Home » Implementing Zero Trust Security with Microsoft Entra » Configuring Microsoft Entra Connect Sync for Hybrid Identity
Configuring Microsoft Entra Connect Sync for Hybrid Identity
Learn about Microsoft Entra Connect Sync and its role in synchronizing identities between on-premises Active Directory and Microsoft Entra ID for seamless hybrid identity management and access control.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Active Directory (AD) is a staple of on-premises identity management in many enterprises. As organizations shift to the cloud, they need identities to be consistent across on-premises networks and cloud environments. Microsoft Entra Connect and its synchronization service, Microsoft Entra Connect Sync, facilitate this hybrid identity requirement.
Microsoft Entra Connect Sync helps integrate on-premises identities with Microsoft Entra ID so that users can use the same identity and password for both on-premises and cloud workloads.
This article will help you understand how to use Microsoft Entra Connect Sync to synchronize identities between on-premises AD and Microsoft Entra ID (formerly Azure AD). We will cover key concepts such as the architecture, features, and authentication methods it supports. Following this, we will learn about different installation methods. This article will also discuss Microsoft Entra Connect Health along with a quick introduction to Microsoft Entra Cloud Sync, the future replacement of Connect Sync.
Summary of key Microsoft Entra Connect Sync concepts
The table below summarizes the key Microsoft Entra Connect Sync concepts and terms this article will explore in detail.
Concept | Description |
Microsoft Entra Connect | A tool from the Microsoft Entra ID product line that enables hybrid identity implementation and access management across cloud and on-premises environments. |
Microsoft Entra Connect Sync | The core component of Microsoft Entra Connect that is responsible for synchronizing identities, groups, etc., between on-premises Active Directory with Microsoft Entra ID. |
Microsoft Entra Connect Health | An add-on monitoring tool that helps with troubleshooting and provides insights and alerts on the health, performance, and synchronization status. |
Microsoft Entra Cloud Sync | A lightweight, cloud-based alternative to Microsoft Entra Connect Sync, which provides similar functionality but is managed entirely from the cloud. |
Azure Active Directory or Azure AD | A monitoring tool that provides insights into the health and performance of your identity infrastructure. It helps you troubleshoot issues and ensure smooth synchronization between your on-premises and cloud environments. |
Object | A general term used to represent users, groups, devices, and other entities within an identity system. |
Microsoft Entra Connect
Microsoft Entra Connect is an application that caters to an organization’s hybrid identity requirements. It primarily enables synchronizing on-premises identities from a directory such as Active Directory with cloud services like Microsoft Azure and Microsoft 365 so users can use a single identity for apps in the cloud and on-premises. This simplifies identity management and access control, reduces administrative efforts for managing identities across multiple environments, provides seamless access to resources anywhere, and improves the overall security posture of the identity layer.
No separate license is required to use Microsoft Entra Connect.
Features
The following is a list of features Microsoft Entra Connect supports:
- It can synchronize objects, attributes, and relationships.
- It supports multiple synchronization modes, such as full, incremental, delta, and filtered, where you can choose to synchronize specific objects or attributes.
- Microsoft Entra Connect Health uses a lightweight monitoring agent to collect data, providing monitoring and troubleshooting capabilities.
- It supports staging mode to test changes before finally applying them.
- You can bulk import users using a CSV file.
- You can also import/export Microsoft Entra Connect configuration data.
- Microsoft Entra Connect also supports custom synchronization rules.
- It also supports Hybrid join, enabling devices to be joined to both on-premises Active Directory and Microsoft Entra ID.
Simplify Hybrid Identity Management with Cayosoft Administrator
Automate and secure your hybrid identity management with Cayosoft Administrator. Ensure seamless synchronization between on-prem AD and Microsoft Entra ID while enforcing security policies.
Microsoft Entra Connect Sync
Microsoft Entra Connect Sync is the engine and the on-premises component responsible for synchronizing on-prem Active Directory identities and their attributes to Microsoft Entra ID (previously called Azure Active Directory or Azure AD).
Another component of the hybrid identity sync service is the Microsoft Entra Connect Sync service, which is the service on the Microsoft Entra ID side. [For clarity, the on-premises component can be called Microsoft Entra Connect Sync engine, and the Entra ID component can be called Microsoft Entra Connect Sync service]
The latest release of the Microsoft Entra Connect is V2.
Please note that in many cases, the files, services, and other components may still say Azure AD; for example, the installation file is called AzureADConnect.msi.
