Home » Five Critical Azure Security Best Practices for Effective Risk Management » Troubleshooting with Azure AD Audit Logs (known as Entra ID audit logs): Identify and Resolve Issues
Troubleshooting with Azure AD Audit Logs (known as Entra ID audit logs): Identify and Resolve Issues
Learn about the importance of comprehensive audit logging, including best practices for configuring, monitoring, and regularly reviewing Azure AD audit logs to enhance security and reduce risk.
Explore the chapters:
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Audit logs are an essential aspect of cybersecurity and compliance. They are detailed records of user activities, system events, and security-related actions within an environment, capturing who did what, when, and where. This level of “record-keeping” provides the visibility necessary to identify unusual or malicious activities and mitigate potential security threats.
Following several breaches in the past, it is clear that organizations have repeatedly struggled with the timely detection of security incidents. For example, IBM’s 2023 cost of a data breach report indicated that the average time to identify a data breach in 2023 was 204 days, and in that time, such a data breach would have cost the organization $4.95M. Delays like this are why monitoring is important, especially because, when configured properly, audit logs can significantly reduce the time it takes to detect and respond to security incidents, thereby minimizing potential damage.
With Azure Active Directory (AD) — now known as Entra ID — playing an essential role in identity management, Azure AD audit logs are a critical component of strong security posture for many organizations. This article will explore Azure AD audit logs in depth, including five powerful best practices that support effective configuration and can enable key insights to help organizations reduce risk.
Summary of key Azure AD audit logs best practices
This table summarizes five Azure AD audit logs best practices that organizations should consider implementing when working with Entra ID.
| Best Practices | Description |
|---|---|
| Enable and configure comprehensive audit logging | Ensure that auditing is turned on and the appropriate log categories are selected. |
| Configure alerts for critical events | Set up notifications for high-priority events like failed logins from privileged accounts. |
| Integrate with SIEM or log management solutions | Connect audit logs to an SIEM for deeper analysis and correlation with other security data. |
| Implement real-time monitoring | Establish continuous monitoring of audit logs to detect and respond to security incidents and compliance issues promptly. |
| Regularly review audit logs | Establish a routine to check for suspicious activity, failed login attempts, and policy changes. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Five essential best practices for Azure AD audit logs
Entra ID ( formerly known as Azure AD) audit logs comprehensively record user activities, administrative actions, and system events. They provide organizations with invaluable insights into their security posture and enable them to identify and respond to potential threats proactively. By carefully analyzing audit logs, organizations can better understand user behavior, detect anomalies, and investigate security incidents more effectively.
#1 Enable and configure comprehensive audit logging
Audit logs in Entra ID are a crucial security safeguard, providing a detailed record of user activities, administrative actions, and system events. They offer a comprehensive overview of user interactions with Azure AD resources, including sign-in attempts, password changes, role assignments, and application access. This information is invaluable for identifying suspicious activities, such as unauthorized access, data exfiltration, or policy violations. Additionally, audit logs can help organizations trace the root cause of security breaches, determine the extent of the damage, and take appropriate remediation steps.
Though we are particularly interested in audit logs, Entra ID offers various log categories that capture different types of activities. It is important to evaluate your organization’s specific security needs and select the most relevant logs. Some other important log categories are:
- Sign-in logs: These logs capture information about user sign-ins, including successful and failed attempts. They help identify unauthorized access attempts and monitor user activity patterns.
- Provisioning logs: These logs record details about user and group synchronization activities, both inbound and outbound, with external enterprise applications. These logs are crucial for tracking changes in user and group configurations.
