Home » Implementing Zero Trust Security with Microsoft Entra » Implementing Microsoft Entra ID Protection: A Step-by-Step Guide
Implementing Microsoft Entra ID Protection: A Step-by-Step Guide
Learn about best practices for effectively using Microsoft Entra ID Protection, such as enabling and configuring risk policies and integrating with Conditional Access for enhanced access security.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Microsoft Entra ID Protection is a Microsoft Azure identity security solution that detects, investigates, and remediates identity-based threats. It gives organizations the proper tools to safeguard user accounts by identifying risky sign-ins, potentially dangerous apps, and compromised identities. This solution integrates seamlessly with other Microsoft Azure and Entra ID products, forming a robust identity and access management ecosystem.
Microsoft Entra ID security also works with other cloud security offerings, like Conditional Access, and can be fed back to a security information and event management (SIEM) tool to enable a layered defense strategy. With the help of advanced machine learning, it automates threat response and enforces risk-mitigating policies after carefully analyzing different data sources and historical data.
In this article, we focus on best practices for effectively using Microsoft Entra ID Protection in your environment. Some concepts in this article, such as implementing other advanced security and cloud concepts, will not be covered. However, readers can expect a clear and practical guide to understanding and utilizing Microsoft Entra ID Protection.
Summary of key Microsoft Entra ID Protection best practices
This article will discuss five best practices for Microsoft Entra ID Protection, which are summarized in the table below.
| Best practice | Description |
|---|---|
| Enable and configure risk policies | Proactively protect your identities by configuring user and sign-in risk policies in Microsoft Entra ID Protection. Customize the policies based on your organization’s risk tolerance and security requirements. |
| Integrate Conditional Access with ID Protection | Strengthen access security by integrating Conditional Access policies to enforce granular access controls based on risk assessments, blocking or challenging risky sign-ins. |
| Regularly monitor risk detections | Stay informed about potential threats by utilizing Microsoft Entra’s reporting and monitoring tools to gain insights into detected risks. Regularly review risk detections, investigate suspicious activities, and take appropriate actions to mitigate potential security breaches. |
| Maintain a strong authentication framework | Implement strong authentication methods, such as passwordless authentication and MFA, for an extra layer of security. |
| Recognize security threats | Be the first line of defense by training employees to recognize and respond to common security threats, such as phishing attempts, suspicious emails, and risky sign-in requests. |
Enable and configure risk policies
Risk policies in Microsoft Entra ID Protection provide automated responses to potential security threats by evaluating user risk and sign-in risk. User risk refers to the likelihood of a compromised account, while sign-in risk measures the probability that a specific authentication attempt is suspicious. These policies are essential for proactively identifying and mitigating identity-based threats.
To enable and configure user risk policies, follow these steps:
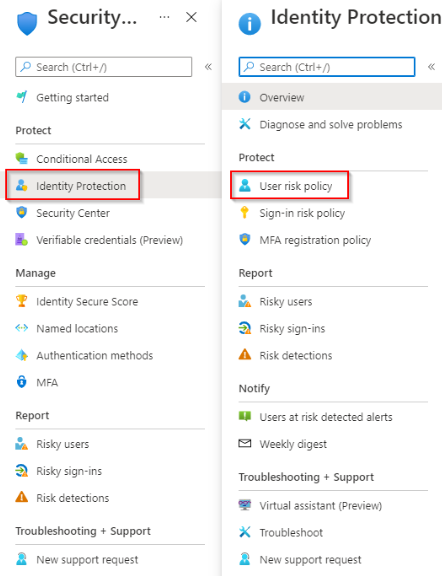
1. Navigate to the Microsoft Entra ID portal and access the Identity Protection settings as a Global Administrator.
2. Under Manage, click Security > Protect > Identity Protection > User Risk Policy.
Navigate to user risk policy configuration page via Identity Protection (source)