Features
The following table summarizes a list of features that Microsoft Entra Connect Sync supports.
| Feature | Description |
|---|---|
| Password Hash Sync | Synchronizes the hash of the passwords from an on-premises Active Directory server to Microsoft Entra ID for password-based authentication. |
| Password Writeback | Allows password changes made in Microsoft Entra ID to be synchronized back to on-prem AD. (The password hash is synchronized) |
| Pass-through Authentication | Enables you to use on-premises AD to validate passwords. |
| DeviceWriteback | Syncs device information from Microsoft Entra ID to on-premises Active Directory when enabled. |
| UserWriteback | Syncs new users and user modifications made in Entra ID back to on-prem AD. |
| UnifiedGroupWriteback | Synchronizes unified group information from Microsoft Entra ID to on-premises AD. |
| DirectoryExtensions | Allows custom attributes to be added to an object and then synced to Microsoft Entra ID. |
Architecture
The diagram below describes the components of Microsoft Entra Connect Sync.
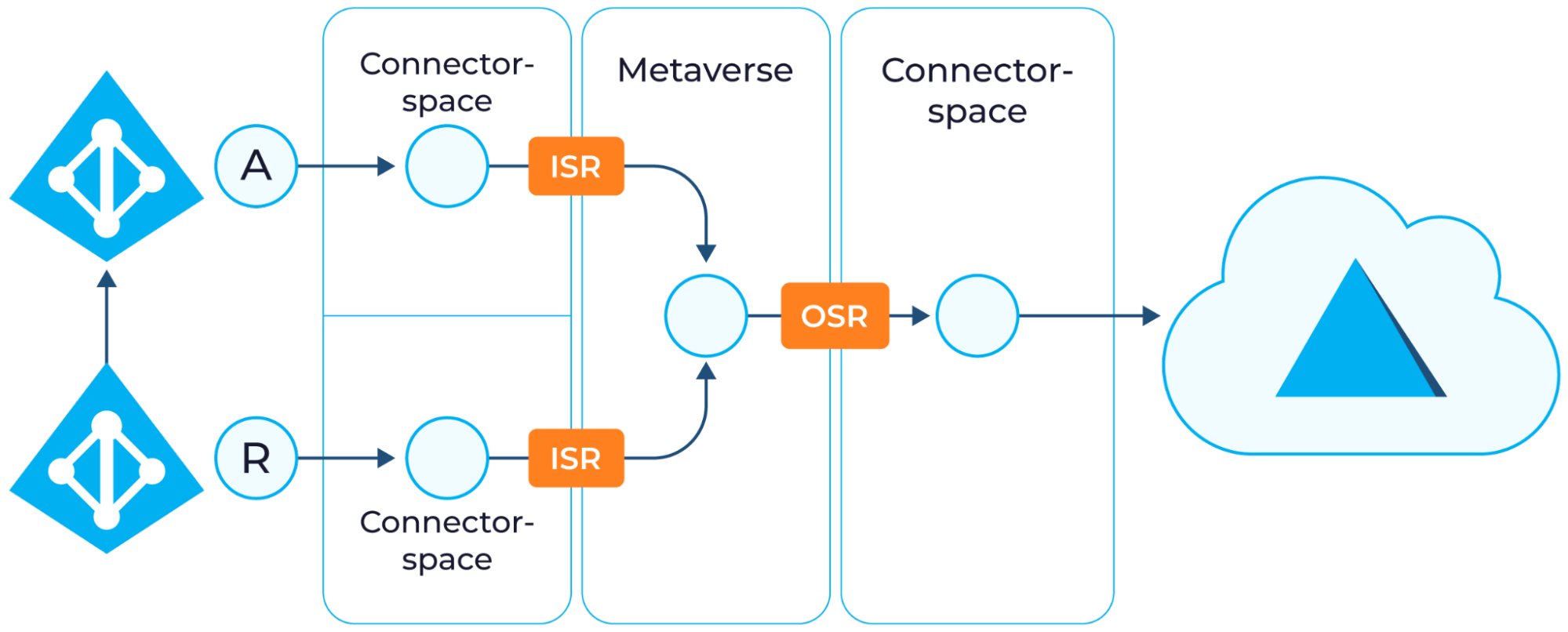
The Microsoft Entra Connect Sync architecture includes several components, each with a specific function:
- Connector: A connector is used for communication with a data source, such as an on-premises directory like Active Directory or Microsoft Entra ID. The component performs the import/export of changes to the data source. It is agentless and usually considered part of the Connector Space.
- Connector space: This component represents the data or objects from each connected system.
- Metaverse: A metaverse represents a unified view of all identities from all connected spaces. Objects in the metaverse are only contributed through attribute flow and cannot be edited in the metaverse.
- Attribute flow: An Attribute Flow defines how data is synchronized, and this is done using Synchronization Rules.
