Home » Active Directory Management Tools: Must-Have Features » How to Disable Active Directory Accounts: A Step-by-Step Guide
How to Disable Active Directory Accounts: A Step-by-Step Guide
Learn the best practices for disabling Active Directory (AD) users, including regularly reviewing and cleaning up disabled accounts and knowing when to disable or delete.
Explore the chapters:
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Maintaining security and operational effectiveness in your organization requires careful management of user account lifecycles. Disabling Active Directory (AD) users is a crucial step in this process and is necessary for mitigating security risks and streamlining access management when employees leave, change roles, or go on temporary leave.
This article explains how to disable AD users, individually or in bulk, and discusses the best practices for managing AD configurations when disabling accounts. This article does not cover AD build and implementation, so we recommend that you have a working AD environment with multiple AD users for testing single and bulk operations in order to follow the step-by-step tutorials below.
Summary of best practices related to disabling Active Directory users
| Best Practices | Description |
|---|---|
| Regularly review and clean up disabled accounts | Maintain a clean and secure Active Directory (AD) environment by regularly scanning, reviewing, and cleaning up disabled AD accounts. |
| Know when to disable and when to delete | Know the different processes and situations related to disabling or deleting user accounts. |
| Create proper documentation | Create documentation and store accurate references on when and why each user account was disabled. |
| Use an organizational unit for disabled accounts | Segregate active users from disabled user accounts by creating workflows to send a user account to a separate organizational unit (OU) after deactivation. |
How to disable Active Directory user accounts
Prerequisites for disabling AD accounts
Specific prerequisites must be in place before you can disable AD users, either individually or in bulk. First, you need to have a working AD environment that contains AD users to simulate testing. Second, you must install administrative tools like the AD Users and Computers (ADUC) console to manage AD users, though you actually only need to install the Remote Server Administration Tools (RSAT) package. If you haven’t installed RSAT yet, you can install it using the following commands.
For workstations:
Add-WindowsCapability –Online –Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
For servers:
Install-WindowsFeature -Name "RSAT-AD-PowerShell" -IncludeAllSubFeature
Once you finish installing the RSAT package, run the following command to also install the ActiveDirectory PowerShell module:
Install-Module ActiveDirectory
Once installed, you can import the module using the command below. We recommend importing this now as you follow the tutorials in this article:
Import-Module ActiveDirectory
Disabling AD users individually using the GUI
Step 1: Open the Active Directory Users and Computers console
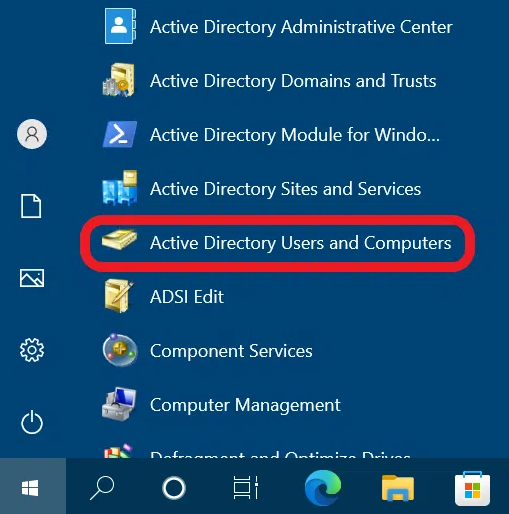
Press Windows Key + R to launch the Run window. Type dsa.msc and press Enter.
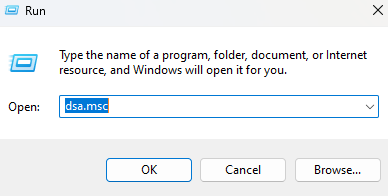
This command will open the ADUC console.
Alternatively, you can search for the console via the Start Menu.
