Home » Implementing Zero Trust Security with Microsoft Entra » Getting Started with Microsoft Entra Registered Devices
Getting Started with Microsoft Entra Registered Devices
Learn how Microsoft Entra-registered devices can help businesses manage and secure various device types while providing necessary access and maintaining compliance.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
The shift to remote work and the popularity of bring your own device (BYOD) policies make supporting secure access from various device types a business necessity. The variety of operating systems that run on client devices further complicates balancing security and functionality. In this context, robust device management is crucial for safeguarding critical data while providing necessary access to eligible users and maintaining compliance and control.
Microsoft Entra-registered devices help businesses solve this problem at scale by supporting device registration and assigning devices with identities that enable secure resource access. In this article, we discuss how the Microsoft Entra registered devices method works and the steps to register devices on Entra.
Summary of key Microsoft Entra Registered device concepts
| Concepts | Description |
|---|---|
| Microsoft Entra | A unified Identity and Access Management platform providing authentication, conditional access, MFA, governance, and more. |
| Microsoft Intune | The cloud-based service for managing devices and applications with security policies. |
| Device | A physical or virtual endpoint that is managed using Microsoft Entra. |
| Hybrid identity | An identity that is present on-premises and in the cloud allows unified authentication across both. |
| Bring your own device (BYOD) | A modern device policy that allows employees and contractors to use their personal devices for work. |
| Mobile device management (MDM) | A solution that provides management capabilities for mobile devices, mainly across monitoring, enforcing security, and compliance |
Identity for devices
A device is a laptop, desktop, mobile phone, or a more modern entity such as an IoT device or even an AI agent.
Identities for devices enable identity administrators and security teams to implement device access controls for applications, data, and resources.
The devices are created in Microsoft Entra using the Device Registration Service or by Intune. In Microsoft Entra, a device can get an identity in one of the following ways:
- Microsoft Entra registration
- Microsoft Entra join
- Microsoft Entra hybrid join
In this article, we will focus on the first method, Microsoft Entra registration, in which the devices are simply registered and not joined.
Microsoft Entra Registered devices
Microsoft Entra Registered devices, also called Workplace joined devices, are personal devices registered by users using their Entra ID to access organizational resources. They enable BYOD, especially mobile device scenarios where users/employees can access organizational resources and data using their personal devices.
These devices can be further enrolled in an MDM tool like Microsoft Intune to enable and enforce additional control mechanisms such as encryption and password complexity.
The devices can be end-user/employee-owned or organization-owned. In simple words, Microsoft Entra is aware of the device but does not require that the user use an organization ID to authenticate to the device.
Device management using Microsoft Entra. (Source)
Enrollment with Microsoft Intune or Mobile Device Management for Office 365 requires Device Registration.
Microsoft Entra Registered device features
While device registration does not provide complete device control, there are still many useful features, such as:
- Unique identification: Registering devices creates a unique identity for the device associated with the user account.
- Secure access to resources: The registration enables secure access to organizational resources like Microsoft 365 applications, OneDrive, SharePoint, or other custom SaaS applications built by the organization.
- Cross-platform support: Microsoft Entra registration provides broad compatibility supporting multiple operating systems/platforms such as Windows, macOS, iOS, and Android.
- Multifactor authentication (MFA): Device registration supports requiring MFA during registration.
- Conditional access: When enrolled in an MDM like Intune, security administrators can enable conditional access, such as blocking access to non-compliant devices.
- Single sign-on (SSO): Avoid repeated logins, enabling SSO to access organizational resources.
- Monitoring and visibility: Security teams can monitor sign-ins and other activities, though limited, and get visibility into devices and their usage.
Supported operating systems and platforms
The following operating systems and platforms can be onboarded as Microsoft Entra Registered devices:
- Windows 10 or newer
- macOS 10.15 or newer
- iOS 15 or newer
- Android
- Linux:
- LTS versions of Ubuntu 20.04, 22.04, 24.04
- Red Hat Enterprise Linux 8, 9
Provisioning devices
The table below shows the provisioning methods each platform supports.
