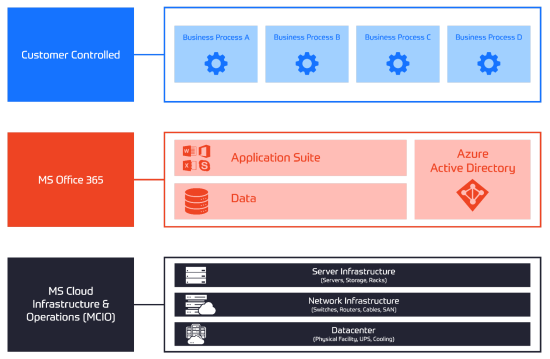
Home » Five Critical Azure Security Best Practices for Effective Risk Management
Five Critical Azure Security Best Practices for Effective Risk Management
Learn about the five essential Azure security best practices, including identity management, data protection, threat detection, and governance, to mitigate risk and maintain compliance.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
There are a number of essential security best practices to mitigate risk for organizations adopting Microsoft Azure. If you are planning on hosting sensitive data or business-critical applications in Azure, it is recommended to implement a comprehensive security strategy that spans identity management, data protection, threat detection, and governance.
This article delves into five essential Azure security best practices that every organization should prioritize. First, we discuss the importance of defining a robust identity strategy, enabling secure access to Azure environments while alleviating complexity. Next, we examine Azure’s shared responsibility model, clarifying the division of security obligations between Microsoft and your organization. We then discuss data privacy and protection guidelines, leveraging Azure’s built-in services and encryption capabilities.
We also highlight the necessity of a well-defined threat detection and response strategy, integrating Azure’s security tools with existing on-premises systems and taking advantage of the benefits of solutions like Cayosoft Guardian. Finally, we emphasize the significance of maintaining compliance through effective governance, encompassing clear policies for change management, cost control, and regulatory adherence.
This article assumes that you have a basic understanding of IT security, including defense-in-depth practices and encryption. It focuses on security strategies and does not dive into the complexities of each cloud service or provide how-to tutorials. Instead, the intention is to help you define clear security goals prior to configuring or deploying workloads.
Summary of Key Azure Security Best Practices
This article explains the five following Azure security best practices.
| Best practice | Description |
| Define your identity strategy | Learn how a robust identity strategy can help your organization stay secure while easing complexity and allowing users to access Azure environments. |
| Define your networking strategy | Expanding an on-premises network into the cloud introduces new patterns and security boundaries to be aware of. |
| Review the shared responsibility model | Understand who is responsible for each aspect of security and compliance in Azure, particularly in hybrid cloud environments. |
| Follow data privacy and protection guidelines | Azure maintains default settings but also includes several services for additional user-managed security, such as Azure Key Vault. |
| Define a threat detection and response strategy | Review existing on-premises security systems along with Azure’s built-in tooling when expanding an environment into the cloud. |
| Maintain compliance through effective governance | Define clear policies for your organization’s cloud environment, including change management and cost controls. |
Define Your Identity Strategy
Before getting too deep, it’s important to note that Microsoft has rebranded its identity offerings under the Microsoft Entra product family to provide a unified identity platform spanning on-premises and cloud offerings. While most of the documentation for Azure AD is still relevant, the terminology may be mixed depending on where you find information.
The vast majority of enterprises operate in a hybrid Active Directory (AD) environment, leveraging on-premises Active Directory along with Microsoft Entra ID for cloud services like Microsoft 365. This hybrid setup makes sense because it allows organizations to extend their existing identity investments to the cloud.
As you move workloads to Azure, it’s crucial to follow the principle of least privilege and implement role-based access control (RBAC) to grant the minimal necessary permissions. Enabling multi-factor authentication (MFA) for all users and implementing conditional access policies based on risk signals is also highly recommended. For advanced scenarios like just-in-time privileged access, consider privileged identity management (PIM) solutions.
Managing a hybrid identity environment can introduce significant complexity. Third-party tools like Cayosoft Administrator can help streamline and secure your identity strategy across on-premises and cloud environments.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Define Your Networking Strategy
Expanding your on-premises network into Azure introduces new networking patterns and security boundaries that you should consider carefully. A well-defined networking strategy will ensure secure connectivity, data protection, and compliance. It serves as the foundation for implementing effective security controls, segmenting resources, controlling traffic flows, and mitigating potential threats.
Without a proper networking strategy, your Azure deployment may be susceptible to various risks, such as unauthorized access, data exfiltration, lateral movement, and compliance violations. A secure networking strategy enables you to isolate resources, enforce access controls, monitor network traffic, and securely integrate with on-premises networks.
