Home » Implementing Zero Trust Security with Microsoft Entra » Implementing Microsoft Entra Permissions Management: A Step-by-Step Guide
Implementing Microsoft Entra Permissions Management: A Step-by-Step Guide
Learn how Microsoft Entra Permissions Management can help organizations manage and control entitlements and permissions for identities in complex and dynamic IT environments for improved compliance and security.
Explore the chapters:
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Permissions management is critical for maintaining a robust security posture and implementing a zero-trust security model, especially one based on the least-privilege model. However, managing permissions can be increasingly difficult in today’s dynamic and complex IT environments and work models. Organizations often face challenges such as unused identities, identities with excessive permissions, and inadequate monitoring and reporting of these identities, which eventually impact compliance.
In this article, we look at how Microsoft Entra Permissions Management can be an essential add-on to your identity and access management strategy, providing visibility, mitigation, and reporting for compliance.
Summary of key Permissions Management concepts
Here are the key features and concepts we will cover in this article
| Term | Description |
|---|---|
| Permissions and entitlements | The specific rights granted to an identity (user or service principal) to perform actions or access resources within a cloud environment, defining what they can and cannot do |
| Permissions gap | The discrepancy between the permissions granted to an identity and the permissions they actually use in practice, highlighting potential areas of excessive privilege and security risks |
| Authorization system type | The type of authorization system (where permissions are managed) you want to connect to Microsoft Entra Permissions Management |
| Authorization system | Cloud-provider-specific services—such as Azure Subscription, AWS Account, or GCP Project—that can integrate with Microsoft Entra Permissions Management for detailed analysis and management of permissions |
| Cloud infrastructure entitlement management (CIEM) | A cloud-based security solution that provides visibility, mitigation, and monitoring of identity access and permissions, preferably across multiple cloud platforms |
| Microsoft Entra Permissions Management | Microsoft’s comprehensive CIEM solution that provides granular visibility and control over permissions across multi-cloud environments |
| Data collector | A dedicated service responsible for securely accessing and collecting permissions data from your configured cloud environments |
| Permissions Creep Index (PCI) | A risk assessment metric that quantifies the disparity between granted permissions and actual usage |
Cloud infrastructure entitlement management (CIEM)
Statistically, identities do not use all the permissions they are granted, and many times, some of these permissions can be high-risk. Dynamic provisioning of cloud resources and applications introduces challenges to permissions management, which native identity and access management (IAM) controls may fail to address. Additionally, a multi-cloud environment can overwhelm the security team with managing entitlements across these environments.
The 2023 State of Cloud Permission Risks Report by Microsoft reveals the following statistics:
- Half of the permissions granted are high-risk.
- The number of workload identities has doubled since the 2021 report.
- Half of the identities have super admin privileges.
- Identities use only 1% of granted permissions.
- Over half (60%) identities remain unused for over 90 days.
A CIEM aids organizations in managing and controlling entitlements or permissions to identities through monitoring and analyzing activity data, thus helping them meet identity compliance. It enforces the principles of zero trust and least privileged access to identities with access to cloud resources.
Microsoft Entra Permissions Management
Microsoft Entra Permissions Management, part of the Microsoft Entra product family, is Microsoft’s cloud-based CIEM solution. It helps organizations manage identity permissions dynamically by providing visibility into access entitlements, automatic right-sizing, and monitoring capabilities for identities across any cloud platform.
It is a SaaS service that collects raw entitlement and activity data every hour over a 90-day window, processes, and analyzes it to generate usage information, reports, etc.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Features
Here are some of the key features of Microsoft Entra Permissions Management:
- Multi-cloud support: Microsoft Entra Permissions Management supports the Azure, AWS, and GCP cloud platforms, providing visibility into permissions across all of them.
- Centralized management: It provides a unified dashboard to manage entitlements across all the cloud platforms.
- Just-in-time access: You can use it to grant temporary permissions as needed.
- Permissions on demand: This feature allows users to request permissions as needed for a certain amount of time. Administrators approve the request.
- Automated rightsizing: Permissions Management will automatically grant, adjust, and revoke permissions based on usage.
- Remediation: You can choose from three remediation options: custom roles, right-sizing using quick actions, and Copilot.
- Analytics: Gain insights into permission usage and potential risks, if any.
- Reporting: Microsoft Entra Permissions Management provides detailed reporting capabilities and has several built-in reports to help you get started quickly. You can also create custom reports. These reports can be downloaded and, depending on the report, the format can be CSV, XLSX, or PDF. You can also schedule them to be emailed.
- Auditing: Use a no-code interface to query activity logs from all configured authorization systems, save them, or export them to CSV format.
- Alerting: Permissions Management provides alerts powered by machine learning (ML) for anomalies, which increases efficiency in detecting unexpected shifts in activity.
- Copilot: Microsoft Entra Permissions Management supports automatic remediation using Copilot.
- Integrations: It can integrate with the Defender for Cloud dashboard for unified security management.
- Third-party support: Microsoft Entra Permissions Management also supports integration with third-party identity providers such as AWS IAM, Okta, and ServiceNow.
Use cases
Microsoft Entra Permissions Management can be applied in various scenarios to effectively manage permissions and improve your cloud security posture. Here are some common use cases:
- Discovery:
- Assess permissions risk by viewing the gap between permissions granted and permissions used.
- Discover and manage permissions across multiple cloud platforms, such as Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP), through a unified platform.
- Remediation:
- Match permissions to actual usage by removing/reducing permissions.
- Automatically remove permissions that are unused over a specific period.
- Enable on-demand and temporary grant of permissions to identities.
- Create custom roles based on the activity of users, groups, and apps.
- Monitor:
- Monitor permissions usage and changes in real time, leading to detection of anomalies or unauthorized activities.
