Home » Active Directory Management Tools: Must-Have Features » Active Directory Reporting: Overcoming Challenges and Implementing Best Practices
Active Directory Reporting: Overcoming Challenges and Implementing Best Practices
Learn about the challenges and best practices for Active Directory reporting, including audit logging, health and performance monitoring, and compliance and governance.
Explore the chapters:
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
A common Active Directory (AD) management challenge is that there aren’t many native AD reporting tools that can meet modern business requirements. Native tools like Active Directory Users and Computers (ADUC) are more of a front-end UI for a Jr. Administrator to do routine tasks like password resets.
PowerShell is powerful but complex and requires coding everything from scratch or stitching together modules and custom functions.
Then, there is the challenge of visibility, and alerting. PowerShell is predominantly text and command-line interface-based. Though with some custom coding HTML and style sheets can be used to output graphical displays of scripts that query AD it is not without significant input from an administrator. Scripts and code of this sort are difficult to maintain and difficult to generalize for other use cases.
Additionally, there is the challenge of real-time visibility. Real-time visibility is critical to stop an issue or process before it spirals out of control. With PowerShell, administrators must depend on complex solutions like Task Scheduler or event triggers. This can be helpful, but what is really needed is real-time monitoring and reporting on all important Active Directory events and alerts that are easy for administrators to digest and action.
Finally, there’s the challenge of reporting on cloud Entra ID environments, especially hybrid environments where information is scattered throughout various systems and can often be overwhelming.
Native AD tools and reporting capabilities have shortcomings. Because of this, most companies rely on or require 3rd party tools for reporting on AD and Entra ID. Logging is complex and difficult to organize, normalize, correlate, and draw useful conclusions from without an intelligent third-party tool. And in reality, Microsoft doesn’t offer much in terms of reporting out of the box.
Solutions like Cayosoft seamlessly report and audit the AD hybrid environment, providing the comprehensive visibility and actionable insights that native tools lack. The platform simplifies the process of gathering, analyzing, and presenting AD data, enabling administrators to effectively manage and secure their environments.
This article will delve into the main concepts of Active Directory reporting and seven best practices to provide administrators with a framework to implement AD reporting that addresses modern business requirements.
Summary of key Active Directory reporting concepts
The table below summarizes the seven AD reporting concepts this article will explore in detail.
| Concept | Description |
|---|---|
| Audit logging | Enable AD Audit logging to collect activity like user logins, group membership changes, and admin actions. Audit logging is also a key enabler of anomaly detection. |
| Health and performance monitoring | Monitor health and metrics for things like DNS, Domain Controller Replication, LDAP queries, Azure connect, and use of resources |
| Security reporting | Create security reports to identify potential vulnerability vectors, weak passwords, permissions creep etc. |
| Change monitoring | Auditing and tracking of changes for critical AD objects |
| Capacity monitoring | Reporting on capacity of Domain Controllers and server resources to ensure sufficient room to grow within projected needs of the organization. |
| Backup and recovery reporting | Monitor the status of regular backups and verify validity. |
| Compliance and governance | Ability to create reports to show compliance with security policies like password complexity, SOX compliance, etc. |
Active Directory reporting concept #1: Audit logging
Enabling auditing logging is an essential step for effective AD security and reporting. Audit logging records who did what, when, and if they were successful. For example, login attempts can be captured and time-stamped by an audit logging policy that also records success or failure.
Microsoft Active Directory (AD) provides detailed group policies that give you granular control over the level of audit logging enabled and the systems to which the policy will be deployed.
