Home » Implementing Zero Trust Security with Microsoft Entra
Implementing Zero Trust Security with Microsoft Entra
Learn about Microsoft Entra, a comprehensive identity and access management solution with a suite of products and a zero-trust security approach.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
In today’s digital landscape, identity is essential for accessing applications and data. Cloud services, bring-your-own-devices, and mobile applications all rely on some form of identity to authenticate and receive authorization. It is essential to have a comprehensive identity and access management (IAM) solution that implements zero-trust security across the digital landscape.
Microsoft Entra provides a suite of products that enable you to create a trust fabric for end-to-end access management. Together, these products can provide zero-trust access to internal and external resources, including multi-cloud patterns.
In this article, we explore the technicalities of Microsoft Entra, its product offerings, and what each product provides. We focus on Microsoft Entra ID—the core service—discussing Entra ID’s architecture and how it works and showing you how to get started.
Summary of key Microsoft Entra concepts
This article will cover many concepts related to Microsoft Entra and Entra ID. The following table describes key terms and products.
| Concept | Description |
|---|---|
| Microsoft Entra | The umbrella name for a set of Microsoft identity and network access management products. |
| License | The purchasing model that enables Microsoft Entra products, features and add-ons. Popular license options are P1, P2, and Suite. |
| Microsoft Entra Suite | A set of add-on products that provides identity protection, governance, verification, and solutions for secure network access for both private and Internet networks. |
| Microsoft Entra ID | The primary service of Microsoft Entra that provides identity, authentication, policy, and protection capabilities to users, devices, apps, and more. |
| Zero trust | A security principle that says to never trust an identity by default and always verify it. |
| Tenant | A unique instance of Microsoft Entra ID representing an organization and its users, groups, apps, etc. |
| Global Administrator | A built-in role in Microsoft Entra ID that has full ownership over a tenant and its resources. |
| Microsoft Entra Admin Center | The dedicated portal for unified administration of Microsoft Entra and its products. |
| Conditional Access | A feature of Microsoft Entra that allows you to control access to resources based on conditions such as location, device, user/group, role, etc. and to prompt for MFA. |
| Multifactor Authentication | An authentication method where a second or third form of identification is requested along with the primary before allowing access. |
| Identity Secure Score | A score that shows how well you fare with standard security recommendations. |
| Microsoft Copilot for Security | A generative-AI-powered solution that provides security professionals faster and better security responses. |
Microsoft Entra
Microsoft Entra is an umbrella name for a suite of products and add-ons related to identity, access management, permissions management, network access management, and more. Microsoft wants to use Entra as the trust fabric to implement zero-trust security across a company’s digital space. Zero trust is a security model that follows a never trust and always verify principle: It advocates that no identity—whether human, app or device—be trusted by default. Each entity requesting access to resources or data, internal or external, must be verified at all times.
Microsoft Entra is part of Microsoft’s broader security portfolio, which includes Microsoft Purview, Microsoft Defender, Microsoft Sentinel, and other products.
Background
Microsoft Entra was announced as a product family that would include all of Microsoft’s existing and new identity and access-related products, including the most popular: Azure Active Directory (or Azure AD). Later, Azure AD and related products were renamed to reflect the Microsoft Entra family; for example, Azure AD was renamed to Microsoft Entra ID.
Microsoft Entra products
While we will cover Microsoft Entra ID in more detail in this article and other Microsoft Entra products in dedicated articles, here’s a quick table describing what each product in the Microsoft Entra family does.
Product | Description |
Microsoft Entra ID | Provides core identity and access management capabilities, including authentication, authorization, and user management |
Microsoft Entra ID Governance | Automates identity lifecycle and access governance to ensure that the right users have the right access to the right resources |
Microsoft Entra ID Protection | Detects and mitigates identity-based risks by identifying suspicious activities and enforcing security policies |
Microsoft Entra Verified ID | Enables users to securely manage and verify digital credentials, improving trust and privacy in online interactions |
Microsoft Entra Private Access | Provides secure access to on-premises and cloud applications without the need for a traditional VPN |
Microsoft Entra Internet Access | Secures access to internet resources and provides granular control over web traffic |
Microsoft Entra External ID | Manages and secures access for external users, such as partners and customers, to internal applications |
Microsoft Entra Permissions Management | Provides comprehensive visibility and control over permissions across multi-cloud environments (Azure, AWS, GCP) |
Microsoft Entra Workload ID | Offers identity and access management solutions specifically designed for workloads, such as applications and services |
Licensing
Microsoft Entra licenses are available in various combinations, depending on feature requirements.