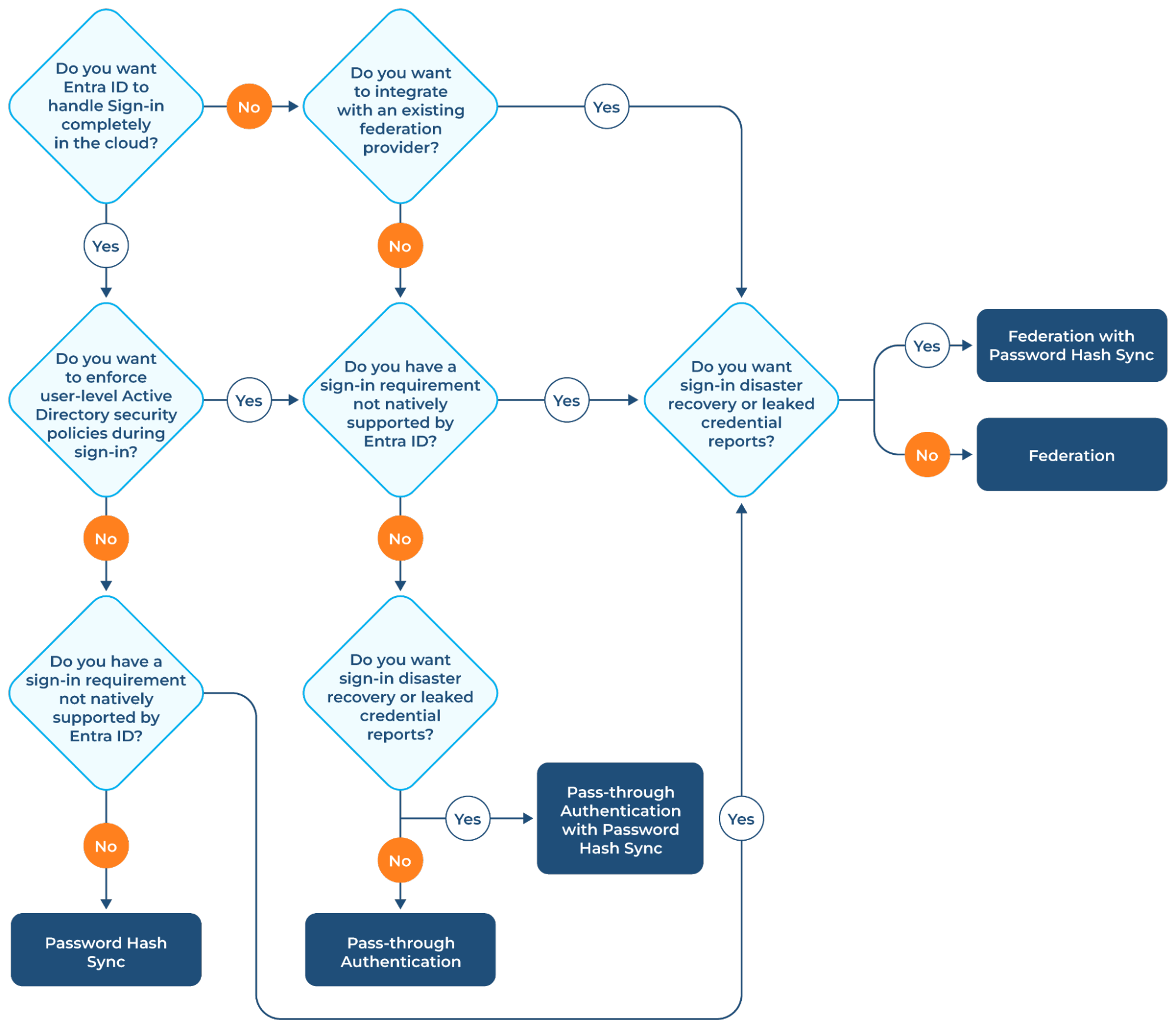
Authentication methods
You can choose between a cloud or federated authentication method when setting up Microsoft Entra Connect. In the cloud authentication method, Microsoft Entra ID handles the sign-in process. This method has two options you can choose from:
- Password hash synchronization: This option synchronizes the password from the on-premises active directory to Microsoft Entra ID, enabling users to use the same password. In other words, password validation happens on the cloud.
- Pass-through authentication: This option uses your on-premises AD to validate the password.
The federated authentication method validates the password using on-premises Active Directory Federation Services (ADFS).
The following decision tree provides a helpful way to choose an authentication method.
How to install Microsoft Entra Connect
To use Connect Sync for identity synchronization, one must install Microsoft Entra Connect. Hence, installing Entra Connect is covered here.
Prerequisites
- A Microsoft Entra tenant. You should have an Entra ID tenant if you already have an Azure or Microsoft 365 Office account. If this is your first time beginning, you can create a trial Azure account to get a tenant.
