Home » Five Critical Azure Security Best Practices for Effective Risk Management » Streamlining Your Active Directory: Top 5 AD Sync Best Practices
Streamlining Your Active Directory: Top 5 AD Sync Best Practices
Learn 5 important best practices for setting up and managing AD sync, including securing the server, limiting administrative access, and minimizing synchronized data.
Explore the chapters:
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Organizations and businesses have increasingly integrated on-premises and cloud applications in recent years, leveraging cloud-based resources like Microsoft 365 and on-premises infrastructures like Active Directory (AD) to drive their operations. This hybrid approach offers flexibility and scalability, but it also presents a unique set of challenges, particularly when it comes to managing identities.
When identities are managed separately in each environment, the result can be complex and prone to inconsistencies, creating administrative overhead and potential security risks. For instance, a terminated employee’s access might be revoked on-premises but inadvertently left active in the cloud.
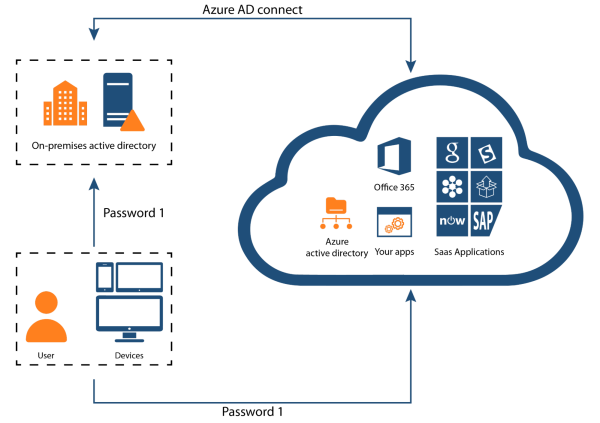
Provisioning and synchronization are two major actions that can be used to achieve a hybrid identity. Provisioning involves creating an object based on certain conditions, keeping it up to date, and deleting it when those conditions no longer match. Active Directory synchronization (AD sync) ensures that identity information on your on-premises AD matches the cloud, resulting in a consistent identity for each user and group.
Microsoft Entra Connect is one tool designed to achieve organizations’ hybrid identity goals, but improper setup can lead to misconfigurations, synchronization errors, and security vulnerabilities. For example, if sensitive attributes are synced unnecessarily, they could be exposed to unauthorized users in the cloud.
This article guides you through five best practices for setting up and managing AD sync, helping you avoid common pitfalls while securing your hybrid identity infrastructure.
Summary of Key AD Sync Best Practices
This table summarizes the five AD sync best practices that we explore in the later sections of this article.
| Best Practices | Description |
| Secure the Microsoft Entra Connect server | Harden the server running Microsoft Entra Connect to minimize the attack surface. |
| Limit administrative access | Restrict who can manage the Entra Connect server to minimize privilege escalation risks. |
| Minimize synchronized data | Synchronize only the attributes required for authentication and authorization. |
| Implement continuous monitoring and auditing | Regularly monitor and audit your Entra connect sync operations and health to identify unusual activities. |
| Have a recovery plan | Have a recovery/backup plan in the event of sync failure or a security incident. |
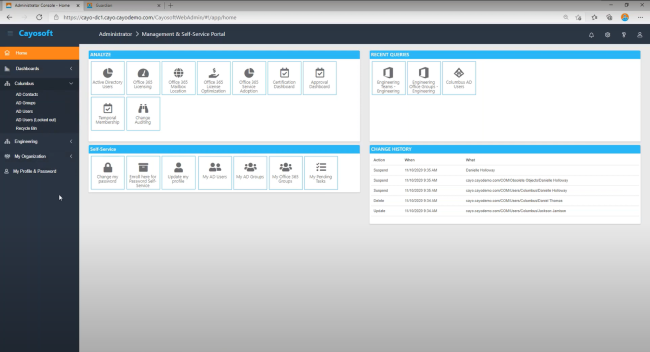
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Five Important AD Sync Best Practices
While this article focuses on Microsoft Entra Connect sync, these five best practices are applicable regardless of the AD sync tool in use—Microsoft Entra Connect Sync or Microsoft Entra Cloud Sync. They can help improve the security posture of the deployed sync tool and hybrid identity infrastructure.