- Track the compliance of permissions for industry standards.
These use cases ensure that permissions are continuously assessed, remediated, and monitored, empowering security teams in an organization to maintain a secure and compliant multi-cloud environment.
Licensing
A Microsoft Entra Permissions Management license is resource-based, but you are charged only for resources that use compute or memory, such as Azure Virtual Machines, Azure Kubernetes Service (AKS), AWS Elastic Kubernetes Service (EKS), Elastic Compute Cloud (EC2), Google Compute Engine, Google Kubernetes Engine (GKE), etc. It is priced at $10.40 per resource per month or $125 per resource per year.
It supports other types of resources, but you are billed only for those in the billable resources list. The table below shows this information.
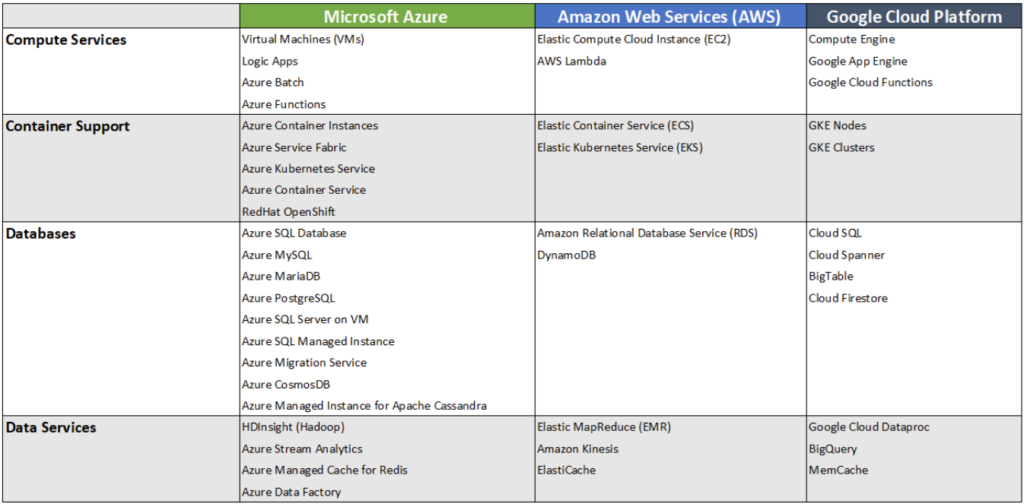
List of billable resources by cloud provider (source)
Note that before subscribing, Microsoft allows you to get a free trial of Permissions Management for 45 days.
Architecture
Microsoft Entra Permissions Management is a SaaS service consisting of multiple components.
- The Data Collector is a service that connects with the cloud provider to retrieve entitlement and activity data. You configure it with the credentials to do so.
- The collected raw data is stored in Object Storage.
- The raw data is processed using the Data Processing and Analytics service.
- The Data Lake store is used for analytics operations such as alerting.
- The Cloud Database is used by the application itself for serving the pages and different tabs.
- The Database handles the identity management to the Permissions Management application.
The following image illustrates the SaaS architecture of Microsoft Entra Permissions Management.
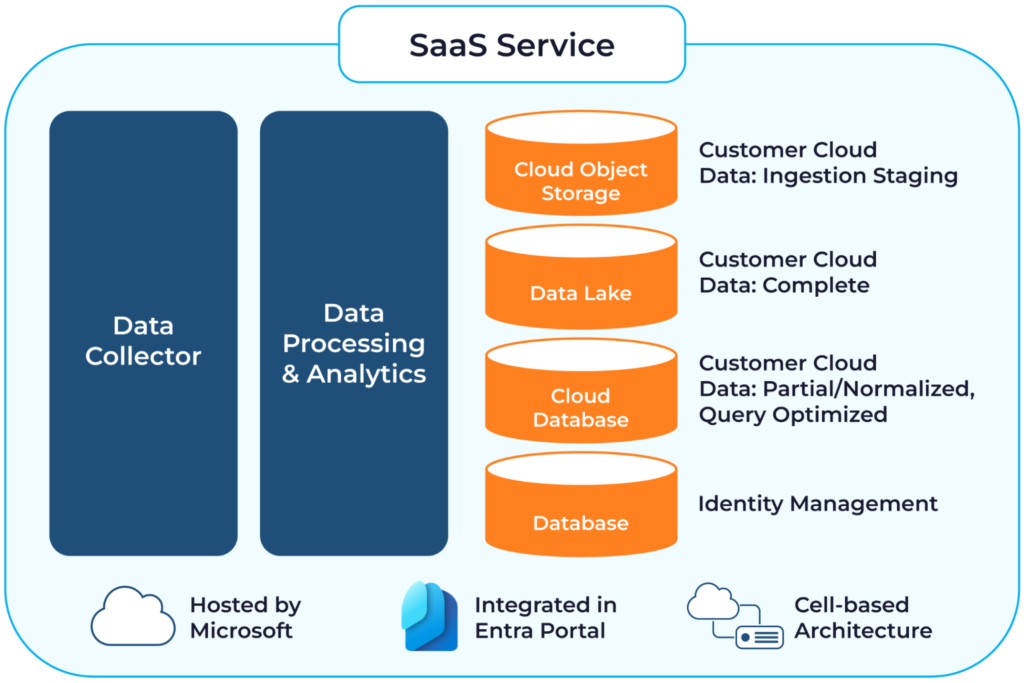
Permissions Management architecture (source)
The following are the key concepts and terminologies you must know to start with Permissions Management:
- Authorization system type: This refers to the cloud providers supported by Permissions Management, namely Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP).
- Authorization system: An authorization system is an account, subscription, or project that you manage from Permissions Management. For Azure, this is the Azure subscription; for AWS, it’s the AWS account; and for GCP, it’s a project.