At a high level, it has three paid licensing options: P1, P2, and Suite. It also has a Free license included by default with Microsoft Azure and Microsoft 365 subscriptions. Certain Microsoft 365 subscriptions include the P1 or P2 variant. For example, Microsoft Entra ID P1 is included in Microsoft 365 E3 and Microsoft 365 Business Premium subscriptions, and Microsoft Entra ID P2 is included in Microsoft 365 E5 subscriptions.
The following table shows the different paid license options and the add-on products they include.
| Product | Microsoft Entra ID P1 | Microsoft Entra ID P2 | Microsoft Entra Suite |
| Microsoft Entra ID | Yes | Yes | No (You must have a Microsoft Entra ID P1 or P2) |
| Microsoft Entra ID Governance | Yes, with selected features | Yes, with selected features | Yes |
| Microsoft Entra Verified ID | Yes, with selected features | Yes, with selected features | Yes |
| Microsoft Entra ID Protection | Yes, with selected features | Yes | Yes |
| Microsoft Entra Internet Access | No | No | Yes |
| Microsoft Entra Private Access | No | No | Yes |
Microsoft Entra Suite products—such as Microsoft Entra Internet Access, Microsoft Entra Private Access, Microsoft Entra ID Governance, and Microsoft Entra Verified ID—are available for purchase as standalone products. Other Microsoft Entra products not part of the Entra Suite—such as Microsoft Entra External ID, Microsoft Entra Permissions Management, Microsoft Entra Workload ID, and Microsoft Entra Domain Services—must be purchased separately as add-ons.
For a complete list of detailed features based on the license, visit the Microsoft Entra pricing page at https://www.microsoft.com/security/business/microsoft-entra-pricing.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Microsoft Entra ID
Microsoft Entra ID, earlier called Azure Active Directory (Azure AD), provides a comprehensive package of identity and access management capabilities that enable secure access to Azure services, applications, devices, and data. Before we dive deeper into the architecture, features, and how it works, let’s first understand some common concepts.
- Identity: An identifier with a set of attributes that may represent a user, application, or device. For example, an email address is a common online identity. In the context of this article, this identity is used to authenticate and authorize access to resources.
- Authentication: The process of asking for credentials such as an email address (or user name) and a password to validate the identity. Other forms of authentication could be fingerprint, face ID, one-time passcode (OTP), etc.
- Authorization: The process of validating that the authenticated identity has permission to access a resource and perform actions on it.
- Identity and Access Management (IAM): A process that ensures that the right identities get access to the right resources at the right time. IAM involves identity management, such as creating and storing identities, authenticating and authorizing identities, defining and validating access controls, providing federation if needed, reporting, and monitoring.
- Standards: Across the industry, a few common authentication and authorization standards are used for IAM. The most popular ones are OAuth 2.0 for authorization and OpenID Connect (OIDC) for authentication. Security Assertion Markup Language (SAML) is also used for authentication and authorization.
- User: A user usually represents a human in Microsoft Entra.
- Group: A group is a collection of users with similar access and permission requirements.
- Role: A role is a collection of permissions that allow certain actions on resources, such as reading and writing to an Azure SQL Database.
- Tenant: A tenant is an instance of Microsoft Entra ID primarily representing an organization.
Architecture
Microsoft Entra ID uses a partitioned architecture that acts as independent scale units, providing performance, scalability, high availability, and failover capabilities.
The data tier consists of a primary replica for writes and one or more geographically distributed secondary replicas for reads. A successful write is returned only when at least one secondary replica in a different data center has a copy of the data, ensuring data durability. Data is then asynchronously copied to all other replicas, following an eventual consistency model.
The secondary replicas provide read scalability, and a secondary replica in a data center close to the originating request serves the read request, which also helps improve performance.
Since data is replicated across multiple independent data centers that do not share resources to avoid a single point of failure, the service is more highly available, so there is no need for downtime during maintenance activities. There are also replicas in the same data center.
Monitoring ensures that in case of a failure, the writes are shifted to a different replica, making it the primary replica. Read availability isn’t affected during this failover, but you may be unable to write for 1-2 minutes.
Features
Apart from its fundamental identity and access management capabilities, Microsoft Entra ID provides many additional features that depend on the license chosen. Here are some of the most popular features:
- Conditional Access is a policy engine that helps you automatically enforce access conditions based on real-time signals such as location, risk level, user type, etc.
- Application and device management features enable you to manage your cloud and on-premises applications and how devices can access these applications and data. Capabilities such as application proxy and single sign-on are used for application management.
