Home » Five Critical Azure Security Best Practices for Effective Risk Management » Securing Azure Identity Management: A Definitive Action Plan
Securing Azure Identity Management: A Definitive Action Plan
Learn five essential Azure identity management best practices to strengthen security in cloud environments, including deploying a centralized system and enforcing multi-factor authentication and role-based access control.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Implementing robust and efficient identity and access management (IAM) best practices is essential in ensuring a strong security posture. IAM grants authorized users access to the right resources at the right times and for the right reasons. This approach can considerably reduce the attack surface and minimize the potential damage caused by cyber threats.
As organizations continue to migrate their operations to the cloud, the need for effective IAM strategies becomes increasingly apparent. This is especially true in cloud environments like Microsoft Azure, where sensitive data and powerful compute resources are readily available and where the complexity and scale of operations often necessitate IAM solutions and make Azure identity management a top business concern for many organizations.
Cyber-attacks are becoming more frequent and increasingly sophisticated, with the consequences of successful attacks becoming increasingly devastating. In a recent IBM report, the average cost of a data breach was reported to reach an all-time high of USD 4.45 million in 2023; stolen or compromised credentials and cloud misconfigurations were responsible for 15% and 11% of breaches, respectively, and 82% of the data breaches involved data stored in the cloud. These are stark reminders of the potential damage when unauthorized individuals access sensitive resources.
In this article, we explore five essential Azure identity management best practices and provide practical guidance on navigating complexities of IAM in the cloud.
Summary of Key Azure Identity Management Best Practices
This table summarizes five Azure identity management best practices this article will explore in detail.
| Best Practice | Description |
| Deploy a centralized identity management system | Consolidate and manage user identities, groups, and access permissions from a single platform |
| Automate identity lifecycle management | Implementing a systematic and automated approach to manage the creation, modification, and deletion of user identities |
| Enforce Multi-Factor Authentication (MFA) | Enhance login security by requiring a second verification factor beyond a username and password |
| Implement Role-based access control (RBAC) | Grant resource access based on users’ roles and responsibilities, minimizing the attack surface. |
| Monitor and audit user activity and review access permissions | Regularly review access logs to identify suspicious behavior, maintain compliance, and update access permissions to maintain security posture |
Five Essential Azure Identity Management Best Practices
Irrespective of an organization’s use case, the five best practices below can help improve security posture of Azure environments by securing identity management systems.
#1 Deploy a centralized identity management system
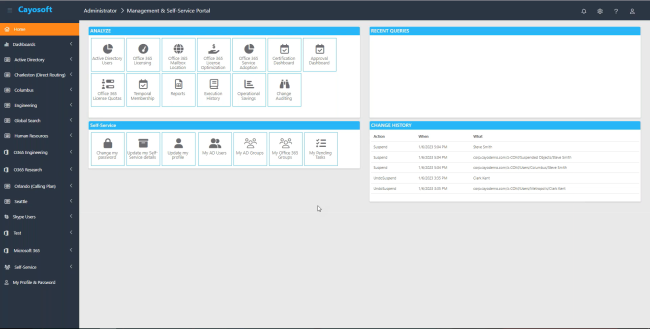
In a hybrid Microsoft environment where user identities often reside in both on-premises Active Directory (AD) and Microsoft Entra ID (formerly Azure Active Directory), a centralized identity management system becomes vital because it allows organizations to manage identities and access rights across both on-premises and cloud environments from a single interface.
A centralized identity management system provides a single source of truth for identity data, and it offers several key benefits in hybrid Microsoft environments:
- Simplified user management: IT admins can manage all user identities from a single location, reducing administrative overhead and minimizing the risk of inconsistencies
- Enhanced security: Centralized policies and access controls can be applied consistently across both on-premises and cloud resources, minimizing security gaps
- Improved user experience: Users can leverage a single sign-on (SSO) experience to access all authorized resources, regardless of location, improving overall productivity.
Microsoft Entra ID serves as the core for centralized identity management in Azure. It seamlessly integrates with your AD through Microsoft Entra Connect (formerly Azure AD Connect), enabling synchronized user identities and access controls. By synchronizing both environments, every change made to user accounts in your AD is reflected in Entra ID and vice versa.