- Controller: This is a configuration mode that, when enabled, allows you to make remediation changes directly from the Permissions Management dashboard.
- Billable resource: A billable resource in Permissions Management is a resource that uses compute and memory.
Enabling Microsoft Entra Permissions Management
In this section of the article, you will learn how to enable Microsoft Entra Permissions Management and onboard cloud providers.
The following prerequisites must be in place before you begin:
- A Microsoft Entra tenant
- An account with Billing Administrator permissions to start a trial or purchase a license
An account with the Permissions Management Administrator role for onboarding providers
Activating Microsoft Entra Permissions Management
Navigate to the Microsoft Entra admin center at entra.microsoft.com and sign in.
Select Permissions Management from the left navigation menu and click Try for free to start a 45-day trial. Alternatively, you can click the Buy now button to make a direct purchase.
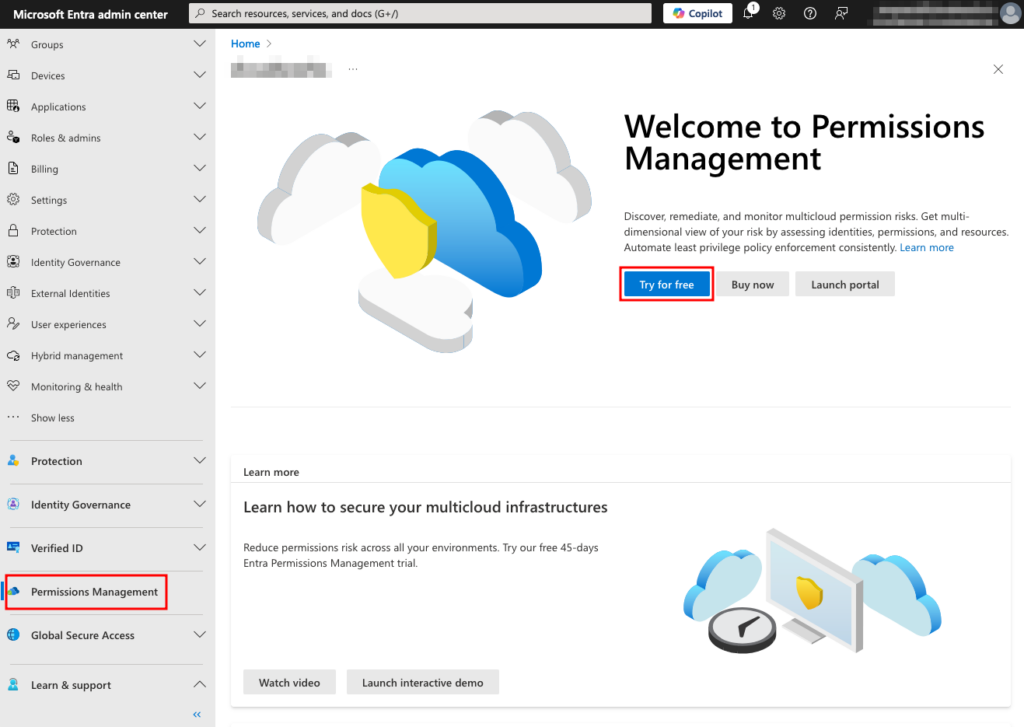
Permissions Management in the Microsoft Entra admin center
This will open a new page for signing up for the Microsoft Entra Permissions Management Trial. Your work or school email address should already be detected. Click Next to continue.
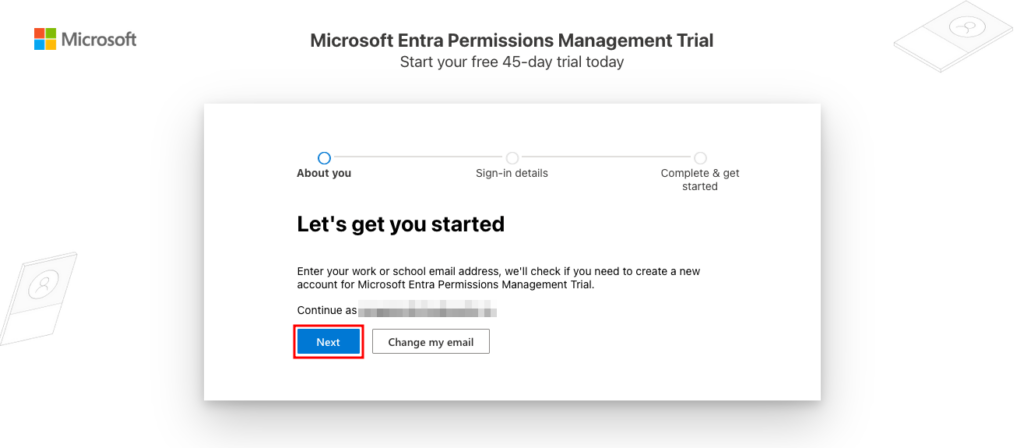
Sign up for the Microsoft Entra Permissions Management trial
Next, click Sign In and complete the sign-in process.