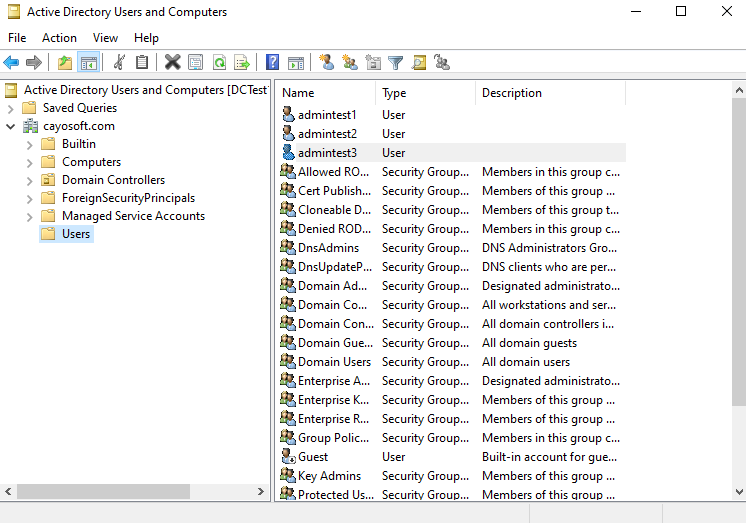
Step 2: Locate the user account
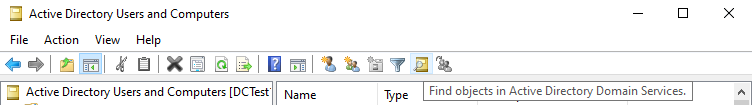
Usually, administrators use the Find feature in the ADUC console because it is the fastest way to find a user account. Select the Find icon and enter the user’s name.
Step 3: Disable the user account
Right-click on the user account you want to disable. From the menu, select Disable Account.
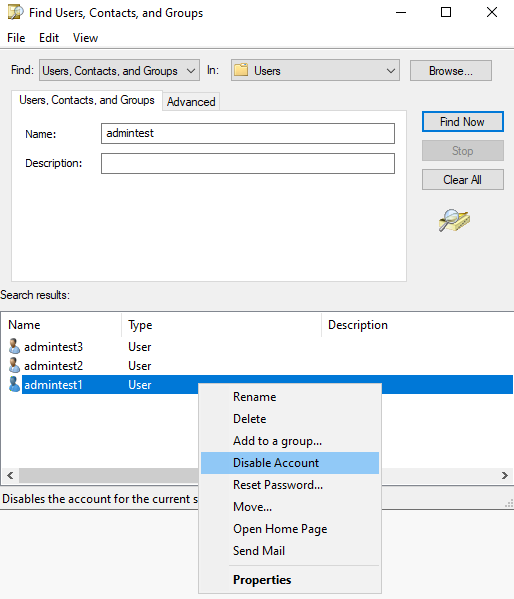
The AD user account icon will immediately display a gray down arrow indicating that the account is disabled.
Simplify AD Account Management with Cayosoft Administrator.
Stop relying on manual scripts. Ensure secure and efficient deprovisioning with automated policies for disabling and managing AD accounts.
Disabling AD users individually via PowerShell
Step 1: Locate the user account
You can use the Get-ADUser cmdlet to locate a single user. The cmdlet’s Identity parameter accepts the value of the AD user object’s SamAccountName or DistinguishedName (DN).
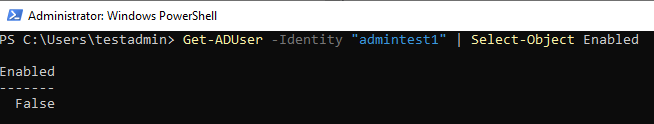
Run the following command to verify if the AD user object to be disabled exists in your AD environment:
Get-ADUser -Identity "admintest1"
Step 2: Disable the user account
The Disable-ADAccount cmdlet uses a similar Identity parameter to disable the AD user object:
Disable-ADAccount -Identity "admintest1"
Since both cmdlets take in a similar set of parameters, you can pipe the output of Get-ADUser directly into Disable-ADAccount. The piping process in PowerShell will reduce the two-step process to a single step.
Get-ADUser -Identity "admintest1" | Disable-ADAccount
Once done, you can verify that the user account has been deactivated by running the command below. The output should return a value of False if the user has been deactivated successfully:
Get-ADUser -Identity "testuser" | Select-Object Enabled
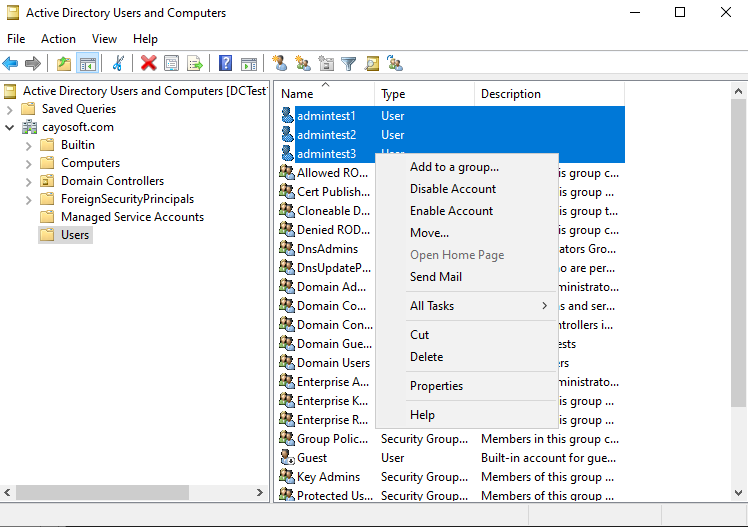
Bulk disabling AD user accounts via GUI
Step 1: Locate the user accounts
In the ADUC console, navigate to the OU, where you can locate the users.