To enable and configure audit logging in Entra ID, follow the steps below:
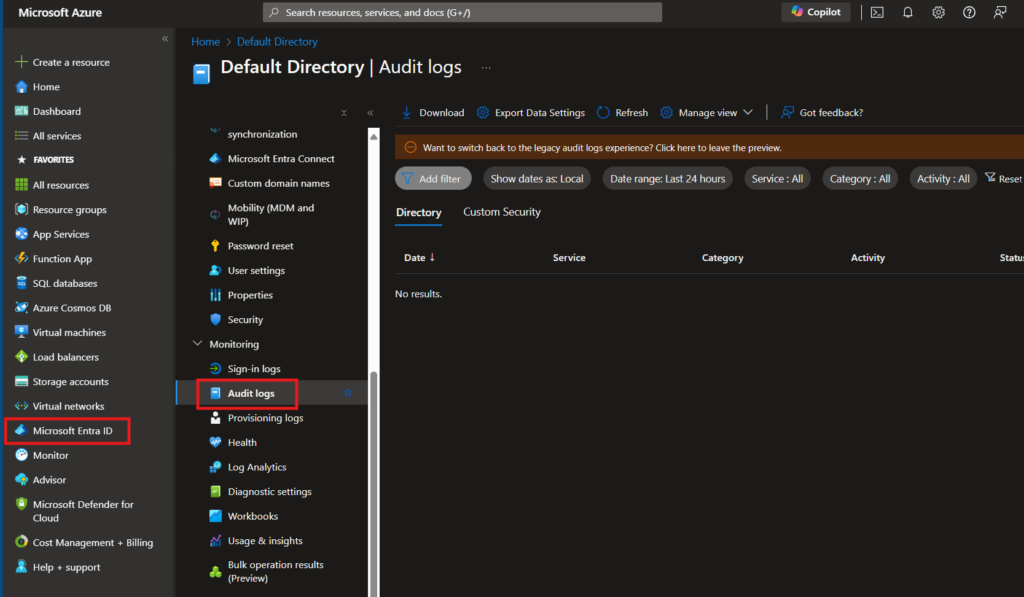
- Access the Azure Portal: Sign in to the Azure portal using an account with the necessary permissions.
- Navigate to Microsoft Entra ID: In the left-hand navigation pane, select “Microsoft Entra ID.”
- Enable Audit Logs: Under “Monitoring,” select “Audit logs.” Here, you can configure the logs to capture the necessary data for your organization.
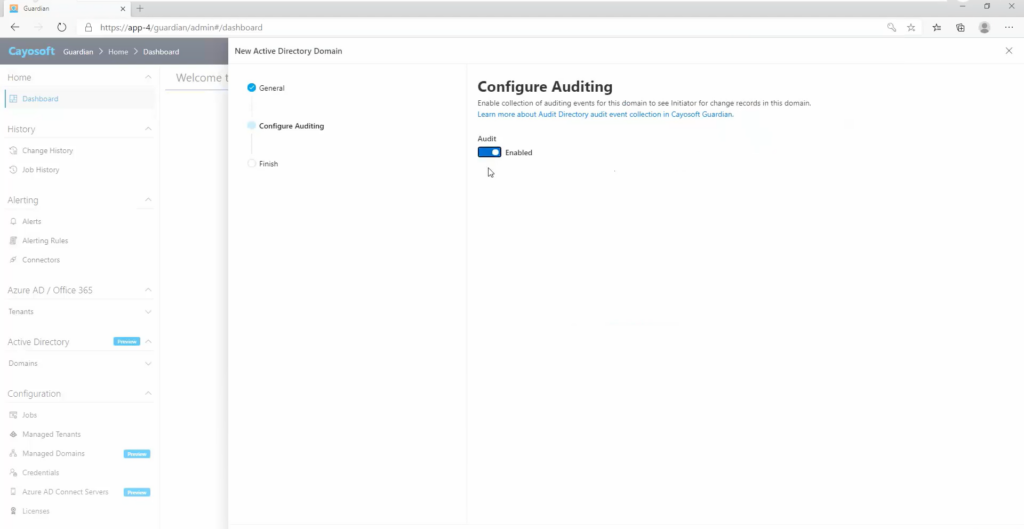
Cayosoft provides a straightforward and detailed approach to auditing logging. With Cayosoft Guardian, you can enable audit logging in less than three minutes. It is not limited to Entra ID but includes on-premises AD, hybrid AD, Office 365, and cloud-based applications.
Cayosoft does this by using Microsoft Graph APIs to access Entra ID and other Microsoft 365 cloud services, which allows it to collect data and track changes for almost any object type available via the Graph API.
#2 Configure alerts for critical events
Enabling and configuring audit logs is important, but it doesn’t make teams proactive. Engineers and incident responders must be notified of security events on the fly to swing into action. Therefore, configuring alerts in Entra ID becomes necessary to ensure timely detection and response to critical security events. By setting up alerts, security teams can be notified immediately when suspicious activities or potential threats are identified. This proactive approach allows for swift investigation and remediation, minimizing the impact of security incidents.
