The FBI arrested a former AWS engineer who allegedly stole data for more than 100 million Capital One customers and credit card applications, thanks to a misconfigured firewall.
Paige A. Thompson, 33, is accused of accessing Capital One‘s network and stealing personal information for more than 100 million customers and individuals who applied for Capital One credit cards. According to a statement from the company Monday, the Capital One breach exposed names, addresses, phone numbers, email addresses, dates of birth and self-reported income for 100 million people in the U.S. and 6 million in Canada.
Capital One’s statement said the breach also exposed “portions of credit card customer data” that includes credit scores, credit limits, balances and payment history, as well as some transaction data from 23 days total during 2017, 2018 and 2019. The financial services giant also said the threat actor obtained about 140,000 Social Security numbers and 80,000 bank account numbers, as well as 1 million Social Insurance Numbers of Canadian customers.
Capital One said the threat actor exploited a “configuration vulnerability,” which the company said it fixed immediately upon discovery. According to the criminal complaint against Thompson, undersigned by Joel Martini, special agent for the FBI, a misconfiguration in a firewall allegedly allowed her to execute commands on a company server.
The FBI alleged Thompson used a single command and “obtained security credential for an account known as ******-WAF-Role that, in turn, enabled access to certain of Capital One’s folders at the Cloud Computing Company.” The complaint doesn’t specify which cloud provider was hosting Capital One’s servers, but the document references “buckets,” which indicates the provider is AWS. The complaint also includes an email sent to Capital One’s vulnerability disclosure email address on July 17 alerting the company to “leaked S3 data” on GitHub, again referring to AWS Simple Storage Service buckets.
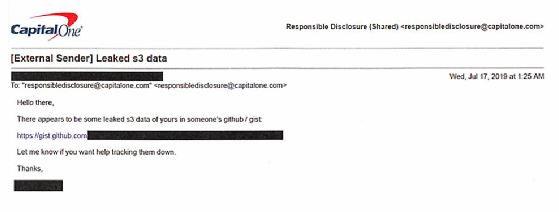
The email from the anonymized tipster included a GitHub URL for the stolen data. Upon receiving the email, Capital One began investigating the incident and contacted the FBI. According to the complaint, the FBI traced the GitHub post and other social media activity to Thompson, which led to her arrest.
Martini added that the FBI found information on a GitLab account connected to Thompson, including a resume that said she was a systems engineer that “formerly worked at the Cloud Computing Company from 2015-16.” A LinkedIn profile connected to the GitLab account said Thompson worked at AWS from 2015-2016 as a systems engineer for S3 (the LinkedIn profile is currently unavailable).
Thompson was charged with one count of computer fraud and abuse in connection with the Capital One breach.
Even though the S3 data was on GitHub, Capital One said it is “unlikely” the stolen data was disseminated or used for fraud.
“While I am grateful that the perpetrator has been caught, I am deeply sorry for what has happened,” Capital One Chairman and CEO Richard D. Fairbank said in a statement. “I sincerely apologize for the understandable worry this incident must be causing those affected and I am committed to making it right.”