- Privileged identity management is another important feature that helps limit the number of people who have privileged access and the amount of time they have it for by providing just-in-time privileged access to resources.
- Single sign-on (SSO) allows users to use one credential to access applications both on-premises and in the cloud.
For a complete list of all features and capabilities, visit the Microsoft Entra ID overview page here.
How Microsoft Entra ID works
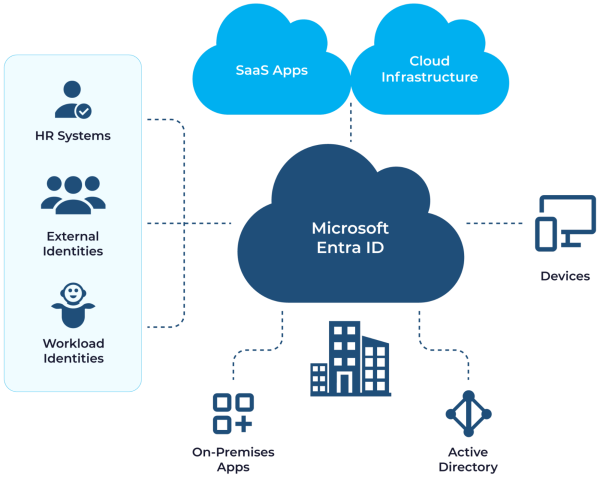
Microsoft Entra ID integrates with both on-premises and cloud services, providing improved security, unified management, and a productive user experience.
The following image illustrates how various identities (internal and external), devices, and services, both on-premises and in the cloud, can use Microsoft Entra ID for identity and access management.
Built-in Entra ID roles
An essential concept in Microsoft Entra ID are built-in roles and their use. Here are some of them:
- Global Administrator: This role allows a user full control over the Microsoft Entra ID tenant and services that use the tenant’s identities. It is a privileged role, so one must be careful about who has it.
- Billing Administrator: This role allows a user to perform most billing-related tasks, such as adding, modifying, or deleting payment information.
- Security Administrator: This is also a privileged role that allows a user to perform security-related tasks across Microsoft’s security products, such as Defender, Purview, Entra ID protection, and more. For example, a user with this role can create and manage Conditional Access policies.
For a complete list of all built-in roles, refer to the link below:
https://learn.microsoft.com/en-us/entra/identity/role-based-access-control/permissions-reference
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Getting Started with Microsoft Entra ID
Microsoft services such as Microsoft 365 and Microsoft Azure use Microsoft Entra ID for sign-in. If you already use one of them, you already use Microsoft Entra ID. It can be accessed from the Azure portal or through its dedicated portal called the Microsoft Entra admin center.
The following section of the article lists the steps to getting started with Microsoft Entra ID – the primary product of the Microsoft Entra family.
Accessing Microsoft Entra ID from Azure
Since the article will demonstrate the steps using the Microsoft Entra admin center, here’s how to access it from Azure if needed.
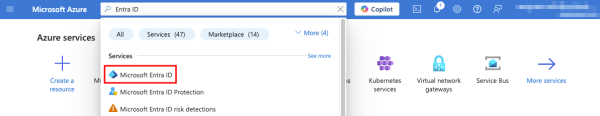
To access Microsoft Entra ID from Microsoft Azure, log on to Azure and click the Microsoft Entra ID icon
If you do not see the icon here, you can also search for it using the search bar within the Azure portal.
Microsoft Entra admin center
Microsoft Entra has a dedicated portal called the Microsoft Entra admin center that provides a more unified experience. It can be accessed at https://entra.microsoft.com/.
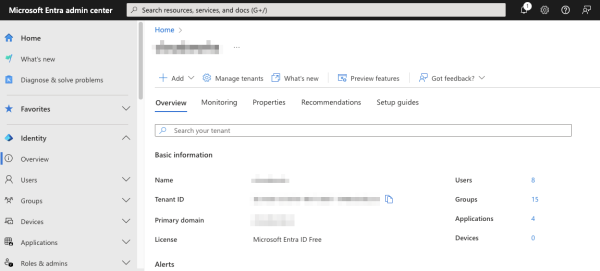
The following image shows the Microsoft Entra admin center tenant overview page.
The subsequent steps and screenshots used in this article use the Entra admin center, but these options are also available on Azure’s Microsoft Entra ID service dashboard.
