Home » Five Critical Azure Security Best Practices for Effective Risk Management » Azure AD Password Policy: Master the Essentials for Enhanced Security
Azure AD Password Policy: Master the Essentials for Enhanced Security
Learn about the importance of Microsoft Azure AD (Entra ID) password policies and how to customize them for optimal security and usability.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
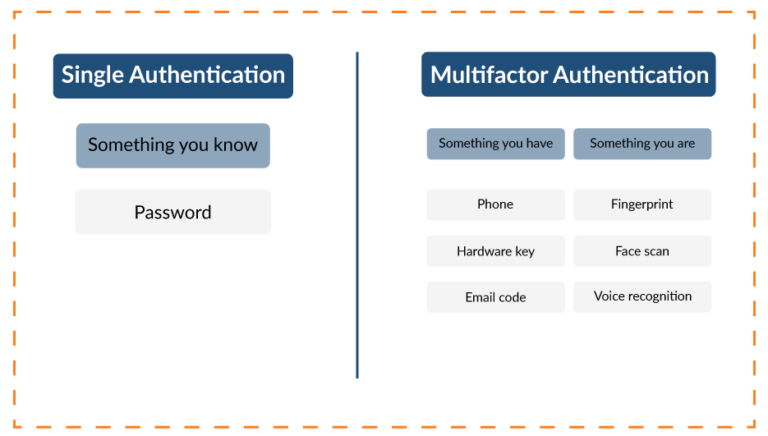
One of the main functions of Microsoft Azure AD (Entra ID) is user authentication, and passwords are the primary authentication method. As a result, passwords are the first line of defense against unauthorized access.
Microsoft developed Azure AD (Entra) password policies to ensure users follow industry best practices for password complexity, length, and age. Administrators can enable features like multi-factor authentication and conditional access to bolster security. Passwordless authentication is an alternative to MFA and is gaining momentum because it provides a more seamless user experience. Getting these Azure AD password policy settings right can help organizations strike the right balance between security and usability.
This article reviews the default Azure AD password policy and what your organization can customize. We also cover common password hacking tactics and review Azure AD password policy best practices such as self-service password reset, multi-factor authentication (MFA), and passwordless authentication.
Summary of key Azure AD password policy concepts
The table below summarizes the Azure AD password policy concepts and best practices this article will explore in more detail.
| Concept | Description |
|---|---|
| Understand how passwords get hacked | Microsoft has experience protecting millions of user accounts against password attacks, and this experience led to the Azure AD password policy. Unfortunately, password-only authentication is vulnerable to breach, phishing, malware, social engineering, and hammering attacks. |
| Default Azure AD password policy | Microsoft cloud-only accounts use a predefined password policy that follows recommended best practices, such as passwords being at least eight characters long and not expiring. |
| Eliminate weak passwords | Banning common passwords is highly effective in preventing users from using weak passwords. Requiring users to change their passwords can lead to weaker password use. |
| Provide self-service password reset | Users will inevitably forget their passwords. Self-service password reset helps users regain access without burdening administrators or help desk staff. |
| Enable multi-factor authentication (MFA) | MFA is a robust defense mechanism against most password attacks. Combining MFA with conditional access policies can improve security and maintain a streamlined sign-in experience. |
| Consider passwordless authentication | Passwordless authentication replaces passwords with safer authentication factors. The Microsoft Authenticator application provides a passwordless capability for Microsoft Entra ID tenants. |
Strengthen Your Hybrid Active Directory Security with Cayosoft Guardian.
Monitor and protect your Active Directory with real-time change tracking and instant recovery. Enhance your password policies and safeguard privileged accounts effectively.
