Home » Five Critical Azure Security Best Practices for Effective Risk Management » No More GPOs? Azure AD Group Policy for Modern IT
No More GPOs? Azure AD Group Policy for Modern IT
Learn about the effectiveness of Azure Security Defaults and how they should be supplemented with custom conditional access policies for robust security measures.
Explore the chapters:
Table of Contents
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
For decades, on-premises Active Directory (AD) device and configuration management has relied on Group Policy Objects (GPOs). These policies have been a powerful tool for Windows administrators to centrally control settings and security across their traditional domain-joined environments. However, traditional GPOs are less effective and practical for managing cloud-based Azure AD devices. Microsoft introduced Intune as a powerful cloud-based alternative to GPOs for managing devices joined to Azure AD.
In this article, we explore the differences between Azure AD, Azure AD on-premises, and Entra Domain Services. We’ll also delve into Microsoft Intune, discuss its role-based configuration policies, and the best practices for implementing group policies in modern environments.
Summary of best practices to implement Azure AD and Intune
The following table summarizes some best practices for implementing Azure AD and Intune.
| Best practice | Description |
|---|---|
| Avoid deploying all configurations into a single policy | It’s better to create modular policies in separate profiles—such as app management, security, and compliance—as this will help you exclude any user or device from the policy when needed. |
| Implement group policies based on user roles and device types | Apply policies according to their roles, as they allow you to implement different configurations to different groups of users according to their job functions. |
| Keep critical settings separate | Separate out critical settings, such as encryption, network configurations, and data protection policies, from non-critical settings to lower the risk of change implementations or updates. |
| Replace GPOs with PowerShell for advanced configurations | Leverage PowerShell scripts to automate tasks such as deploying applications, configuring custom policies on Windows devices, and remediating common device errors. |
Transitioning from GPOs to Intune configuration profiles
Managing devices in Azure AD is a bit different than the traditional on-premises world. Azure AD extends your on-prem AD to the cloud as a cloud-based control center for users and devices. While GPOs don’t directly apply to Azure AD, the recommended approach is to use Microsoft Intune to manage devices joined to Azure AD. Intune also lets you configure settings, deploy apps, and enforce security policies from the cloud.
For those with a hybrid environment, Microsoft offers hybrid Azure AD join to manage and join devices in both environments.
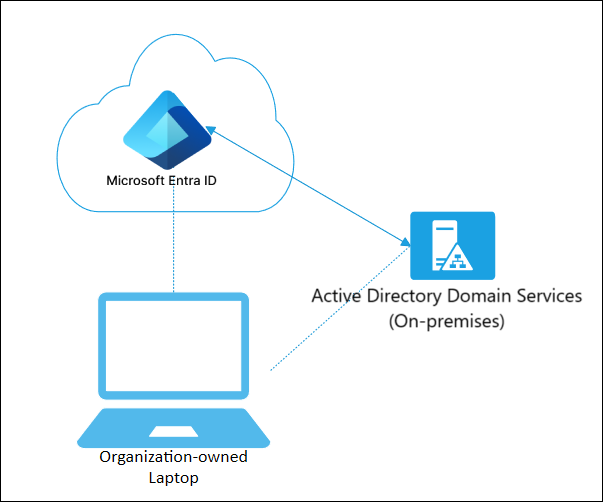
With hybrid Azure AD join, devices continue to function as domain-joined machines, receiving Group Policy updates, accessing on-premises resources like file shares, and utilizing Kerberos authentication for domain-joined applications. The same devices can also access cloud resources like Microsoft 365, utilize SSO for cloud apps, and be managed with Intune for things like conditional access policies.
Since devices can remain joined to your on-prem domain, GPOs can continue to apply and configure settings on the device. In instances where you need to enforce specific settings or configurations for your cloud-connected devices, you can also configure your Intune policies to override conflicting GPOs.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Comparing Azure AD, On-Prem AD, and Azure AD Domain Services (DS)
When businesses migrate from on-prem to Azure cloud, they must understand the difference between on-prem AD and the Azure AD and Azure ADDS identity services. The three services, while related, offer different capabilities when managing devices and deploying policies.
On-premises Active Directory (AD)
On-prem AD enables IT administrators to manage Windows devices and deploy central security policies using GPOs. Its integration with the Windows operating system makes it a valuable resource in domain-based environments, particularly for devices within a defined network boundary.