To enable audit logging in Microsoft AD, create a GPO and navigate to:
Computer Configuration → Policies → Windows Settings → Security Settings → Advanced Audit Policy Configuration → Audit Policies:
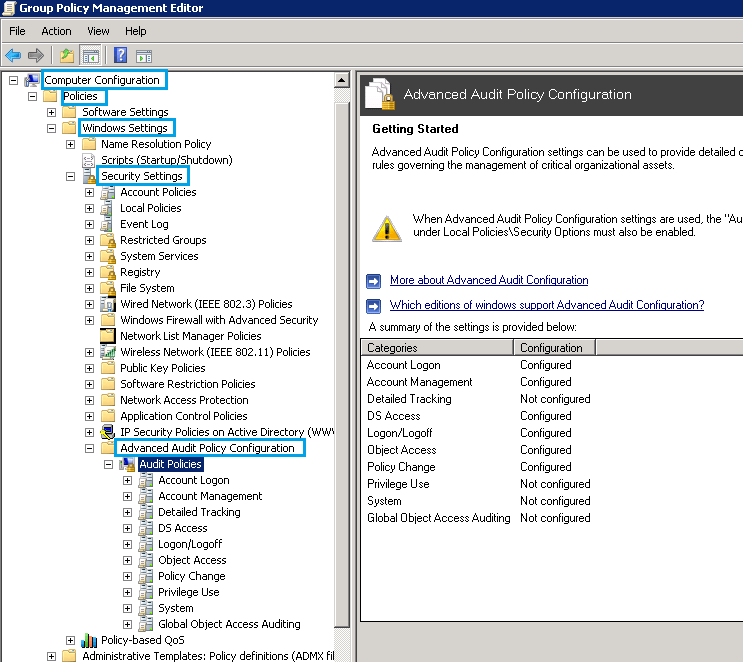
In addition to setting categories as configured/unconfigured an administrator can also choose if success, failure, or both will be logged. There is a benefit to both because a successful login from a previously non-privileged account can indicate privilege escalation by a nefarious actor, and a high number of failures indicate an ongoing brute-force attempt.
Turning on audit logging for all systems is a good idea. Note that audit logging needs to be enabled on domain controllers for accountability since they will allow or deny directory actions, authentications, Kerberos tickets, account changes, and user logins. Audit logs are stored as events in Windows Event Logs and can be viewed remotely or on the local system in the Windows Event Viewer.
The built-in audit logging is a good start, but Microsoft Sysinternals provides a well-tested add-on tool called Sysmon that amplifies built-in audit logging capabilities.
Sysmon expands Windows audit logging capabilities to provide visibility into network connections, process creation, and file system changes. Sysmon also helps identify indicators of compromise or gives an administrator the foundation to contain or even stop compromises before they happen. In the event of an actual breach, Sysmon provides vital information for incident response and identifying the source and extent of the compromise.
The main challenge with Sysmon and with Windows event logging in general is they are reactive tools that do not proactively enable organizations to mitigate risks. Because Windows event logs aren’t correlated in any way, there is no alerting or pattern recognition built in.
To be effective, a third-party SIEM tool is a must-have. One that can ingest and normalize all the audit logs including those gleaned from Sysmon to identify irregular patterns, determine potential signs of compromise, and alert an administrator on critical events without bombarding with false positives.
With Cayosoft Administrator and Guardian, additional audit logging from AD isn’t even necessary because the platforms don’t rely on event logs. Event logs are typically configured to roll over so quickly that even a SIEM will not pick them up and store them. Guardian though captures events with easy, clear, and concise information and can alert. Anything captured in Guardian can also become a report and be emailed or sent to collaboration channels. This event capture setup gives Guardian the capability to do a single click rollback of unwanted changes at the attribute level. Rollbacks can be automated to protect sensitive objects in hybrid environments from unapproved changes such as conditional access policies, roles, GPO’s etc.
In addition, Guardian offers a threat module that is 100% ready to go out of the box and requires zero config. The module can not only conduct scans on schedules, but can also audit changes to determine if they pose a threat and can produce real-time alerts based on this audit monitoring.
Besides Guardian’s report generation capabilities, Cayosoft Administrator also logs changes made by admins in detail and can generate scheduled reports. Administrator can also use the information it receives to perform automated environment clean-ups. For example, Cayosoft Administrator can find disabled users that are older than a certain time frame and perform any action needed like moving to an “Inactive” OU, removing attributes and groups, or deleting. Depending on the circumstances, it can also look for unoptimized Microsoft license usage and make recommendations for license downgrade or upgrade.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Active Directory reporting concept #2: Health and performance monitoring
In AD monitoring, audit logging is critical for accountability and security. However, you can have the most secure AD in the world, yet if your DNS stops working, the network and business operations come to a costly screeching halt.