Understand how passwords get hacked
Microsoft sees over 10 million username/password pair attacks daily, giving them a unique vantage point to recommend how to protect passwords. The following table summarizes various types of password attacks using these parameters:
- Frequency – indicates how common the tactic is
- Efficacy – indicates how effective the tactic is
- The remaining columns indicate whether using unique, long, or complex passwords, rotating passwords, or MFA is effective against a tactic.
| Tactic | Description | Frequency | Efficacy | Unique | Long | Complex | Rotate | MFA |
|---|---|---|---|---|---|---|---|---|
| Breach | An individual or group steals sensitive data, including username and hashed password information. | 90% | ↑↑ | Yes | Yes | Yes | No | Yes |
| Phishing | Websites masquerading as trustworthy entities to lead you to divulge sensitive information. | 9% | ↑↑ | Yes | No | No | No | Yes |
| Malware | Malicious software that spies on you and can include keystroke logging. | ↑↑ | Yes | No | No | No | Yes | |
| Social engineering | Pretending to be a support agent to obtain sensitive information from you. | <1% | ↓ | Yes | No | No | No | Yes |
| Hammering | Hackers take a common list of passwords and try them against a list of user accounts. | ↓↓ | Yes | Yes | Yes | No | Yes | |
| Spear phishing | Hackers craft messages to lure you into downloading malicious software or visiting a malicious link. | ↑↑ | Yes | No | No | No | Yes | |
| Proof compromise | Your alternative email or phone is hacked, meaning your MFA is compromised. | ↑↑ | No | No | No | No | No |
Table summarizing the various types of password attacks. (Source)
How to create strong passwords
Microsoft AD (Entra) recommends that administrators avoid following these anti-patterns and follow these successful patterns.
| Anti-patterns | Successful patterns |
|---|---|
|
|
Default Azure AD password policy
Microsoft cloud-only accounts use a predefined password policy that administrators cannot change. The only items you can change are the password expiry duration in days and whether or not passwords expire.
The following default Azure AD password policy applies to all user accounts in Microsoft Entra ID. The password policy can also be applied to user accounts synchronized from an on-premise AD DS environment using Microsoft Entra Connect by enabling the EnforceCloudPasswordPolicyForPasswordSyncedUsers setting.
The Azure AD default password policy aligns with Microsoft’s password guidance, and we recommend that you follow it.
| Password property | Password requirements |
|---|---|
| Characters allowed | A – Z a – z 0 – 9 @ # $ % ^ & * – _ ! + = [ ] { } | \ : ‘ , . ? / ` ~ ” ( ) ; < > Blank space |
| Characters not allowed | Unicode characters |
| Password restrictions | A minimum of 8 characters and a maximum of 256 characters. Requires three out of four of the following types of characters: – Lowercase characters – Uppercase characters – Numbers (0-9) – Symbols (see the previous password restrictions) |
| Password expiry duration (Maximum password age) | Default value: 90 days. If the tenant was created after 2021, it has no default expiration value. |
| Password expiry (Let passwords never expire) | Default value: false (indicates whether passwords have an expiration date). |
| Password change history | The last password cannot be reused when the user changes a password. |
| Password reset history | The last password cannot be reused when the user resets a forgotten password. |
Default Azure AD password policy (Source)
Organizations can further enhance security by focusing on:
- Educating users to use unique passwords across their online accounts, especially for your organization
- Implementing MFA
- Using passwordless authentication
Implement Fine-Grained Password Policies.
Discover how to apply fine-grained password policies to secure privileged accounts in Active Directory environments.
Provide self-service password reset
Enabling users to change or reset their passwords reduces the burden on administrators and help desk staff. Instead of logging a support ticket, a self-service password reset allows users to unblock themselves and return to work.
Self-service password reset scenarios
The following table outlines three self-service password reset scenarios and which Microsoft Entra ID license is required.
| Feature | Microsoft Entra ID Free | Microsoft 365 Business Standard | Microsoft 365 Business Premium | Microsoft Entra ID P1 or P2 |
|---|---|---|---|---|
| Cloud-only user changing their password | ● | ● | ● | ● |
| Cloud-only user resetting a forgotten password | ● | ● | ● | |
| A user synchronized from an on-premises directory trying to change or reset their password. | ● | ● |
The table outlines different select-service password reset scenarios. (Source)
Cayosoft Administrator for robust self-service password reset
Cayosoft Administrator provides complete capabilities for self-service password reset in cloud and hybrid Microsoft AD environments. A significant source of frustration for users, administrators, and help desk staff is dealing with expired passwords and account lockouts. Cayosoft Administrator provides the capability to send:
- Password expiration notification to users
- Account lockout notification alerts for administrators and help desk
These notifications help to reduce help desk calls/tickets by reminding users to make changes themselves.
Eliminate weak passwords
Bad actors exploit weak passwords because they include common phrases, predictable patterns, or widely used combinations.