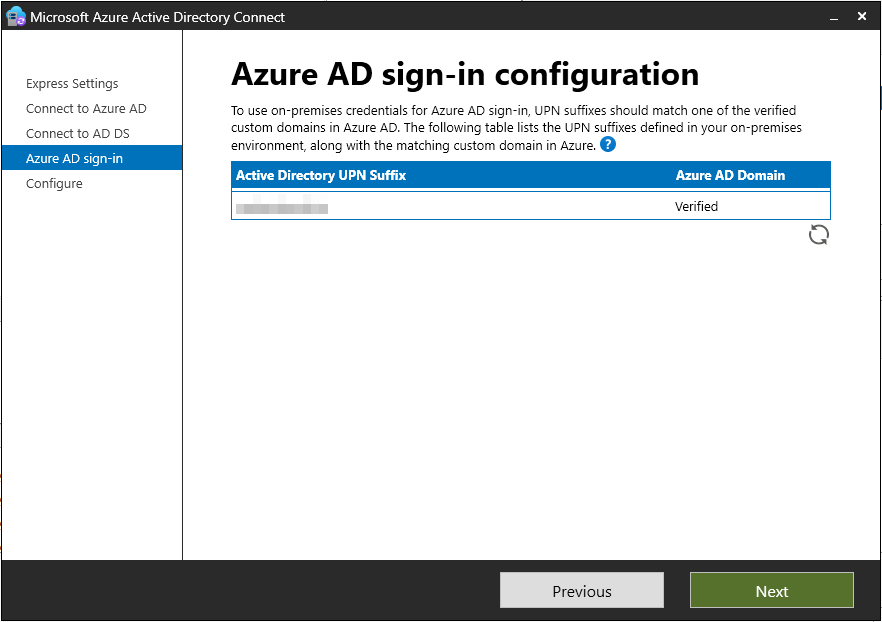
- You must associate a verified domain with the tenant.
- The sync service requires a Windows service account, and a set of credentials is automatically created by default during the installation. However, if you want to use a custom service account, you must create one and use it during the installation. Changing the service account after installation isn’t supported and causes synchronization failure, among other issues.
- You will also need an account with various permission levels during installation and later for synchronizing.
| Step | Permissions required |
|---|---|
| For installation |
|
| For synchronization |
|
- Microsoft SQL Server for the database. The express installation method (discussed below) installs a SQL Server 2019 Express LocalDB by default. However, it is recommended that you use a dedicated SQL installation.
- Microsoft Entra Connect version 1.2.65.0 and later only supports TLS 1.2 for communications with Azure. Hence, you must enforce it on the server where it will be installed.
Installation methods
When installing Microsoft Entra Connect, you can choose from two installation methods: Express and Custom. The selection of an installation method depends on many factors, the most important being the authentication method, the number of objects for synchronization, and the number of forests.
Installing Microsoft Entra Connect
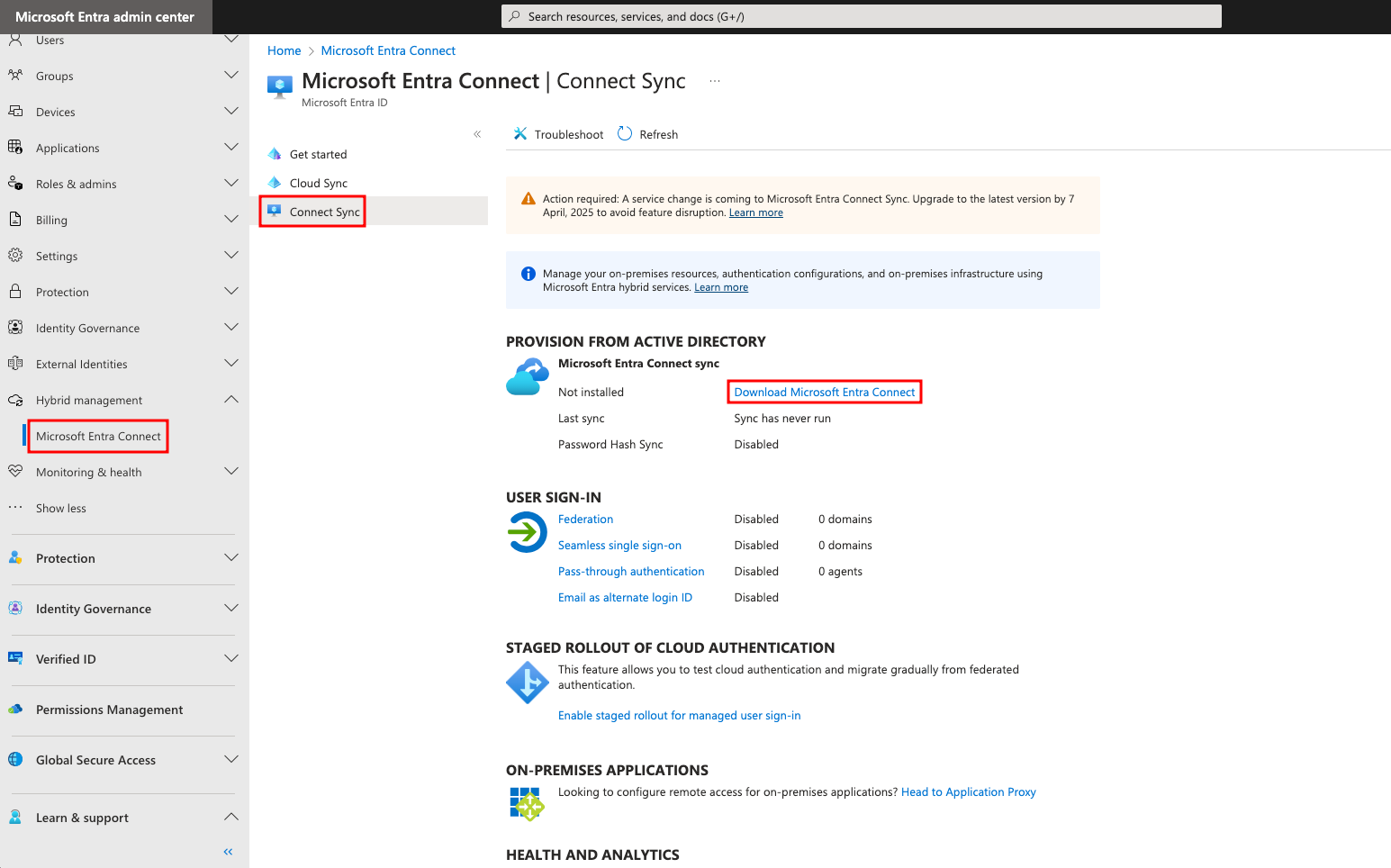
The first step to installing the Microsoft Entra Connect Sync tool is downloading the installation file. It can be downloaded from the Microsoft Entra Connect section under Hybrid management in the Microsoft Entra admin center.