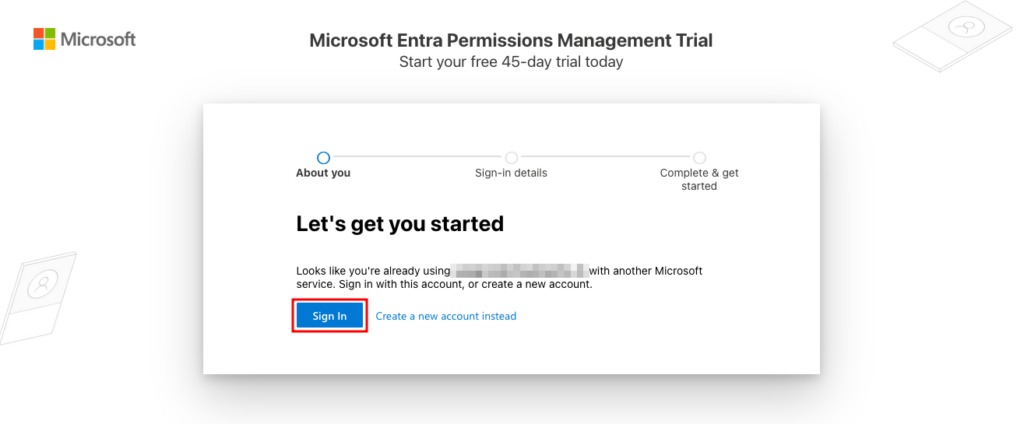
Sign up for the Microsoft Entra Permissions Management trial
Finally, click the Try now button to complete the trial sign-up process.

Confirm the order for the Microsoft Entra Permissions Management Trial
You will be presented with an order number. Click Continue, which will redirect you to the Microsoft 365 Admin Center. You have now successfully subscribed to Microsoft Entra Permissions Management, and you can close this window.
Back at the Microsoft Entra admin center, click Launch portal to open the Permissions Management portal in a new window.
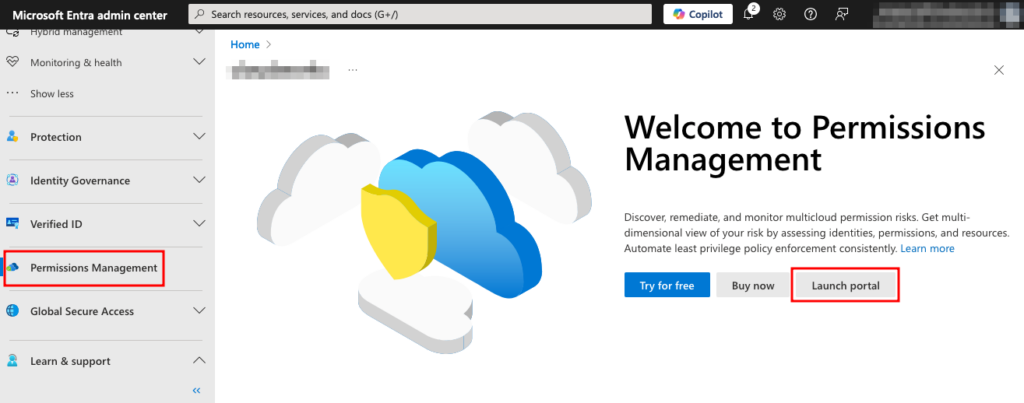
Launch the Permissions Management portal
This will open the Permissions Management portal in a new window. It will have a .cloudknox.io domain.
Onboarding Azure subscriptions
Since Microsoft Entra Permissions Management is built on Azure, onboarding an Azure subscription is straightforward. Let’s take a look at how to do this.
Before starting the onboarding process, make a note of the subscription IDs or the management group IDs you wish to onboard to Permissions Management. For this demonstration, we will onboard a single Azure subscription.
In the Data Collectors tab, ensure that Azure is selected. Then click Create Configuration to configure a data collector.
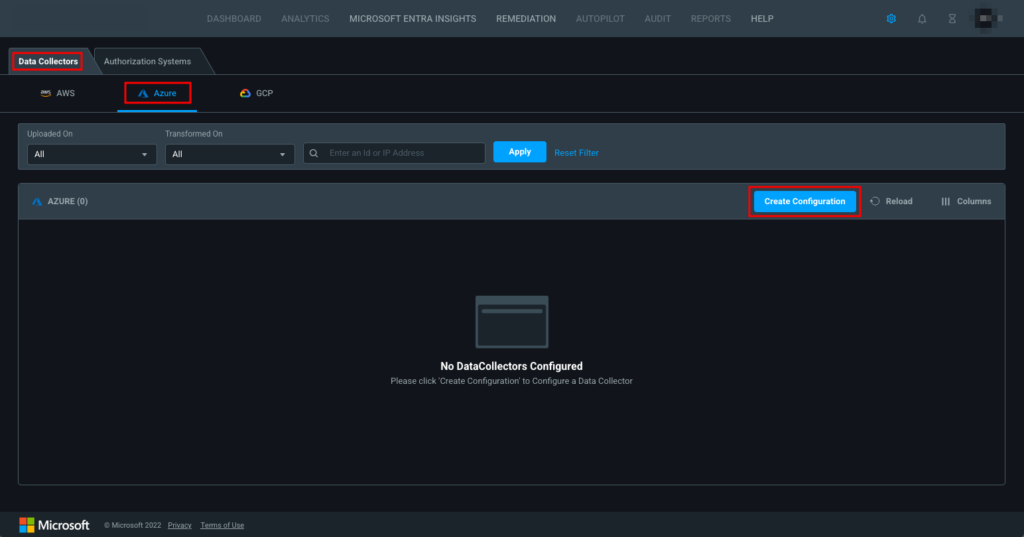
Create an Azure data collector configuration
Select the Enter Authorization Systems radio button and paste the subscription ID in the box provided.