| Platform | Provisioning Method |
|---|---|
| Windows 10, 11 | Register the device using the Access work or school option in Accounts under Settings |
| iOS/Android |
|
| macOS |
|
Sign-in options
Microsoft Entra registered devices can use one of the multiple sign-in options supported, such as:
- Password
- PIN
- Windows Hello
- Device local credentials
- Biometrics
Use cases for Microsoft Entra Registered devices
The Microsoft Entra Registered devices are ideal for use cases where organizations need a lightweight and flexible access control method for multiple devices. Specific examples of common use cases include:
- Device access for contractors, guests, and vendors
- BYOD support for employees
- Enabling users to access resources from a wide range of platforms
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Microsoft Entra Registered vs. Joined vs. Hybrid Joined
Choosing between the three device join types depends on factors such as who owns and manages the device, who owns the data, cloud-first or hybrid environment, and what features/capabilities are needed. The following table provides a high-level overview, and the difference between these device join types:
| Microsoft Entra Registered | Microsoft Entra Joined | Microsoft Entra Hybrid Joined | |
|---|---|---|---|
| Device type | User-owned (or personal) device | Company-owned device | Company-owned device |
| Join status | Devices are not joined to either an on-premises AD or Microsoft Entra | Devices are joined to Microsoft Entra only | Devices are joined to an on-premises AD and Microsoft Entra |
| Authentication |
| Device authentication using Microsoft Entra ID | Device authentication using an identity that exists both in on-prem AD or Microsoft Entra ID |
| Authentication types supported | OAuth, SAML | OAuth, SAML | Kerberos/NTLM, LDAP, OAuth, SAML |
| OS/platform support | Windows 10 and above, iOS, Android, macOS 10.15 and above, Ubuntu Linux 20.04/22.04/24.04 LTS, Red Hat Enterprise Linux 8 and 9 | Windows 10 and 11, excluding Windows Home Editions | Windows 8.1, 10, and 11, excluding Windows Home Editions, Windows Server editions 2008 and above |
| Device sign-in methods | Password, PIN, Windows Hello, Device local credentials, Biometrics | Password, Windows Hello for Business, FIDO | Password, Windows Hello for Business (Windows 10 and above) |
How to register devices with Microsoft Entra
In this tutorial, we will learn how to enable device registration, enable MFA (optional), register, and view a device in the Microsoft Entra admin center.
Enable device registration
One of the first things you must do is allow users to register their devices with Microsoft Entra.
You can enable this in Device settings under Devices in the Microsoft Entra admin center. In most cases, this is already enabled and set to All.
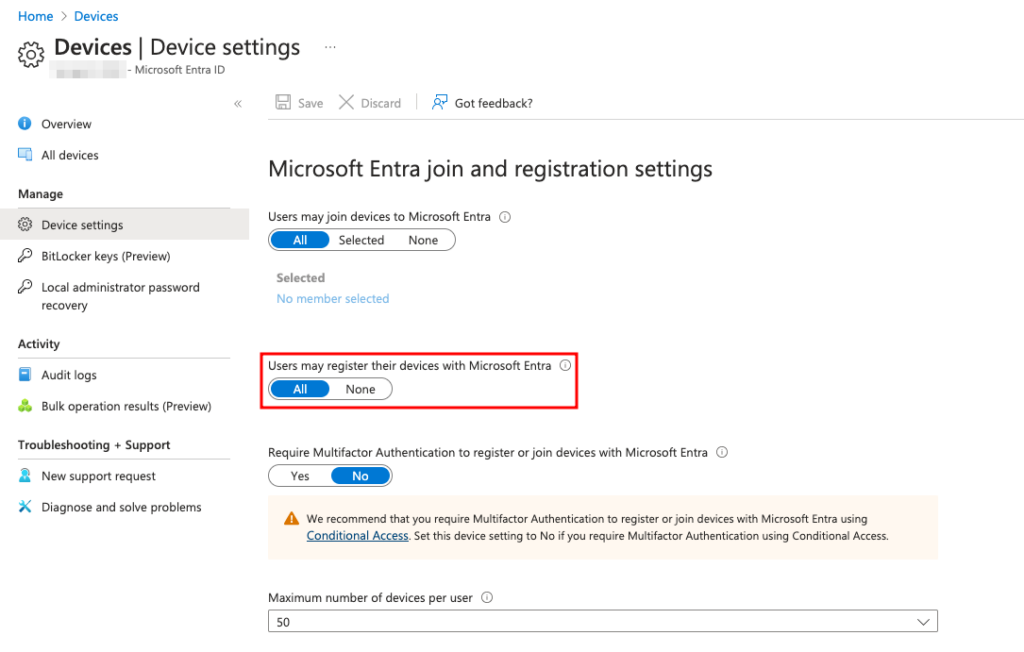
Allow Users to Register Devices
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
This setting is automatically set to All and disabled from further changes if you have configured Enrollment with Microsoft Intune or Mobile Device Management for Office 365.
NOTE: Device registration is mandatory for enrollment to MDM.