Secure the Microsoft Entra Connect server
The Entra Connect server is a critical component of your hybrid identity infrastructure that synchronizes identities between on-premises Active Directory and Microsoft Entra ID (formerly Azure AD). It contains sensitive identity data, and based on the Active Directory tier model, and it should be treated as a Tier 0 component. This categorization emphasizes its critical nature and the need for stringent security measures to maintain the integrity and confidentiality of your hybrid identity infrastructure.
Here are some key steps to secure the server:
- Implement strong password policies for all accounts associated with the Entra Connect server, including local administrator accounts. Consider using the Local Administrator Password Solution (LAPS) to automatically manage and rotate local admin passwords.
- Enable multi-factor authentication (MFA) for all users with privileged access to the Entra Connect server and Microsoft Entra ID.
- Implement network segmentation and use firewalls and network security groups (NSGs) to restrict network access to the Entra Connect server. Only allow necessary inbound and outbound traffic from trusted sources.
- Regularly update and patch the Entra Connect server, including the operating system, Entra Connect software, and other installed applications.
In addition, Cayosoft offers a suite of products that seamlessly complements these security measures and provide additional layers of protection and management for your hybrid identity environment:
- Cayosoft Administrator allows administrators to implement strong access control policies that align with the principle of least privilege, ensuring that admins only have the necessary permissions to perform their tasks.
- Cayosoft Administrator also supports role-based access control (RBAC) to granularly manage permissions for different administrative roles involved in managing the hybrid identity infrastructure.
- Cayosoft Guardian gives admins detailed auditing and reporting capabilities to monitor changes and activities related to the Entra Connect server and synchronized identities.
Implementing these security best practices and leveraging complementary tools like Cayosoft can significantly improve the security posture of the Entra Connect server and protect the hybrid identity infrastructure from potential threats and unauthorized access.
Limit Administrative Access
Limiting administrative access to the Entra connect server can significantly reduce the risk of unauthorized access and potential data breaches. This practice aligns with the principle of least privilege, which is fundamental to maintaining a robust security posture in any IT environment. When applied to the Microsoft Entra Connect server, this principle ensures that only a select group of authorized personnel have administrative access, thereby minimizing the attack surface and reducing the potential impact of compromised accounts.
To effectively implement limited administrative access, IT admins need to do the following:
- Determine which roles require administrative access to the Entra Connect server and restrict access to only the identified group. This typically includes domain administrators and a small group of identity management specialists. This limitation reduces the attack surface by minimizing the number of accounts with privileged access.
- Create dedicated accounts distinct from regular user accounts for administrative tasks to prevent accidental exposure of privileged credentials during routine activities.
- Implement role-based access control (RBAC), utilizing Entra ID’s built-in roles or creating custom roles that align with specific job responsibilities. This granular approach ensures that administrators have only the permissions necessary for their tasks.
Proper role assignment means that only essential personnel have administrative access. By carefully defining and assigning roles, organizations can maintain tight control over who can change the Entra Connect configuration and related settings.
However, this usually isn’t as straightforward as it sounds when using native tools. Cayosoft Administrator can play a significant role in simplifying the management of administrative access for Entra Connect and related Microsoft 365 services. Some key features that support this best practice include:
- Centralized role management: Cayosoft Administrator provides a unified interface for managing roles across on-premises Active Directory and Entra ID, making it easier to maintain consistent access controls.
- Automated provisioning and deprovisioning: Cayosoft Administrator can automate granting and revoking administrative access based on predefined rules, reducing the risk of human error and ensuring timely access changes.
- Granular permission controls: Cayosoft Administrator allows for fine-tuned permission assignments, enabling organizations to implement the principle of least privilege more effectively.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Minimize Synchronized Data
It is important to minimize synchronized data when using Entra Connect sync to integrate on-premises AD with Entra ID because this approach helps protect sensitive information and reduces the potential impact of data breaches. The basic idea behind this is simple: The less data you synchronize to the cloud, the smaller your attack surface becomes. By carefully choosing which data to synchronize, organizations can significantly reduce the risk of unauthorized access to sensitive information while maintaining the necessary functionality for cloud-based applications and services.
