Tier 0 and privileged service accounts in Active Directory are critical to the security of your organization. These accounts hold the highest level of access, and if compromised, the consequences can be severe—potentially leading to full domain control or widespread ransomware incidents. With Cybersecurity Month upon us, now is the perfect time to take action. One of the most effective measures is applying Fine-grained Password Policies (FGPP). This guide will show you the importance of securing these accounts and how FGPP can help reinforce your AD security.
Importance of Securing Tier 0 and Privileged Accounts
Tier 0 accounts and Privileged Service Accounts are high-value targets for attackers. These accounts typically have elevated privileges, granting them control over critical systems and sensitive data. If compromised, these accounts can be used to escalate attacks, deploy ransomware, or manipulate AD configurations, leading to a full domain compromise.
By implementing Fine-grained Password Policies , you can enforce stricter security measures, such as longer and more complex passwords, shorter password expiration cycles, and tighter account lockout policies specifically for these accounts. This approach ensures these critical accounts are less vulnerable to brute-force attacks, password reuse, and other common methods attackers use to gain unauthorized access.
What are Tier 0 Accounts?
Tier 0 objects hold the highest level of privileges in an Active Directory environment, typically admins associate these accounts with the built-in, highly privileged groups in Active Directory like Domain Admin, Enterprise Admin, or Schema Admin permissions.
They are not wrong. These are indeed Tier 0 accounts, but Tier 0 accounts extend well beyond these groups and members of these groups. They should be considered as any account that has control over the core AD infrastructure, including domain controllers, identity systems, and other critical systems. They have direct access to sensitive systems and if compromised would have a detrimental impact to the entire enterprise.
Examples of Tier 0 Accounts
Domain Admins: Full control over the domain, including permissions to access any object in the Active Directory.
Enterprise Admins: Manage the entire forest and can make critical configuration changes across domains.
Schema Admins: Modify the AD schema, impacting all objects and how they interact within the domain.
AD Service Accounts: Service accounts running domain controllers or AD-related services that have elevated privileges.
Entra ID Connect Sync Account and Groups
What are Privileged Service Accounts?
Privileged Service Accounts are non-interactive accounts used by services, applications, or scheduled tasks to perform automated processes. These accounts often require elevated privileges to function properly.
Examples of Privileged Service Accounts
SQL Server Service Accounts: Operate SQL services with necessary permissions.
Application Pool Identities (IIS): Used for web services within IIS.
Backup Software Service Accounts: Access files and directories across the network for backup operations.
Accounts that are used for system management etc.
Immediate Actions: Applying Fine-grained Password Policies for Enhanced Security
To secure Tier 0 accounts and Privileged Service Accounts, you can apply stricter Fine-grained Password Policies right now, using the built-in features of Active Directory, without additional spending.
Fine-grained Password Policy Settings
- Minimum Password Length: Should be 30 characters or longer.
- Enforce Password History: Should be 24 or higher.
- Password must meet Complexity: Should be enabled.
- Store Password using reversible encryption: should be disabled.
- Protect from accidental deletion: should be enabled.
- Enforce minimum password age: 1.
- Enforce maximum password age: 30.
- Number of failed logon attempts: 3
- Reset failed logon attempts after: 15 minutes.
Active Directory Admin Center Steps: Fine-grained Password Policies
- Create a new Password Setting Object (PSO), this is used to define the FGPP.
- Open the AD Administrative Center (ADAC)
- Navigate to the systems container select Password Settings Container as depicted below in the picture.
