Home » Five Critical Azure Security Best Practices for Effective Risk Management » Hybrid Active Directory Health Check: 5 Must-Know Tips for IT Administrators
Hybrid Active Directory Health Check: 5 Must-Know Tips for IT Administrators
Learn 5 essential hybrid active directory best practices for managing and connecting on-premises data centers and private/public clouds, ensuring AD health and security.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
While many organizations have migrated workloads to the cloud, on-premises infrastructure remains common. Some workloads are simply better suited for on-premise deployments, and in other cases cloud costs can be prohibitive. As a result, many modern organizations have a hybrid infrastructure.
Hybrid infrastructure comprises on-premises data centers and private and public clouds. AD administrators need specialized tools to manage and connect hybrid components in this complex infrastructure seamlessly. One example is the hybrid Active Directory (AD), which manages on-premises AD objects such as users and devices and syncs them to the cloud.
This article will explore five essential hybrid active directory best practices. With these best practices, administrators can improve hybrid AD health and security and ensure an undisrupted synchronization between on-premises and cloud environments.
Summary of Key Hybrid Active Directory Best Practices
Hybrid active directory management requires maintaining the connection of both on-premises AD and a public cloud entity, Microsoft Entra ID (previously known as Azure Active Directory). Administrators are also responsible for securing two environments at the same time.
The five best practices summarized in the table below can help address these challenges. This article will discuss each of them in detail.
| Best practice | Description |
| Maintain Azure AD Synchronization Health and Security | Leverage Microsoft Entra Connect Health to monitor and implement secure methods for synchronizing AD data between on-premises and the cloud. |
| Optimize Hybrid User and Group Management | Efficiently manage users and groups in cloud and on-premises AD and streamline access using role-based access control (RBAC) |
| Secure Hybrid Environment with strong authentication methods | Employ authentication methods such as conditional access policies and multi-factor authentication (MFA) for both on-premises and cloud. |
| Regularly monitor and audit hybrid AD Infrastructure | Regular monitoring and audits are conducted with Azure Monitor to ensure system integrity and security. |
| Plan for a regular backup and disaster recovery | Utilizing backup technologies like Azure Backup, plan and regularly test backup and disaster recovery strategies in a Hybrid environment. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Hybrid Active Directory Best Practice #1: Maintain Azure AD Synchronization Health and Security
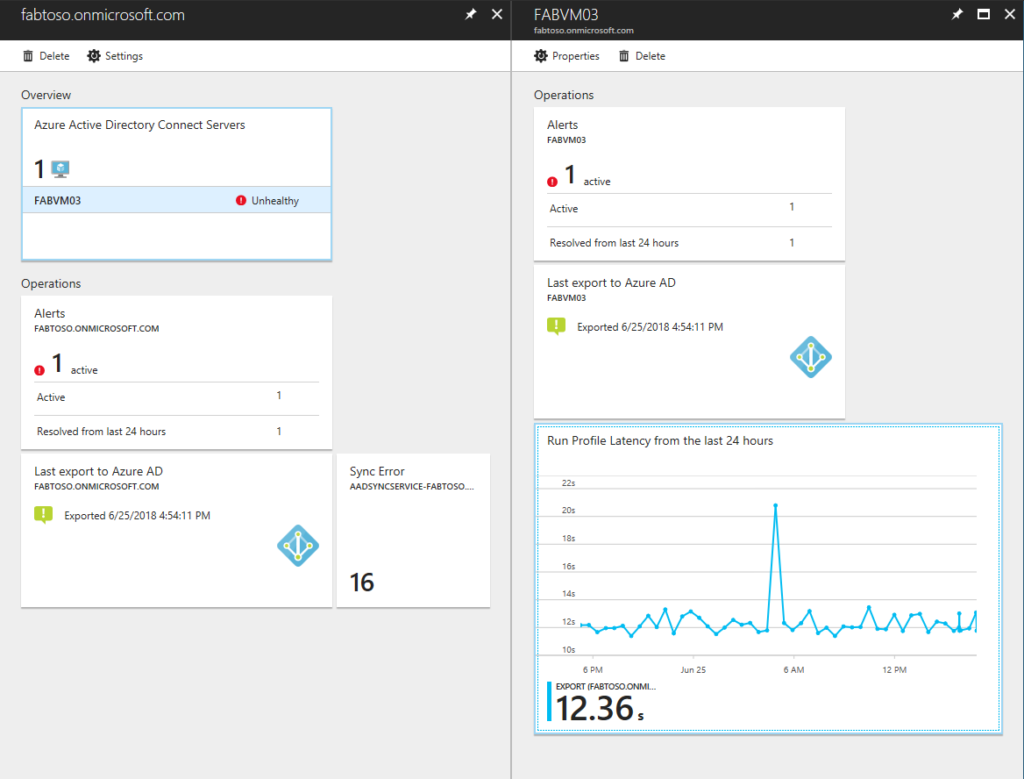
Pairing our primary synchronization tool with Microsoft Entra Connect Health efficiently monitors our hybrid active directory environment. It monitors on-premises to cloud synchronization and provides alerts on on-premises domain controller health, replication, and security. Microsoft Entra Connect Health also offers additional monitors on other performance counters related to Active Directory, and provides administrators with environment visibility.
