Home » Implementing Zero Trust Security with Microsoft Entra » Strengthening Security with Microsoft Entra ID Governance
Strengthening Security with Microsoft Entra ID Governance
Learn best practices for leveraging Microsoft Entra ID Governance and optimizing identity management to strengthen your organization's security.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Microsoft Entra ID Governance is a comprehensive identity governance solution designed to help organizations manage access lifecycles and minimize security risks. It offers a unified framework for controlling who has access to resources, under what conditions, and for how long. You can ensure that access is granted based on well-defined policies.
Identity governance balances security with user productivity, ensuring that the right users have appropriate access to resources when needed while protecting sensitive data. As organizations increasingly adopt cloud services and remote work models, identity governance reduces risks like unauthorized access and over-privileged accounts.
However, it also comes with challenges, such as managing the lifecycle of user identities, ensuring least privilege access, and maintaining visibility and control over role bindings. Organizations struggle with the lack of a centralized view and managing identities across multiple environments. Overcoming these obstacles requires combining automation, continuous monitoring, and adaptive policies.
This article explores best practices for leveraging Microsoft Entra ID Governance to address identity governance challenges, optimize identity management, and strengthen your organization’s security posture.
Summary of key Microsoft Entra ID governance best practices
This table summarizes five best practices organizations should consider when working with Microsoft Entra ID Governance.
Best practice | Description |
Implement Role-based access control (RBAC) | Define and assign roles based on job functions to ensure appropriate access levels. |
Automate identity lifecycle management | Implement automated workflows for onboarding, changes, and offboarding processes. |
Enforce multi-factor authentication (MFA) | Require MFA for all users, especially for privileged accounts |
Use privileged identity management (PIM) | Control and monitor privileged access with just-in-time (JIT) and time-bound permissions |
Actively monitor and audit for suspicious activities | Utilize logging and auditing features to track and analyze identity-related events. |
Identity governance requires more than simply assigning roles and permissions; it requires a thoughtful blend of security measures, automation, and proactive management.
#1 Implement role-based access control (RBAC)
One of the core principles in securing your organization’s identity management system is the principle of least privilege. It dictates that users should only be granted the minimum access level necessary to perform their job functions. That way, you can reduce the attack surface and mitigate the risk of internal threats or compromised accounts being misused.
Microsoft Entra ID Governance makes it easy to implement this principle through Role-Based Access Control (RBAC). RBAC allows you to define roles that align with specific business functions and then assign users to these roles. Microsoft Entra provides a range of built-in roles designed to fit common administrative and operational needs, such as:
- Global Administrator: Can manage all aspects of Microsoft Entra ID, typically reserved for a select few with top-level responsibilities.
- User Administrator: This is a privileged role that can manage all aspects of users and groups, including password resets.
- Security Reader: Grants read-only access to security-related features: useful for teams that monitor security but don’t require control over configurations.
These roles come with predefined permissions for consistency and compliance with security best practices.
However, not all organizations fit neatly into predefined roles. Custom roles offer the flexibility to tailor RBAC to your organization’s unique needs. You can fine-tune permissions and create more granular access control to maintain a high-security level in complex environments with specific requirements. For example, if a team requires view-only access to specific app logs and reporting tools, a custom role can be created with these precise permissions, avoiding unnecessary exposure to other resources.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
#2 Automate identity lifecycle management
Identity governance requires managing the entire identity lifecycle, from onboarding to offboarding and handling role or access changes during employment. Manually managing these processes is inefficient, error-prone, and risky—often leading to users retaining resource access long after they need it.
Automating identity lifecycle management ensures that the right people have the right access at the right time—without human error or delay. It greatly enhances security and operational efficiency. Automated workflows can:
- Immediately provision new users with the appropriate accounts, permissions, and resources required.
- Adjust access rights for employees changing roles or departments
- Reliably revoke access during offboarding.
Automation reduces the risk of ex-employees retaining access to sensitive information. It prevents over-provisioning or lingering unnecessary access.
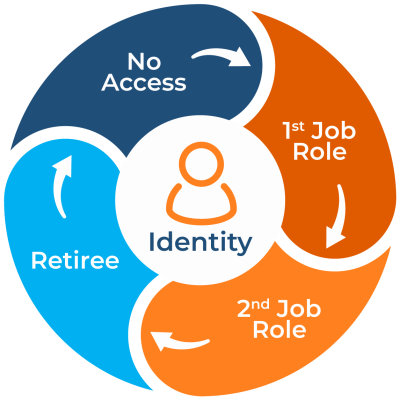
Microsoft Entra ID offers several powerful tools to automate identity lifecycle management:.