Here are some specific actions to consider:
- Determine which user attributes are required for your cloud applications and services. Common essential attributes include user principal name, display name, email address, and group memberships.
- Use Entra Connect’s attribute filtering capabilities to exclude attributes that are not necessary for cloud operations. This may include personal information, detailed job titles, or internal organizational data.
- Implement filters to exclude dormant or inactive user accounts from synchronization. This will prevent unnecessary clutter in your Entra ID environment and reduce the risk associated with forgotten accounts.
- Only synchronize groups relevant to cloud applications and services. Exclude internal administrative groups or groups used solely for on-premises purposes.
- Consider enabling password hash synchronization (PHS) for enhanced security while minimizing data exposure. PHS works by synchronizing a user’s password hash from on-premises AD to Entra ID, allowing them to sign in to cloud-based services using the same password used to sign in to on-premises AD.
The default synchronization rule isn’t always the best fit for every scenario. While it provides a starting point, customization is often necessary to align with specific organizational requirements. Cayosoft Administrator offers powerful functionalities to help organizations filter and manage data synchronized to Entra ID:
- Using Cayosoft Administrator’s automated lifecycle management, organizations can automate disabling or removing inactive accounts, reducing the risk of unnecessary data synchronization.
- Cayosoft Administrator can help IT admins manage group memberships more effectively using its easy-to-create granular membership rules. These rules allow the inclusion or exclusion of members from a particular group, ensuring that only authorized people are synchronized and given access to on-prem and cloud resources.
Using Cayosoft Administrator to carefully curate and prepare what groups will be synced and coupling this with Entra Connect sync’s filtering capabilities allows organizations to implement a more refined and secure approach to identity synchronization between on-premises AD and Entra ID.
Implement Continuous Monitoring and Auditing
In 2022, IBM reported that it took businesses an average of 277 days (roughly nine months) to identify a breach, emphasizing the importance of continuous monitoring and auditing to detect and respond to potential security incidents or unauthorized changes.
Organizations can leverage various tools and services to implement effective monitoring and auditing, with Entra Connect Health being a specific option for monitoring Entra Connect Sync. Entra Connect Health offers several features that are particularly useful for Entra Connect sync monitoring:
- Alert management allows admins to view active alerts, including relevant information and steps to resolve them.
- It provides Sync Insight, which allows admins to know the time it takes to sync changes to Entra ID and the volume of changes. It also provides graphical trends for sync operations’ latency, helping admins detect anomalies.
- Microsoft Entra Connect Health diagnoses duplicated attribute sync errors and provides specific fixes.
While Entra Connect Health offers robust capabilities, it has some limitations, one of which is that the evaluation of alerts depends on the sync configuration in use. For example, suppose an IT admin does not use the default sync configuration. In that case, the Microsoft Entra Connect Health agent will not upload the error events related to Microsoft Entra Connect sync.
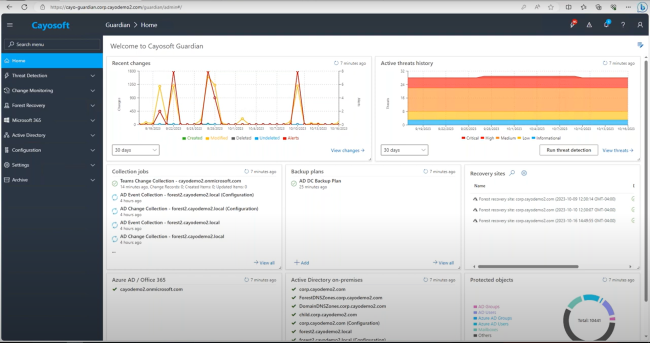
Cayosoft Guardian resolves these limitations by providing advanced monitoring and auditing capabilities tailored to hybrid identity environments, including these features:
- Cayosoft Guardian comprehensively monitors and records all Entra Connect server configuration changes, capturing who made changes, what was changed, and when the changes occurred.
