Home » Active Directory Management Tools: Must-Have Features » Mastering Active Directory Groups: A Deep Dive into Types, Scopes, and Management Strategies
Mastering Active Directory Groups: A Deep Dive into Types, Scopes, and Management Strategies
Learn how to effectively organize and manage Active Directory (AD) groups of various types and scopes, including hybrid and dynamic groups, using advanced strategies and best practices.
Explore the chapters:
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Active Directory (AD) groups are the key objects facilitating the organization, management, and assignment of permissions for user accounts, computer accounts, and other resources in a Windows environment. Understanding and leveraging the various types and scopes of groups is essential to maintaining a secure and efficient Active Directory setup.
Each group type serves a unique purpose. AD groups can also have different scopes, including domain local, global, and universal. The scope determines the reach of the group and its applicability across domains within an AD forest. Effective management of these groups is critical for maintaining access control, security posture, and allocation of resources within an organization.
Native AD GUI tools, and especially command line interface ( CLI) tools like PowerShell, have come a long way in their ability to automate and manage AD groups. However, groups and group membership can quickly become unmanageable in even a mid-sized organization. Challenges such as nested group memberships, complex permission inheritance, and cross-domain group dependencies can create administrative overhead and potential security risks.
In this article, we delve into the technical intricacies of AD groups, exploring their types, scopes, and the challenges associated with their management at scale. We also discuss advanced strategies and best practices for optimizing group management, including automation, security hardening, and leveraging third-party tools to address the limitations of native AD tools.
Summary of key concepts related to Active Directory groups
| Key elements | Description |
| Group types | Groups can be broken down into three categories, which organize users and devices for various purposes, such as security, distribution, or administration. |
| Group scopes | The scope of a group defines its reach and visibility within Azure AD, determining which objects the group can contain and how it can be used. |
| Hybrid on-premises/cloud Entra ID groups | Groups that span both on-premises AD and cloud-based Azure Active Directory enable seamless management and access control for resources in both environments. |
Group types
Active Directory (AD) groups play an important role in organizing and managing access to resources within a Windows environment. There are three primary types of groups in Active Directory:
- Security Groups: These groups are primarily used to manage access permissions to resources such as files, folders, and network shares. Security groups can be assigned permissions directly or nested within other security groups to simplify access management. It is a best practice to assign permissions to security groups rather than individual users because this provides easier management and better security control.
- Distribution Groups: Distribution groups are used for email distribution lists. They’re not intended for security purposes but rather for sending emails to multiple recipients. Distribution groups don’t have security permissions associated with them and are commonly used for sending announcements, newsletters, or other non-sensitive information.
- Dynamic Distribution Groups: This type of group only exists in Entra ID and is a special type of distribution group that automatically updates its membership based on a set of criteria defined by an administrator. For example, a dynamic distribution group might include all users from a specific department or location. This dynamic updating reduces administrative overhead and ensures that the group membership stays current.
Managing these groups can be challenging using native tools such as Active Directory Users and Computers (ADUC) or PowerShell scripts, particularly in large and complex environments. Challenges include adhering to consistent group naming conventions, enforcing group membership via reviews and audits, and automating group lifecycle management tasks such as provisioning, deprovisioning, and the expiration of groups. Sometimes it is a case of anything being possible but needing to ask yourself whether you have the resources to realistically accomplish it and get it right every time. Frequently, the answer is “no” when it comes to using only native tools like PowerShell and ADUC.