However, on-prem AD setups have significant architectural limitations in cloud and hybrid environments due to their lack of built-in support for managing devices outside the domain or across multiple platforms like iOS, Android, and macOS. Due to these limitations, organizations adopt cloud-based solutions like Azure AD and Intune to manage device security, identity, and configurations.
Azure AD
Azure AD (now Microsoft Entra ID) is a cloud-based identity and access management solution that controls access to cloud applications like Microsoft 365, Azure, and other SaaS platforms. It provides basic user authentication, group memberships, and role-based assignments but doesn’t support traditional GPOs.
Entra ID is considered ideal for organizations adopting a cloud-first strategy that needs identity management, SSO, and MFA to secure cloud infrastructure. However, it’s important to note that Entra ID, by itself, doesn’t provide the same level of granular device control that you might be used to with on-prem AD and GPOs. For such instances, a common recommendation is to integrate Entra ID with other cloud-based management tools like Microsoft Intune.
More details on device-based conditional access through Entra ID and Intune can be found here.
Azure AD Domain Services
Many organizations have applications that rely on traditional AD and GPOs, but they want to take advantage of the cloud. Microsoft Entra Domain Services (formerly Azure ADDS) is a managed service that allows you to use familiar GPOs to manage and configure devices and users even though they are in the cloud. The service provides domain-join capability, LDAP, Kerberos authentication, and even support for Group Policies in an Azure environment.
With Domain Services, you can simply lift and shift your domain-dependent applications to Azure and continue using GPOs to manage it, just like you did on-premises. It also works natively with your Microsoft Entra tenant, so the same users can access those apps with their usual logins, and you can use existing groups and user accounts to control access.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Microsoft Intune: Modern device management solution
Microsoft Intune offers a cloud-native approach to managing configurations, implementing security, and ensuring compliance across different devices, including Windows, iOS, Android, and macOS. Unlike on-premises AD and GPOs, Intune works seamlessly in the cloud, providing flexibility, scalability, and device-agnostic policy enforcement. It also ensures that all devices are managed from a single platform with advanced configuration options.
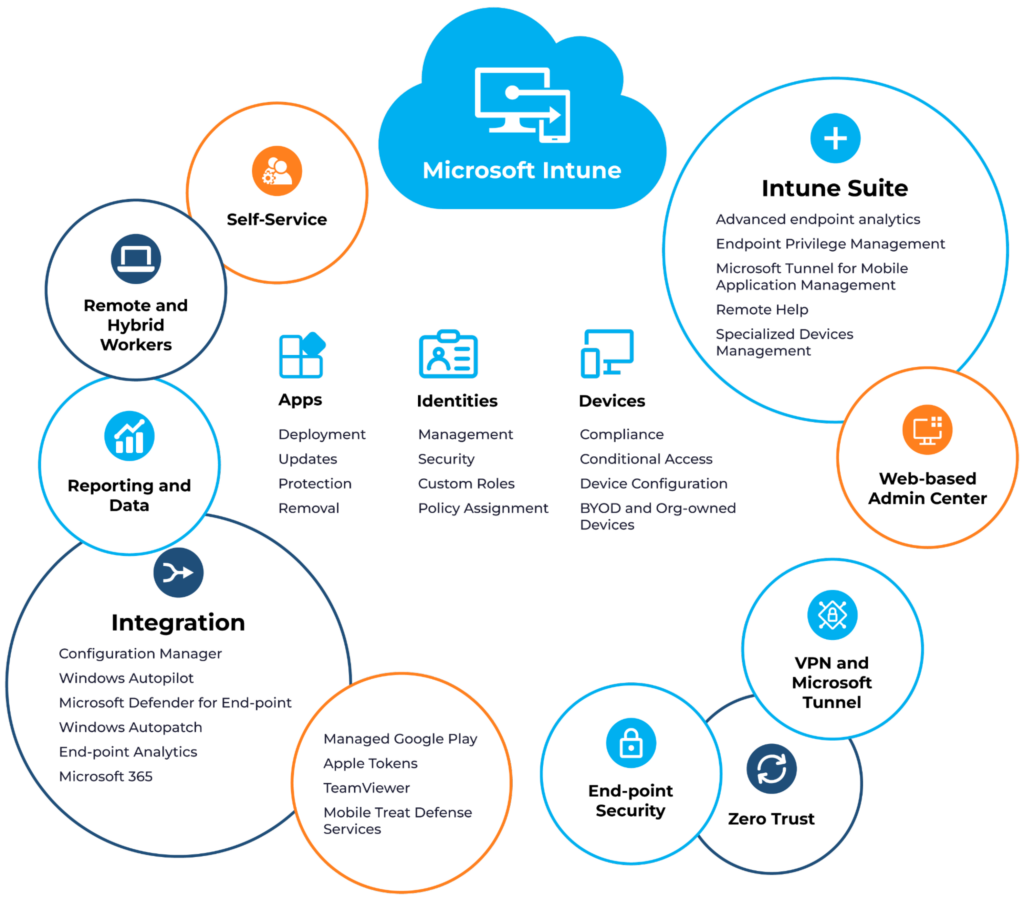
Intune creates and manages configuration profiles for various operating systems and device types. These profiles enable IT administrators to apply encryption, passwords, and application management policies. Here’s how Intune supports various devices:
- Windows devices: Intune integrates with Cayosoft Guardian, Windows 10, and Windows 11 devices, allowing configurations similar to GPOs. IT administrators can deploy policies for security, compliance, VPNs, and Wi-Fi configurations.