3. Click All users > Exclude > 0 users and groups selected and click Select.
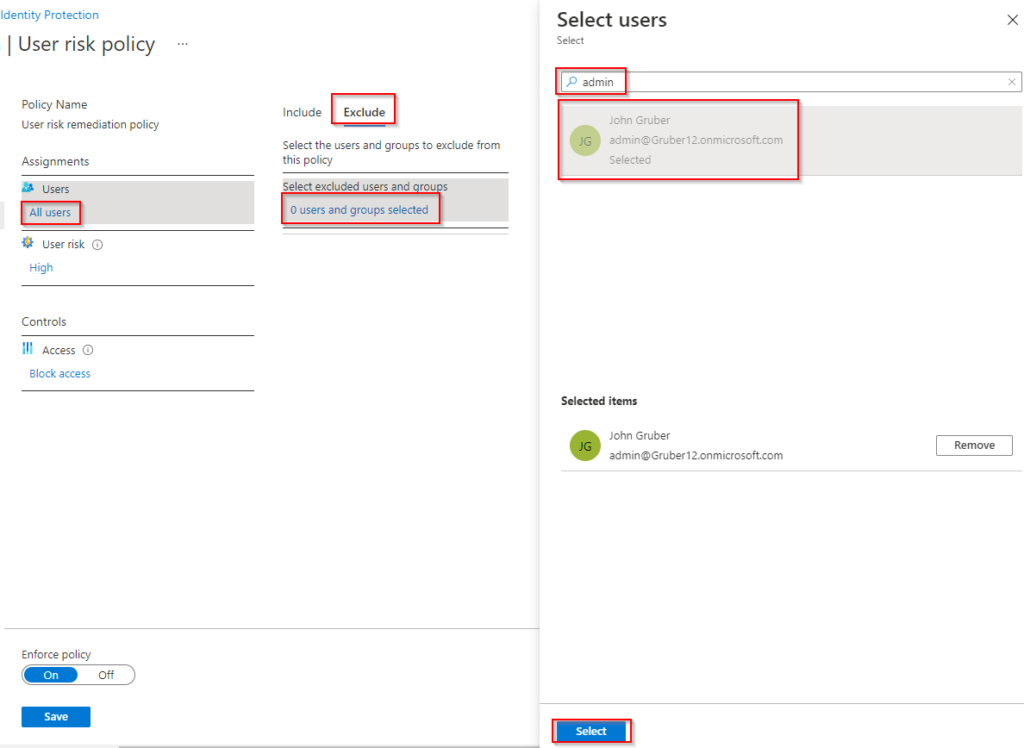
Configure user risk policies for all users. (source)
We may also exclude members in this step, but we wouldn’t recommend doing this as it introduces a risk attackers can exploit.
4. Click Low and above (original value found under User risk). Click High > Done.
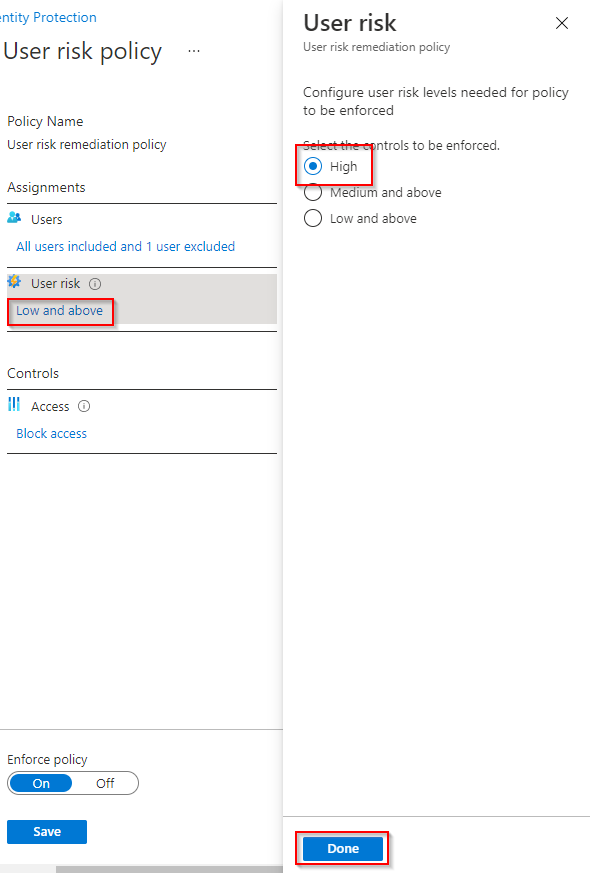
Enabling High risk on user risk policies (source)
5. Click On (original value Off found under Enforce policy). Click Save.
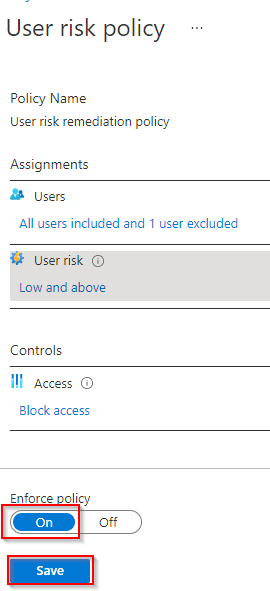
Enabling the user risk policy enforcement (source)
To enable and configure sign-in risk policies, follow these steps:
1. Navigate to the Microsoft Entra ID portal and access the Identity Protection settings as a Global Administrator.
2. Under Manage, click on Security > Protect > Identity Protection > Sign-in Risk Policy.
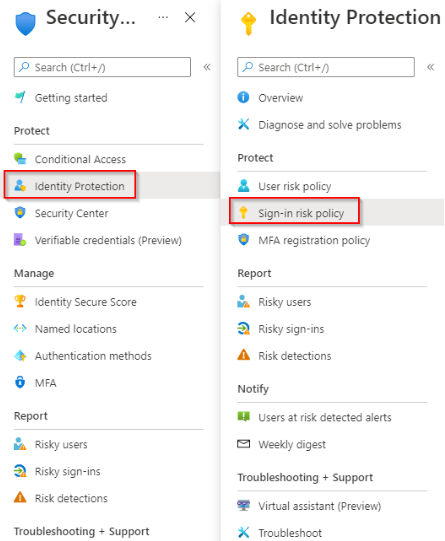
Navigate to Sign-in risk policy configuration page via Identity Protection (source)
3. Click All users > Exclude > 0 users and groups selected and click Select.

Configure sign-in risk policies for all users. (source)
Like user risk policies, you can exclude members from this step, but we don’t recommend doing this for the same reason.
4. Click Low and above (original value found under Sign-in risk). Click High > Done.
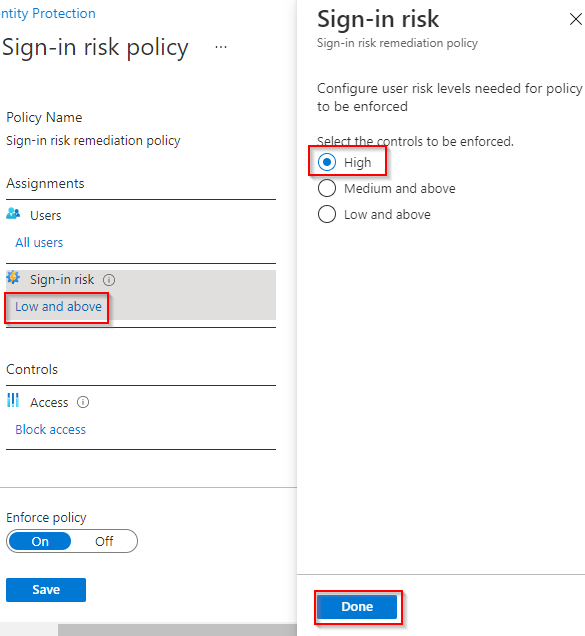
Enabling High risk on sign-in risk policies (source)
5. Click On (original value Off found under Enforce policy). Click Save.
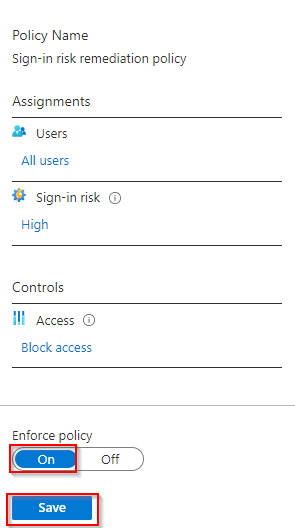
Enabling the sign-in risk policy enforcement (source)
Once the account is blocked due to a suspicious sign-in, the user will receive a block message that is similar to the screenshot below:
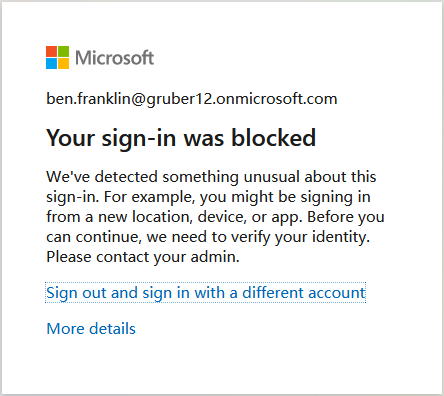
Sign-in blocked due to user and sign-in risk policies (source)
Aligning risk policies with organizational security goals is critical to balancing security and usability. For example, organizations should consider the sensitivity of protected resources when defining risk thresholds. Reviewing policy effectiveness periodically and adjusting thresholds to address evolving threat landscapes is also beneficial.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Integrate Conditional Access with ID Protection
After setting up your initial risk policies, Microsoft Azure recommends setting up your Conditional Access policies. Conditional Access is a core feature in Microsoft Entra ID protection that enables your organization to enforce security policies based on specific and granular conditions. Organizations can more effectively secure sign-ins under particular conditions by integrating Conditional Access policies with the previously discussed risk policies.