Creating a tenant
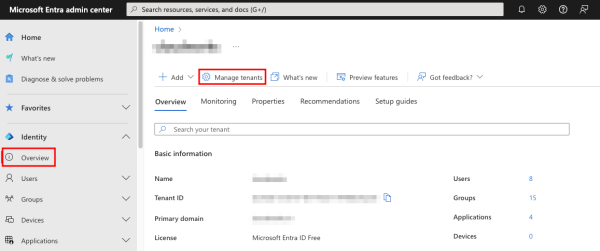
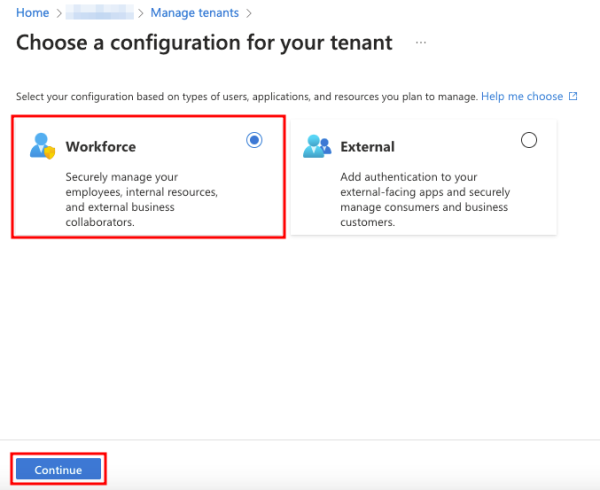
Creating a tenant is very simple. Navigate to the Overview page in the Entra admin center and click Manage tenants.
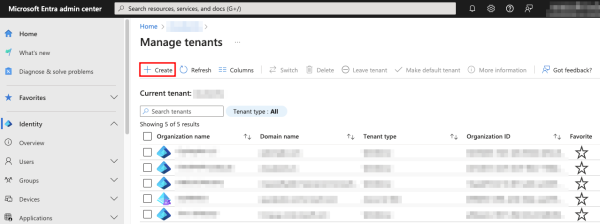
Then click + Create.
Next, choose the type of tenant and click Continue. For this example, we will select Workforce.
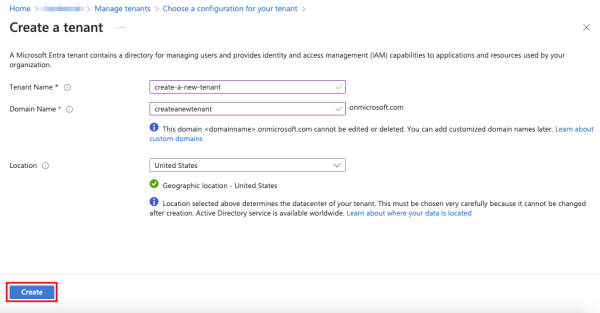
Finally, enter a Tenant Name and Domain Name and select the Location where the tenant data will reside.
Once the tenant is created, you can begin using it.
Watch a 12-minute product demo video of Cayosoft’s hybrid user provisioning
Managing Microsoft Entra ID
As part of the day-to-day operations or management of a Microsoft Entra tenant, you will create users and groups, assign built-in roles, create custom roles, register applications to the directory, and configure self-service password reset, to name a few management tasks.
Roles and administrators
Microsoft Entra ID provides over 100 built-in roles that can be used for most common Entra administrative tasks. You can create custom roles for a granular and restricted access level to manage Entra ID. Creating custom roles requires a P1 or P2 license. You can also define protected actions that include one or more permissions that, when performed, enforce Conditional Access requirements, for example, when deleting or adding a named location.
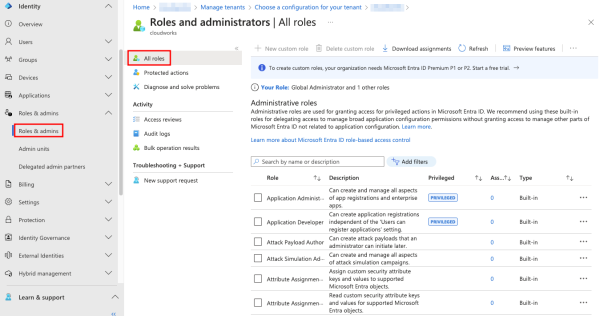
To view all roles, click Roles and admins under Identity in the Entra admin center menu, followed by All roles.
To create a custom role, click + New custom role. Note that this option is disabled if you do not have a P1 or P2 license.