- Guardian provides immediate notifications for critical events or suspicious activities, allowing for rapid response to potential security threats.
- It offers intuitive dashboards that provide visibility into the health and security status of the hybrid identity infrastructure at a glance.
- Cayosoft Guardian provides a unified view of activities across on-premises AD and Entra ID, enabling comprehensive monitoring of the entire hybrid identity infrastructure.
These practices help with monitoring changes, detecting and responding to security issues, and providing valuable insight for ongoing optimization and compliance management. By implementing continuous monitoring and auditing practices using Cayosoft Guardian and Entra Connect health, organizations can significantly enhance their security postures and maintain the integrity of their hybrid identity infrastructure.
Watch demo video of Cayosoft’s hybrid user provisioning
Have a Recovery Plan
A comprehensive backup and recovery plan is a crucial security best practice for organizations with a hybrid identity infrastructure. It ensures business continuity in case of a failure during synchronization, breach, or other disaster that could affect the hybrid identity environment. A well-designed recovery plan minimizes downtime, data loss, and the potential for cascading failures across the organization’s IT systems.
Many organizations with hybrid identity infrastructure wrongly assume that AD synchronization automatically denotes proper management and backup. They soon find out that most Entra ID objects often have certain attributes that exist only in the cloud.
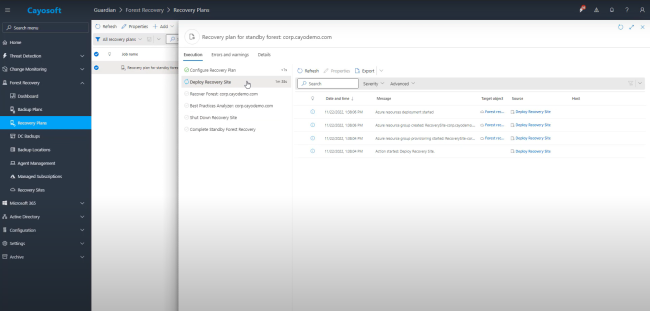
Cayosoft Guardian Forest Recovery offers a powerful solution for implementing and executing a comprehensive recovery plan for hybrid identity environments.
Some key features include the following:
- Cayosoft Guardian forest recovery can quickly and efficiently restore an entire Entra ID forest, minimizing downtime and data loss.
- With Guardian’s real-time audit and rollback feature, administrators can restore individual objects or attributes, like group memberships, group policy objects (GPOs), and account settings, providing flexibility in recovery scenarios.
- Guardian Forest Recovery automates all the complex steps involved in forest recovery, reducing the time required for full forest recovery and the risk of human error and potentially cutting recovery time from weeks to hours.
- Guardian Forest Recovery uses clean source installation media for the operating system during recovery, reducing the risk of reintroducing malware or other security threats.
Organizations can use Cayosoft Guardian Forest Recovery to implement a robust and efficient recovery plan that ensures business continuity and provides a reliable fallback option in case of AD synchronization failures, security incidents, or system failures. This gives organizations confidence that they can quickly recover from a wide range of potential disasters, minimizing the impact on business operations and maintaining the trust of customers and partners.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
In this article, we examined five essential best practices for synchronizing your on-premises AD with Entra ID using Entra Connect sync. We explored the critical need to secure the Microsoft Entra Connect server, treating it as a high-value asset and implementing strong access controls, multi-factor authentication, and network segmentation.
We also highlighted how Cayosoft’s suite of products aligns closely with these best practices by offering simplified management of administrative access and granular permission controls and providing advanced monitoring and auditing features, including real-time alerts and anomaly detection. It represents a cutting-edge solution for rapid and reliable recovery of your entire AD forest.
These solutions work in tandem to provide a holistic approach to securing and managing your Entra Connect environment, addressing the complex challenges of hybrid identity infrastructures. To further enhance your organization’s security posture and streamline your hybrid identity management, request a personalized demo to see Cayosoft’s solutions and understand how they can address your needs.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content