The most common weak passwords include:
- 123456
- password
- qwerty123
Using weak passwords leaves your users open to password spray attacks. These attacks use a few commonly used passwords against many accounts. Targeting many accounts with only a few password attempts minimizes the chance of triggering account lockouts. To protect your organization against these attacks, block weak passwords and create a custom banned password list.
Block weak passwords
Microsoft Azure AD (Entra ID) Password Protection detects and blocks known weak passwords, and you can customize them with your own banned password list. We recommend that this includes terms specific to your organization, such as:
- Brand names
- Product names
- Locations, e.g., the company HQ
- Company-specific internal terms and abbreviations
Custom banned password list
Organizations using Microsoft Entra ID already benefit from Microsoft’s global banned password list. To enable a custom banned password list, visit the Microsoft Entra admin center and then:
- Browse to Protection
- Authentication methods, then Password protection
- Set the option to Enfore custom list from No to Yes
- Add strings per line to the Custom banned password list
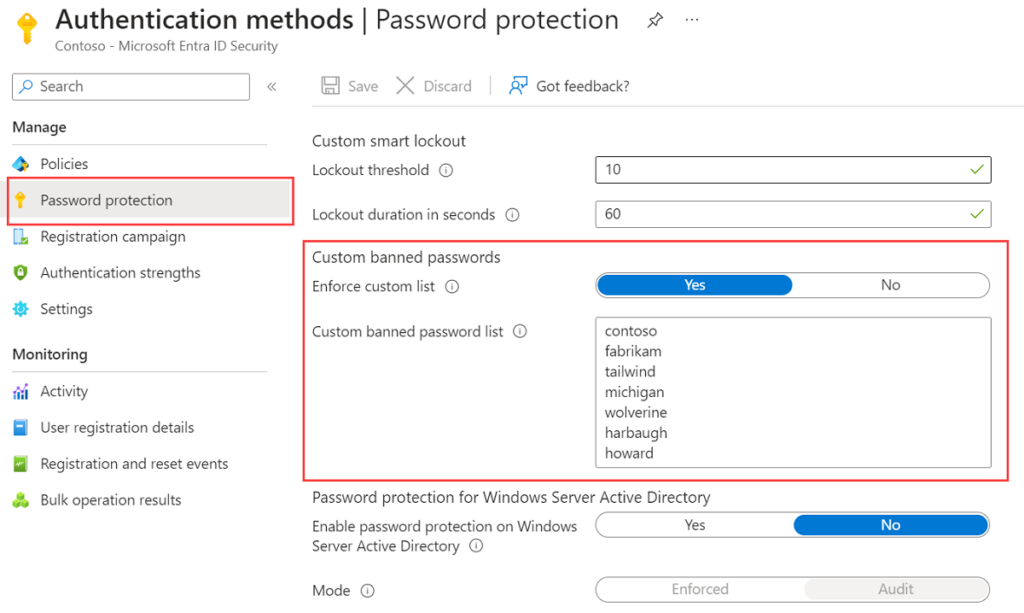
Administrators can add 1,000 terms to the custom banned password list. Remember that the list is case-insensitive, and Microsoft’s password validation algorithm blocks weak variants and combinations. Your custom banned password list should only include key base terms. For example, for the base term “michigan” variations like mIchIgAn, michigan@, MichiganHQ or !Michigan will also be blocked.
In a hybrid environment, you can extend the security benefits of Microsoft Entra Password Protection into your AD DS environment.
Cayosoft password enforcement and protection
Third-party tools like Cayosoft Administrator enable you to enforce stronger password policies for privileged accounts, which may be required by your organization’s security team or industry compliance requirements.
Cayosoft Guardian will identify privileged accounts with weak password policies in on-premise AD, hybrid AD, and cloud Entra ID environments. Furthermore, Cayosoft Guardian actively monitors for password-based attacks, like password spray attempts.
Enable multi-factor authentication
Password-only authentication leaves your organization vulnerable to password-based attacks against your user accounts. Multi-factor authentication (MFA) safeguards against password attacks by requiring a second form of authentication. However, even with MFA enabled, you must educate your users to avoid them being tricked into accidentally approving MFA requests. MFA fatigue or MFA bombing attempts to trick users into approving requests, and the Microsoft Digital Defense Report 2023 reported approximately 6,000 MFA fatigue attempts per day. Even so, based on Microsoft’s studies, your account is more than 99.9% less likely to be compromised if you use MFA.