To integrate Conditional Access policies within your Entra ID environment, follow these steps:
1. Open the Azure Active Directory admin center > All services > Azure AD Conditional Access > New policy > Create new policy.
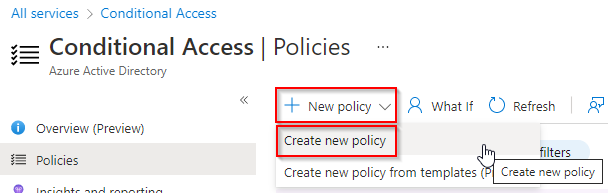
2. Set the name to Sign-in Risk Policy.
3. Click 0 users or workload identities selected. Click All users.
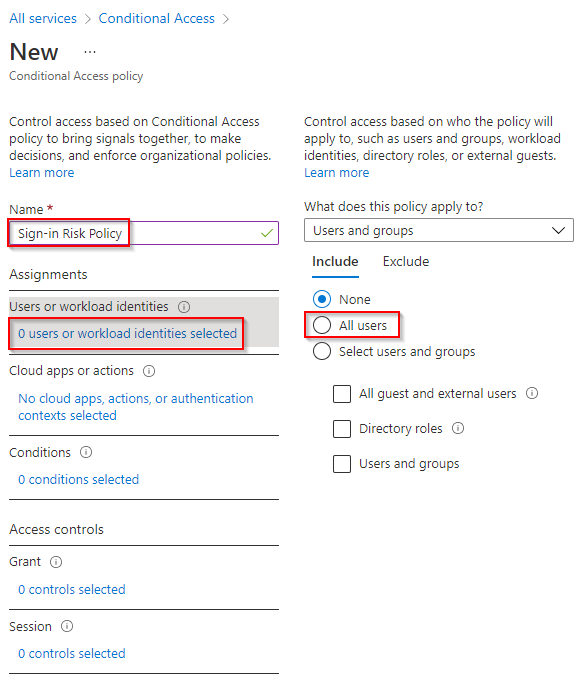
4. Click No cloud apps, actions, or authentication contexts selected. Click All cloud apps.
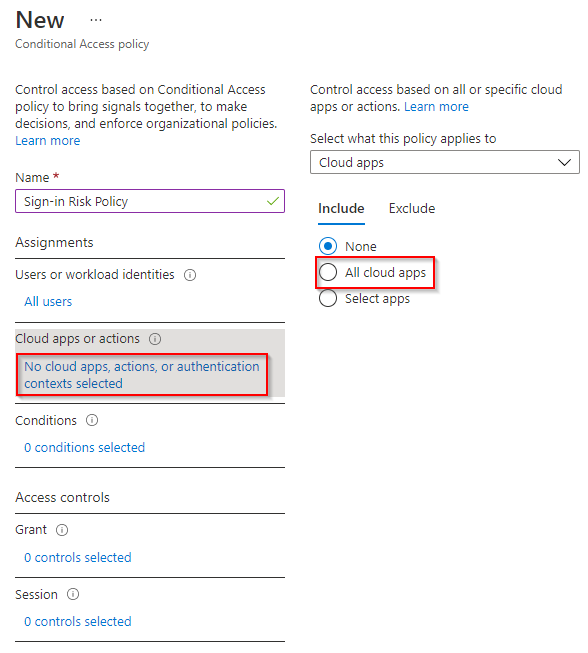
5. Click 0 conditions selected > Not configured (found under Sign-in risk). Click Yes > High > Done.
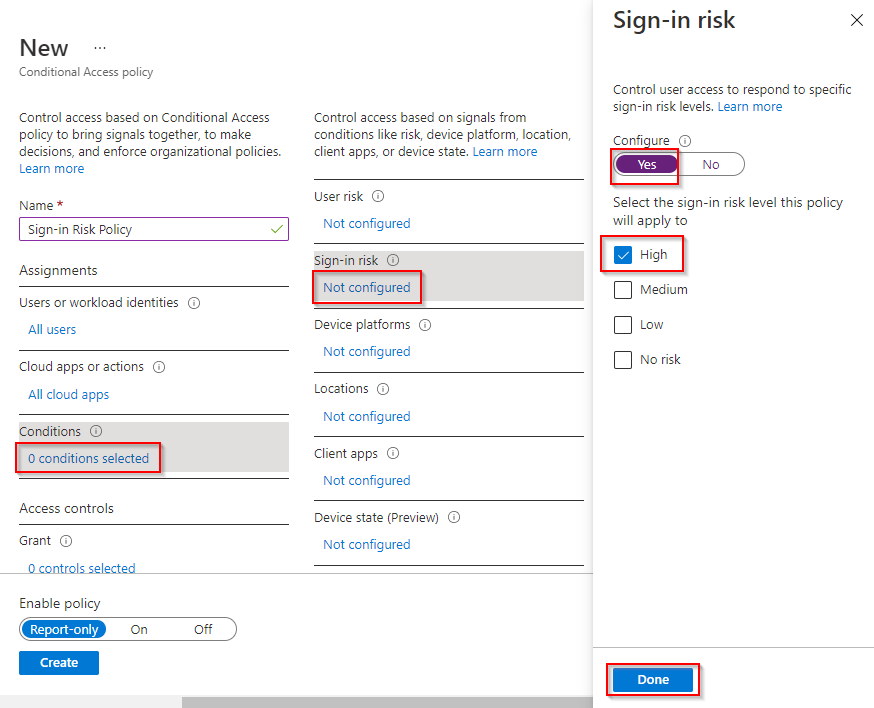
6. Click Not configured (found under Device state) > Yes > Exclude > Device Hybrid Azure AD joined. Click Done.
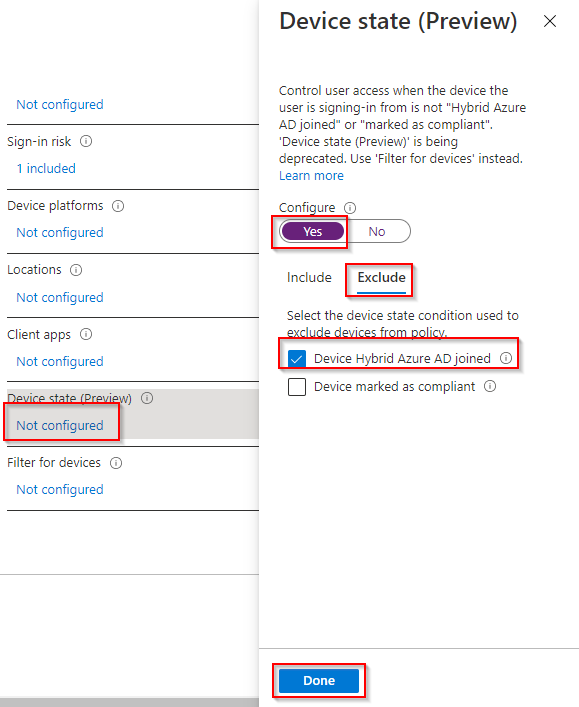
7. Click 0 controls selected (found under Grant). Click Grant access > Require multi-factor authentication > Select. Click On (found under enable policy) > Create.
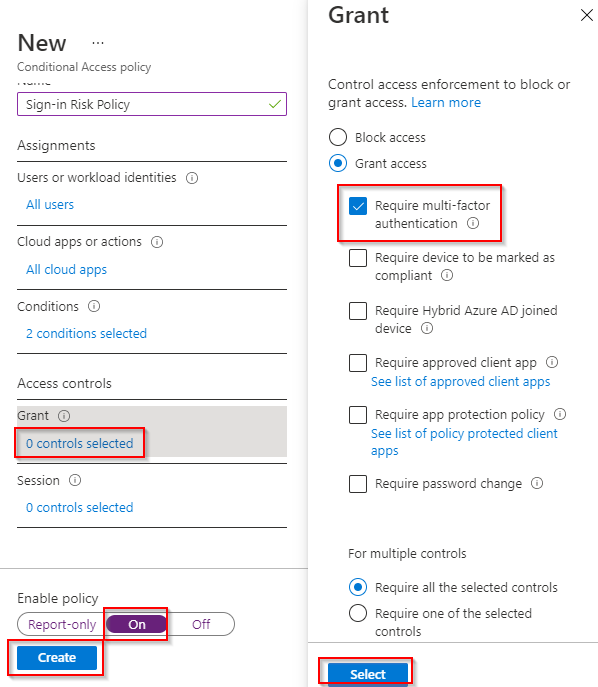
In a real-world scenario, it is best to test risk and Conditional Access policies on a few pilot users and administrators inside an isolated environment before implementing them in a live production setting. This process ensures that the policies work as expected and that users and administrators are not accidentally locked out of their environments.
In an emergency, Cayosoft Guardian provides recovery of Conditional Access policies. Whether changes are made by accident or malicious actors, Cayosoft Guardian can restore a previous good state to Microsoft Entra ID. This functionality is not available natively in Microsoft Entra ID—if a Conditional Access policy is accidentally changed or deleted, it is treated as a hard deletion.
Regularly monitor risk detections
Continuous monitoring of risk detection is a crucial component of maintaining robust identity security in Microsoft Entra ID Protection. Regularly reviewing detected risks helps organizations identify potential threats early and take immediate action to prevent breaches. This proactive approach minimizes the impact of compromised accounts and suspicious sign-ins.