Note: In April 2024, Microsoft introduced a new synchronization tool called Microsoft Entra Cloud Sync. With this latest tool, manual installation of cloud sync agents on on-premises domain controllers is not mandatory and is orchestrated solely through Microsoft Online services. According to Microsoft, this would replace Microsoft Entra Connect in the future.
Hybrid Active Directory Best Practice #2: Optimize Hybrid User and Group Management
When dealing with hybrid identities and groups, AD admins should always follow the principle of least privilege. This principle protects our environment by minimizing the attack vectors that bad perpetrators can exploit. In addition to following the industry standard principle, both on-premises and cloud environments have corresponding security mechanisms.
Here are some examples:
| On-Premises | Cloud |
| AD Security Groups | Entra ID Groups |
| NTFS Permissions | Identity and Access Management (IAM) |
| Group Policy | Azure Policy |
| Windows Firewall | Network Security Groups (NSG) |
The table above includes NTFS Permissions and IAM. As a best practice, admins should only provide the least privilege permissions in both environments. This method is how Role-based Access Control (RBAC) permissions work.
For example, an administrator can create AD security groups for on-premises, name them appropriately, add AD users, and configure NTFS permissions on the domain level. That same group will synchronize to the cloud, and the admin can assign an appropriate IAM role to manage the Entra ID environment sufficiently. By doing something similar, they have added a level of security to their hybrid environment.
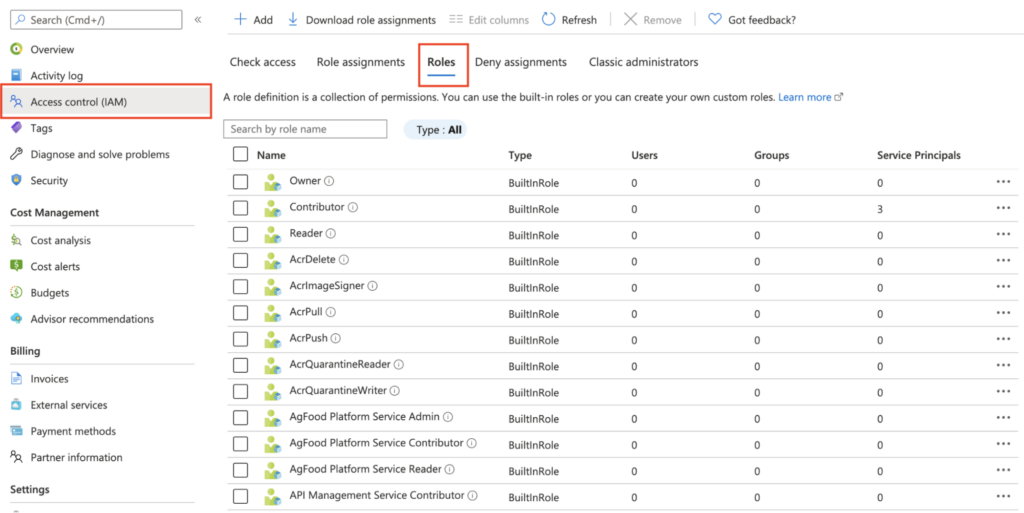
Adding a layer of security is just one example. For seamless and efficient hybrid user and group management, consider leveraging solutions like Cayosoft Administrator. Its powerful automation capabilities streamline provisioning, lifecycle management, and de-provisioning across both on-premises Active Directory and Azure Entra ID.
Additionally, while dynamic group membership control helps maintain clean and accurate memberships based on predefined criteria, achieving an actual least-privileged delegation model involves more than just managing group access. This model is implemented through a combination of delegated roles and policies, ensuring administrators only have visibility into what is necessary and are limited to actions that align with their specific responsibilities.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Hybrid Active Directory Best Practice #3: Secure Hybrid Environments with Strong Authentication Methods
In addition to the previous section, there are other ways of securing hybrid active directory besides using RBAC permissions. For example, verifying a user’s identity by enabling multi-factor authentication (MFA) and including it as an access control in a conditional access policy. Using these methods and the previously mentioned NTFS and IAM concepts strengthens hybrid infrastructure security and access controls.