Creating users and groups
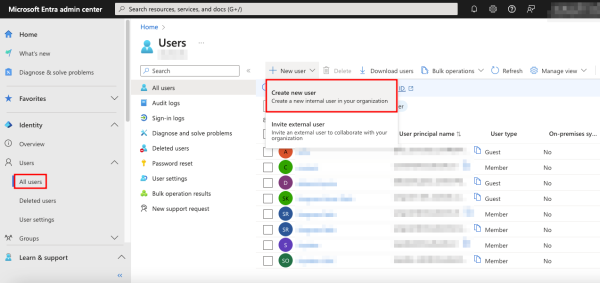
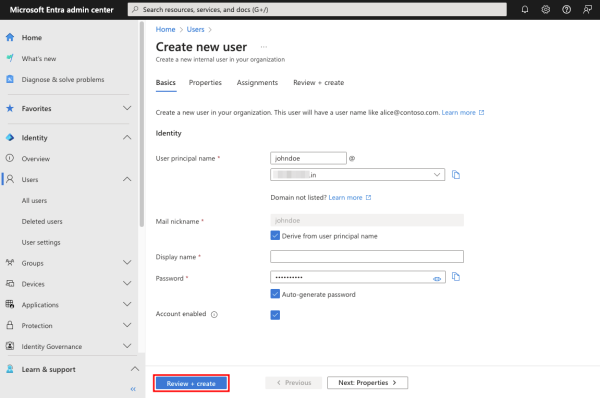
To create an Entra user of the Member type, navigate to All users under Users, click + New user, and select Create new user.
Next, provide a Username and display name and choose a Password. You can provide additional properties now or add them later. Click Review + Create to complete the user creation process.
Groups come in two types:
- Security groups: This group type is selected to give group members access to applications and resources and assign licenses. Group members can be users, devices, service principals, or other groups.
- Microsoft 365 groups: This type is used for collaboration and giving members access to a shared mailbox, calendar, files, SharePoint site, etc. Group members can only be users.
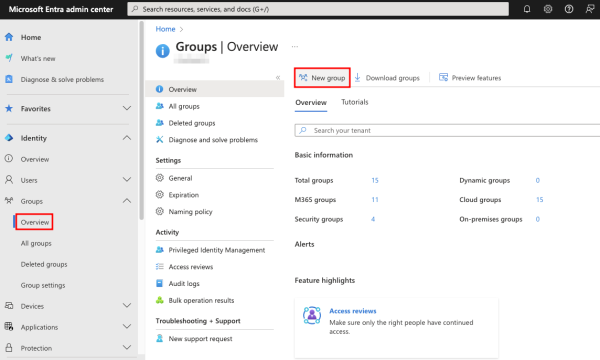
To create a group, navigate to the Overview page in Groups and click New group.
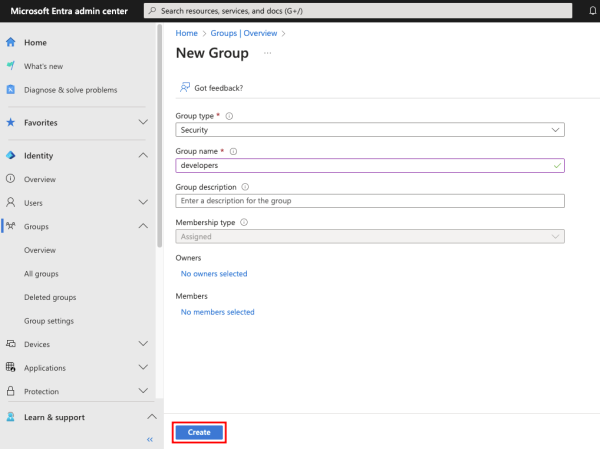
Next, select the group type (here, it’s set to the Security group type) and provide a group name. You can also optionally set an owner for this group and add members at this step or do it later. Click Create to complete creating the group.
Register an app
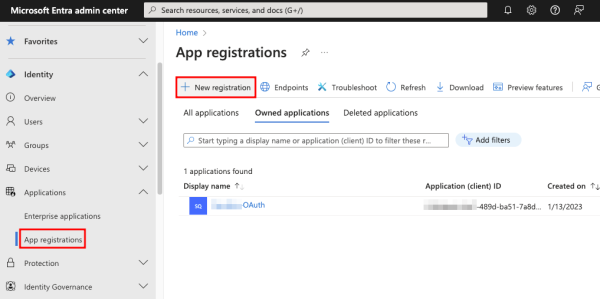
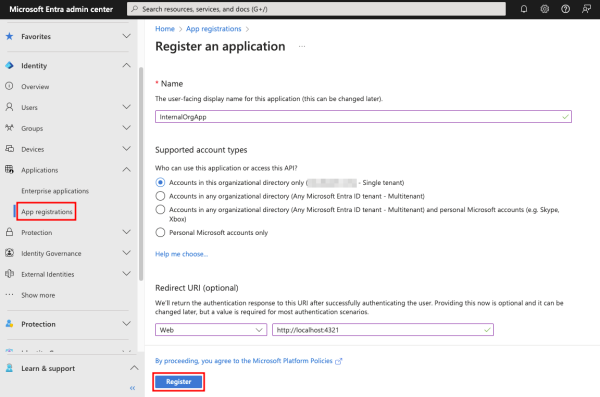
To register an app with Microsoft Entra, navigate to App registrations in Applications under Identity and click + New registration.