Click Download Microsoft Entra Connect to navigate to the download page and click Download again next to the language of choice. The filename is AzureADConnect.msi.
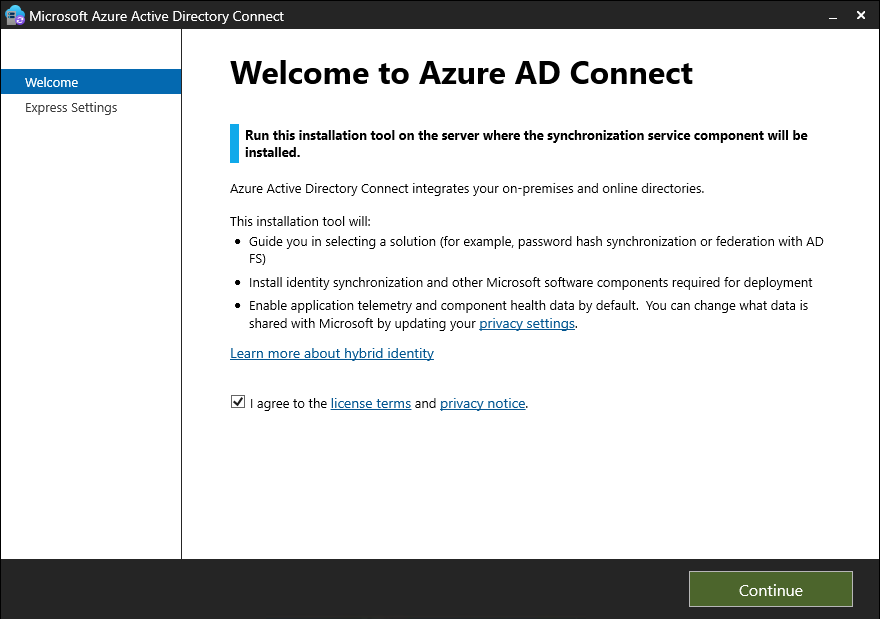
After downloading, launch the downloaded MSI file. On the welcome screen, agree to the terms and conditions and select Continue.
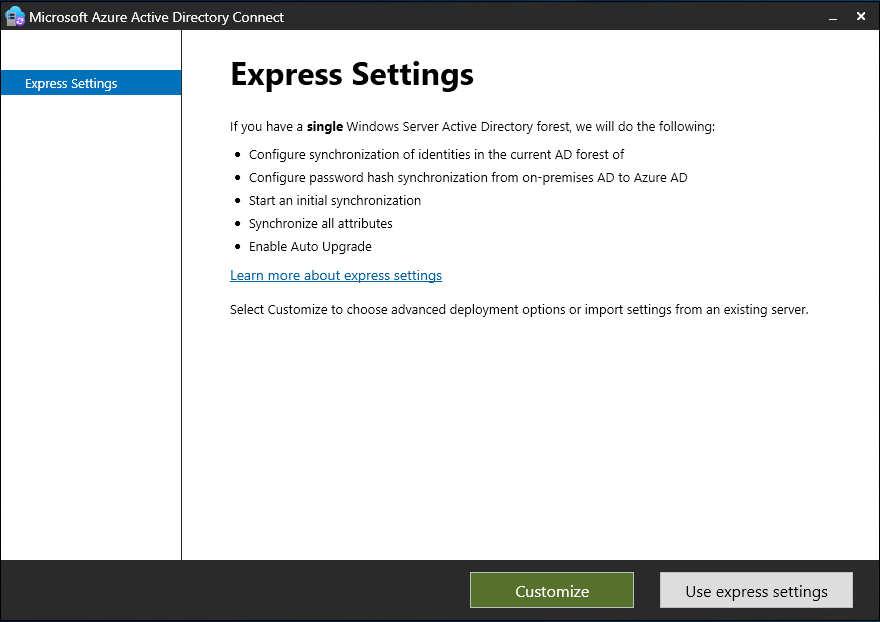
In the next step, select the installation method, i.e., express or custom.