The following approaches are similar to those used for other cloud providers, such as AWS and Google Cloud, but they are specifically mentioned here because they are unique to Azure:
- ExpressRoute or VPN gateway: For hybrid cloud scenarios, establish a secure connection between your on-premises network and Azure using ExpressRoute or a site-to-site VPN gateway. This ensures secure data transfer and extends your on-premises network to Azure.
- Virtual network (VNet) segmentation: Segment your Azure virtual networks based on their uses, such as production, development, and testing environments. This isolation helps mitigate the risk of lateral movement if one network is compromised.
- Virtual network peering: Use VNet peering to securely connect multiple virtual networks within the same Azure region or across different regions. This allows resources in different VNets to communicate securely without traversing the public internet.
- Network security groups (NSGs): Implement network security groups to control inbound and outbound traffic to and from your virtual machines and subnets. Define rules to allow only necessary traffic and deny everything else by default.
- Azure Firewall: Deploy Azure Firewall as a centralized network security service to secure and monitor traffic across your virtual networks. It provides features like application-level filtering, threat intelligence, and centralized logging.
By proactively defining your networking strategy, you can establish a layered defense, implement security best practices, and align with industry standards and regulatory requirements. This approach not only enhances the overall security posture of your Azure deployment but also facilitates easier management, scalability, and integration with existing on-premises infrastructure.
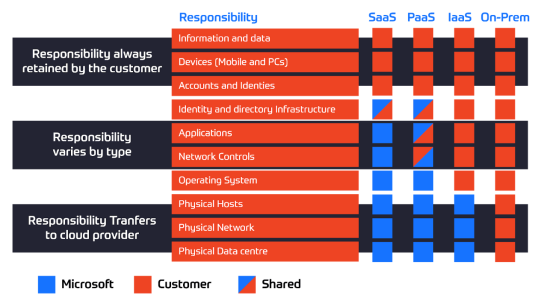
Review the Shared Responsibility Model
Azure, like most cloud providers, operates on a shared responsibility model. This means that the security and compliance responsibilities are shared between you and Microsoft. It’s crucial to understand what both parties are responsible for to ensure a secure and compliant environment. The specific responsibilities for your chosen architecture will help you better allocate resources, implement appropriate security controls, and maintain a secure and compliant environment in Azure.
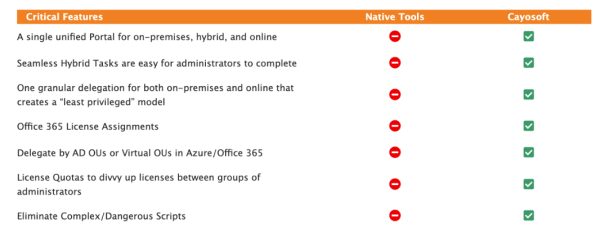
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
At a high level, Microsoft is responsible for securing the underlying Azure infrastructure, including the physical data centers, networks, and host machines. Azure users, on the other hand, are responsible for securing their applications, data, operating systems, and network traffic.
The specific responsibilities vary depending on the model of each service that you’re using: infrastructure as a service (IaaS), platform as a service (PaaS), or software as a service (SaaS). With IaaS, you have more control and responsibility over the guest operating system, data, and applications. With PaaS and SaaS, Microsoft manages more components, reducing your responsibilities.
Let’s take the example of managing Active Directory infrastructure. In an IaaS scenario, where you’re running self-managed AD domain controllers on virtual machines, you’re responsible for securing the VMs, the AD infrastructure, and the data within them. If you use Entra ID instead, a SaaS offering, Microsoft manages the underlying infrastructure and ensures the service’s availability and security.
In hybrid scenarios, the responsibilities are shared. With Entra Hybrid, you manage the on-premises AD infrastructure while Microsoft secures the Azure AD Connect sync components. With Entra Domain Services (formerly Azure Active Directory Domain Services), Microsoft provides the managed domain services, but you’re still responsible for securing the workloads and data within the domain.
Note that managing Active Directory infrastructure is no small feat, even when Microsoft is responsible for securing the cloud components. If you’re seeking a unified solution to manage hybrid Active Directory environments, consider using a product like Cayosoft Administrator to simplify this complexity. Cayosoft Administrator is specifically designed for successfully managing hybrid Active Directory environments. It includes many useful features, such as Family Groups to automate creating and managing groups and memberships and License Profiles to delegate and automate M365 licenses across an organization.