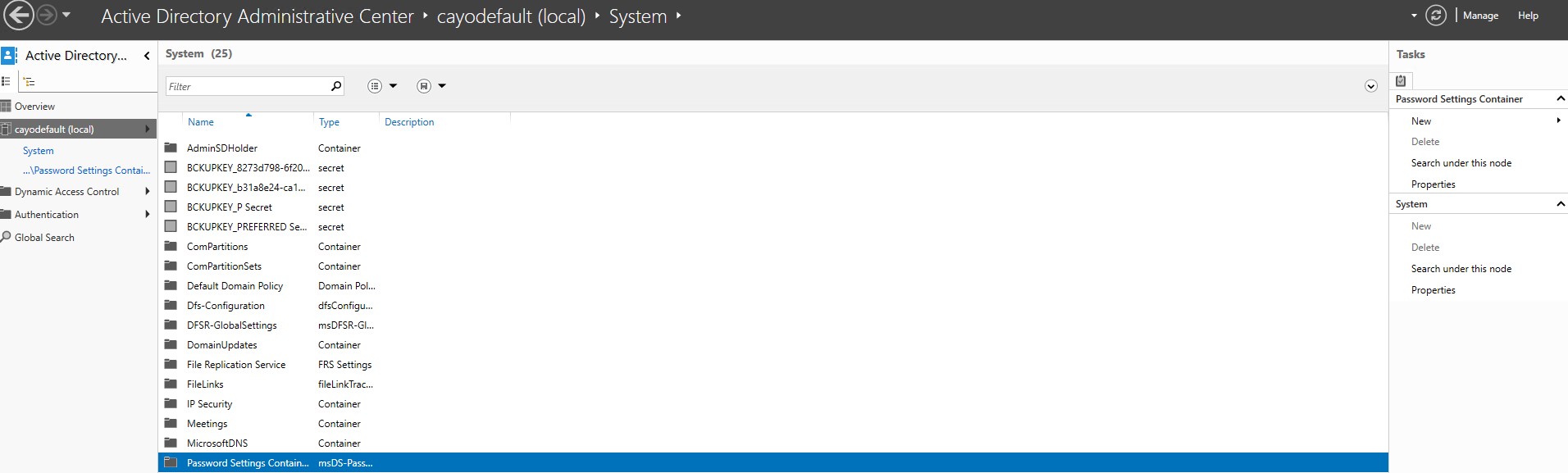
- Select New Password Settings
- Create a new PSO and configure the desired settings as outlined above and depicted in the picture.
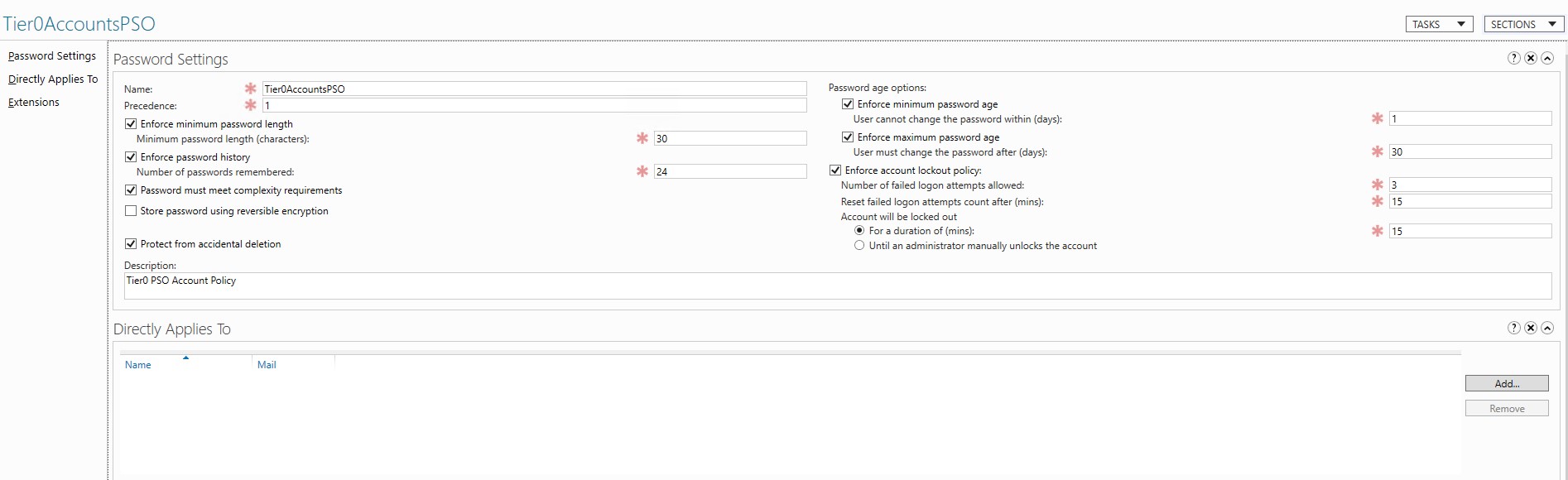
- Apply the PSO to Tier 0 accounts
- Go to the Direct Applies to Section and add in all Tier 0 accounts
- Repeat the same process for your Service Accounts.