The express installation is ideal for a single forest structure and sets up password hash synchronization from on-prem AD to Microsoft Entra ID. It synchronizes all attributes by default and starts an initial synchronization. Auto-upgrade of the tool is also enabled by default.
To customize the installation, click the Customize button instead of the Use express settings button.
Using this option, you can customize the installation location, choose to use an existing SQL server, specify a custom service account, import synchronization settings, and more.
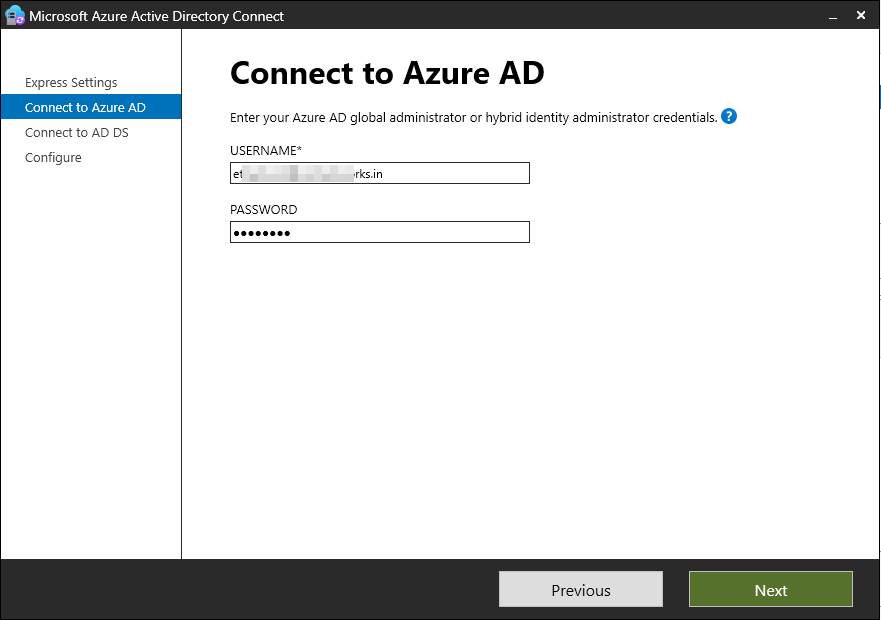
In the next step, you have to provide the credentials of a Hybrid Identity Administrator. You can also use a Global Administrator account.
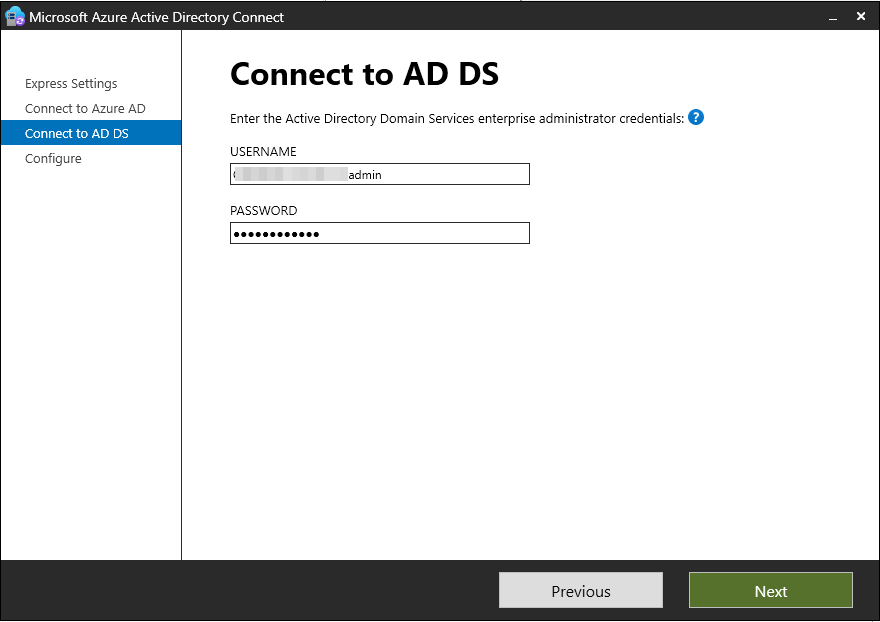
Following this, you will also need the credentials of an Enterprise Administrator for the on-premises AD.