AD admins can either enable MFA individually at the synchronized AD user level or enable MFA in bulk using a conditional access policy. To do this, create a conditional access policy requiring MFA to grant access, like the screenshot below. Once an admin creates the conditional access policy, they can add synced AD users or a synced group with members.
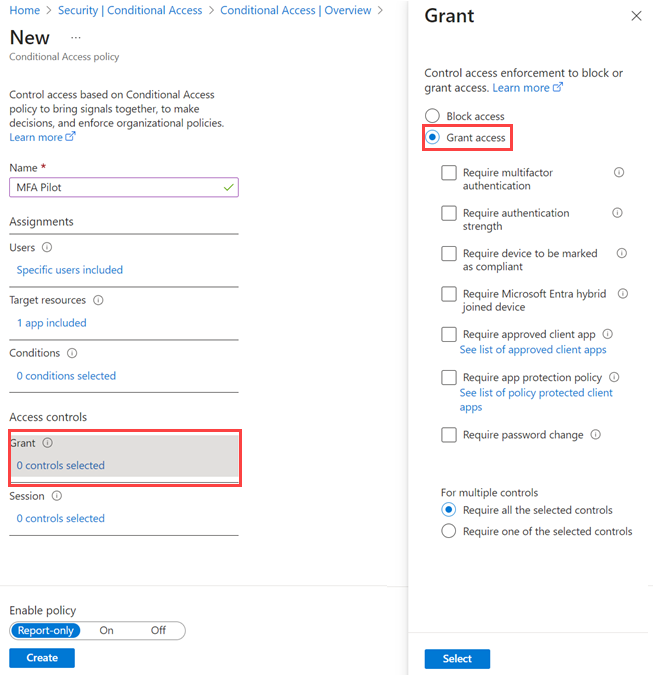
It is essential to not only set conditional access policies for verification and authentication but also combine this with other methods to enhance security.
Conditional access policies can be easily spoofed, bypassed, and exploited, thus making our hybrid environment prone to attacks that lead to compromise and extensive damage to our Active Directory. Notably, modifications and deletions made through conditional access policies often bypass the Azure recycle bin, making recovery challenging. Cayosoft Guardian offers a robust solution by enabling the rollback of AD objects and attribute-level changes with a single click. The same capability can also be applied for Entra ID objects, even those that have been hard deleted or have cycled out of the recycle bin after 30 days. This includes not just the aforementioned conditional access policies but also AD users, groups, intune devices, policies, configurations, and many other items that typically never make it to the recycle bin.
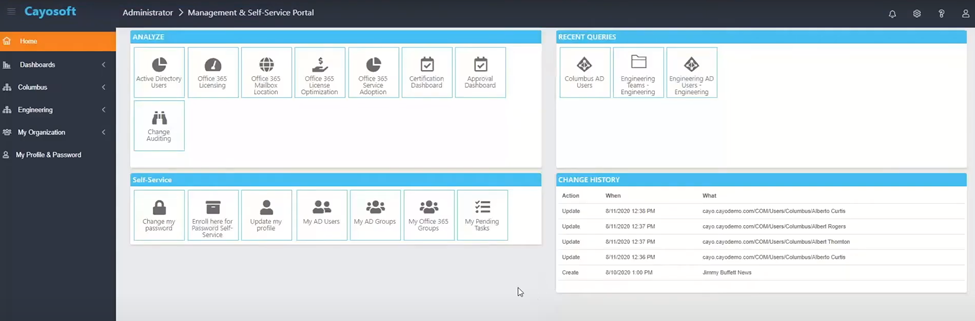
On a related note, admins can also enable the authentication method where users can self-reset their passwords by providing their preferred authentication method during first-time login on any Microsoft online service. However, from a user’s perspective, it is inconvenient to give out personal information like mobile number or email and set it up themselves. To help with this, third-party applications like Cayosoft Administrator integrate well with Microsoft Azure and manage self-service password resets autonomously.
