
Multi-factor authentication can prevent accounts from being accessed if passwords are stolen or obtained using brute force tactics; however, Proofpoint has discovered that multi-factor authentication is being bypassed on Office 365 and G Suite accounts using the legacy IMAP protocol.
Massive IMAP-based password-spraying attacks successfully breached Microsoft Office 365 and G Suite accounts, circumventing multi-factor authentication (MFA) according to an analysis by Proofpoint.
This technique takes advantage of the fact that the legacy authentication IMAP protocol bypasses MFA, allowing malicious actors to perform credential stuffing attacks against assets that would have been otherwise protected.
As noted by Proofpoint’s Information Protection Research Team in a recent report, during a “recent six-month study of major cloud service tenants, Proofpoint researchers observed massive attacks leveraging legacy protocols and credential dumps to increase the speed and effectiveness of brute force account compromises at scale.”
72% of cloud tenants targeted at least once
Their analysis unearthed the fact that around 60% of all Microsoft Office 365 and G Suite tenants have been targeted using IMAP-based password-spraying attacks and, as a direct result, approximately 25% of G Suite and Office 365 tenants that were attacked also experienced a successful breach.
Proofpoint reached the conclusion that threat actors managed to reach a surprising 44% success rate when it came to breaching accounts at targeted organizations.
“As organizations continue to move their mission-critical business functions to the cloud, cybercriminals are taking advantage of legacy protocols that leave individuals vulnerable when using cloud applications,” said Ryan Kalember, executive VP of Cybersecurity Strategy for Proofpoint.
After going through roughly 100,000 unauthorized logins “across millions of monitored cloud user-accounts,” the researchers also discovered that:
• 72% of tenants were targeted at least once by threat actors
• 40% of tenants had at least one compromised account in their environment
• Over 2% of active user-accounts were targeted by malicious actors
• 15 out of every 10,000 active user-accounts were successfully breached by attackers
The IMAP-based password-spraying campaigns used to breach into Office 365 and G Suite accounts saw a boost in volume between September 2018 and February 2019, with the attacks targeting mainly “high-value users such as executives and their administrative assistants.”
Following successful breaches, most attackers logged on Nigerian IP addresses with around 40% of all successful malicious efforts originating from Nigeria, while Chinese actors were behind roughly 26% of successful breaches.
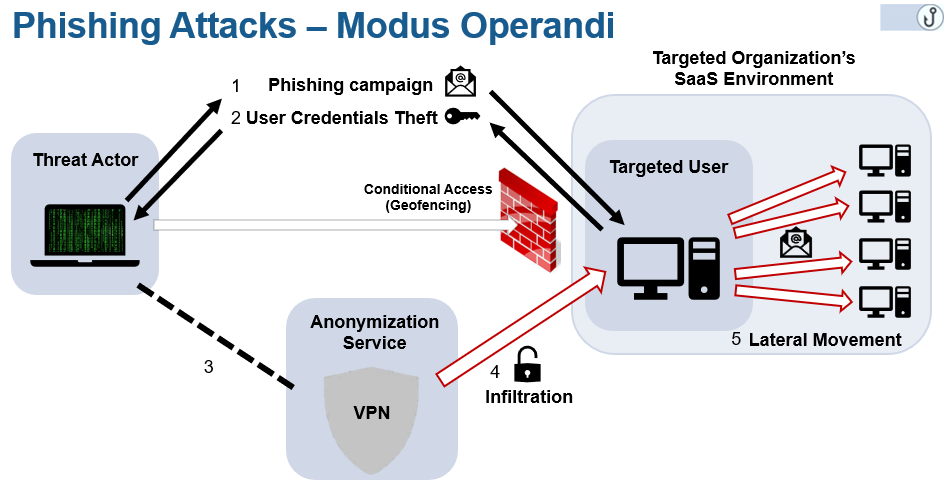
Successful breaches lead to internal phishing, lateral movement
As further detailed in the Proofpoint report, “Attackers utilized thousands of hijacked network devices around the world — primarily vulnerable routers and servers — as operational attack platforms. These hijacked devices gained access to a new tenant every 2.5 days on average during a 50-day period.”
While the bad actors behind these attack series against cloud accounts managed to bypass MFA protections by abusing the unprotected IMAP protocol, the brute forcing attacks they used to crack their way inside the accounts employed tried-and-tested techniques such as large-scale phishing campaigns, as well as credentials obtained following data breaches and data leaks.
The attackers would use the breached cloud accounts to disseminate malware throughout the targeted organizations, gain access to confidential information that can either be sold or used as part of future attacks, as well as fraudulently reroute fund transfers to accounts they control by hijacking employee payroll systems and company banking accounts.
Malicious actors would also “modify email forwarding rules or set email delegations to maintain access and sometimes launch man-in-the-middle attacks. They also leverage breached accounts to phish users in other organizations, causing cross-tenant contamination.”
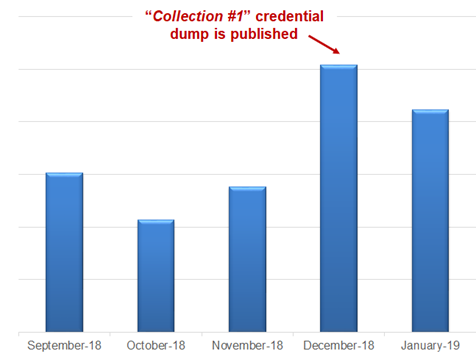
Credential leaks and theft behind huge numbers of credential stuffing attempts
The huge 60% spike in breached accounts noticed by Proofpoint during December stands witness of the impact leaked collections of credentials can have, considering that during that period of time the 87 GB Collection #1 containing 773 million unique emails and associated passwords was spotted being promoted on an online hacking forum.
However, as discovered later, Collection #1 was just a small part of a much larger 993 GB credential database, made available for sale for only $45 and comprised of credentials in the email:pass, user:pass, or number:pass formats.
What’s certain is that, for the time being, there is definitely no shortage of readily available huge collections of credentials given that even more recently, during February, a batch of 127 million records stolen from eight different companies was put up for sale on the Dream Market marketplace for $14,500 in Bitcoin.
And, to make things even worse, the same group listed another batch of 620 million accounts earlier during the same week, stolen from 16 other companies and coming with a price tag of $20,000.
Huge credential leak events lead to large increases in the number of credential stuffing attacks as shown by Akamai in their 2019 State of the Internet report which revealed that 28 billion credential stuffing attempts were detected during the second half of 2018, between May and December 2018, with retail websites being the main target of credential abuse with 10 billion attempts.
“These attacks are laser-focused on specific individuals, rather than infrastructure, and continue to grow in sophistication and scope. As a best practice, we recommend that organizations establish a cloud-first approach to security that prioritizes protecting employees and educates users to identify and report these advanced techniques and methods,” also stated Kalember.