Alerting can be customized to meet an organization’s specific needs, enabling it to focus on the most critical events. Organizations can tailor alerts to their unique security landscape by carefully defining alert criteria, ensuring that only relevant and actionable alerts are generated.
There are many ways to configure alerts in Entra ID. For example, you can create alerts with Azure Monitor by following these steps:
- Navigate to Azure Monitor: In Azure Portal, from the left-hand menu, select “Monitor” to access Azure Monitor.
- Select “Alerts” and click “Create > Alert rule.“
- Choose the resource you want to monitor, such as a specific Azure AD tenant or application.
- Define the condition that will trigger the alert. This could be based on specific log data or metrics, such as failed login attempts or changes to user roles.
- Choose how you want to be notified when the alert is triggered. This could be via email, Azure Monitor alert, or automation tools like Azure Logic Apps.
- Once all configurations are set, review and create the alert rule.
It’s important to effectively manage alerts since uncontrolled alert volumes can lead to alert fatigue, hindering the ability to identify and respond to critical events.
- Prioritize alerts: Focus on critical alerts that significantly impact security or operations.
- Consolidate and filter alerts: Group related alerts together and filter out non-actionable notifications to reduce noise and prevent security analysts from becoming overwhelmed.
- Automate responses: Implement automated responses for common incidents to reduce manual intervention and speed up resolution times.
Though Microsoft boasts an impressive monitoring and alerting system, configuring them can become cumbersome and expensive. IT admins can use Cayosoft Guardian’s advanced monitoring capabilities for directory changes and configure custom alerting rules to be notified about critical changes. These rules are workflows with predefined configurable actions, which means that when an event occurs, a set of defined steps are triggered, allowing IT admins to respond promptly.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Alerting rules are based on queries with more than 127 built-in queries for IT admins to choose from and the option to create custom queries. These allow you to effectively configure alerts and automate responses or actions to help prevent alert fatigue.
To enable alerting in Cayosoft Guardian:
- Navigate to the Cayosoft Guardian web portal and expand the “Change Monitoring” node.
- Select the “Change History” node.
- In the “Quick Filter” bar, select the condition(s) for the alert. This can be Action, Object Type, etc.
- In the “Quick Filter” bar, click Save, and these conditions will be added to a new query.
- Click “Add Alert” to create a new alerting rule.
#3 Integrate with SIEM or log management solutions.
To gain a comprehensive view of your organization’s security posture and to effectively detect, investigate, and respond to threats, it’s highly recommended to integrate audit logs with Security Information and Event Management (SIEM). SIEM tools provide a centralized platform for collecting, analyzing, and correlating security data from various sources, including Entra ID, enabling security teams to identify patterns and detect threats that might go unnoticed. With advanced analytics and threat intelligence integration, SIEMs can detect complex threats by correlating seemingly unrelated events.
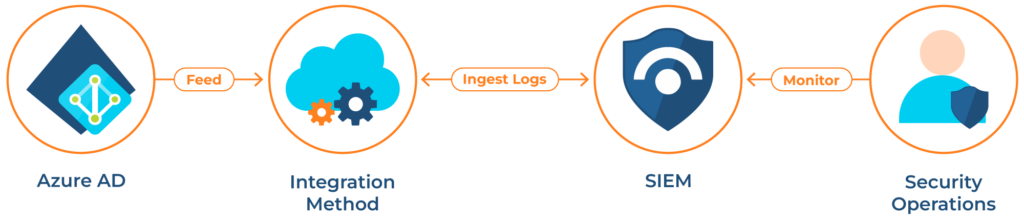
There are several ways to integrate Azure AD audit logs with a SIEM:
- Microsoft Sentinel (formerly Azure Sentinel): Azure Sentinel, Microsoft’s cloud-native SIEM solution, seamlessly integrates with Azure AD and can automatically collect and analyze Azure AD audit logs, enabling organizations to leverage its advanced threat detection and response capabilities.
- Third-party SIEM or log management solutions: Many popular SIEM and Log Management tools offer connectors or APIs for integrating Azure AD. These integrations typically involve configuring the SIEM solution to receive audit logs from Azure AD and mapping the data to the appropriate fields in the tool’s schema.