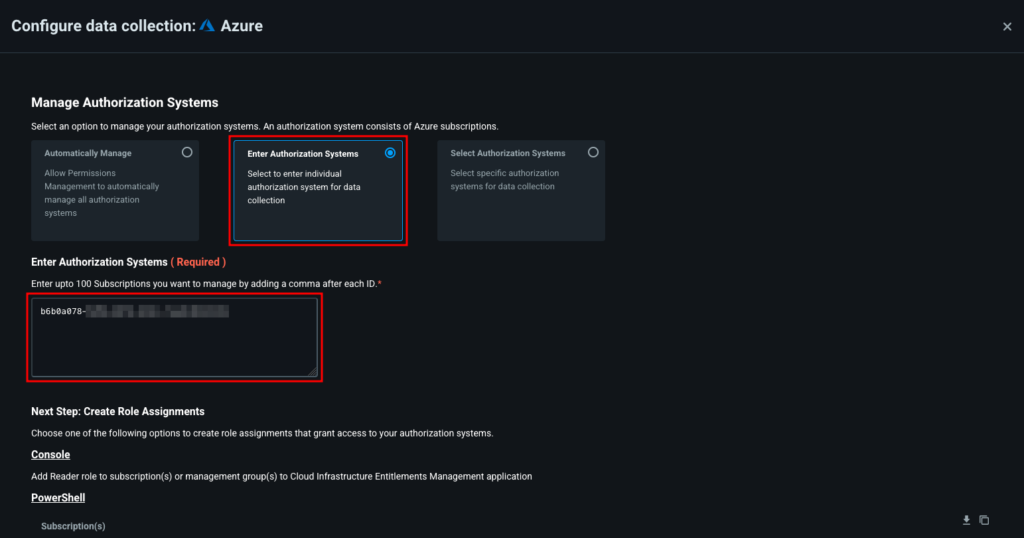
Select an Authorization System management option.
Scroll down and copy the command under Azure Command-Line for subscriptions. Do not click Next yet.
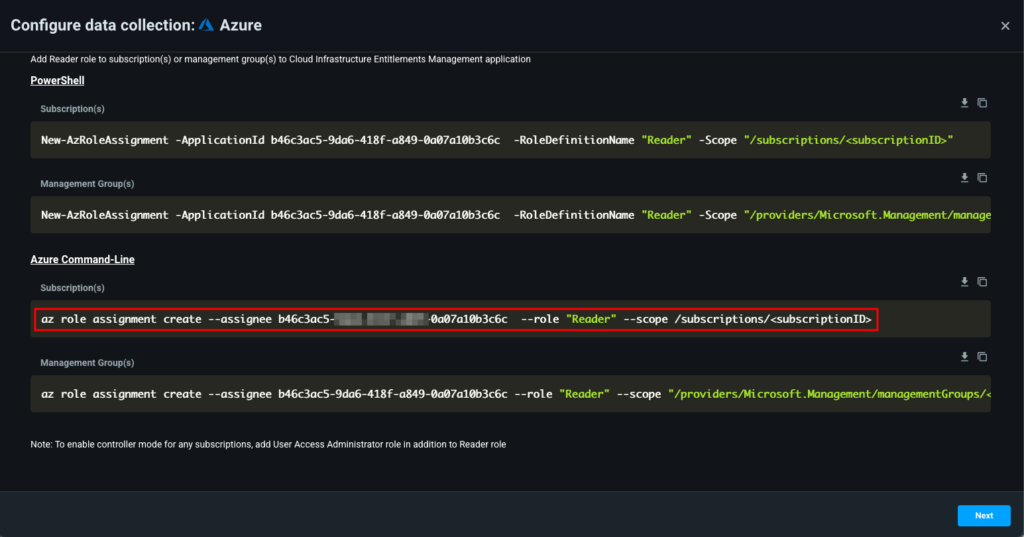
Copy the command to assign a reader role to the Permissions Management app.
The next step is to create a Reader role assignment for the CIEM application in the subscription. The easiest way is to use the Azure Cloud Shell in the Azure Portal.
Navigate to the Azure Portal and click the Cloud Shell button on the top next to Copilot. Once the Shell has initialized, paste the command copied earlier and replace <subscriptionID> in the command with the actual value. Press Enter to execute the command.
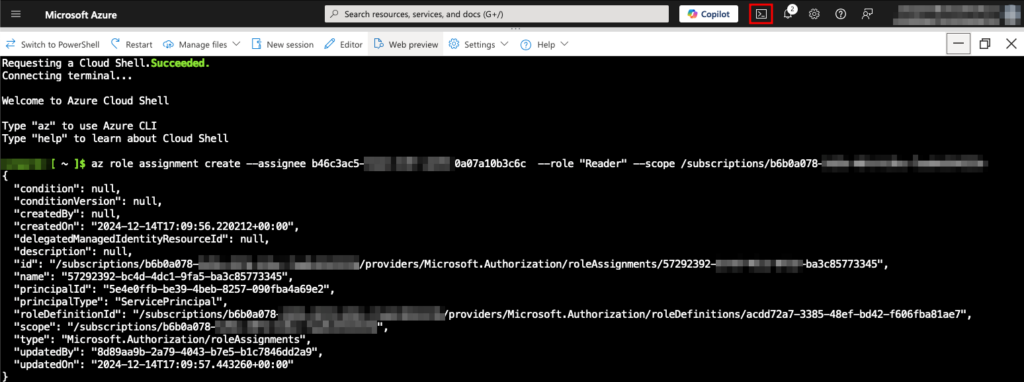
Execute the reader role assignment command in Azure Cloud Shell
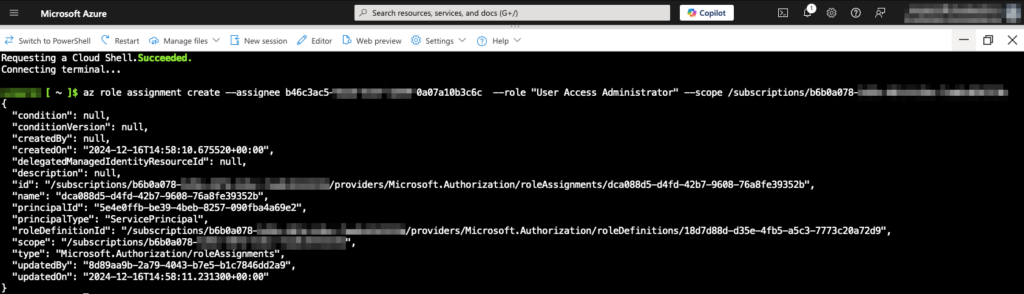
If you want to enable the Controller, you must also give the User Access Administrator role to the Permissions Management application. Re-run the same command, replacing the word Reader with User Access Administrator.