- Dynamic groups automatically assign users to specific roles based on attributes like department or job title. For example, a new employee in the Security Operation Centre might automatically be assigned to security-related groups and given access to the relevant applications and resources. As employees move departments, access adjusts dynamically.
- Lifecycle workflows allow administrators to set up automated tasks that trigger based on specific events. For instance, during onboarding, a workflow can be set to send welcome emails with onboarding steps. Similarly, offboarding workflows can trigger notifications, disable access, and reassign open tasks.
For organizations with hybrid environments, additional flexibility in automation is often required. Cayosoft Administrator offers a robust solution that integrates Microsoft Entra ID with on-premises Active Directory and any HR/ERP system, allowing for full provisioning and de-provisioning across environments. IT administrators can use the platform’s automation feature to execute specific actions based on lifecycle events, such as new hires, role changes, or terminations. You can ensure timely, accurate identities and access management across the hybrid cloud.
Automating identity lifecycle management strengthens security and enhances operational efficiency and compliance, and by using Microsoft Entra’s built-in tools alongside third-party solutions when needed, organizations can ensure that their identity and access management processes are timely, accurate, and well-suited for cloud and hybrid environments.
#3 Enforce Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) requires users to provide multiple forms of identity verification, such as a password and a one-time code sent to a mobile device, to access systems and data. It reduces the risk of unauthorized access, even if some credentials are compromised. This additional layer of security is important in defending against attacks like phishing and credential stuffing, which are increasingly common in today’s threat landscape.
- To enforce MFA within Microsoft Entra ID, administrators have several options: Conditional Access Policies allow administrators to implement MFA for specific groups, applications, or conditions. For example, they can require MFA for all users accessing Microsoft 365 applications from outside the corporate network or from unfamiliar locations or devices. To set up:
- Navigate to Microsoft Entra admin center > Protection > Conditional Access
- Create a new policy
- Set the conditions (e.g., cloud apps, locations)
- Under Access controls, select “Grant” and check “Require multi-factor authentication“
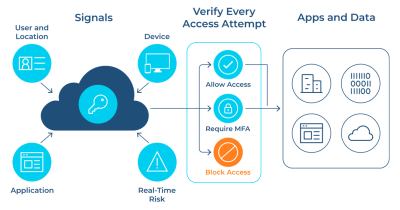
- Security Defaults: For smaller organizations or those new to identity governance, Microsoft Entra Security Defaults offer a straightforward method to enable MFA across all accounts. This default setting enforces basic security measures, such as requiring MFA for all administrators and blocking legacy authentication, which is more susceptible to attacks. Security Defaults provide a solid baseline for organizations seeking essential protection without complex setup. To enable security defaults:
- Sign in to the Microsoft Entra admin center.
- Browse to Identity > Overview > Properties > Manage security defaults.
- Set Security defaults to Enabled.
- Select Save.
As a best practice when enforcing MFA, it is advisable to:
- Implement MFA first on accounts with administrative privileges and access to sensitive data, as these are most likely to be targeted by attackers.
- Educate users about MFA-related attacks, such as MFA fatigue attacks, where attackers repeatedly prompt users with MFA requests in the hope they will accidentally approve one. Training can help users recognize and report suspicious activity.
- Regularly review Microsoft Entra ID logs and reports to identify any issues or anomalies.
Microsoft Entra ID’s MFA options—from Security Defaults to Conditional Access—allow organizations to deploy MFA in a manner that meets their specific security and usability requirements, and by implementing these strategies, organizations can improve their security posture. Remember, while MFA adds an extra step to the login process, the security benefits far outweigh any minor inconvenience.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
#4 Use Privileged Identity Management (PIM)
Privileged Identity Management (PIM) is a service in Microsoft Entra ID that enables IT admins to manage, secure, and monitor access to highly sensitive resources. One of its most powerful features is Just-in-Time (JIT) access which ensures that elevated permissions are granted only when needed and for a limited time. This minimizes the risk of compromised privileged accounts by reducing the duration during which anyone can hold elevated access to those accounts. It prevents misuse and accidental exposure of critical systems.
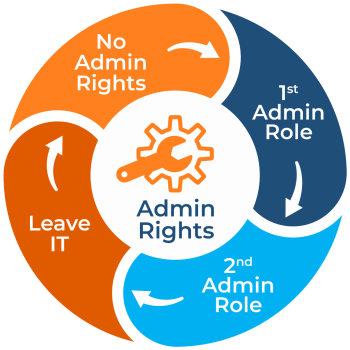
In addition to JIT, some other features of PIM includes:
- Time-Bound Role Activation: Admins can set specific time limits for role activations, such as 2 hours, 8 hours, or custom durations.
- Approval Workflows: Admins can configure multi-stage approval processes for sensitive roles.
- Audit Logging: PIM provides comprehensive logs of all role activations and changes for compliance and security analysis.