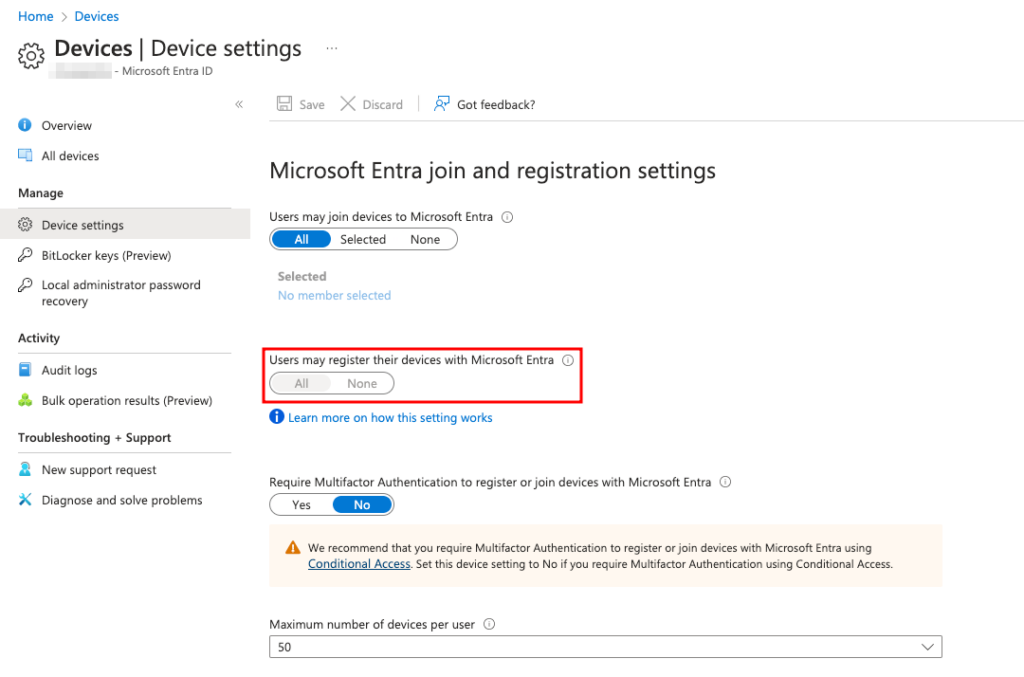
Allow Users to Register Devices Disabled
Require MFA (optional)
For security reasons, you may require MFA when registering devices with Microsoft Entra. There are two ways to do this:
- With Conditional Access (recommended) which requires enrolling devices in Intune. Note you must have a Microsoft Entra Premium license.
- Without Conditional Access
In the Microsoft Entra admin center, you can turn on the option to require MFA (without Conditional Access) in the Device settings under Devices.
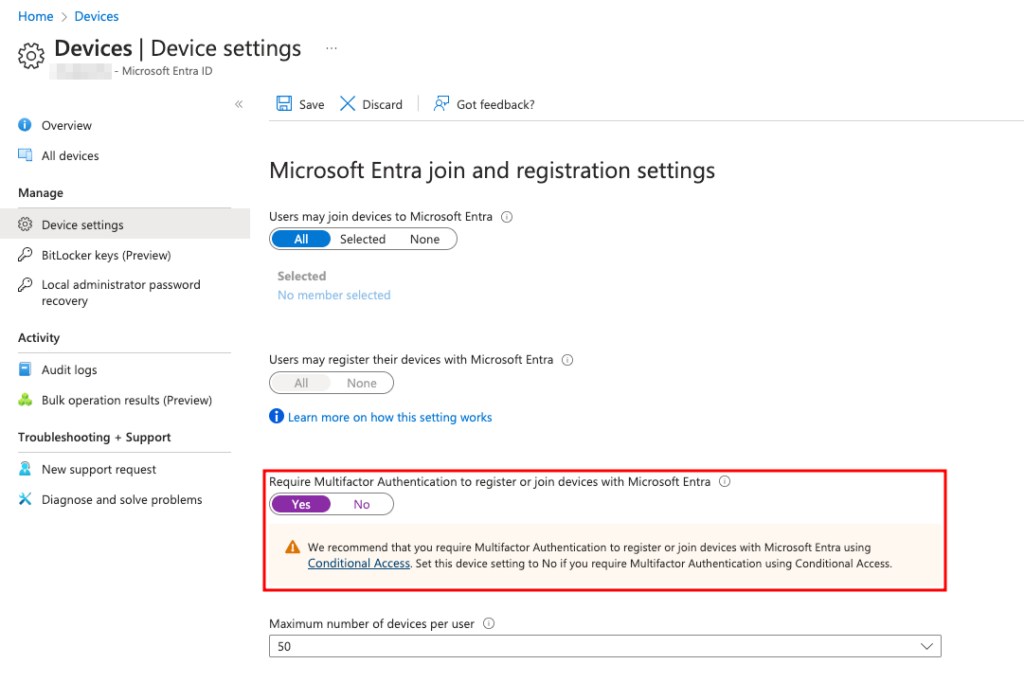
Turning on Require MFA
Registering a Windows device
To register a Windows device, go to Settings and select Accounts. Select the Access work or school option on the left and click Connect.