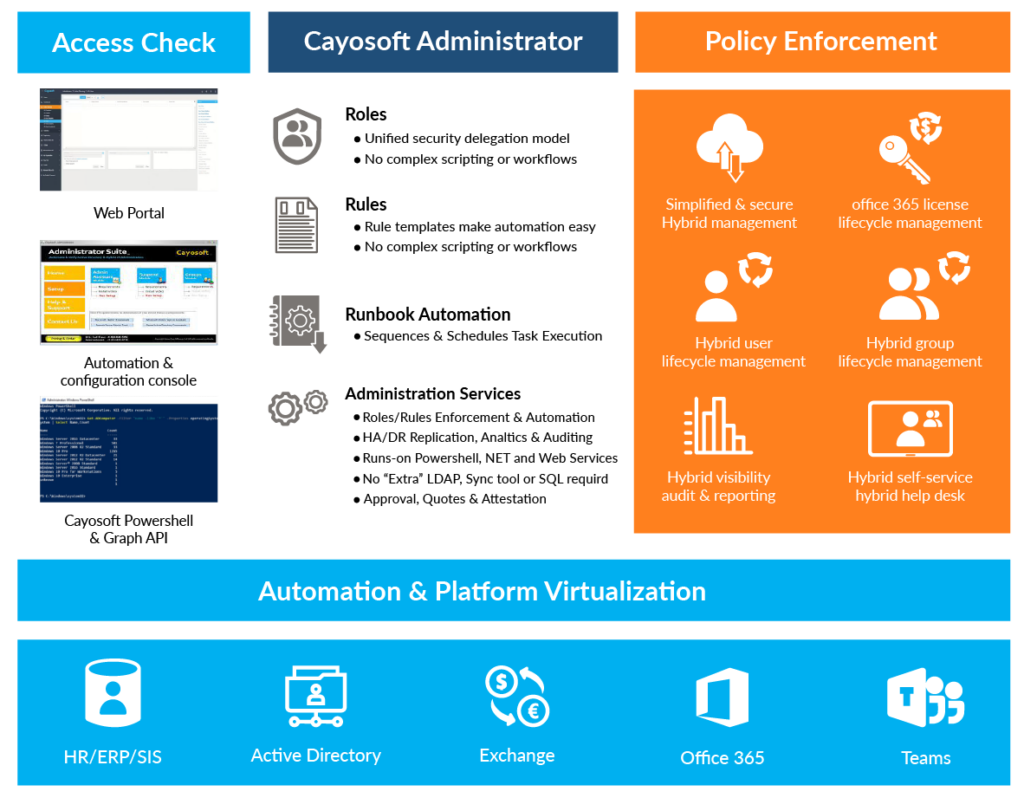
Cayosoft’s dynamic groups take automation a step further by intelligently managing group membership based on predefined attributes and criteria. For example, when an employee gets a promotion with a new title, the new title will auto-trigger new group memberships based on the role their title falls under. This facilitates much easier group lifecycle management and sustainability.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Group scopes
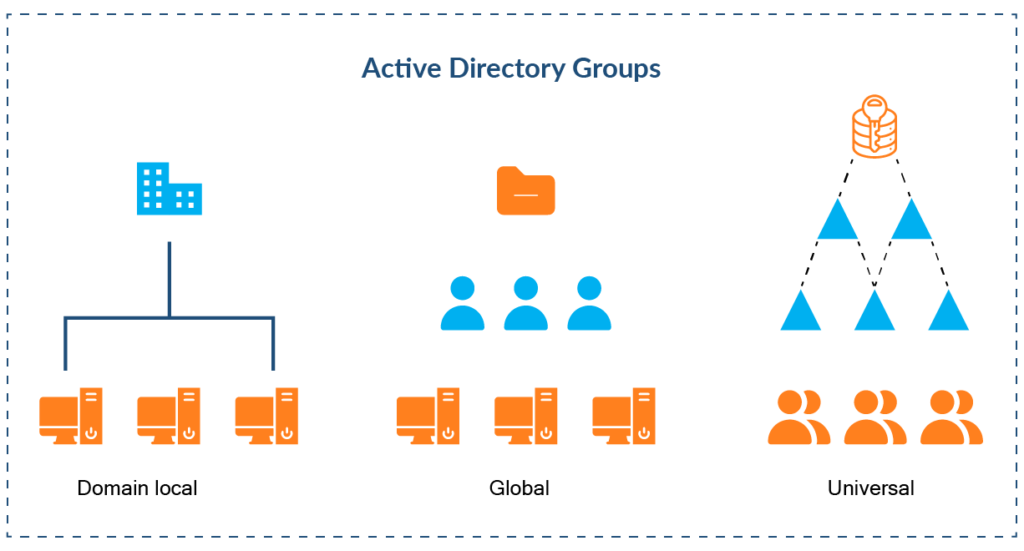
- Domain Local Groups: These groups are for assigning permissions within a single domain. They can contain users, groups, and computers from any domain within the forest. Domain local groups are typically used to grant access to resources within a specific domain, allowing for granular control over permissions.