Hybrid Active Directory Best Practice #4: Regularly Monitor and Audit Hybrid AD Infrastructure
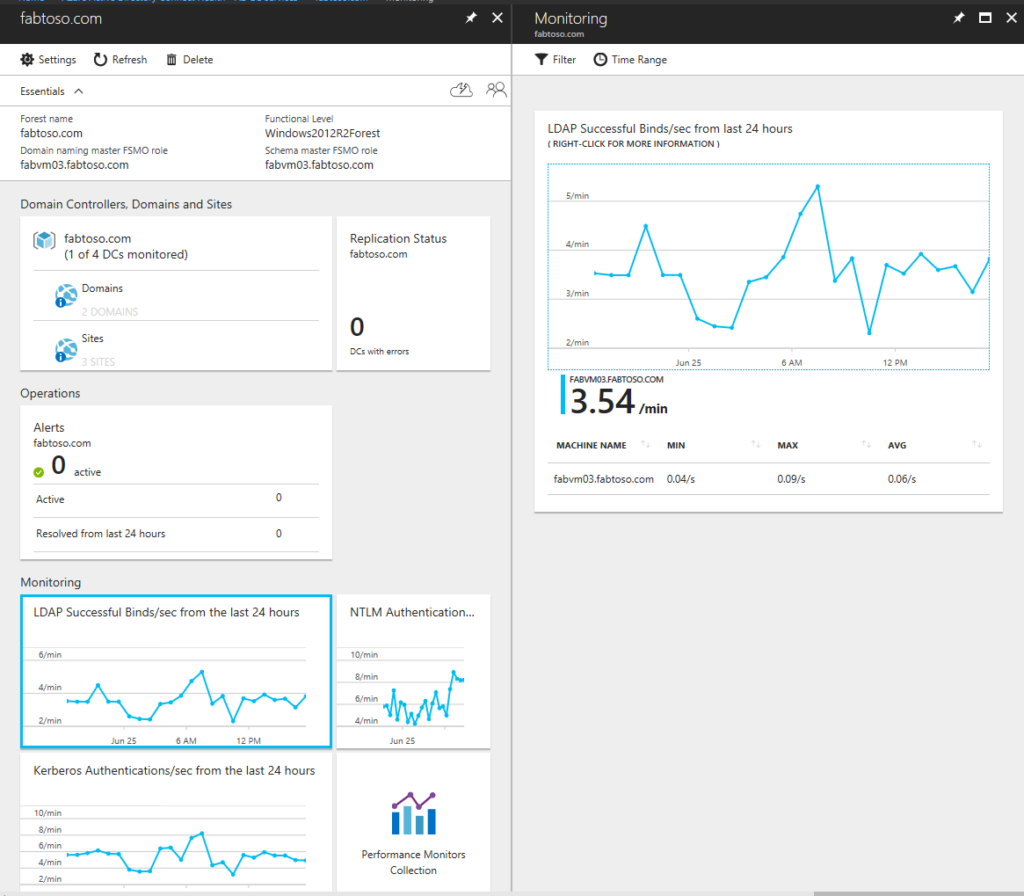
In the initial section of the article, we discussed monitoring hybrid AD health using Microsoft Entra Connect. However, if organizations want to expand the scope of their monitoring beyond AD sync and domain services, they can use Azure Monitor. Specializing in comprehensive monitoring, Azure Monitor collects telemetry data and metrics from multiple sources, such as on-premises and Azure servers.
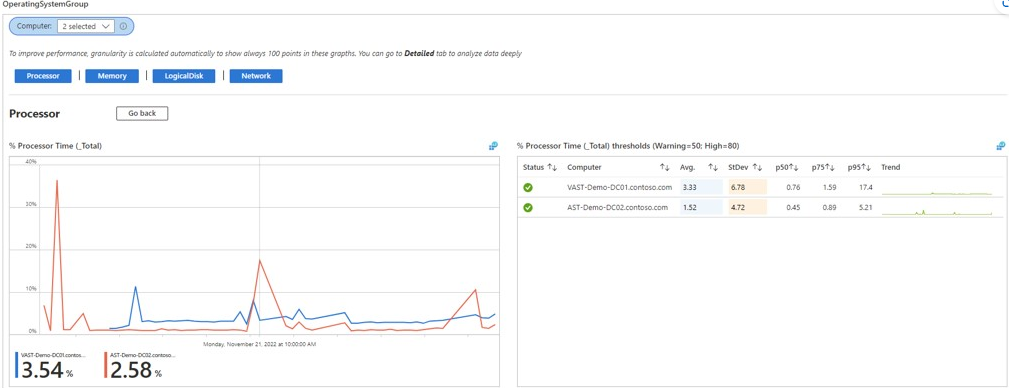
By storing and auditing events from servers or services, we can increase our hybrid environment’s visibility and observability. Administrators can collect all the events received on both on-premises and cloud environments and send them to Log Analytics. Also, by sending the logs to a centralized workspace, all servers in a hybrid environment can benefit from more reclaimed space, as organizations don’t need to keep the logs in each server for a long time.