AD is a complex machine made up of central domain controller servers as well as core services that are integrated and essential to functionality such as DNS, DFS replication, LDAP, Kerberos, and more. This gets even more complex for hybrid deployments as there are often added components such as Azure-AD connect sync servers that rely on a healthy on-premise AD environment to correctly synchronize with the Entra ID (formerly Azure AD) cloud.
Having a system that can monitor DNS queries in real time and at regular, set intervals is important because if DNS stops working for any reason (e.g., a forwarder goes offline, firewall misconfiguration, etc.) it can take down the entire network.
AD replication is also important to monitor because it can be the canary in the coal mine for larger problems. Replication failures can stem from any number of causes, things like Network Time Protocol (NTP) being out of sync on Domain Controllers, or a poor uplink to a remote site with a remote Domain Controller.
Microsoft provides some native tools that can help in monitoring health and performance. Server Manager can be used to monitor core services like DNS, DHCP, Hyper-V, etc. Task Manager and resource monitor provide detailed real-time breakdowns of system resources like CPU, Memory, and Disk I/O. For historical data, administrators can use Performance Monitor. These tools are good in a pinch or for a quick look. Still, they either lack historical data or, in the case of a Performance Monitor, are challenging to configure, must be done individually, and require manual interpretation and analysis of data.
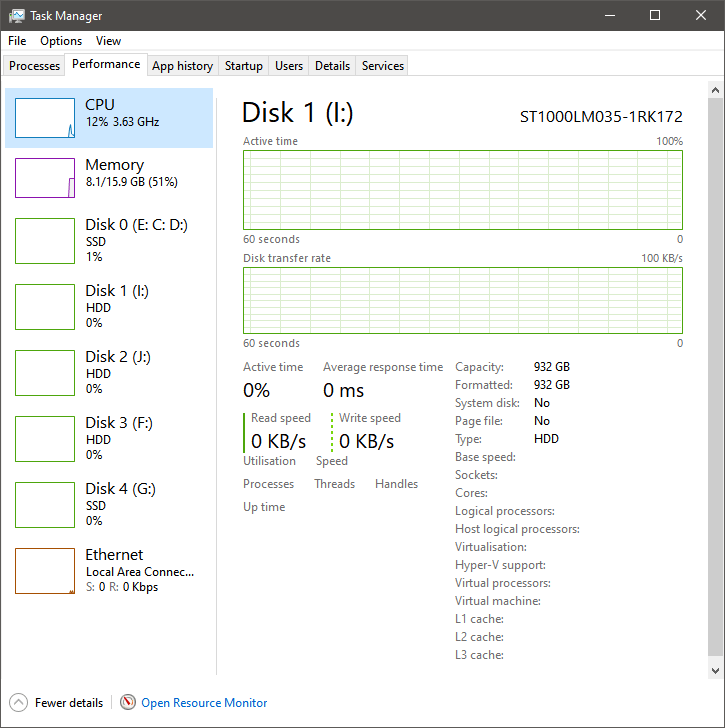
Command line utilities like repadmin and ntdsutil are also go-to’s for checking AD health.
The newer Entra Connect Health service is a cloud-based service tool that can provide insights into performance, replication, and other health issues and alert administrators when there are problems. It requires the installation of an agent on each Domain Controller.
Unlike audit logging, Microsoft does provide some good tools for monitoring health and performance. However, they still often leave AD admins without full context and understanding of the source and scale of a problem related to AD.
While Cayosoft doesn’t specifically focus on health and performance, the platform can audit for threats related to Entra ID and AD misconfigurations or changes happening that can impact health. Some examples include changes to the SYSVOL share or Active Directory sites and services.
Active Directory reporting concept #3: Security reporting
Native tools are pretty thin when it comes to security reporting. An administrator is left with things like custom SQL reports assuming they have actionable data being piped into SQL databases or creating SQL queries to interact with other systems that integrate with AD, such as Microsoft Endpoint Configuration Manager (MECM), and this is again assuming these tools are already available. Without tools like this, custom PowerShell scripts must be created to query AD and other systems and generate reports. It is possible to generate reports in a graphical format with PowerShell. Still, it is very cumbersome for an administrator to take this on, and it is a very manual process, not to mention the significant maintenance burden.