Go back to the Permissions Management portal and click Next. Click the Verify Now & Save button in the Review and Confirm screen.
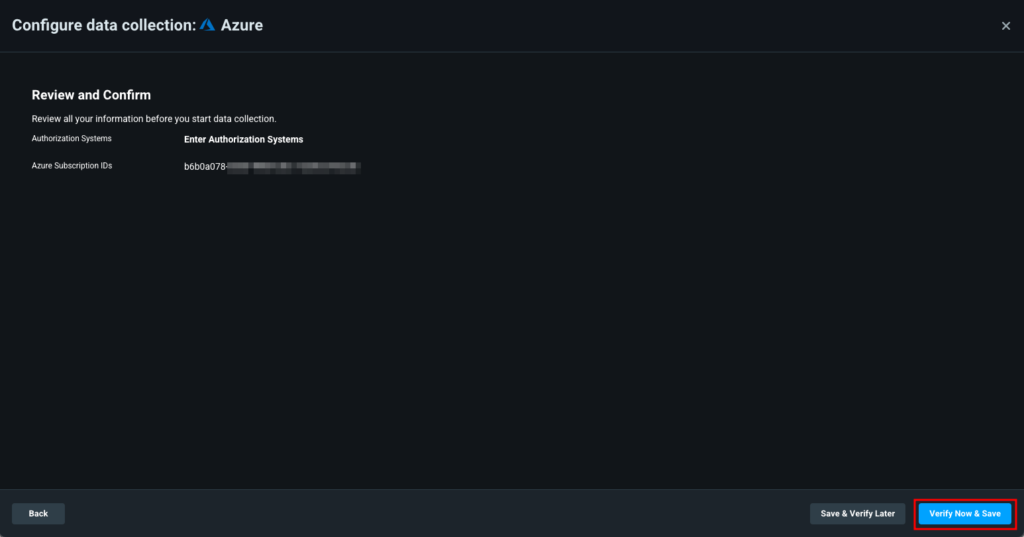
Verify and save the Authorization System
Wait until the status changes from Collecting Inventory to Consented to Onboarded. This takes a few minutes. You will also notice that the Authorization System Status is now ONLINE.
Onboarding Other Cloud Providers
As discussed earlier, Microsoft Entra Permissions Management supports AWS and GCP, too. Here are reference links for them:
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Navigating the Microsoft Entra Permissions Management portal
We will now learn how to navigate around the Permissions Management portal, especially focusing on the dashboard, analytics, remediation, audit and reports tabs.
Overview and Permissions Creep Index (PCI)
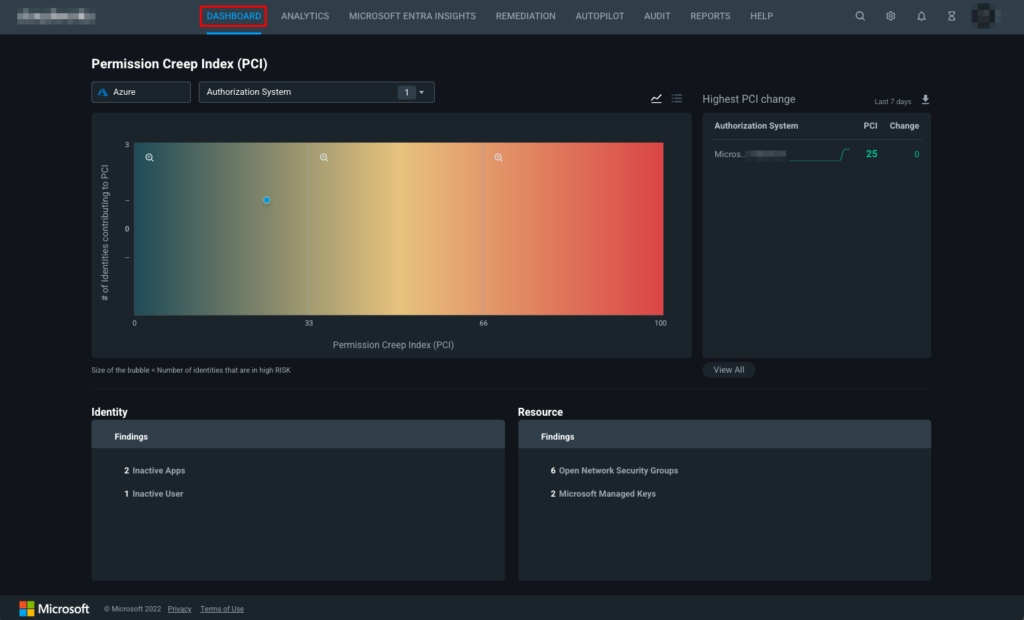
Select the DASHBOARD tab to view the Permissions Creep Index (PCI) and overall findings for Identity and Resources. The Identity tile shows the number of inactive apps, users, etc., while the Resource tab shows the number of resources with overprivileged identities, inactive identities, and unused permissions.
