Home » Five Critical Azure Security Best Practices for Effective Risk Management » Azure Application Security Groups: Best Practices for Granular Network Control and Security
Azure Application Security Groups: Best Practices for Granular Network Control and Security
Learn the best practices for effectively utilizing Azure application security groups to enhance network security and flexibility in cloud deployments.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Cloud deployments have revolutionized how organizations manage their infrastructure and applications. They have quickly become the new business normal because they offer scalability, flexibility, and cost-effectiveness. However, as these deployments grow in scale and complexity, a robust security strategy is necessary to safeguard valuable data and services within these dynamic cloud environments. This is important because the ability to manage and control network traffic lies at the heart of cloud security.
Traditional network security often focuses on IP addresses and subnets to manage access. However, as applications evolve and scale, this approach can become difficult to manage and maintain, potentially leading to errors. Azure security groups (ASGs) offer a more flexible and efficient solution. By operating at the transport layer, ASGs enable administrators to define security policies based on application logic and workload. This simplifies network security rules management and allows for a more adaptable and application-centric approach to security.
This article explores Azure application security groups, how they enable organizations to achieve a more refined and targeted approach to network security, and best practices and practical insights for leveraging this feature in your cloud environment.
Summary of key application security group best practices
This table summarizes the five best practices to consider when working with ASGs.
| Best practice | Description |
|---|---|
| Plan and design ASGs upfront. | Define a clear strategy for grouping cloud resources based on security needs. |
| Create ASGs for different application tiers. | Create distinct ASGs for various application tiers to enforce granular access and segmentation. |
| Maintain clear naming conventions. | Use descriptive names for ASGs and rules for clarity and easy management. |
| Implement the principle of least privilege. | Grant access only to the required ports and protocols. |
| Audit and review your ASGs | Regularly review and update security rules to reflect changes in your environment. |
Effortless Azure AD Management & Security
Gain full control over Azure AD with Cayosoft Administrator — automate tasks, enforce policies, and strengthen overall security without complexity.
Understanding Azure application security groups
Before we delve into the Azure application security group best practices, it’s important to establish a solid understanding of what ASGs are, how they function and the distinction between ASGs and network security groups (NSGs). The sections below will explain these concepts in depth.
What is an Azure application security group?
An Azure application security group is a network security feature that enhances the flexibility and granularity of network traffic control within Azure environments. They operate at the transport layer (Layer 4) and allow granular control over network traffic between different tiers of an application. It enables you to group various resources, such as containers, virtual machines, databases, and web services, based on their roles or functions within your application and define security policies based on these groups. So, instead of configuring and managing network security rules for each resource, you can apply security rules to the entire group.
Azure ASGs vs. NSGs
An ASG should not be confused with a Network Security Group (MSG). NGSs act as basic, stateful, and flexible firewalls for controlling inbound and outbound network traffic. They operate at the network layer (Layer 3) and the transport layer (Layer 4). Unlike ASGs, NSGs are not specifically designed to manage application tiers. Instead, they provide network-level security by controlling traffic flow within subnets, between subnets, and between virtual networks.
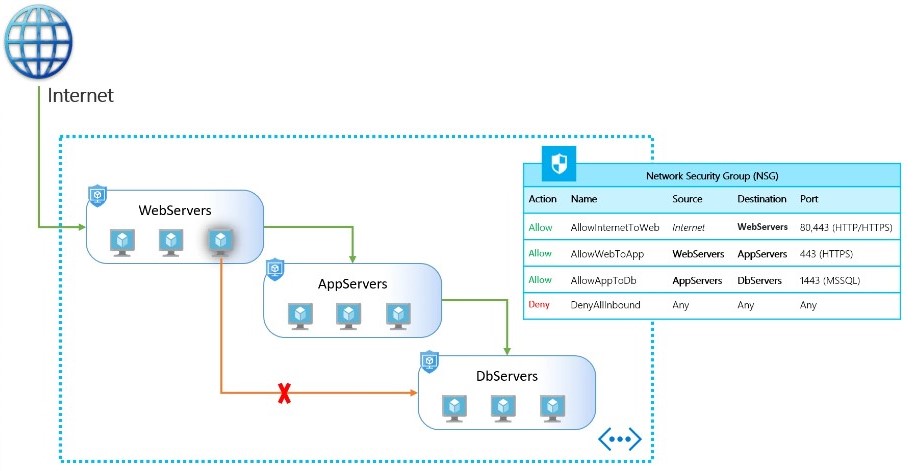
Think of Azure’s network security model as a layered cake. At the base layer sits the virtual network, which defines the overall network space for your Azure resources. Next is the NSG layer, which acts as a firewall that controls inbound and outbound traffic to specific subnets within the virtual network. NSGs use rules that allow or deny traffic based on source/destination IP addresses, ports, and protocols. Finally, we have the ASGs. They reside within the NSG layer, functioning as a sub-layer for defining even more granular security policies. Let’s take virtual machines (VMs) as an example; instead of managing security rules for individual VMs with dynamic IP addresses, ASGs let you group VMs based on their function (web server, database server, etc.) and apply security policies to the entire group. This simplifies management and ensures consistent security across all VMs within the same application tier.