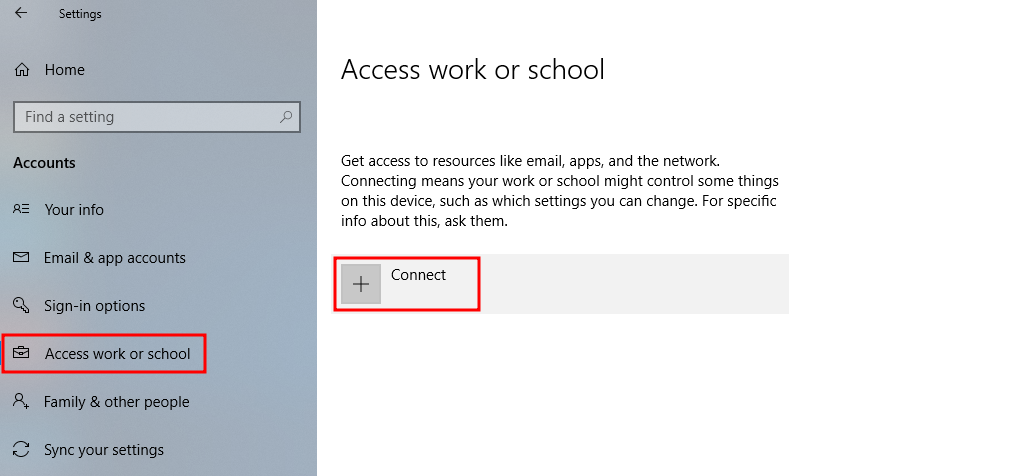
Register a Windows Device
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Sign in using a Microsoft Entra ID and complete the sign-in process. Do not click any of the Join this device options at the bottom. They are for Microsoft Entra joined scenarios.
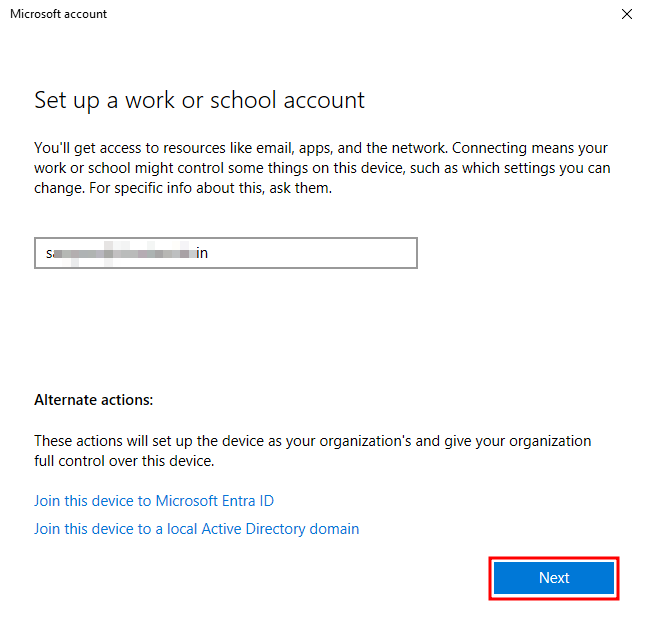
Sign in using Microsoft Entra ID
Registering an iOS device
Use the Microsoft Authenticator app to register an iOS or Android device to Microsoft Entra. In the app, click the menu icon on the left and select Settings. Next, select
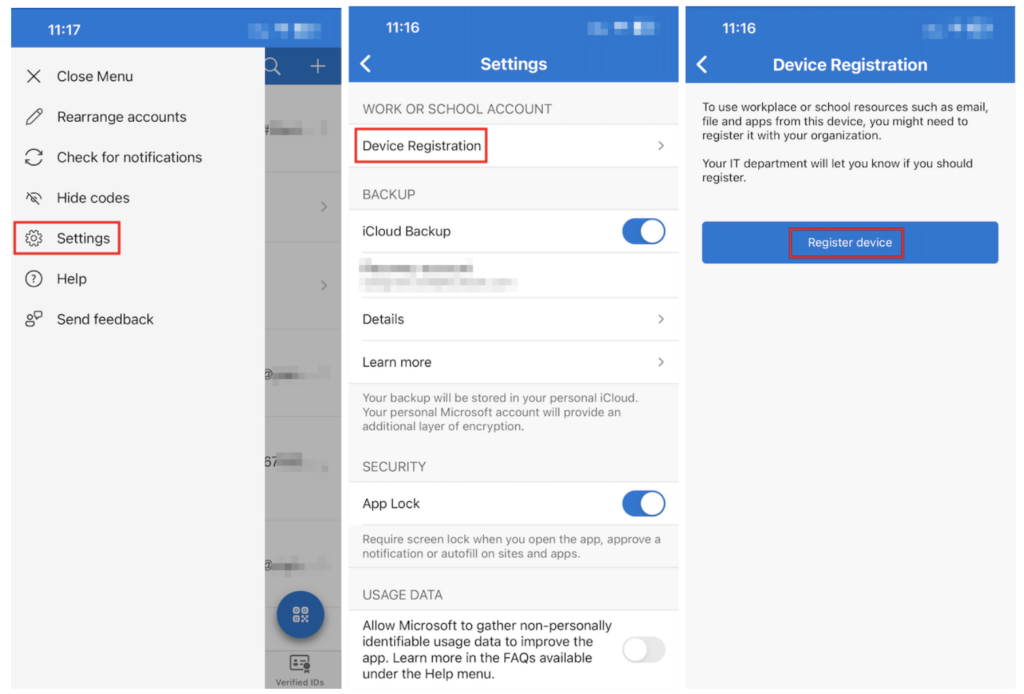
Registering an iOS Device Workflow
In the next step, enter an organizational email (Microsoft Entra ID) and complete the sign-in process. Once the sign-in process is complete, the device is registered.
For an Android device, the steps are similar using the Microsoft Authentication app.
Viewing registered devices in Microsoft Entra
You can view and manage the registered devices either from Microsoft Entra in Azure or from the Microsoft Entra admin center.
To manage devices through the Microsoft Entra admin center, expand Identity followed by Devices in the left navigation menu and select Overview.
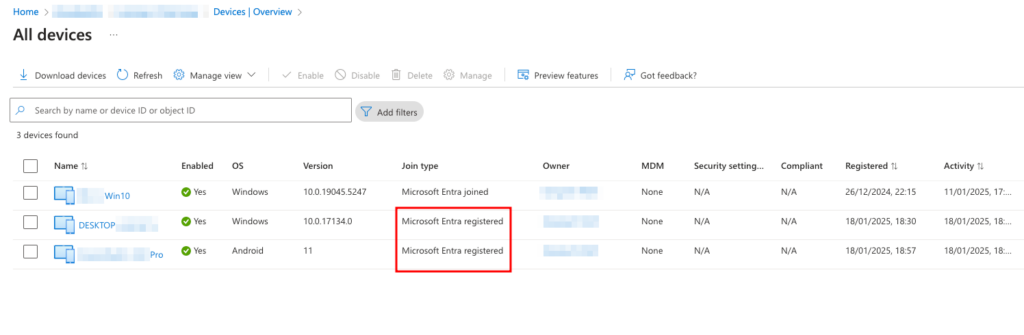
Viewing Devices in Microsoft Entra
It is important to note that simply registering a device in Microsoft Entra does not enroll the devices. For device enrollment, a Mobile Device Management (MDM) such as Microsoft Intune is required. More details on device enrollment can be found in the Microsoft enrollment guide.
Managing Devices using Cayosoft
Cayosoft is a leader in Active Directory and Entra management, monitoring, and recovery solutions and has products that can help you manage registered devices.
For devices that are simply registered and not managed through Intune, you can use Cayosoft Administrator to view them and move them to Azure AD Administrative units. You can also modify certain properties associated with these registered devices. Cayosoft Guardian monitors changes to these devices but cannot recover them since they are not Intune-managed.
Using the Administrator web portal, users can enable, disable, delete, and update the properties of Intune-managed devices. Additionally, Guardian collects changes in the properties of Intune-managed devices and can help recover Intune devices or policies, which is not natively possible with Microsoft Entra.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
While Microsoft Entra offers robust device registration capabilities, many organizations struggle with the practical realities of maintaining visibility and control across their hybrid identity infrastructure.
Cayosoft’s unified management platform bridges these gaps by providing a single pane of glass for your entire Entra device ecosystem. Our solution gives you real-time visibility into device registration status, automates critical lifecycle processes, and maintains detailed audit logs of all device identity changes.
Organizations using Cayosoft report a considerable reduction in device management tasks and faster incident response when security issues arise. To know more about how Cayosoft can transform your Entra device management experience – request a personalized demo today at here.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content