- Global Groups: Global groups are used to organize users who share a common access need across multiple domains within a single forest. They can contain users and other global groups from the same domain. Global groups are often used to simplify access management by aggregating users with similar roles or responsibilities.
- Universal Groups: Universal groups are the most flexible for organizing users and resources across multiple domains in a forest. They can contain users, groups, and computers from any domain in the forest and can be used to assign permissions across domains. Universal groups are particularly useful in large, multi-domain environments where centralized access management is necessary.
A recommended approach for managing different group scopes involves designing a group nesting strategy that balances simplicity with scalability and manageability. To manage permissions efficiently, a typical practice is to use a combination of global and universal groups. Global groups can be used to organize users within domains, while universal groups can be used to aggregate global groups and assign permissions across domains.
Managing group scopes with native tools like Active Directory Users and Computers (ADUC) or PowerShell scripts is challenging, especially in large and complex environments. Native tools provide basic functionality for managing group scopes but may become unsustainable at scale. With Cayosoft, administrators can define and enforce consistent group scope assignments based on organizational policies and best practices. Cayosoft’s automation features streamline group management tasks such as group creation, modification, and deletion, reducing manual effort and minimizing the risk of misconfigurations. Additionally, it provides reporting and auditing capabilities to track changes to group scopes and ensure compliance with security policies and regulations.
Hybrid on-premises/cloud Entra ID groups
In addition to on-premise AD groups, Entra ID also has its own set of groups. These Entra ID groups play a crucial role in managing access to resources and applications within the Entra cloud environment. The following are the different Entra ID groups, each serving a specific purpose. Note that some of the group types do not map one-to-one with the on-premises AD groups, which adds management complexity in hybrid environments:
- Security groups: Entra ID security groups are used to manage permissions to Azure resources such as Azure Virtual Machines, Azure Storage, or Office 365 applications. Users can be directly added to security groups, and these groups can also be nested within other groups for easier management.
- Microsoft 365 Groups: Microsoft 365 Groups are a type of Entra ID group that provides collaboration features across various Microsoft 365 services like Outlook, Teams, SharePoint, and Yammer. These groups are designed to make it easier for users to collaborate and share resources such as emails, documents, and calendars.
- Distribution Groups: Distribution groups in Entra ID are similar to distribution groups in traditional Active Directory. They are primarily used for email distribution lists and do not have security permissions associated with them. Distribution groups can be used to send emails to multiple recipients within an organization.
- Mail-Enabled Security Groups: This group combines the functionalities of both security groups and distribution groups. Mail-enabled security groups can be used for both granting access permissions to resources and sending emails to multiple recipients.
- Dynamic Groups: Entra ID dynamic groups automatically update their membership based on rules defined by administrators. These rules can be based on user attributes such as department, job title, or location. Dynamic groups help ensure that users have the appropriate access to resources based on their attributes without manual intervention.
Understanding the differences between these groups is essential for effectively managing access and collaboration within the Azure environment. Depending on the requirements of the organization, administrators can leverage different types of groups to streamline access management and collaboration processes.
It’s worth noting that while Entra ID groups offer powerful capabilities for managing access and collaboration, challenges may arise in ensuring compliance with organizational policies at scale. This can be particularly challenging in hybrid on-premises/cloud environments where there may be groups in AD that don’t map one-to-one with Entra ID groups in terms of type, scope, role, or membership.
Cayosoft bridges the gap between on-prem and cloud Entra ID groups and provides a single pane of glass through which to manage the entire group lifecycle. The platform offers advanced group lifecycle management capabilities, automation of group provisioning and deprovisioning, enforcing naming conventions, and ensuring compliance with security policies and regulations within the Entra ID environment.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Best practices for managing AD groups
Efficient group management in a diverse environment encompassing on-premise AD and Microsoft Entra ID relies on a set of best practices, techniques, and an understanding of the limitations inherent in native tools.