How to create and manage Azure application security groups
Setting up and maintaining ASGs is straightforward. The process involves creating ASGs, configuring their security rules, and associating relevant resources. You can create an ASG using the Azure Portal, Azure CLI, or Azure Powershell.
The examples below will use the Azure Portal method because it provides a straightforward experience for creating and managing ASGs.
Creating an ASG in Azure Portal
- Search for Application Security Groups: In the search box at the top of the portal, type “Application security group” and select Application security group from the results.
- Select “+ Create”.
- Provide Details: Fill in the required details, such as the subscription, resource group, region, and ASG name.
- Review and Create: Review the configuration and click “Create” to finalize the process.
Unlock the Full Potential of Azure Network Security Groups
Understand how to configure and secure Azure NSGs to strengthen your cloud defense and prevent vulnerabilities.
Configuring security rules for an ASG
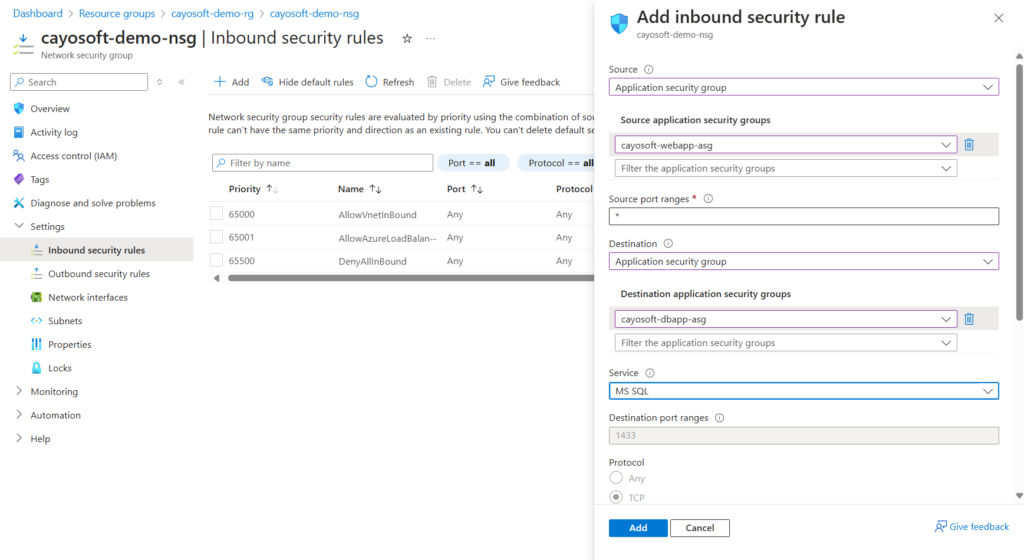
- Create or Select an NSG: If you don’t have an NSG, create a new one by clicking “+ Create” and filling in the required details.
- Add security rules: In the selected NSG, go to “Settings,” and depending on the direction of traffic you want to control, select either “Inbound security rules” or “Outbound security rules.”
- Click “+ Add” to create a new security rule.
- Specify Details: In the rule creation blade, specify the following:
- Source: Select the ASG you have created.
- Source port ranges: Specify the source port ranges.
- Destination: Select the destination ASG or a specific IP address range.
- Destination port ranges: Specify the destination port ranges.
- Protocol: Choose the protocol (TCP, UDP, or Any)
- Action: Select an action, “Allow” or “Deny.”
- Priority: Set the priority for the rule (lower numbers have higher priority).Specify Details: In the rule creation blade, specify the following:
- Name: Enter a name for the rule
- Save the Rule: Save the rule to apply it to the ASG.
Associating resources with an ASG
To apply security policies, you need to associate your resources with the ASG you’ve created.
- Select the resource: In the Azure portal, search for and select the resource (e.g., a virtual machine) you want to associate with the ASG.
- Configure Networking: Go to the “Networking” section in the selected resource settings.