Security defaults
A quick way to benefit from MFA is to enable security defaults in Microsoft Entra ID, which allows MFA via Microsoft Authenticator for all users. Security defaults is a preconfigured security feature that is available to Microsoft Entra ID Free tenants.
While this is a convenient way to benefit from MFA, you need to consider whether all of your users can use MFA. Some users may be restricted from carrying a mobile device. Furthermore, emergency access and service principals should be excluded from requiring MFA. Replace service principals in scripts and code with managed identities to handle credentials automatically.
Microsoft Entra Conditional Access requires a Microsoft Entra ID P1 or P2 license. A basic level of security is available via security defaults for free to cover the following scenarios:
Specific users
MFA can be enabled for specific users and is available to Microsoft Entra ID Free tenants. If your organization has only a small number of users, this is a viable approach to benefit from MFA and control which user accounts it applies to.
Conditional access policies
Conditional access policies, which consist of assignments and access controls, provide a flexible way to decide whether MFA is required to authenticate a user.
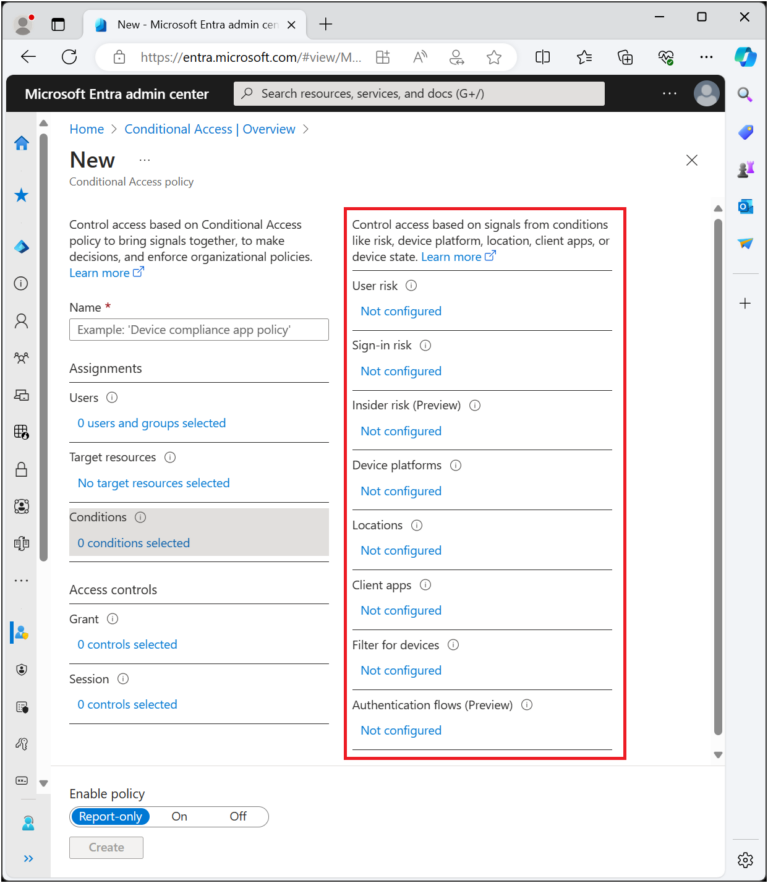
- Assignments control which users, applications, devices, and locations the policy applies to. The assignments also include conditions that control whether the policy is used or not. For example, a conditional access policy can be applied only to guest users within your Microsoft Entra ID tenant or users identified as a risky sign-in.
- Access controls are split into grant, block, and session options.
- Grant enforces one or more controls when granting access. For example, Require multifactor authentication (Microsoft Entra multifactor authentication)
- Block prevents a user from signing in. For example, you can block access when a user uses a legacy authentication method to sign in.
- Session enforces restrictions within specific cloud applications. For example, you can block the download, cut, copy, and print of sensitive documents from unmanaged devices like an employee’s personal PC.
Conditional Access requires a Microsoft Entra ID P1 or P2 license. Microsoft provides several conditional access policy templates.