Note: It is best to have a separate PSO for service accounts, as you may need to adjust certain settings to align with your business needs.
PowerShell Commands: Fine-grained Password Policies
For those who prefer automation, here’s how you can create and apply FGPP using PowerShell.
New
-ADFineGrainedPasswordPolicy
-Name "Tier0AccountsPSO"
-Precedence 1 -ComplexityEnabled $true
-Description "Tier0 PSO Account Policy"
-DisplayName "Tier0AccountPSOPOlicy"
-LockoutDuration "0.00:15:00"
-LockoutThreshold "3"
-LockoutObservationWindow "0.00:15:00
-MaxPasswordAge "30.00:00:00" -MinPasswordLength "30"
-PasswordHistoryCount "24"
-ReversibleEncryptionEnabled $false
-ProtectedFromAccidentalDeletion $true
To apply this policy to Tier 0 or Service Accounts: Example Domain Admins
Add
-ADFineGrainedPasswordPolicySubject
-Identity " Tier0AccountsPSO "
-Subjects “Domain Admins”
This will apply the PSO to the Domain Admins group.
Note: Repeat the process for your Service Accounts be sure to update the PSO name and the precedence variables
Why This Matters: The Importance of Securing Privileged Accounts
Tier 0 accounts and Privileged Service accounts represent the keys to your Active Directory kingdom. Attackers often target these accounts because they provide the most direct path to critical systems and sensitive data. Once compromised, these accounts can lead to:
Lateral movement within the network.
Escalation of privileges to access other systems.
Deployment of ransomware or malware that affects the entire organization.
Applying stronger password policies and lockout thresholds via Fine-grained Password Policies (FGPP) helps mitigate these risks by reducing the chances of brute-force attacks, minimizing password reuse, and tightening security around your most critical assets.
Take Action Now
In the spirit of Cybersecurity Month, take these immediate steps to apply Fine-grained Password Policies and enhance the security of your Active Directory environment. By doing so, you strengthen your defenses against potential attackers and ensure that your Tier 0 and service accounts are well-protected. For organizations looking to simplify and automate this process, Cayosoft’s suite of Active Directory management tools can help. With Cayosoft Administrator, you can easily manage Fine-grained Password Policies, enforce security best practices, and streamline the protection of privileged accounts, all from a single, intuitive platform.
FAQs
A common risk is that these accounts are typically not monitored as closely as user accounts, which can lead to weak security practices, such as using the same password for extended periods or failing to rotate passwords.
Identifying privileged service accounts in Active Directory can be tricky since these accounts are often non-interactive and used by various applications and services. A good starting point is to audit accounts that have elevated permissions or that are linked to essential services, such as SQL Server, IIS, or backup software. Using tools like Cayosoft Administrator can help streamline this process by providing detailed reports on privileged accounts, making it easier to identify and secure them.
A Fine-grained Password Policy in Active Directory allows administrators to apply different password and account lockout settings to specific users or groups, without affecting the entire domain. This means you can enforce stricter security measures for sensitive accounts like Tier 0 and privileged service accounts while maintaining more lenient settings for regular users.
To create a Fine-grained Password Policy in Active Directory, you need to use the AD Administrative Center or PowerShell. You can create a Password Settings Object (PSO) to specify password complexity, expiration rules, and lockout policies for particular groups or users. For more detailed steps, refer to the section on how to apply FGPP in ADAC in the article above.
To view which Fine-grained Password Policy is applied to a user or group, you can use the Active Directory Administrative Center (ADAC) or PowerShell. In ADAC, navigate to the Password Settings Container and check the PSO associated with the user. In PowerShell, you can use the Get-ADFineGrainedPasswordPolicy command to retrieve details about the policies.
Fine-grained Password Policies provide a more flexible approach to managing account security by allowing different password policies for different sets of users. This is especially important for accounts like Tier 0 and Privileged Service accounts, where stricter rules on password length, complexity, and lockout thresholds can enhance security while minimizing the risk of a domain-wide compromise.
Fine-grained Password Policies can be tailored specifically for service accounts by creating a separate Password Settings Object (PSO) with appropriate rules. Since service accounts often require longer password validity and may have different operational needs, FGPP allows you to customize policies to ensure security without disrupting business processes. Use PowerShell or ADAC to apply these policies directly to service accounts.