Although Entra ID seamlessly integrates and synchronizes user identities and access controls with your AD, managing both environments can still be complex. Cayosoft Administrator further simplifies AD management by providing a unified interface for managing on-premises, cloud, and hybrid environments. As an IT admin, you can leverage Cayosoft Administrator to:
- Gain centralized visibility into all user accounts and permissions across the hybrid environment.
- Perform user provisioning and management tasks from a single console, streamlining administration.
- Automate routine tasks such as user onboarding and offboarding, reducing manual workload and potential errors.
Implementing a centralized identity management system like Microsoft Entra ID and utilizing solutions like Cayosoft Administrator provides a unified platform for managing user identities and access across the hybrid environment and significantly enhances security by eliminating inconsistencies in your security policies and enforcement across the various interfaces of your environment.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
#2 Automate identity lifecycle management
Effective IAM practice involves the meticulous management of user identity lifecycles, an ongoing process encompassing the entire user journey within an organization, from creation and access assignment to review, potential updates, and eventual deactivation or removal upon departure.
Entra ID offers identity management features, including user provisioning and de-provisioning capabilities. As an IT admin, you would use the user provisioning feature to create and configure user identities within Entra ID. This process is essential for onboarding new employees or granting access to other users within the organization. On the other hand, de-provisioning is equally critical as it involves removing user access when it is no longer required. This step is particularly important when an employee leaves the company, or access must be revoked for security reasons. De-provisioning ensures that former employees or users can no longer access sensitive data or resources, reducing the risk of unauthorized access and data breaches.
While Entra ID provides the necessary tools for managing the identity lifecycle, manual management of these processes, especially in large organizations, can be complex, time-consuming, error-prone, and require technical expertise. This can leave your environment vulnerable to security risks associated with stale or unused accounts.
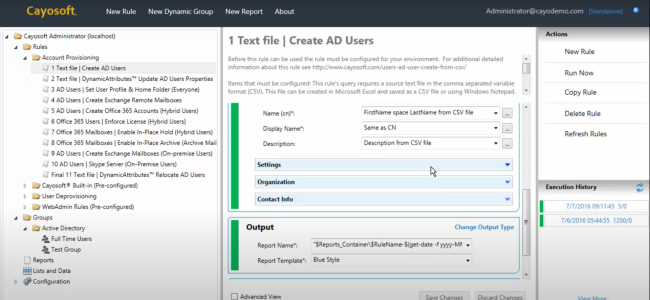
Cayosoft Administrator provides powerful automation capabilities for identity lifecycle management. It integrates seamlessly with Microsoft Entra ID and features Rule-Based Administration (RBA), allowing you to automate routine and complex identity management tasks efficiently. Additionally, Cayosoft Administrator fully automates account provisioning and de-provisioning by integrating with HR systems and third-party data sources. Using Cayosoft Administrator, you have access to a user-friendly interface that allows you to:
- Define automated workflows for user provisioning and de-provisioning by synchronizing with virtually any HR/ERP system and triggering a workflow based on predefined criteria like changes in an employee’s HR record
- Automate access control assignments based on user roles and department affiliations, ensuring users have the least privilege necessary for their tasks
- Schedule regular reviews to identify and automatically remove stale user accounts or unused permissions, further tightening security
Administrators should leverage Entra ID’s features and Cayosoft Administrator’s automation capabilities to significantly reduce manual errors, improve security, and enhance compliance with regulatory requirements. Automating identity lifecycle management increases operational efficiency and strengthens overall security posture by ensuring that access rights are granted and revoked in a timely and controlled manner.