Provide a Name for the app, the kind of accounts that can use it (in the screenshot below, the accounts within the organization option is selected), and optionally a Redirect URI. Click Register to complete the process.
Configure Self-service Password Reset (SSPR)
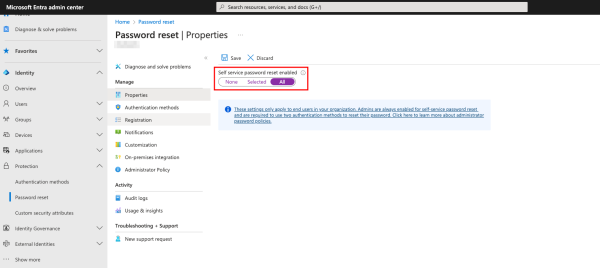
When enabled, Microsoft Entra Self-Service Password Reset (SSPR) allows selected users/groups to change or reset their passwords. This is particularly useful in cases where the password has been forgotten or the account is locked, as it reduces administrative effort.
It is recommended that users register for SSPR and Microsoft Entra administrators configure additional authentication methods when enabling SSPR. Users can reset the password from the application or page prompting authentication or from the dedicated portal available at https://passwordreset.microsoftonline.com/.
You can choose between enabling self-service password reset for all users, no users or for selected users.
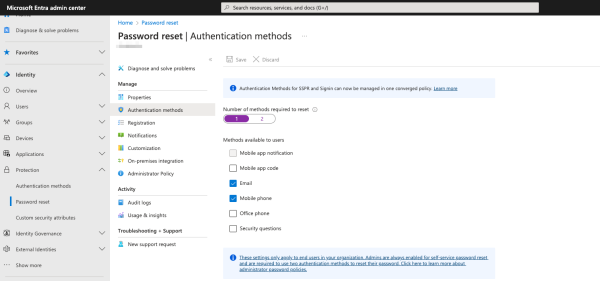
You can then set the number of authentication methods required for SSPR. Multiple authentication methods add to the overall security posture.
Securing identity and access using Entra ID
Many features within Microsoft Entra ID implement various security levels for identity authentication, authorization, and access control. This article discusses Conditional Access, multifactor authentication, Identity Secure Score, and how to view risk reports such as risky users and sign-ins.
Conditional Access
Conditional Access policies enforce a zero-trust approach by making access decisions based on various signals and events, such as risky users, locations, application types, etc. This feature uses an if-then kind of logic to determine if additional actions are required before access is granted.
You must have a P1 or P2 premium license to use Conditional Access policies.
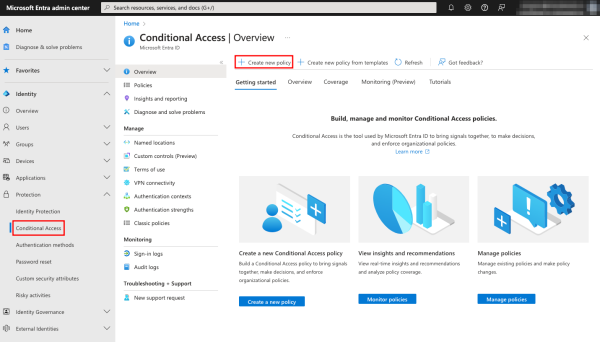
To create a Conditional Access policy, navigate to Conditional Access under Protection and click + Create new policy.
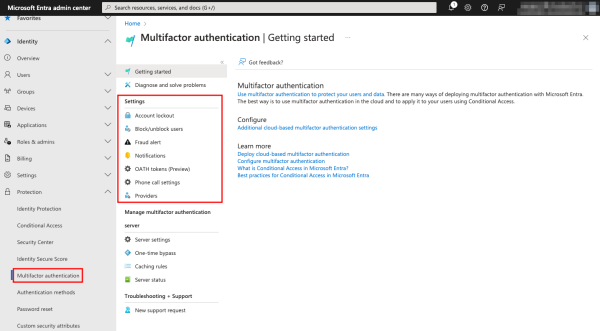
Multifactor authentication
Microsoft Entra multifactor authentication is already enabled through security defaults in Microsoft Entra ID. The recommended approach is to use MFA with Conditional Access policies, which lets you define fine-grained policies when MFA is required based on sign-in signals and events. For example, MFA is requested when signing in from an unnamed location.