- Select the “Network interface” associated with the selected resource.
- Click on “Configure the application security groups” and select the ASG(s) you want to associate with the network interface.
- Click on Save to apply the changes.
Benefits of using Azure application security groups
Now that you understand the basics of Azure application security groups, let’s review the advantages of using ASGs:
- Fine-grained network security policies: ASGs enable you to define network security policies with unprecedented precision. Instead of applying broad rules to entire subnets, you can tailor rules based on the specific applications or services running in your cloud environment.
- Granular control over network traffic: ASGs allow you to gain meticulous control over network traffic flow between resources by defining rules based on source and destination ASGs. This means you can specify which resources are allowed to communicate with each other and under what conditions.
- Improved isolation and protection: ASGs enhance the isolation and protection of application workloads. By segmenting your network based on application function, you create separate security zones, which limit the potential impact of security breaches by preventing lateral movement within the network.
- Simplified security definition: ASGs simplify defining security policies by allowing you to define rules at the group level. This approach reduces the number of rules you need to maintain. Additionally, as your application scales, you can easily add new resources to the appropriate ASG, and they will automatically inherit the relevant security policies.
- Zero-trust model implementation: ASGs align seamlessly with the zero-trust principle. By default, no traffic is allowed between ASGs unless explicitly permitted. This approach assumes that no entity can be trusted implicitly, whether inside or outside the network. Every request must be verified before access is granted.
- Enhanced security layers: By combining ASGs with NSGs, you can create multiple layers of security that protect your network from various threats. NSGs provide broad network-level security, while ASGs offer more granular, application-centric security. This layered approach ensures comprehensive protection for your cloud environment, addressing both external and internal threats,
Considerations and best practices when using ASGs
While Azure Application Security Groups (ASGs) offer significant advantages, it’s important to be mindful of certain considerations and follow best practices to maximize their effectiveness.
Azure application security group limitations
Azure application security groups can help improve your Azure security posture, but they also have limitations. Two of the biggest ASG limitations are:
- Subscription limits: Azure placed a limit of 3000 ASGs per subscription, and a maximum of 10 ASGs can be referenced as source/destination per NSG rule.
- Limited to a virtual network: ASGs can only be associated with resources within the same virtual network (VNet). If your resources span multiple VNets, you must create separate ASGs for each VNet.
Five essential Azure application security group best practices
To effectively leverage ASGs in your Azure environment, consider the following best practices:
Plan and design ASGs upfront
Before implementing ASGs, define a clear strategy for grouping cloud resources based on security needs. This proactive approach ensures that your ASG structure aligns with your security strategy and application architecture. Consider factors such as application tiers, data sensitivity, and access requirements when planning your ASG design.
Create ASGs for different application tiers
Create distinct ASGs for each tier of your application (e.g., web, application, database). This separation allows for more granular control over network traffic and enhances security by limiting lateral movement within your network.
Maintain clear naming conventions
Use descriptive names for your ASGs and security rules. For example, instead of “ASG1”, use names like “WebServerASG” or “DatabaseASG.” This naming convention improves clarity and makes managing and troubleshooting your network security configuration easier.
Implement the principle of least privilege
Apply the principle of least privilege when defining security rules. Only allow the minimum necessary access required for each application component. This approach minimizes the potential attack surface and reduces the risk of unauthorized access.
Third-party tools like Cayosoft Administrator can be particularly helpful in implementing least privilege access. Although it does not directly manage ASGs, by enabling granular, role-based access control, Cayosoft Administrator allows you to define and enforce precise permissions across your cloud environment. This means that only authorized personnel can make changes to cloud resources, including ASGs.
Audit and review your ASGs
Security requirements change over time, so it is important to review and update your security rules regularly. Solutions like the Cayosoft platform can effectively minimize security risks and exposure by employing a delegation security model that eliminates the need for extensive native privileges and audits to detect malicious activities..
Discover Key Azure Security Strategies for Risk Reduction
Learn key tactics for securing your Azure environment — covering identity protection, threat detection, and compliance enforcement.
Conclusion
Azure Application Security Groups represent a powerful and flexible approach to network security in cloud environments. By enabling granular, application-centric control over network traffic, ASGs significantly enhance the security posture of Azure deployments.
When combined with Network Security Groups (NSGs), ASGs provide a robust, layered security model that can adapt to the evolving needs of modern cloud applications. The ability to group resources logically, apply consistent security policies, and dynamically update configurations makes ASGs an essential tool for implementing the principle of least privilege and maintaining a strong security stance in Azure.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content