- Android devices: Intune supports Android device management, which allows organizations to create work profiles, enforce device-level encryption, and protect data.
- MacOS devices: Intune can also manage MacOS devices. You can implement security policies such as encryption, manage software updates, and set network settings.
Watch demo video of Cayosoft’s hybrid user provisioning
Role-based configuration profiles in Intune
Intune leverages Azure AD groups to help you create groups based on different criteria, including job roles, departments, and device types. In addition, you can create configuration profiles that define specific settings and restrictions for devices. The profiles utilize Open Mobile Alliance Uniform Resource Identifier (OMA-URI) settings to define device configurations, which are essentially key-value pairs that specify various aspects of device behavior and restrictions.
Once assigned to Azure AD groups, configuration profiles are automatically applied to devices when users enroll them in Intune. In cases where multiple policies apply to a device, Intune has a built-in conflict resolution mechanism that prioritizes policies based on factors like assignment type (user vs. device) and specificity (more specific policies take precedence).
Broad (less flexible) vs. tailored (more flexible) policies
You can enforce broad policies across all devices to ensure consistency, but this approach can lack flexibility and might not be suitable for all users or device types.
In contrast, creating tailored policies for specific groups or roles allows you to apply configurations based on the unique needs of different users or devices. For instance, field technicians might require different security policies than on-site employees. Tailored policies are also more effective for specific devices that might need custom configurations to support specialized applications.
Cayosoft Administrator can further enhance Intune’s capabilities by automating role-based device enrollment and policy assignment. As an outcome, you can streamline the process of deploying policies based on user roles or groups, reducing manual configuration and ensuring consistent enforcement.
Microsoft Intune provides security baselines and configuration profiles to ensure that devices meet strict security standards. With these profiles, IT administrators can enforce security policies to protect sensitive data and ensure compliance on various devices.
Security baselines for devices
Predefined security baselines offer a set of recommended security settings based on industry best practices and security standards like NIST or CIS benchmarks. For granular control, you can use configuration profiles to define and deploy specific security policies to different groups of devices.. Some of the key security policies include:
- Password enforcement: Enforce passwords on devices to prevent unauthorized access.
- Screen lock timeouts: Set screen lock timeouts to prevent data exposure when devices are unattended.
- Device encryption: Encrypt all company files to protect sensitive information from theft or loss.
Controlling app permissions and data sharing
With Intune, organizations can control how applications behave on a device. You can limit which apps can access company data and prevent unauthorized apps from sharing. For example, you can prevent users from copying company data from corporate apps like Outlook or Teams and pasting it into personal apps and services. This is often achieved through app protection policies in Intune, which can define data loss prevention (DLP) rules and restrict actions like copy-paste, sharing, and printing for specific applications.
When you apply these types of controls, it ensures that your sensitive information is kept within corporate-approved applications, and it reduces the risk of accidental or intentional data leaks.
Enforcing preferred encryption standards
Intune can configure VPN profiles and certificates to enforce SSL/TLS encryption and secure communication channels. With these security features, you can protect devices and ensure data security even when accessing from multiple devices and locations.
Best practices for implementing policies in Intune
The following are some best practices that help for grouping policies in Intune for better flexibility and control.