Analytics
The Analytics tab provides detailed visibility into the identities in an Authorization System (cloud provider) and their state of entitlements (permissions). It shows details such as the account it belongs to, PCI, tasks (permissions) granted and executed, the number of resources it has access to, the group it is a member of, and the last activity of that identity. Expanding an identity gives you additional details such as unused and used tasks, detailed information on Azure roles that the identity is assigned, etc.
You can filter the view based on users, groups, active resources, serverless functions, and more.
The image below shows a detailed analysis of an identity called githubactions.
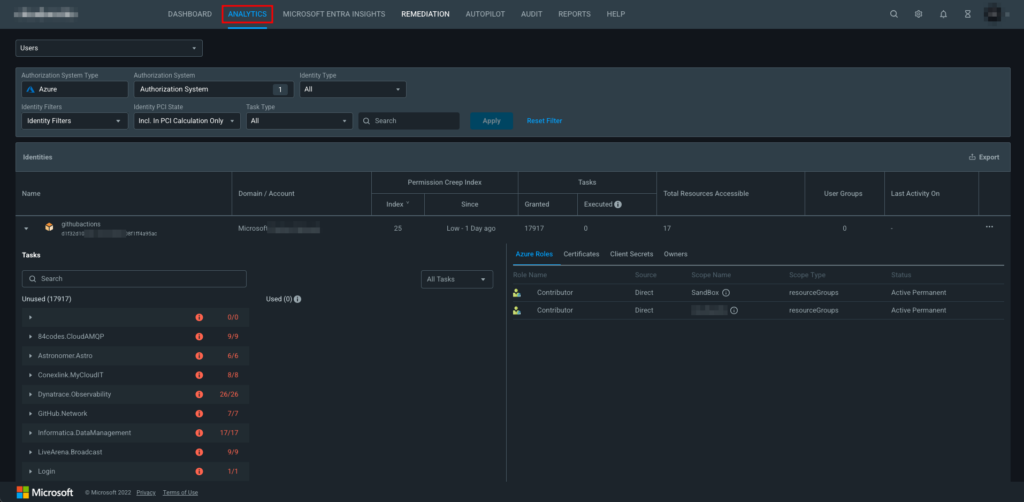
Permissions Management Analytics view
Remediation
Permissions Management provides multiple options for remediation, also called right-sizing, such as:
- Creating custom roles based on the past activity of users, groups and apps. You can also create custom roles from an existing role or create one from scratch.
- Quick actions that allow correcting permissions with a single click. There are four options available: Revoke Unused Tasks, Revoke High-Risk Tasks, Revoke Delete Tasks, and Assign Read-Only Status.
- Finally, you can remediate using Autopilot, where you use prebuilt rules to automatically apply the recommended remediations.
In the following example, we will see how to use quick actions to right-size permissions.
In the REMEDIATION tab, select Permissions and then filter to search for Users with the status Inactive. Click Apply to see the list. Next, select a user to view the Quick Actions to the right.
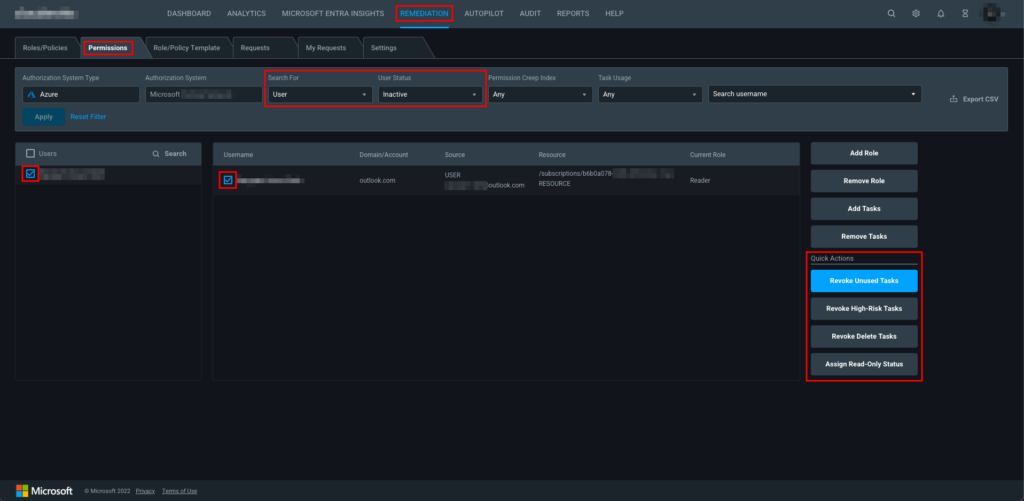
Remediate an identity with Quick Actions
Selecting a quick action generates a script you can copy or download to execute using a command line or shell. You can also download a JSON version of the script.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Audits
You can query the historical activity log for Authorization Systems Type or Authorization Systems in the Audit tab. Queries are no-code-based and use a drop-down approach, making them easy to construct. You can write multiple queries using tabs and save, load, and export the queries.
Here’s an example of a query for virtual machines that have been stopped/deallocated in the last 90 days.