Highlight the desired AD accounts that you want to deactivate.
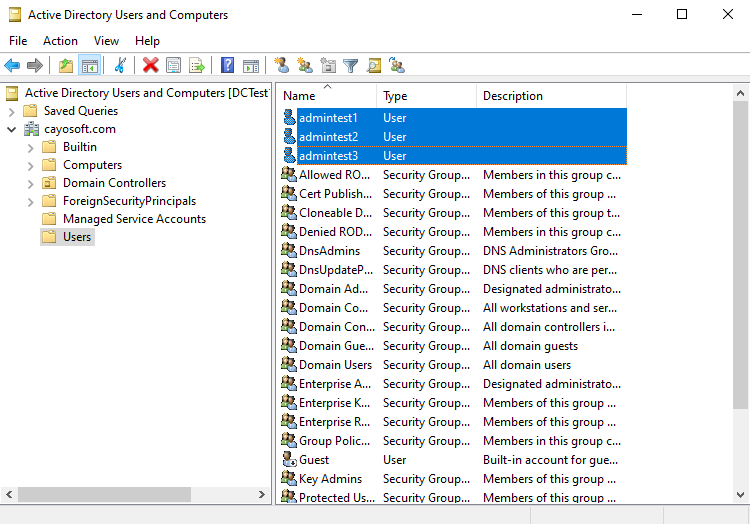
Step 2: Bulk disable the user accounts
Right-click on any of the highlighted accounts and choose Disable Account from the context menu to deactivate all selected accounts simultaneously.
Bulk disabling AD user accounts via PowerShell
PowerShell allows you to efficiently disable multiple users simultaneously through various methods. Like disabling AD users individually in the previous section, you need to start by knowing which user accounts to deactivate.
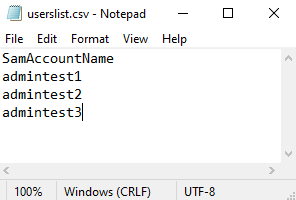
Step 1: Prepare the list of users
When preparing a user list, this information can come from various sources. Here are some common examples.
CSV files
Create a CSV file containing all the SamAccountNames of the AD user accounts that you want to deactivate, with one entry per line.
Step 2: Bulk disable the user accounts
Right-click on any of the highlighted accounts and choose Disable Account from the context menu to deactivate all selected accounts simultaneously.aEnsure that the column’s header is also called SamAccountName, which will act as the object attribute when called later. Use the Import-CSV cmdlet to save the list’s contents in a variable.
$userslist = Import-CSV "C:\Temp\userslist.csv"
AD organizational units
You can also use the Get-ADUser cmdlet to filter all users within a specific OU:
$userslist = Get-ADUser -Filter * -SearchBase "OU=Users,DC=CAYOSOFT,DC=com"
The cmdlet accepts the SearchBase parameter, the value of which contains the OU DN.
AD filter
Unlike the previous command, if you do not wish to select all users in a specific OU, you can use the Get-ADUser cmdlet’s Filter parameter to choose only a particular set of users.
For example, you can query for all inactive users who didn’t log into your domain within the last 90 days:
$userslist = Get-ADUser -Filter {LastLogonDate -lt (Get-Date).AddDays(-90)}
Step 2: Bulk disable the user accounts
Once you have your users list, you can deactivate these users in bulk. You may have noticed that all of the commands above are saved in a variable called $userslist. You will make use of this variable together with a process called looping.
In PowerShell, there is a cmdlet called ForEach-Object, a looping cmdlet that iterates through the list of entries inside a variable. You can make use of this to deactivate user accounts in bulk:
$userslist | ForEach-Object { Disable-ADAccount -Identity $_.SamAccountName }
After disabling the accounts, verify their status with the following command:
$userslist | ForEach-Object { Get-ADUser -Identity $_.SamAccountName -Properties Enabled }
In addition to using the ADUC console and PowerShell, numerous tools are available in the market that can provide a better experience in managing AD user accounts. One is Cayosoft Administrator, which includes a customized set of post-deactivation workflows called Suspend to manage deactivated users. Like the examples above, it can also handle individual and bulk disabling of AD users.