Avoid deploying all settings into a single policy
Deploying several configurations in a single monolithic policy can lead to high processing overhead on devices. Combining many settings within a single profile can also increase the risk of conflicts between OMA-URI settings, especially when dealing with different device platforms or versions.
It is better to create modular policies to improve the organization and readability of your Intune configurations. Separating configurations into profiles like security, compliance, and app management gives you more control over policy applications. Troubleshooting is also easier because you can narrow the issue to a specific policy.
Implement group policies based on user roles and device types
You can also group policies according to user roles or device types for more granular and effective policy enforcement. Creating role-based policies allows you to apply different configurations to groups of users based on their job functions. For instance, you can apply separate policies more efficiently for a field executive using a handheld device compared to an IT administrator using a laptop.
Consider using dynamic groups in Azure AD to automatically add or remove users from groups based on attributes like job title or department. With this feature, you can enforce appropriate policies over devices without manual intervention.
Keeping critical settings separate
If you need to exclude a device from a specific policy, it’s easier to do so by segmenting critical policies from non-critical ones. You can separate critical settings such as encryption, network configurations, and data protection policies from non-critical settings to minimize the risk of change implementations or updates.
With Intune’s conflict resolution mechanism, you can prioritize critical policies over non-critical ones, so essential security settings are always enforced. You can also deploy critical policies with higher priority or use expedited deployment options to ensure that they are applied promptly.
Replace GPOs with PowerShell for advanced configurations
While Intune offers a wide range of configuration options, there might be situations where you need to implement more specialized or complex settings that aren’t directly supported by Intune’s built-in policies. PowerShell helps you automate advanced configurations and extend Intune’s built-in policies through remediation scripts.
You can use PowerShell’s scripting capabilities to implement complex logic, conditional statements, and loops to execute custom installers with precise parameters. Since Intune’s remediation scripts run in the system context, you achieve elevated permissions to perform actions that might not be otherwise possible with standard user-level policies. Because PowerShell provides a vast library of cmdlets and the ability to execute any command-line tool, these scripts can offer you immense flexibility in what you can automate.
A typical use case of remediation scripts is to detect noncompliance, correct it, and ensure that all devices meet your organization’s standards. For instance, consider a scenario where you want all devices to have a specific version of Office 365 installed. The following PowerShell script checks the installed version of Office 365 on a device and automatically updates it if it does not meet the minimum required version.
In addition to using a PowerShell script, there are also specialized tools like Cayosoft Guardian that ensures the critical device management capability is monitored for device compliance and suspicious behavior, including attempts to alter policies and procedures.
$OBuild = Get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Office\ClickToRun\Configuration' `
| Select-Object -ExpandProperty VersionToReport
$Minimum = "16.0.17400.00000"
if ($OBuild -ne $null) {
if ($OBuild -ge $Minimum) {
Write-Host "Office version is up to date, build is $OBuild"
exit 0
} else {
Write-Host "Warning: Outdated office version, build is $OBuild"
exit 1
}
} else {
Write-Host "Office not installed or version information unavailable"
exit 0
}
Enhancing role-based user creation with Cayosoft
Cayosoft Administrator provides role-based user creation and policy assignment, simplifying onboarding new employees and managing devices. It can also automate the assignment of users to specific roles, ensuring the deployment of policies appropriate for their job function from the start. This saves time and lowers the possibility of errors during manual configuration.
With Cayosoft Administrator, IT admins can automate tasks such as managing group memberships, device enrollments, and application permissions using predefined roles, making policy management more efficient and less prone to misconfiguration.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Organizations are increasingly choosing cloud-first and hybrid infrastructures, and Microsoft Intune is the preferred device management solution. Intune offers better flexibility, scalability, and centralized management for Windows, macOS, iOS, and Android devices than using GPOs. For administrators who need more customization, PowerShell scripts can automate complex tasks and fill device management gaps.
Furthermore, Cayosoft Administrator automates user provisioning, manages group memberships, and simplifies hybrid Active Directory administration across on-premises and cloud environments. Integration of Cayosoft reduces the number of manual tasks, ensures secure delegation, and boosts hybrid and cloud infrastructure management efficiency.
Explore how Cayosoft Administrator can simplify hybrid environment management and automate user provisioning, license optimization, and group lifecycles while ensuring security and compliance.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content