One access policies are set, you can check and start investigating any risks detected via the Identity Protection report page. Under the report page, there are three reports that you can rely on when performing any investigations, as shown below.
| Report | Description |
|---|---|
| Risky Users Report |
|
| Risky Sign-ins Report |
|
| Risk Detections Report |
|
To navigate to the reports page from the Entra ID page, select Security > Identity Protection > Report.
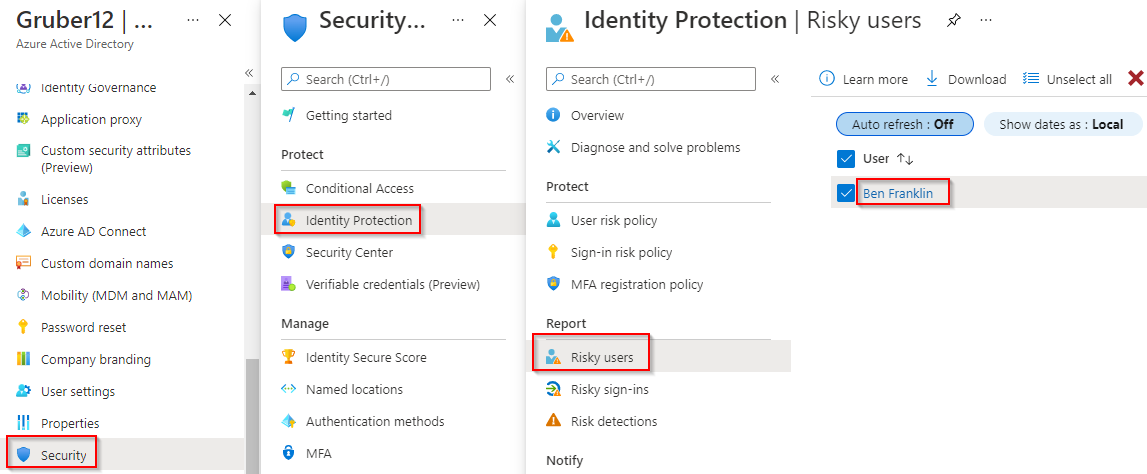
Remediating a risky user
Consider a scenario where a user’s sign-in is flagged as a high risk due to multiple failed login attempts from an unfamiliar location. The security team can investigate the activity, verify its legitimacy, and apply corrective actions from the Reports page.
To remediate a user, follow these steps:
1. Click the user risk you want to dismiss from the risky users report.