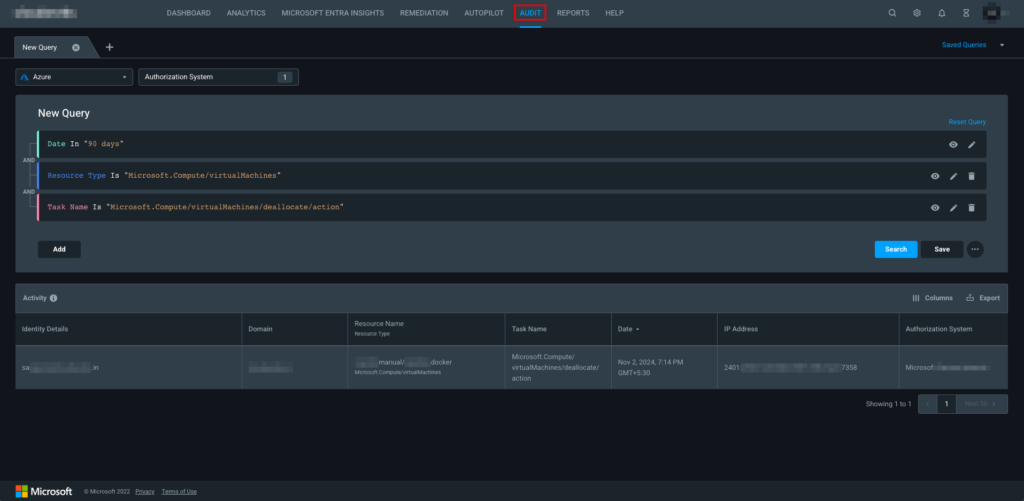
Query Permissions Management for auditing
Reports
This tab is where you can view and use the built-in system reports or create a custom report of your own. As of this writing, there are 10 system reports. The format of the reports vary depending on the report and could be in CSV or XLSX format.
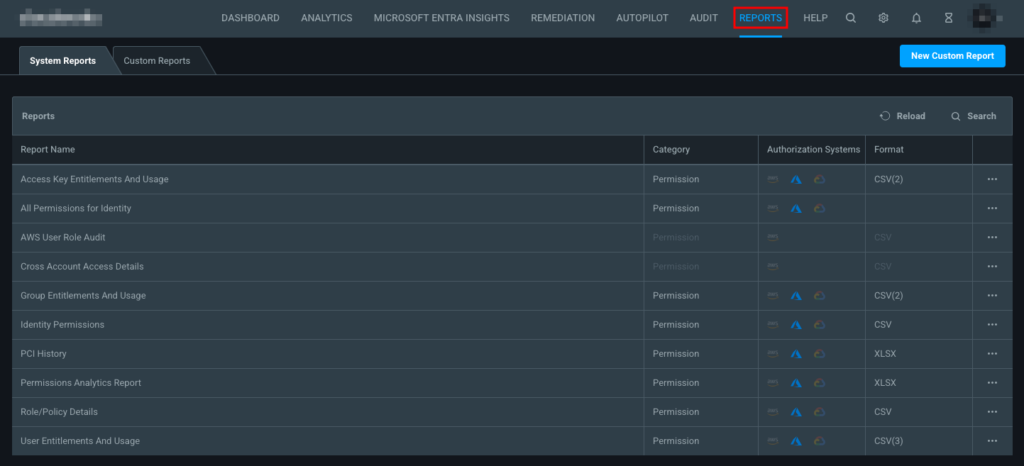
View built-in system reports in Permissions Management
For example, let’s click on the Permissions Analytics Report, which will load the report on a new page. This report displays a lot of findings such as inactive identities and groups, super identities, over-provisioned active identities, PCI distribution, etc. You can use the left navigation menu to view them. Reports can be exported to PDF.
The default view will load the inactive user identities as in the screenshot below:
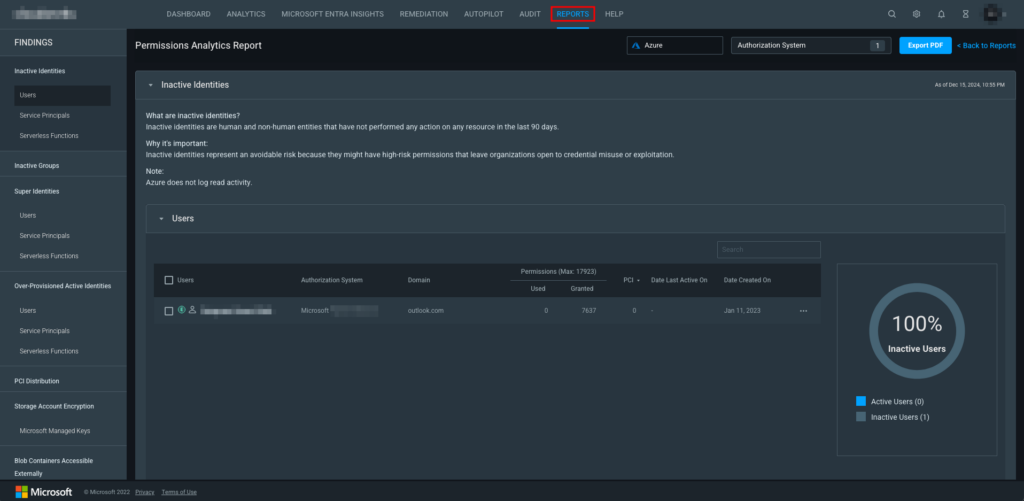
View of the Permissions Analytics built-in system report
Best practices
Here are some best practices for administering and operating Permissions Management:
- Define Permissions Management administrators in your organization with clear responsibilities.
- Implement a folder structure for organizing the Authorization Systems.
- Set PCI thresholds based on identity type and your organization’s use case.
- Consider using built-in reports for general visibility and insights.
- Implement a reporting system by identifying key stakeholders who would consume reports and schedule a report delivery to their mailboxes.
- Create, save and share custom queries that align with your organization’s compliance needs. Review them regularly.
- Implement continuous monitoring by creating alerts to be notified for anomalies, potential threats, overprivileged accounts, etc.
- Additionally, you can configure automated responses to these alerts like remediation.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Microsoft Entra Permissions Management provides a single-pane solution for clarity and control over identity permissions across multi-cloud environments. It provides visibility into the state of permissions through discovery, facilitates right-sizing through remediation, and provides continuous monitoring so organizations can adhere to compliance requirements such as the least privilege principle, working toward a zero-trust strategy.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content