Threat actors often target SIEM solutions as part of their attack strategies by compromising or overloading them. By doing this, attackers can hinder organizations’ ability to detect and respond to malicious activities. Additionally, attackers may attempt to disable or remove SIEM agents from critical systems, limiting the visibility into network and system activity.
Cayosoft management and protection suite offers advanced auditing and threat detection capabilities that surpass traditional SIEMs’ limitations. By providing a more granular level of visibility into security events, it enables organizations to detect and respond to threats more effectively.
Implementing Cayosoft solutions, in addition to existing SIEM solutions, offers numerous advantages, including:
- Seamless integration with SIEMs: Cayosoft can seamlessly integrate with existing SIEM solutions, enriching the SIEM with data by writing change history to the Windows Event Log. Most SIEMs use the Windows Event Log as an aggregation for logs, and by constantly writing security-related changes, Cayosoft ensures that these logs are consolidated in a single location, making it easier for the SIEM to correlate and analyze data.
- Enhanced data integrity: One of the most impressive features of Cayosoft Guardian is its ability to record changes even when security logs or SIEM tools may have been compromised. This ensures that organizations have a reliable record of security events, even in the face of attacks that target logging infrastructure.
Even better is how fast and simple it is to integrate Cayosoft with SIEM solution via Windows Event Log:
- Open the Cayosoft Guardian Web Portal
- Go to Settings->Service Settings
- Select Windows Event Log Settings and click Properties.
- In the Windows Event Log for Alerts section, uncheck the “Disabled” checkbox.
By integrating Entra ID with a SIEM solution and utilizing advanced solutions like Cayosoft Guardian, organizations can significantly improve their ability to detect, analyze, and respond to security threats, ensuring a more secure and compliant environment.
Watch demo video of Cayosoft’s hybrid user provisioning
#4 Implement real-time monitoring
In addition to security alerts, real-time monitoring is a recipe for proactive threat detection and incident response. By continuously monitoring Azure AD for suspicious activities and potential threats, organizations can proactively detect and respond to incidents, minimizing the impact of security breaches. This enables organizations to protect sensitive data, maintain business continuity, and demonstrate compliance with industry regulations.
The benefits of real-time monitoring are numerous. It enables organizations to:
- Instantly identify suspicious activities, allowing security teams to respond promptly to potential threats.
- Minimize the time attackers spend in the system, limiting potential damage.
- Proactively approach security, enabling teams to address vulnerabilities before they can be exploited.
Azure Monitor is a cloud-native monitoring solution that provides organizations with real-time insights into their cloud resources’ health, performance, and security. It offers a range of capabilities, including:
- Log Analytics: Azure Monitor can collect and analyze logs from various sources, providing insights into user sign-ins, password changes, role assignments, and other security-related events.
- Alerts and notifications: Azure Monitor allows organizations to configure alerts for specific events or conditions.
While Microsoft Entra ID provides visibility and monitoring capabilities into your cloud environment, it lacks a unified reporting tool that covers your entire cloud environment.
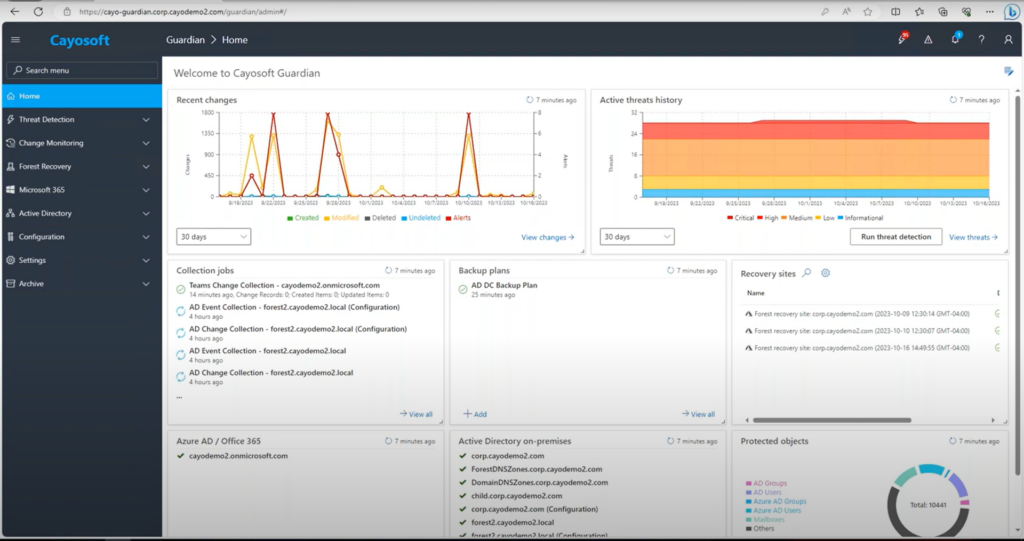
Cayosoft Guardian was specifically designed to simplify AD security and hybrid AD monitoring. It enhances the monitoring capabilities in Entra ID by providing continuous, real-time monitoring and unified reporting tailored across integrated Microsoft services, including on-prem AD and Entra ID. With Guardian monitoring all directory changes, administrators can immediately see, understand, and instantly roll back malicious changes across their entire hybrid AD environment.