With Log Analytics within the Azure Monitor portal, we can browse the history of events using the Kusto Query Lane (KQL), a powerful querying tool for data analysis within the Azure environment. Pairing KQL with data stored in Azure Data Explorer, admins can easily visualize the events collected and export them as a readable report for auditing and compliance.
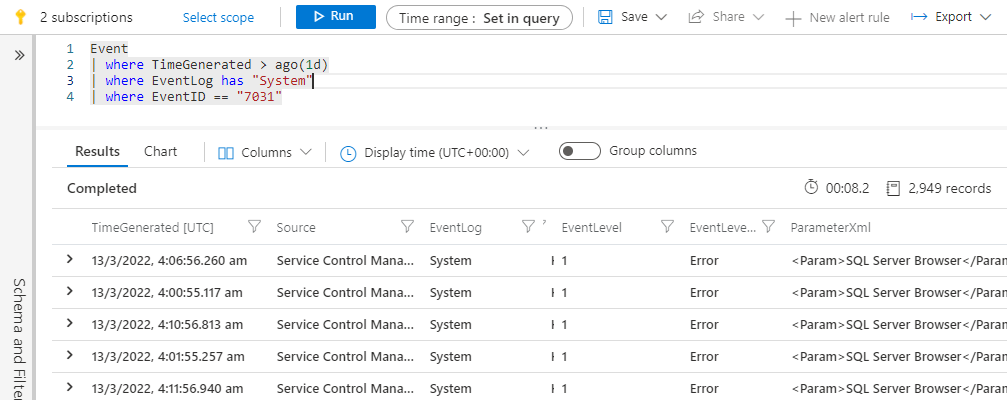
Watch demo video of Cayosoft’s hybrid user provisioning
Hybrid Active Directory Best Practice #5: Plan for a Regular Backup and Disaster Recovery
When maintaining IT infrastructure such as hybrid IT environments, Administrators should know the importance of regularly backing up critical components in the event of security breaches or disasters. One of these essential components that we need to regularly back up is our Active Directory environment; losing it initially would result in a much more difficult recovery.
Working on an on-premises domain controller, we can back up our AD environment by storing the NTDS.DIT file containing directory information such as users, groups, computers, and other AD objects. However, since our environment is syncing to the cloud, we can generally back up our environment to the cloud with backup solutions like Azure Backup.
Cayosoft Guardian enables quick rollback of critical AD and M365 object modifications, providing unparalleled flexibility and control. For even more robust protection and near-instant recovery, Cayosoft’s Guardian Forest Recovery is a patented, all-in-one forest recovery solution that can reestablish your entire AD forest in mere minutes–a capability that goes far beyond traditional backups. With a single click, you can restore objects, attributes, domain controllers, or an entire forest to their previous state, ensuring business continuity even in the face of the most devastating attacks.
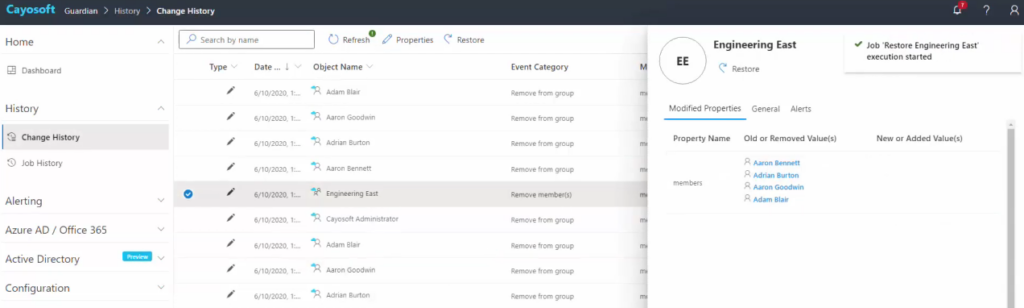
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Large enterprises, like Microsoft, roll out more hybrid-centered certifications, simultaneously pushing the boundaries on how they can innovate hybrid infrastructure. As long as hybrid infrastructure and services like hybrid active directory are around, it is best to follow proven best practices.
Most of the best practices above revolve around protecting and securing two environments simultaneously. Following them would preserve our hybrid environment and the whole organization.
Finally, simultaneously managing two environments takes time, and public clouds like Microsoft Azure don’t have all the tools yet to manage a hybrid infrastructure efficiently. That is why most organizations rely on centralized software like Cayosoft to manage their operations. The Cayosoft Management and Protection Suite, including Cayosoft Administrator and Cayosoft Guardian, helps administrators follow and scale the best practices covered in this article.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content