In the Multifactor authentication section under Protection, you can configure MFA settings such as when to lock out an account, block/unblock accounts, set notifications, and more.
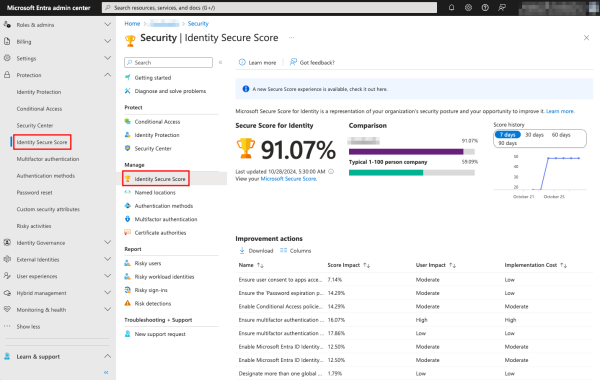
Identity Secure Score
The Identity Secure Score is a measure of the identity security posture, shown as a percentage. It is based on security recommendations from Microsoft.
To view the Identity Secure Score and to see improvement actions, navigate to the Identity Secure Store option under Protection.
Cayosoft for secure identity management
Guardian by Cayosoft provides active threat detection, monitoring, and recovery of objects and attributes for Entra ID, Office 365, on-premises AD, Teams, and Exchange. A key feature of Guardian is the ability to revert changes faster, especially in case of accidental mistakes, cyber-attacks, or malicious changes, reducing authentication and authorization outages. (Microsoft Entra ID and other identity solutions have limitations on native recovery.)
Other features of Guardian include continuous change monitoring, real-time alerting, change history for tracking changes, automatic threat detection, and reversal of malicious changes.
Monitoring Entra ID
This section will show where to view audit logs, sign-in logs, and overall health and cover setting diagnostic settings.
All monitoring-related views and settings are consolidated under the Monitoring dropdown in the menu blade. This article will cover three kinds of activity logs: audit logs, sign-in logs, and provisioning logs.
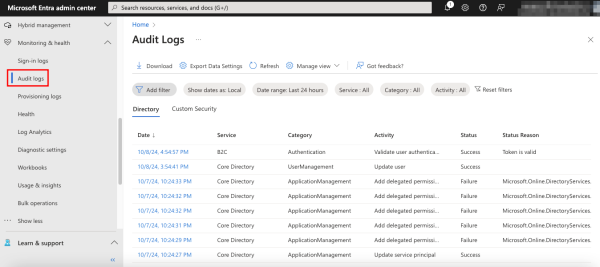
Audit logs record all events in Entra ID, including changes to users (such as password changes) or groups, changes to applications, licenses, etc. These are system-logged events, so they cannot be modified. Audit logs are important for an organization’s compliance and can also be used to investigate incidents and troubleshoot scenarios.
To view Microsoft Entra ID audit logs, expand Identity, then Monitoring & Health, and then select Audit logs.
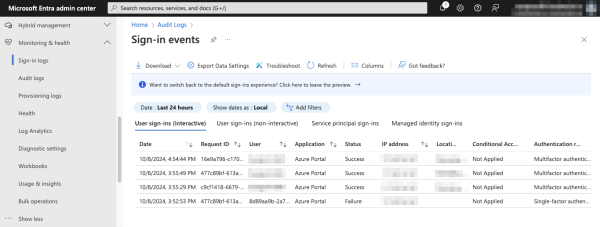
To view sign-in logs, click Sign-in logs under Monitoring & health.
Customizing Entra ID
This section covers aspects such as adding a custom domain, associating an Azure subscription, and adding company branding.
Adding a custom domain
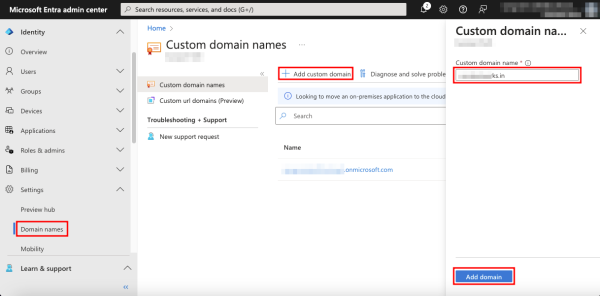
When a Microsoft Entra ID tenant/organization is initially created, it uses a .onmicrosoft.com domain as the primary domain, which cannot be changed or deleted. However, you can add a custom domain name that reflects your organization’s name and make it the primary domain.