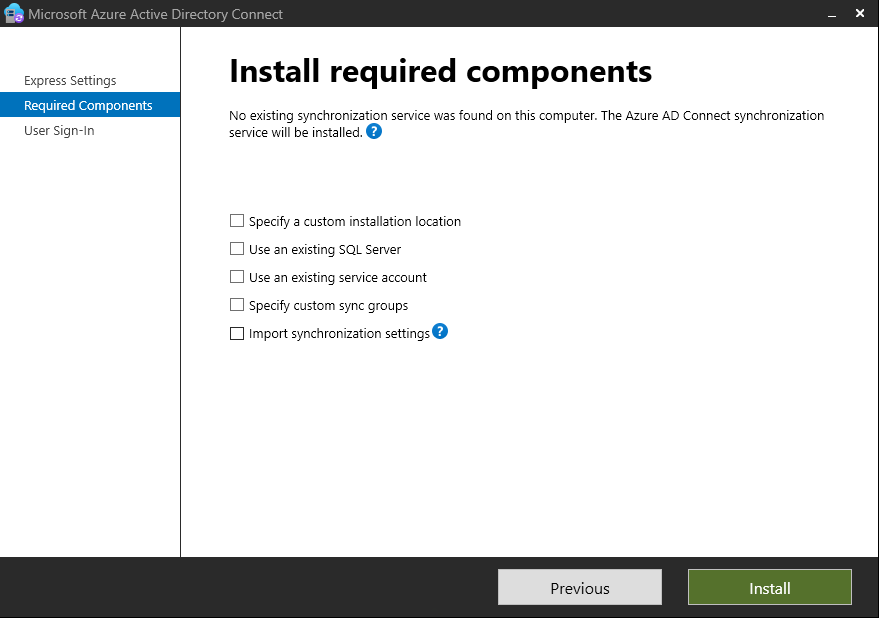
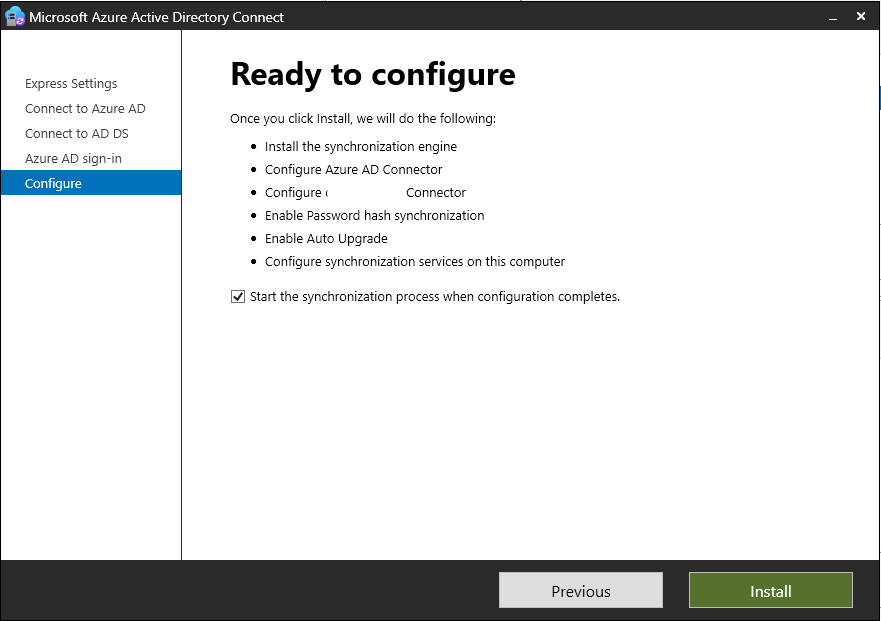
On the final screen, click on Install to start the installation process. If you wish to make more customizations later, you may uncheck synchronization after configuration here before clicking install.
This will begin the Microsoft Entra Connect installation process and its related components. After the successful installation and configuration, you should see a “Configuration complete” message. Click Exit to close the wizard.
Master Active Directory Management Best Practices
Improve your AD management strategy with our comprehensive guide on security, automation, and compliance.
Microsoft Entra Connect Health
Microsoft Entra Connect Health is a monitoring agent for on-premises identity services such as Active Directory Federation Server (ADFS) that provides insights, alerts, and performance and usage metrics for maintaining a reliable hybrid identity infrastructure. It has a dedicated portal where all this information is available in a unified view.
Microsoft Entra Connect Health can be used to monitor one or more of the following services:
- Active Directory Domain Service
- Active Directory Federation Service
- Microsoft Entra Connect Sync Service
- Microsoft Identity Manager Service
It collects data using a health agent installed on the on-premises identity servers. You can install them on as many identity servers as you like.
You need a Microsoft Entra ID P1 license to use this feature.
Benefits of Microsoft Entra Connect Health
Microsoft Entra Connect Health offers organizations these identity management benefits:
- A single dashboard for all services.