2. Click the ellipsis (…) > Dismiss user risk.
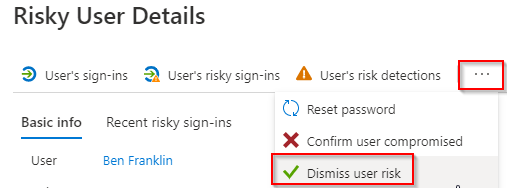
3. Click Yes.
4. Then go to Risky sign-ins
5. Click the sign-in you want to dismiss. Click the ellipsis (…) > Confirm sign-in safe.
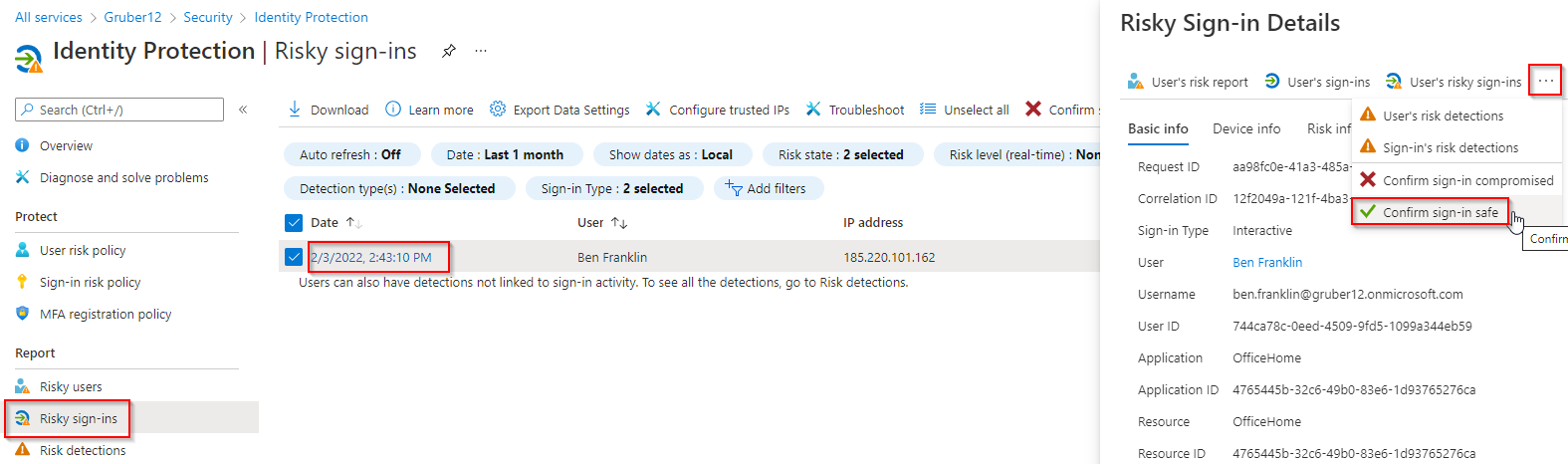
6. Click Yes to confirm the remediation.
Have the user wait for 15 minutes before signing in. However, remember to perform the necessary investigation before confirming and remediating a risky user’s sign-in.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
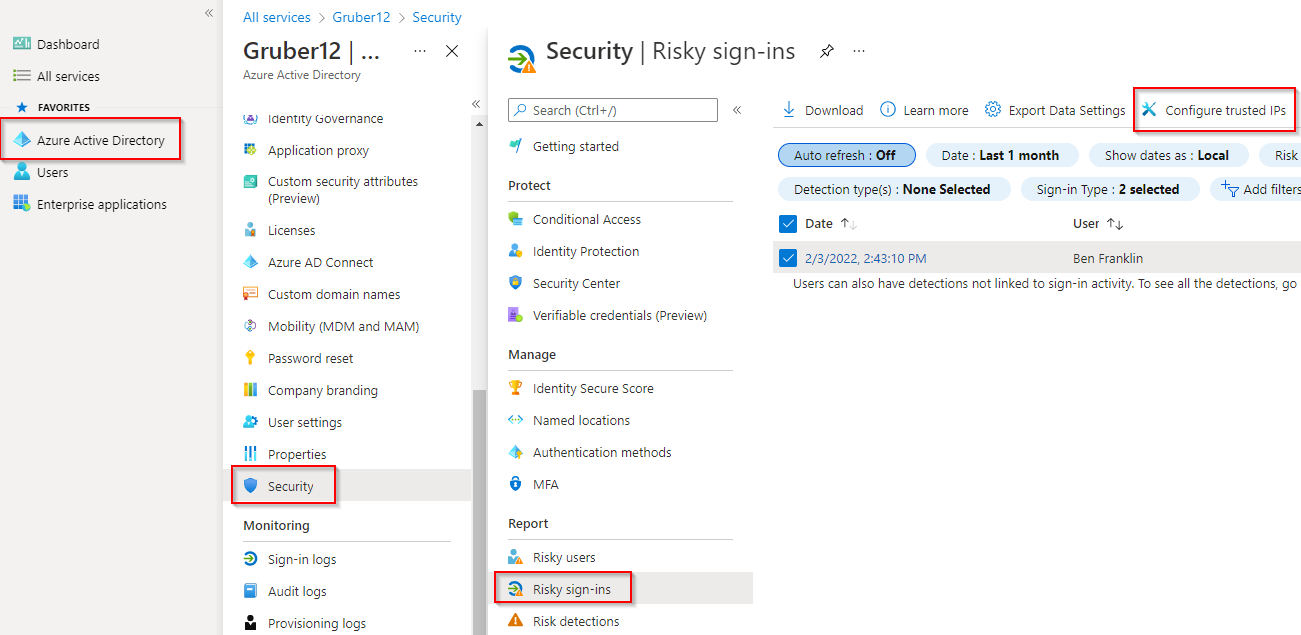
Whitelisting an IP address range
Another potential action is to flag your IP addresses as trusted, which means that users will be less likely to be blocked in a false positive scenario.