#3 Enforce Multi-factor Authentication (MFA)
Multi-factor authentication (MFA) is a security measure requiring users to provide two or more verification factors to access a resource, such as an application, online account, or a VPN. By combining something the user knows (like a password) with something they have (like a phone or security token) or something they are (like a fingerprint), MFA significantly enhances security by adding an extra layer of protection against unauthorized access. This additional step makes it more challenging for attackers to compromise accounts, even if they have obtained login credentials.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
In Microsoft Entra, various methods are available to implement MFA to secure user accounts. Each method offers different levels of security and user experience, allowing organizations to choose the most suitable option based on their security requirements and user preferences. These methods include:
- Microsoft Authenticator
- Authenticator Lite (in Outlook)
- Windows Hello for Business
- FIDO2 security key
- OATH hardware token (preview)
- OATH software token
- SMS
- Voice call
Conditional access in Microsoft Entra allows organizations to define policies that control access to resources based on specific conditions, such as user location, device compliance, or risk level. Enforcing MFA through Conditional Access prompts users to provide additional verification when accessing sensitive data or applications based on predefined criteria. For instance, users can sign in without MFA when on the corporate network or using a registered device. However, they will be prompted for additional verification if they work remotely, use a personal device, or attempt to access a sensitive resource.
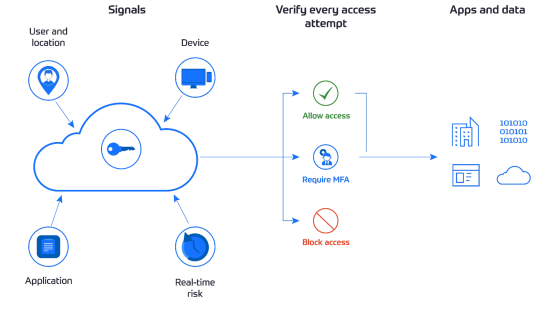
Enforcing MFA for all users adds a critical security layer and reduces the risk of unauthorized access by requiring a second factor, like a code from a phone app or security key. This second factor confirms the user’s identity, making it harder for attackers to gain access even if they have obtained the user’s password.
Watch demo video of Cayosoft’s hybrid user provisioning
#4 Implement Role-based access control (RBAC)
Role-based access control (RBAC) is a security model that assigns permissions to users based on their roles within an organization. With RBAC, users only have access to the resources and data necessary to perform their tasks, following the principle of least privilege. By granting access based on roles, organizations can minimize the risk of unauthorized access and data breaches by restricting permissions to what is essential for each user’s role.
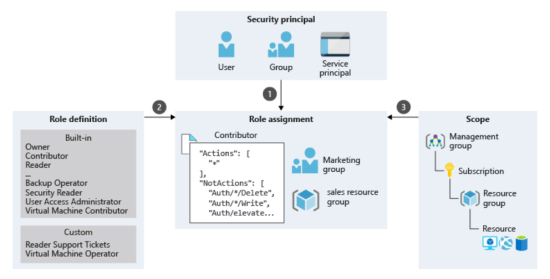
In Entra ID, RBAC is a fundamental feature that allows organizations to manage access to Entra ID services like Microsoft 365 by utilizing concepts like security principal, role definitions, scopes, and role assignments.
- Security Principal: this component represents a user, group, service principal, or managed identity that requests access to Azure resources. It is the entity seeking permission to perform actions on resources
- Role Definition: a role definition, often referred to as a role, is a collection of permissions specifying the actions that can be performed, such as read, write, or delete. Roles can be high-level (e.g., Owner) or specific (e.g., Virtual Machine Reader), and role definition dictates what a user can do within Azure
- Scope: the scope defines the set of resources to which access applies. It establishes the boundary within which the permissions granted by a role are effective. Scopes can range from a subscription to a resource group or even a single resource
- Role Assignment: a role assignment links a role definition to a security principal at a specific scope. It is the mechanism through which users or groups are granted permissions based on their organizational roles
By implementing the principle of least privileges, RBAC minimizes the potential damage caused by compromised credentials. Also, managing access through predefined roles simplifies administration, reduces the risk of accidentally granting excessive permissions to users, and aligns with best practices.