- Alerts and Notifications: Admins can set up alerts for suspicious activities or critical role activations.
JIT access operates on the principle that administrative or privileged access should not be a permanent status but rather something that is granted temporarily when a task requires it. By requiring users to request elevated permissions only when necessary, JIT access reduces the attack surface associated with constant administrative rights. It limits the time window when an attacker could exploit high-level credentials, thereby improving security.
Implementing JIT access through Microsoft Entra’s Privileged Identity Management (PIM) involves a few straightforward steps.
- Go to Identity Governance > Privileged Identity Management > Microsoft Entra roles in the Microsoft Entra Admin Center.
- Within PIM, choose the role you want to configure for JIT access. This can include Global Administrator, Security Administrator, or any other privileged role within your organization.
- Enable “eligible” role assignments rather than permanent ones for the selected role. Eligible users can request access to the role when necessary, but they won’t have elevated privileges by default.
- Set parameters such as the duration of access (e.g., 1 hour, 4 hours) and whether approvals are required before granting access.
PIM allows you to define approval workflows, ensuring that elevated permissions are granted only after proper authorization. You can also enforce MFA during the request process for additional security.
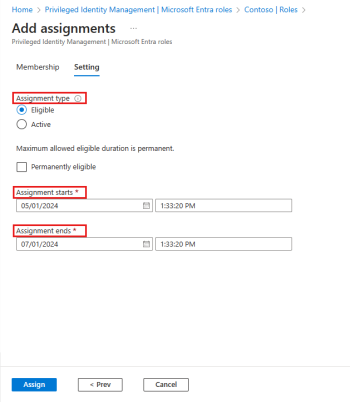
Implementing PIM provides several benefits in securing your organization’s resources, including:
- Reduced Attack Surface: By limiting the time users have elevated access, PIM decreases the window of opportunity for attackers to exploit privileged credentials.
- Enhanced Control and Accountability: Approval workflows and MFA for privileged access requests ensure that only authorized users gain elevated access, creating a trail of accountability.
- Prevention of Privilege Creep: As users change roles or their access needs shift, scheduled access reviews and the eligible assignment model prevent the accumulation of unnecessary privileges over time.
Once configured, users needing temporary access can request elevation through PIM. Administrators or predefined approvers can review and approve the request, activating the elevated role for the specified time window. This model ensures that privileged access is available on a strictly need-to-have basis, reducing the risks associated with over-provisioned accounts and giving administrators full control over critical resources.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
#5 Actively monitor and audit for suspicious activities
Implementing all the previously highlighted best practices without continuous monitoring and auditing is counter-productive. Proactive monitoring helps organizations detect and respond to suspicious activities before they escalate into security incidents. In Microsoft Entra ID, continuous monitoring and comprehensive audit logging ensure that identity-related events—such as unauthorized access attempts, privilege escalation, or abnormal user behavior—are quickly identified and mitigated.
Microsoft Entra ID audit logs provide a detailed record of all actions performed within the environment. You can combine them with sign-in and provisioning logs to get a comprehensive report on every logged event, including user sign-ins, administrative actions, and changes to roles or group memberships. These logs are invaluable for operational insight and compliance reporting, as they offer visibility into who did what, when, and where.
In the Microsoft Entra Admin Center, navigate to Monitoring & health. Here, you’ll find Audit, Sign-in, and Provisioning logs, where you can also find detailed records of every administrative action performed within your tenant, including user activity, application management, and directory changes.
The interface allows you to filter by specific criteria, such as Date Range, Category (e.g., User Management, Group Management), or Activity (e.g., Sign-in, Role Assignment). These filters help administrators quickly find relevant information for specific incidents or activities.
You can also create alerts for specific activities that may indicate potential security risks. For example, you might want to be notified whenever a privileged role is assigned or if an unusually high number of failed sign-in attempts occur. These alerts can be sent to security teams via email or integrated with security information and event management (SIEM) solutions for real-time monitoring.
For even more advanced auditing and monitoring, tools like Cayosoft Guardian can be integrated with Microsoft Entra ID to enhance visibility and automate threat detection. It provides real-time visibility into changes across hybrid environments, including on-premises Active Directory and Microsoft Entra ID. You can capture activities such as user creations, deletions, and modifications and also instantly roll back unwanted changes.

Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Microsoft Entra ID governance provides a robust framework for managing identities and access across complex environments, but its effectiveness relies on proper implementation with best practices. The Cayosoft product suite enhances and supports your Microsoft Entra implementation with additional automation and a user-friendly admin interface.
However, remember that robust identity governance is not just about implementing tools—it’s about fostering a culture of security awareness and continuous improvement.
To see how Cayosoft can help you with Microsoft Entra ID governance, request a personalized demo here.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content