Cayosoft streamlines Microsoft Entra ID management and recovery
Cayosoft provides a unified solution for securing and managing all your Microsoft Entra ID directories and reporting on users’ MFA status. To help you monitor MFA enrollment, a report of users and MFA status can be created on a schedule.
In addition, Cayosoft Guardian delivers real-time monitoring capabilities and provides administrators with detailed logs to understand unauthorized actions. These logs can help develop conditional access policies.
Cayosoft Guardian provides recovery of conditional access policies. Whether changes are made by accident or malicious actors, Cayosoft Guardian can restore a previous good state to Microsoft Entra ID. This functionality is not available natively in Microsoft Entra ID, if a conditional access policy is accidentally changed or deleted it is treated as a hard deletion.
Consider passwordless authentication
Given all the issues with passwords and the various ways bad actors look to exploit password-protected systems, passwordless authentication is gaining momentum because it combines high security with convenience. Meanwhile, MFA can frustrate users because it requires a second step before sign-in.
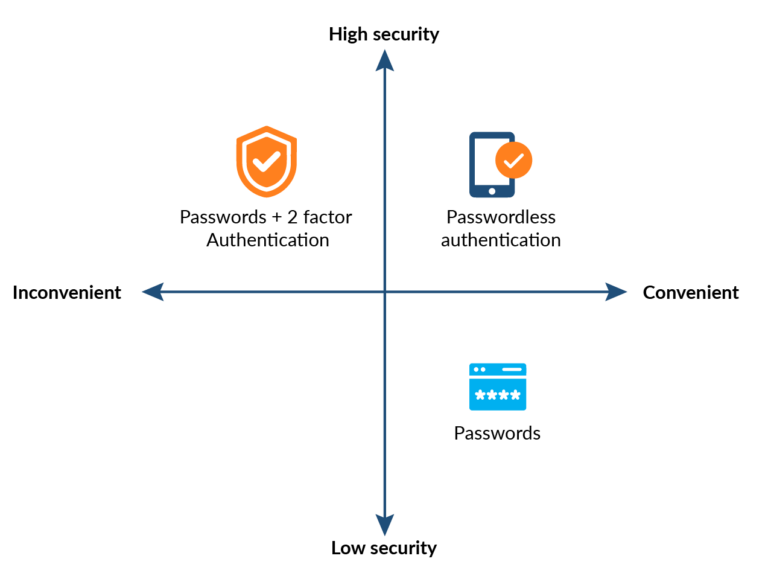
Passwordless authentication replaces passwords with either a:
- Windows 10 Device, phone, or security key
- Biometric or PIN
Microsoft Entra ID has the following passwordless authentication options:
- Windows Hello for Business
- Platform Credential for macOS
- Platform single sign-on (PSSO) for macOS with smart card authentication
- Microsoft Authenticator
- Passkeys (FIDO2)
- Certificate-based authentication
Microsoft Authenticator
Using Microsoft Authenticator is a free and simple way to explore whether passwordless authentication is beneficial to your organization. Microsoft Authenticator enables your user’s phone to become a passwordless authentication device. A notification is sent to their phone, and an employee is granted access after matching a number displayed on the screen to one on their phone within the Authenticator app. To get started, follow the enable passwordless sign-in with Microsoft Authenticator guide.
Enable Self-Service Password Reset.
Reduce help desk calls and empower users by implementing self-service password reset capabilities.
Last thoughts on Azure AD password policy
Password fatigue is a reality due to the sheer number of online accounts an individual has. For organizations using Microsoft Entra ID with user passwords, the default Azure AD password policy follows industry password best practices. However, if your organization only uses password-based authentication, you are open to password-based attacks.
Educating your users to avoid reusing their passwords across multiple sites and eliminating weak, easily guessable passwords using Microsoft Azure AD (Entra ID) Password Protection will improve security against some password-based attacks. However, you should implement MFA via security defaults or conditional access policies to provide further security to your organization.
Passwordless authentication is an alternative to password-based systems. It brings the security benefits of MFA without the inconvenience of a multi-step sign-in process for your users.
Whatever your authentication approach, third-party tools like Cayosoft Administrator help improve the operational efficiency of your Azure AD (Entra) environments. Cayosoft Guardian also provides threat monitoring and restore capabilities not natively available in Microsoft Entra ID.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content