To add a custom domain, navigate to Settings under Identity on the left menu and select Domain names. Click + Add custom domain, enter the domain name, and click Add domain.
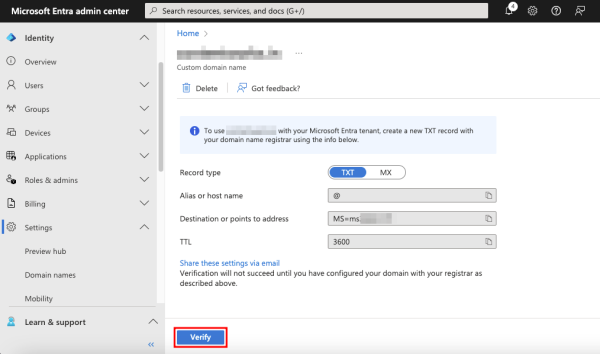
You must then verify your domain by creating a TXT / MX record with the domain name registrar using the info provided on the screen. After adding the records, click Verify for Microsoft Entra to validate. Depending on the registrar, this could take 24 hours or more.
Company branding
Company branding enhances users’ sign-in experience while providing assurance that they are in the right place. You need a Microsoft Entra ID P1 or P2 license to add your branding. Licenses such as Microsoft 365 Business Standard also provide this capability.
You can change the favicon, banner logo, background image, sign-in page title and description, and footer options, among other customizations. To access the custom branding page, navigate to User experiences under Identity and select Company branding.
Associate an Azure subscription to a tenant/directory
An Azure subscription is required to create Azure resources, such as virtual machines, storage, networks, etc. You must associate at least one subscription with the Microsoft Entra ID tenant to be able to do so. You can associate more than one Azure subscription with a single tenant, but a single subscription cannot be associated with multiple tenants.
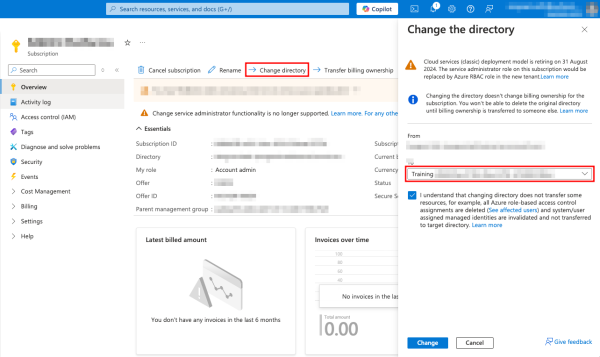
You can change the tenant or directory of an Azure subscription from the subscriptions blade in Azure. The account making the change is ideally the Account admin with the subscription’s owner role and exists in both the tenants, i.e., the source and the destination tenant.
To do this, navigate to the Subscriptions page at https://portal.azure.com/#view/Microsoft_Azure_Billing/SubscriptionsBladeV2 and select the desired subscription. Next, click Change directory and select the new tenant/directory from the list. Agree to the warning and click Change.
This moves the resources to the new tenant except the ones that cannot be moved, as shown in the warning.
Microsoft Entra and Copilot
Microsoft Copilot for Security is a generative-AI-based solution that integrates into various Microsoft security products, such as Defender and Sentinel, to help security professionals manage and respond to threats more effectively.
Microsoft Copilot for Security is enabled in Microsoft Entra, which helps security teams analyze and respond faster to incidents. It gets insights from user sign-ins, groups, and logs (like audit logs and sign-in logs). It then uses machine learning and natural language processing to summarize a particular risk and recommend instructions on mitigating the risk.
In summary, Microsoft Copilot for Security in Microsoft Entra enables security teams to enhance identity security, implement effective access management, and improve identity governance in their organizations.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Entra ID empowers businesses to navigate the complexities of modern IAM, ensuring secure access to resources while meeting evolving compliance requirements. While concerns about cost and integration may persist for some, the long-term benefits of enhanced security, improved productivity, and reduced risk make a compelling case for adopting a comprehensive cloud-based IAM solution like Entra ID.
Tired of juggling separate tools to manage your growing number of on-premises and cloud identities? Cayosoft Administrator provides a single portal to efficiently handle all your Microsoft Entra ID tasks, from user provisioning to group management. Book a demo today to see how Cayosoft can save you time and streamline your identity administration.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content