Follow Data Privacy and Protection Guidelines
Azure provides default security and encryption settings for certain services, but you may need to implement additional encryption measures based on your organization’s needs and regulatory requirements. If you’re new to cloud security or need a starting point for your organization’s guidelines, the Cloud Security Alliance is an excellent resource.
Services like Azure Disk Encryption and Azure Storage Service Encryption allow you to encrypt virtual machine disks and data stored in Azure Storage, respectively. Azure Key Vault provides a secure and centralized location for storing and managing encryption keys, secrets, and certificates, simplifying key management processes. If you choose to manage encryption keys yourself, be mindful of the additional complexity this introduces: Simply put, don’t add unnecessary layers of encryption if your organization does not require you to do so.
Access control through Active Directory or Entra is essential for data privacy and protection. As a best practice, segment users into groups and leverage RBAC to streamline access management and ensure that only authorized individuals can access sensitive data. This way, when users leave your organization, you can simply remove them from a group as opposed to chasing down each individual permission they may have been granted across your environment.
Watch a demo video of Cayosoft’s hybrid user provisioning
Define a Threat Detection and Response Strategy
Early security threat detection and swift responses can help mitigate risks, comply with regulatory requirements, and protect your organization’s reputation. However, it’s important to note that maintaining an effective security posture requires ongoing efforts from security experts, a cost that should not be underestimated.
Azure provides several built-in threat detection and response capabilities to help you identify and respond to potential security threats. Azure Security Center is a unified infrastructure security management system that continuously monitors your Azure resources, providing security recommendations and alerting you to potential threats. Additionally, Microsoft Sentinel is a cloud-native security information and event management (SIEM) solution that enables you to collect, analyze, and respond to security events across your entire organization.
These services offer advanced threat protection features—such as anomaly detection, behavioral analytics, and threat intelligence based on machine learning—to help you identify and respond to various security threats effectively. The Azure portal also provides recommendations and guidance to help you further strengthen your security posture.
While leveraging Azure’s built-in security capabilities can significantly enhance your threat detection and response efforts, it’s important to consider the additional maintenance and operational overhead required to effectively manage these systems. Engaging with experienced security vendors, such as Cayosoft, can help you successfully identify threats while eliminating solution bloat and reducing operational overhead. For Entra identity environments, Cayosoft Guardian, an end-to-end threat detection and response solution. It offers a unified console for monitoring environment changes and helps administrators quickly find and fix unwanted changes.
Maintain Compliance Through Effective Governance
Effective governance practices ensure that your Azure environment remains secure, compliant, and aligned with your business objectives. To begin, establish clear policies and guidelines for your organization, such as defining processes for identities and change management. Ensure that identities cannot be created outside your defined toolset, and implement change management procedures to track and approve modifications to your Azure resources.
Governance also involves certification, attestation, and reporting processes. Solutions like Cayosoft Administrator can streamline group certification and attestation, helping you maintain compliance with industry regulations and internal policies. Regular attestation of user access and privileges can help mitigate the risks associated with excessive or unauthorized access.
Azure Policy is a powerful tool that enables you to enforce compliance across your Azure environment. By defining and assigning policies, you can ensure that your resources remain compliant with specific standards or regulations. Azure Policy also provides built-in policy definitions for various compliance requirements, making it easier to maintain compliance from day one.
For specific compliance documentation and attestation, Microsoft Service Trust Portal (STP) is an invaluable resource that saves administrators a lot of time. The STP provides access to audit reports, compliance guides, and other relevant documentation, helping you demonstrate compliance with various industry standards and regulations.
Finally, it’s important to consider cost management as part of your governance strategy. Microsoft Cost Management tools can help you monitor and optimize your cloud spending, ensuring that you stay within your organization’s cloud budget.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Begin your cloud journey by defining a comprehensive identity strategy that extends your existing on-premises investments to the cloud while adhering to basic identity principles like least privilege access and multi-factor authentication. Understand the shared responsibility model to clarify the split of security obligations between your organization and Microsoft. Leverage Azure’s built-in encryption and data protection capabilities while implementing rigorous access controls via groups.
Before moving into production, establish an effective threat detection and response strategy that leverages Azure’s security tools alongside experienced vendors. Finally, maintain compliance through governance practices that encompass clear policies, change management processes, cost optimization methods, and adherence to your organization’s regulatory requirements.
By following Azure security best practices and leveraging Cayosoft’s suite of products, you can confidently extend your identity infrastructure and mission-critical workloads to the cloud.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content