#5 Regularly review audit logs
Reviewing Azure AD audit logs regularly is essential to fully leveraging their benefits. By analyzing audit logs, organizations can gain valuable insights into user behavior, identify suspicious activities, detect potential threats, and investigate security incidents more effectively.
Regular review of audit logs can help organizations:
- Identify unauthorized access: Detect attempts by unauthorized users to access sensitive data or systems.
- Detect data exfiltration: Identify signs of data being copied or transferred outside the organization’s boundaries.
- Identify policy violations: Detect violations of security policies, such as password reuse or unauthorized access to sensitive resources.
- Investigate security incidents: Use audit logs to trace the root cause of security breaches and determine the extent of the damage.
- Monitor user behavior: Analyze audit logs to identify trends and patterns in user behavior that may indicate potential threats.
When reviewing audit logs, you want to pay particular attention to the following:
- Authentication patterns: Look for unusual login times, multiple failed login attempts, or logins from unexpected locations.
- Privilege escalation: Monitor for unexpected changes in user roles or permissions, especially for admin accounts.
- Resource access: Track access to sensitive resources or applications, noting deviations from normal usage patterns.
- Policy changes: Keep an eye on modifications to security policies, as these could weaken your security posture.
- User and Group Management: Monitor the creation, deletion, or modification of user accounts and group memberships.
Cayosoft Guardian significantly simplifies the audit log review process by providing unified management and reporting capabilities:
- Centralized dashboard: Cayosoft offers a centralized dashboard that aggregates audit data from multiple sources, including Entra ID, on-premises Active Directory, and other Microsoft 365 services. This unified view eliminates the need to switch between different interfaces, saving time and reducing the risk of overlooking critical information.
- Customizable reports: Cayosoft allows you to create customized reports that focus on the specific areas most relevant to your organization’s security needs.
- Intelligent filtering: Cayosoft’s advanced filtering capabilities allow you to quickly sift through large volumes of log data, highlighting the most critical or unusual events. This feature helps security teams focus on potential threats rather than getting lost in routine log entries.
- Automated alerts: Cayosoft can be configured to send automated alerts based on specific criteria or thresholds. This proactive approach ensures that critical events are brought to the attention of security personnel immediately, even outside of scheduled review periods.
By leveraging Cayosoft’s unified management and reporting capabilities, organizations can transform the often daunting task of audit log review into a streamlined, efficient process. This not only improves the effectiveness of security monitoring but also frees up valuable time for security teams to focus on more complex security challenges. Regular review of audit logs, especially when enhanced by tools like Cayosoft Guardian, provides the visibility and insights necessary to maintain a strong security posture in an ever-evolving threat landscape.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Audit logs are the cornerstone of a sound security strategy. They provide invaluable insights into user activities, system changes, and potential security threats, enabling organizations to maintain a strong security posture.
The five Entra ID (Azure AD) audit logs best practices in this article form the foundation of a comprehensive Azure audit logging strategy. The right technology can make a significant difference in how effectively and efficiently an organization can implement these practices. By leveraging Cayosoft’s solutions, organizations can more easily implement and maintain the best practices we’ve discussed, significantly enhancing their security posture and simplifying compliance efforts.
Whether you’re looking to improve your current audit logging processes or implementing a comprehensive strategy from scratch, Cayosoft’s solutions can provide the tools and support you need to succeed.
Take the next step and contact Cayosoft today for a personalized demo, and discover how our solutions can elevate your organization’s security and compliance efforts.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content