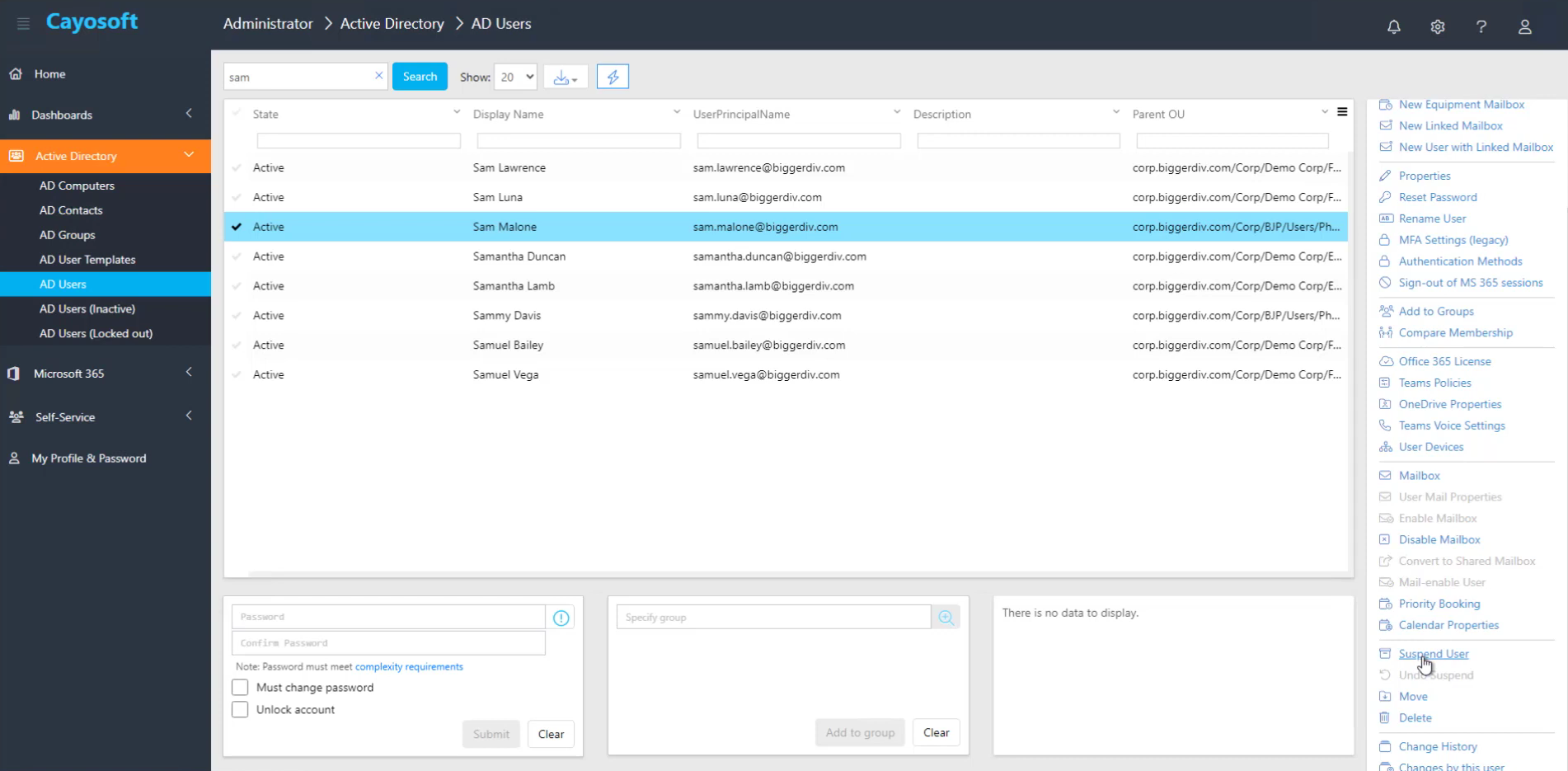
Best practices for disabling Active Directory accounts
The following section explores best practices for managing disabled user accounts in AD.
Regularly review and clean up disabled accounts
One of the best practices for securing your AD environment is regularly reviewing and cleaning up disabled accounts. Deactivated accounts should not be left unattended because they can become an entry point for attackers if reactivated or mismanaged.
