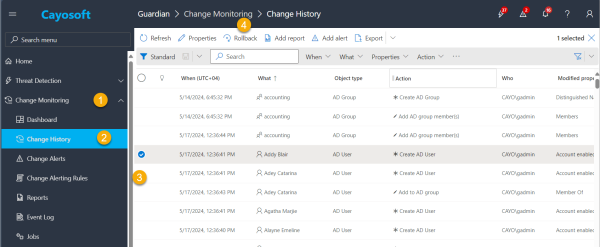
By leveraging Cayosoft Guardian’s advanced monitoring and alerting capabilities, organizations can significantly enhance their ability to detect and respond to potential security threats related to role activities and changes in their Microsoft Entra ID environment. This proactive approach to security helps maintain the integrity of your identity infrastructure and protects against unauthorized access and potential data breaches.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Proper management of Microsoft Entra ID roles is critical for maintaining a secure and efficient cloud environment. As explored throughout this article, effective role management in Microsoft Entra ID is not just about assigning permissions—it’s about creating a robust security framework that protects your organization’s digital assets while enabling productivity. Implementing these best practices is not a one-time task but an ongoing process that requires vigilance and adaptation to evolving security threats.
Navigating the complexities of Microsoft Entra ID security can be challenging, especially for organizations with limited resources or expertise. However, with solutions like Cayosoft Administrator for streamlined user lifecycle management and Guardian for advanced monitoring and auditing, you can elevate your security posture while reducing administrative overhead.
Take the next step in securing your Microsoft Entra ID environment. Contact Cayosoft today to learn how our expertise and solutions can support your journey toward robust and efficient role management.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content