Security reporting is essential to help identify issues such as weak passwords, suspicious logins, permissions creep, and unnecessary administrative access. This need spans both on-premise AD and Entra ID, assuming an organization uses both, which is now the norm. Trying to roll your own solution for all of this is typically unmanageable. Because it is such a vital resource to operations, investing in a product can help with security reporting and overall compliance makes business sense.
Cayosoft’s product suite allows an administrator to set parameters on user data entry to ensure data integrity and fulfill auditing requirements for regulations such as SOX and HIPAA. Besides just placing guardrails around data entry, Cayosoft’s Administrator can also help implement a granular least-privileged delegation model.
In essence, you can give your IT team just the right level of access they need to do their jobs. This means you can remove the broad “admin” rights that let them change anything and everything. Instead, you can be very specific:
- Need someone to reset passwords? They get the “password reset” key, and nothing else.
- Need someone to manage user accounts? They get the “user account” key, and nothing else.
This way, you’re limiting the potential damage if someone’s account is ever compromised..
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Active Directory reporting concept #4: Change monitoring
Change monitoring is vital to security and active directory reliability. Knowing who did what, and when, and being alerted on critical changes is paramount to a systems administrator.
Ideally, you should monitor built-in privileged accounts and groups like Domain Admins, Enterprise Admins, Administrators, and any custom groups with high levels of access. You need to be alerted about any changes to these groups or the actions taken by these accounts. This includes crucial Domain and Forest-level changes, such as adding a new Domain Controller or deleting an Organizational Unit (OU). In hybrid setups, the equivalent to Domain Admins such as Global Admins should be monitored for changes in membership and actions.
There aren’t good automated ways to monitor changes with built-in AD tools. A savvy administrator could roll their own utility to comb through Domain Controller logs and generate email alerts based on event ID. But, this is extremely tedious work not to mention highly skilled work that often becomes unsustainable.
Cayosoft offers a better way by providing a unified change monitoring for your entire hybrid environment—AD, Entra ID, and Office 365—with advanced auditing and real-time threat detection features:
- Cayosoft Guardian captures changes with clear and concise information, going beyond basic event logs that can be overwritten too quickly.
- Receive actionable alerts the moment critical changes occur, allowing you to respond swiftly to potential threats.
- Guardian enables single-click rollback of unwanted changes, even at the attribute level. The granular control allows you to undo specific modifications without affecting other configurations.
- Configure automated rollbacks for highly sensitive objects like conditional access policies, roles, AD privileged groups, and Group Policy Objects (GPOs) to prevent unauthorized changes.
- Guardian includes a built-in threat module that requires zero configuration. It actively analyzes changes to identify potential threats and provides real-time alerts, helping you proactively secure your environment.
- Any event captured in Guardian can be easily transformed into a report and shared via email or platforms like Microsoft Teams.
Active Directory reporting concept #5: Capacity monitoring
Being able to monitor the capacity of systems that are responsible for Active Directory operations is an important facet of any monitoring plan. Physical or virtual servers must have adequate capacity to support the number of connections and directory operations that occur during normal lines of business. Reporting on CPU, memory, and disk space hardware capacity is important for real-time performance. Additionally, monitoring and reporting for protocols like DNS and LDAP is also essential. These are core services to AD, and hiccups will almost immediately be noticeable.
Capacity monitoring should also provide forecasting insight into whether the hardware has sufficient resources to accommodate projected growth in authentications and traffic.
Windows provides some native tools like resource monitors that can help an administrator understand if there is a server capacity issue and what the cause might be. But, with AD, often, the source of a problem could be something related to AD operations like DNS or replication. Domain Controller or other server logs may provide more insightful, actionable clues. Cayosoft Guardian ingests logs, makes them much more readable for an Administrator, and allows the dots to be connected to see if the root cause is related to AD.