To whitelist a single IP address or an IP range, follow the steps below:
1. From the risky sign-ins report, click on Configure trusted IPs.
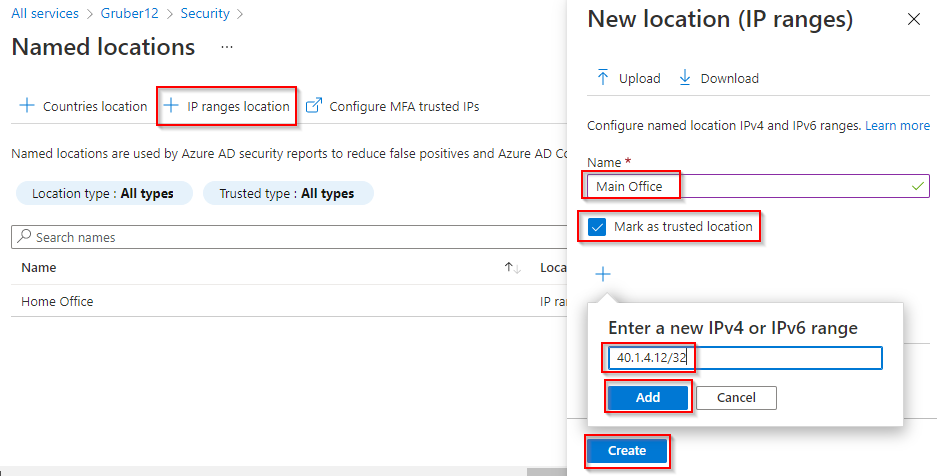
2. Click IP ranges location.
3. Enter a Name, for example, Main Office. Click Mark as trusted location. Click the + plus sign. Enter your public IP address + subnet mask. Click Add. Click Create.
Microsoft Entra ID Protection also uses machine learning to detect risks intelligently, so every remediation contributes to training the policies to become more intelligent. This targeted remediation mitigates threats, trains policies, and strengthens the organization’s security posture.
In addition, Cayosoft Guardian delivers real-time monitoring capabilities and provides administrators with detailed logs to understand unauthorized actions. These logs can help develop a more granular conditional access policy.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Maintain a strong authentication framework
A strong authentication framework is essential for protecting user accounts and reducing security risks. It guarantees that only authorized users can access vital resources, reducing the possibility of identity-based attacks.
Here are some points to consider in maintaining a strong authentication framework. Most of these items are natively available in Microsoft Azure:
- Enable multi-factor authentication (MFA) for all user accounts in Microsoft Entra ID. Since the second half of 2024, Microsoft Azure has enforced and enabled an MFA policy for all users. The user must set up at least one authentication method (by default) to allow MFA during the first login.
- Configure additional authentication methods, such as passwordless methods like Windows Hello for Business.
- Having an authenticator like Microsoft Authenticator as one of the primary authentication methods provides an additional layer of protection.
- Have another third-party program handle single sign-on (SSO). Dedicated SSO programs serve as another layer of security gateway before signing in applications like Microsoft 365 apps, giving administrators more visibility into user sign-ins.
- Configure Conditional Access policies to detect specific sign-in locations and conditions, such as whether a user has authenticated through an SSO before authenticating in Microsoft Azure.
Cayosoft provides a unified solution for securing and managing all your Microsoft Entra ID directories and reporting on users’ MFA status. To help you monitor MFA enrollment, a report of users and MFA status can be created on a schedule. Alternatively, administrators can also monitor authentication activity through the Identity Protection dashboard to identify and respond to anomalies.
Recognize security threats
Recognizing security threats is critical for strengthening an organization’s defenses against cyberattacks. Specifically, Microsoft Entra ID Protection addresses various common security threats, including, but not limited to:
- Phishing attempts to steal user credentials
- Brute-force attacks targeting weak passwords
- Credential stuffing using previously compromised credentials
- Risky sign-ins from unfamiliar or malicious locations
- Account takeover through compromised or shared accounts
However, despite having all of the security tools at your disposal, without user awareness, your organization slowly loses efficiency in protecting your environment. By continuously promoting user awareness, you can ensure that end-users and administrators understand the risks they face and the actions needed to mitigate them.
To educate users effectively:
- Provide real-world examples of attack scenarios, such as phishing emails or suspicious sign-in attempts, to illustrate the risks clearly.
- Offer training sessions for end-users and administrators on identifying and responding to security threats.
- Develop guidelines for verifying the authenticity of sign-in attempts and responding to MFA challenges appropriately.
- Distribute regular updates on emerging threats and recommended security practices.
- Encourage a culture of security awareness by recognizing and rewarding proactive behaviors that contribute to organizational safety.
By combining robust user education with Microsoft Entra ID Protection’s capabilities, organizations can significantly enhance their resilience against evolving cyber threats.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Microsoft Entra ID Protection offers a comprehensive approach to mitigating identity-based threats, combining automated tools with best practices for proactive security management. By implementing effective risk policies, integrating Conditional Access, maintaining strong authentication frameworks, and fostering security awareness, organizations can strengthen their defense against evolving cyber threats. These measures ensure a balance between robust security and operational efficiency, safeguarding both users and resources.
To learn more about how Cayosoft Administrator can significantly reduce the time needed to detect risky users and sign-ins, request a free demo here.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content