- You can view usage metrics across all supported services, including on-premises ones such as AD FS, AD DS, etc.
- You can receive email alerts on various data, such as Sync errors.
- Provide Microsoft team access to data during troubleshooting to streamline support.
How to access Microsoft Entra Connect Health
You can access the Microsoft Entra Connect Health portal from the Microsoft Entra Connect page in the Entra admin center.
You can download the right health agent for your identity service from the quick start page of Microsoft Entra Connect Health.
Discover Top 5 AD Sync Best Practices
Avoid common pitfalls and optimize AD synchronization with these best practices.
Microsoft Entra Cloud Sync
Microsoft Entra Cloud Sync is a newer cloud-based synchronization option that syncs objects from on-premises to Microsoft Entra ID. This method stores all configuration data using Microsoft Online Services and Microsoft Entra ID. It uses a lightweight provisioning agent deployed on-premises to bridge the AD and Entra ID. Many such provisioning agents can be used for high availability. As of this writing, it only supports users, groups, and contacts.
Cloud Sync is considered the successor to Microsoft Entra Connect Sync, and all future feature improvements are expected to be done here. You can also use Microsoft Entra Connect Sync and Cloud Sync together.
Microsoft Entra Cloud Sync vs Microsoft Entra Connect Sync
The table below summarizes the differences between Microsoft Entra Connect Sync and Cloud Sync.
| Attribute | Microsoft Entra Connect Sync | Microsoft Entra Cloud Sync |
|---|---|---|
| Sync cycle time | 30-minute default sync cycle. | 2-minute default sync cycle. |
| Pass-through connection support | Supported | Not supported |
| Device synchronization support | Supported | Not supported |
| Multi-forest environment support | Supported | Not supported |
| Resource consumption | High. Consumes considerable resources depending on the objects managed and the need for a dedicated server. | Low. Has a minimally invasive deployment and fewer resource requirements. |
| Customization | High. Highly customizable with attribute flow, filtering, transformation, etc. | Low. Offers less customization options. |
Eight tips for effective Microsoft Entra Connect and Microsoft Entra Connect Sync implementation
The eight tips below can help organizations improve performance, security, and identity management when implementing a hybrid solution using Microsoft Entra Connect and Microsoft Entra Connect Sync.
- Scale resource requirements appropriately. Ensure the hardware and resource requirements meet the number of objects the Microsoft Entra Connect server will manage. For example, the minimum CPU and Memory required for up to 50000 objects is 1.6 GHz and 6 GB, respectively. As the number of objects increases, you will mostly need more memory.
- Address on-prem identity issues with IdFix. You should identify and fix issues with on-premises identities, such as duplicate identities, formatting problems, etc. You can use IdFix for this.
- Avoid read-only domain controllers. Do not use a read-only domain controller for Microsoft Entra Connect.
- Don’t use NETBIOS names with Entra Connect. NETBIOS names aren’t supported either.
- Turn on the AD recycle bin. Enabling the Active Directory recycle bin is also recommended.
- Harden the server running Entra Connect. Secure access to the server running the Microsoft Entra Connect tool and the SQL server if you use a separate one through hardening and proper access control methods.
- Spread out large-scale user onboarding. Use a separate time window or a spread-out approach when onboarding many users, as Microsoft Entra ID uses throttling to reduce Denial of Service (DoS) attacks.
- Be mindful of technology compatibility. Refer to the list of supported topologies to ensure you are not using an unsupported topology for synchronization.
To learn more about how to effectively deploy and maintain Microsoft Entra Connect and Microsoft Entra Connect Sync, we recommend reading the official Microsoft Entra Connect: Prerequisites and hardware – Microsoft Entra ID | Microsoft Learn and Factors influencing the performance of Microsoft Entra Connect – Microsoft Entra ID | Microsoft Learn documentation.
Cayosoft for hybrid identity management
Using native Microsoft tools alone can make hybrid identity management complex and challenging to scale. The right third-party tooling can empower organizations to implement secure hybrid identity solutions without unnecessary complexity.
For example, Cayosoft’s hybrid identity management software, Caysoft Administrator, can simplify identity and access management across on-premises and cloud identity services by providing a unified interface for managing tasks, groups, policies, licenses, etc., with a zero-trust approach using granular permissions management. The unified interface also includes reporting and auditing.
Secure & Automate Hybrid Identity Management
Managing hybrid Active Directory environments can be complex — Cayosoft simplifies it. Explore how our solutions help to secure, control, and automate hybrid AD administration.
Conclusion
Microsoft Entra Connect Sync is essential for organizations that want to implement a hybrid identity infrastructure using on-premises Active Directory and Microsoft Entra ID. It acts as a bridge, synchronizing user, group, and password information between these two environments. You can choose between multiple synchronization options discussed in this article and customize it as needed. The key to effective hybrid identity management is combining the right strategy and practices with the right set of native Microsoft capabilities and third-party identity management solutions.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content