Watch a demo video of Cayosoft’s hybrid user provisioning
Active Directory reporting concept #6: Backup and recovery reporting
Because AD is critical to day-to-day operations, backing up AD is equally critical. AD is a database and databases can become corrupt, domain controllers can get out of sync, and servers sometimes fail. Simply backing up is not sufficient. You must regularly verify and validate backups to be certain they will work in a worst-case scenario.
Given the importance of AD backups, an ironclad backup system is needed. Although Windows server has a built-in backup capability, the granularity offered is usually insufficient to meet the needs of most organizations. Usually, organizations will want a robust backup tool that can do incremental and differential backups in addition to full backups. Beyond this there must be some sort of intel on whether backups have been completed successfully, and if they are usable backups. Also, for organizations using hybrid AD with Entra ID, there should be reporting on the status of Entra ID backups.
Native backups can be inefficient, including the entire operating system and potentially reintroducing malware during recovery. They also lack easy validation and cloud integration, making it difficult to ensure recoverability and off-site protection.
Cayosoft Guardian offers a powerful alternative with granular recovery, instant restores, and a clean machine approach. It automates the recovery environment setup and works across different hardware and operating systems. Your backups are encrypted and can be seamlessly integrated with AWS or Azure for off-site storage.
Guardian also allows you to easily spin up a test environment on demand. This is perfect for validating your backups and for safely testing changes like GPO updates, schema modifications, or hotfixes before applying them to your live AD.
Key Benefits:
- Avoid reintroducing malware by backing up only essential AD components.
- Minimize downtime with instant object and attribute recovery.
- Simplify recovery with automated environment setup and cloud integration.
- Enhance security with encrypted backups and off-site storage.
- Proactively test changes in a safe environment to prevent issues.
Active Directory reporting concept #7: Compliance and governance
Maintaining compliance with whatever policies and rules an organization is subject to is often one of the key jobs a systems administrator is tasked with. Part of compliance is having policies in place and tools to accomplish them. Another part is being able to prove that the policies in place are actually working.
Organizations are subjected to different compliance and governance policies depending on what laws and/or organizations regulate them. Some companies in certain industries may have very little oversight from the government or agencies that regulate them, whereas others may have strict rules like SOX compliance or PCI-DSS that they must comply with.
Trying to achieve and maintain compliance with strict laws and regulations is a challenging task. Achieving or maintaining compliance with custom scripts, Group Policy Objects (GPOs), and registry hacks in most cases turn out to be unsustainable.
Cayosoft Guardian standardizes changes across both on-prem AD and Entra ID cloud (formerly Azure AD), and the standardization makes it much easier to maintain compliance, since setting things up correctly in one place will make unified changes. Queries can also be saved, so frequently requested reports can be pulled easily, which can help provide evidence of compliance. Guardian also acts as an ITDR (Identity Threat Detection and Response) solution for AD and Entra ID, helping you meet compliance requirements related to threat detection, investigation, and response.
Cayosoft Administrator complements Guardian by allowing you to utilize criteria-based automation for maintaining clean group memberships and preventing unauthorized access.
In addition, Cayosoft Administrator offers the following features:
- Enable group and resource owners to regularly certify memberships, ensuring adherence to internal policies and regulatory requirements.
- Implement a granular least-privilege access model, making it easier to comply with regulations and policies that mandate strict access controls.
- Generate detailed reports on a wide range of AD and Entra ID attributes, providing the evidence needed to demonstrate compliance.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Active Directory reporting is vital to network and business operations. Reporting takes on many forms from audit logging to health and performance monitoring. Native tools can address some enterprise use cases. However, for others, native tools such as custom PowerShell scripts typically fall short in both their capabilities and sustainability.
Microsoft’s lack of unified reporting creates a fragmented view of your enterprise’s data. Struggling with manual data collection, scattered reports, and compliance headaches? It’s time for a change.
Cayosoft empowers IT teams with unified reporting across on-premises Active Directory, Entra ID, and Microsoft 365, enabling data-driven decisions and streamlined operations.
To know more about Cayosoft’s comprehensive AD reporting capabilities, book a demo here.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content