Follow these best practices:
- Schedule regular audits of user accounts according to your use case to check whether they need to be deactivated.
- To prevent security gaps, verify that all accounts associated with an inactive user are deactivated, including any accounts used for administrative purposes, service/privileged accounts, or application-specific logins.
- Implement automatic alerting and monitoring for user accounts not used in a specific period.
- Monitor critical AD user criteria, such as the last logged-in time or Kerberos events.
Know when to disable and when to delete
A common question in AD user management is whether to disable or delete a user account:
- Disabling accounts: Deactivate accounts when an employee is on leave, changes roles (and their previous role granted them elevated permissions or access to sensitive data handling), or departs from the organization. You may need the user account for historical data and auditing purposes or when a user decides to return to the organization.
- Deleting accounts: Delete a user account when the associated user profile, permissions, or historical data are no longer needed or when the deactivated account has been idle for a long time.
A typical policy is that when a user leaves a company, their account is deactivated and deleted after thirty (30) days. This practice is heavily used in the industry, especially in large organizations, since it is a good workflow for reviewing and cleaning up user accounts. With Cayosoft Administrator, you can conveniently set up these workflows and ensure a proper user account lifecycle.

Create proper documentation
Documenting deactivated accounts is critical for audit and compliance purposes. This documentation should include details like when and why an AD user account was deactivated. This readily available information ensures that the organization can pass audits and comply with industry regulations.
In addition, you can use PowerShell to generate a report of all disabled user accounts:
Get-ADUser -Filter {Enabled -eq $false} | Select-Object Name,
SamAccountName, LastLogonDate | Export-Csv -Path
"DisabledAccountsReport.csv" -NoTypeInformation
Use an organizational unit for disabled accounts
Many organizations create a dedicated OU for disabled AD accounts to streamline their management. Moving disabled accounts to a specific OU simplifies tracking and auditing, and you can apply group policies to these OUs to enhance security.
In addition, you can also use PowerShell to automate moving disabled accounts to the designated OU:
Get-ADUser -Filter {Enabled -eq $false} | ForEach-Object {
Move-ADObject -Identity $_.DistinguishedName -TargetPath
"OU=DisabledUsers, DC=CAYOSOFT, DC=local" }
When disabling a user with Cayosoft Administrator, you can set up a quick and easy automation that automatically moves the AD user to a specified OU without needing a PowerShell scan like the script above.
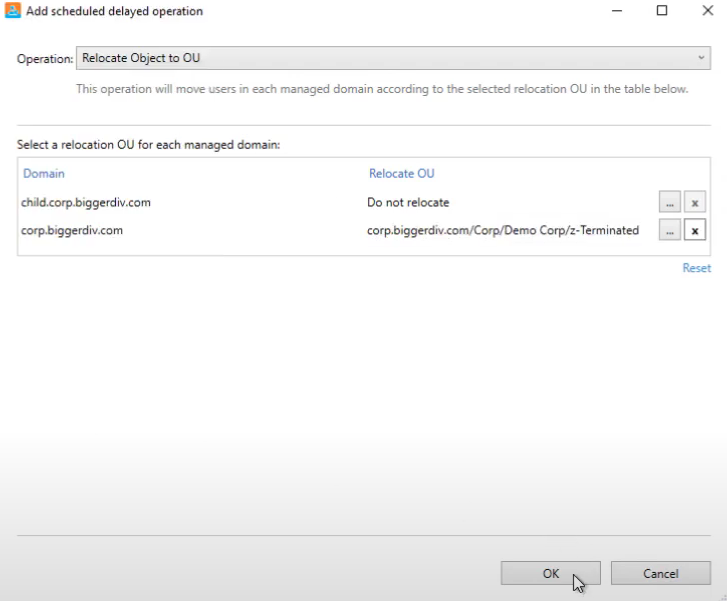
Automate User Provisioning and Deprovisioning in Hybrid Environment.
Learn how to securely and automatically disable user accounts across on-prem and cloud environments with a unified approach.
Final thoughts
Managing user accounts can take a great deal of work, especially in large businesses and organizations. Whether you prefer using the ADUC console or PowerShell, by following these strategies for managing disabled AD accounts, you can ensure that your AD environment remains secure and compliant.
With specialized tools like Cayosoft Administrator, you can significantly reduce the time and error rate when performing user lifecycle operations like deactivating accounts, especially when dealing with large numbers of users.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content