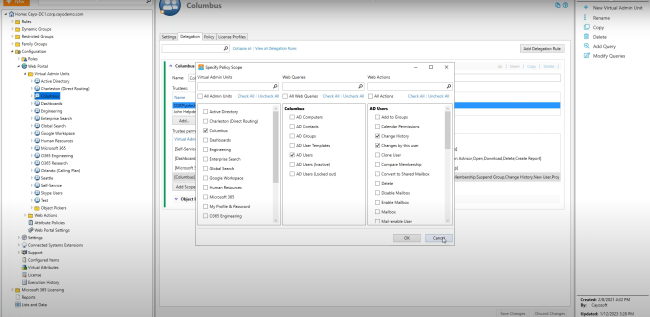
While Entra ID offers predefined roles, granting highly granular permissions for specific tasks can be challenging. This might lead to assigning broader roles than necessary, potentially granting more access than intended. Cayosoft Administrator simplifies the implementation of RBAC by providing automation features to manage user permissions and allowing IT admins to delegate roles more precisely. It even breaks down the least-privileged administrative role in Microsoft Entra into more specific and granular roles.
Cayosoft Administrator provides a visual representation of role permissions, making it easier to understand what access each role grants to users. IT admins can also leverage a checklist interface to assign roles to users and groups, simplifying access management and reducing the risk of errors. Using Cayosoft Administrator to leverage RBAC allows you to overcome these limitations and achieve fine-grained access control. This combination empowers IT admins to strike a balance between security and efficiency.
#5 Monitor and audit user activity and review access permissions
Maintaining a secure and compliant Azure environment requires constant vigilance, including monitoring user activity and access logs. These logs provide valuable insights into user behavior, access patterns, and potential security incidents. By closely monitoring user activity, organizations can detect and respond to suspicious or unauthorized access attempts, mitigate the risk of data breaches, and ensure adherence to regulatory requirements.
Microsoft Entra provides monitoring and auditing features that give IT admins a comprehensive view of identity-related activity in their environment. These features enable you to understand how users access and utilize apps and detect potential security risks. As an IT admin, you can generate reports that show detailed activity logs, including login attempts, password changes, and role assignments. These reports can be reviewed to detect unusual activity, such as multiple failed login attempts, which could indicate a brute-force attack.
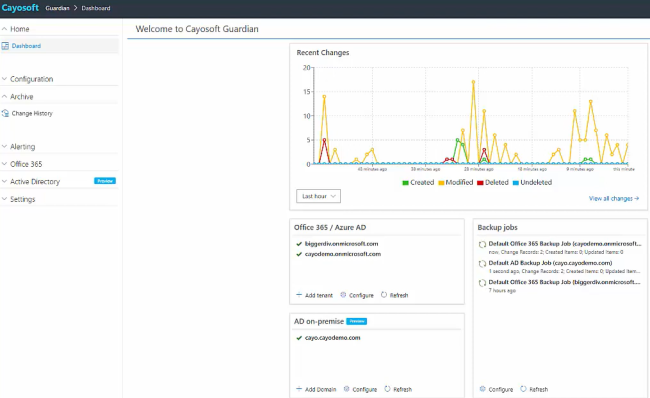
In addition to Microsoft Entra ID’s built-in reporting and auditing capabilities, tools like Cayosoft Guardian can enhance your ability to monitor user activity and review access permissions.
Cayosoft Guardian provides real-time monitoring and alerting for Microsoft Entra ID, helping you quickly detect and respond to security threats. It provides the following key features:
- Unified reporting: Cayosoft Guardian consolidates activity logs from multiple sources, including Entra ID, AD, and other cloud services, into a single, comprehensive reporting interface.
- Advanced alerting and notifications: The tool can be configured to generate alerts based on predefined rules, such as suspicious user activities or changes to critical resources, ensuring that security teams are promptly notified of potential issues.
- Automated access reviews: Cayosoft Guardian streamlines the process of reviewing and validating user access permissions, helping organizations maintain the principle of least privilege and ensure that access rights are aligned with business requirements.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Securing access to critical resources in your Azure environment is paramount, and as we have explored, implementing robust IAM best practices is fundamental to achieving this goal. In this article, we highlighted the critical role of IAM in securing Azure environments. We outlined best practices that should be implemented to significantly enhance your Azure security posture and minimize the risk of unauthorized access.
Remember, a robust identity management strategy is not just about securing your Azure environment—it’s about enabling your organization to operate more efficiently and effectively in the cloud.
To know more about how Cayosoft’s Administrator and Guardian can provide advanced capabilities for managing identities and access rights, automating identity lifecycle management, and monitoring user activity, request a free personalized demo here.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content