Here are some recommended practices in three areas.
Use of native tools for group management
One critical best practice here is to establish a consistent naming convention for groups across both AD and Microsoft Entra ID, ensuring clarity and ease of administration. This uniformity aids in quickly identifying the purpose and scope of each group, facilitating efficient management and reducing the likelihood of confusion or mismanagement.
Adopting a role-based access control (RBAC) strategy is another key practice that enables organizations to assign permissions based on users’ roles and responsibilities. RBAC simplifies access management by grouping users with similar job functions into roles and assigning permissions accordingly. This approach streamlines access control and enhances security by ensuring that users only have access to the resources necessary for their roles, minimizing the risks associated with permissions creep and unauthorized access.
Despite following the above practices, it is worth noting that native tools have limitations, particularly in hybrid environments. Native tools often lack centralized management capabilities across multiple identity providers, requiring administrators to navigate between different interfaces for AD and Microsoft Entra ID management. It is important to adopt tools that offer advanced automation features for group lifecycle management tasks, ultimately helping reduce manual effort and potential errors in managing groups.
Scalability, security, and lifecycle management of groups
Native tools in both Active Directory and Microsoft Entra ID lack scalability, security, and lifecycle management, especially in complex and hybrid environments. In most cases, these tools lack the automation and centralized management capabilities necessary to efficiently handle large numbers of groups and users. Manually creating, modifying, and deleting groups can be time-consuming and error-prone, leading to inefficiencies and potential security risks.
Speaking of security, ensuring adherence to security best practices—such as enforcing least privilege access and regularly reviewing group memberships—can be difficult to achieve with native tools alone. Without robust automation and reporting capabilities, administrators may struggle to maintain a secure environment and respond effectively to security threats and compliance requirements.
The lifecycle management of groups presents further challenges with native tools. Managing the creation, modification, and deletion of groups throughout their lifecycle requires careful attention to detail and adherence to best practices. However, native tools may lack features for automating routine group management tasks, enforcing naming conventions, and tracking changes to group memberships over time, making it challenging to maintain consistency and compliance.
A recommended practice is to employ scripts or automation tools like Cayosoft to streamline routine tasks like group creation, modification, and membership updates, thereby reducing manual errors and saving time. It is also important to implement automated workflows to create, modify, and delete groups based on predefined rules or triggers (e.g., new employee onboarding, department changes, or employee termination). This ensures timely and accurate group management, reduces manual effort, and minimizes the risk of errors.
Watch a 12-minute product demo video of Cayosoft’s hybrid user provisioning
Compliance with policies
Native tools like PowerShell offer powerful capabilities for managing the policy compliance of Active Directory and Microsoft Entra ID environments, but they come with limitations that can impact compliance with organizational policies. One significant limitation is the lack of built-in controls and guardrails to enforce policy compliance automatically. While PowerShell provides extensive scripting capabilities for automating administrative tasks, ensuring that scripts adhere to organizational policies requires manual validation and oversight, which can be time-consuming and prone to errors.
Additionally, PowerShell scripts may lack the granularity needed to enforce specific policies comprehensively. For example, enforcing naming conventions for group creation or ensuring consistent application of access controls across different resources may require complex scripting logic that is difficult to maintain and troubleshoot. Without the proper controls in place, administrators may inadvertently violate policies or overlook critical security requirements when using PowerShell scripts for managing AD and Entra ID environments.
Adopt a policy-as-code framework to define and enforce organizational policies for AD and Microsoft Entra ID environments. Use declarative configuration files (e.g., JSON or YAML) to describe policies such as naming conventions, access controls, and password requirements. These configuration files can be version-controlled and integrated into a CI/CD pipeline for automated testing and deployment, ensuring consistent and auditable policy enforcement.
Cayosoft simplifies AD compliance by automatically enforcing naming conventions and policies throughout the account lifecycle. This reduces the risk of human error and ensures consistent adherence to security best practices, relieving the burden on IT administrators.
If you still prefer to use PowerShell scripts, establish a process for mandatory code reviews of all scripts that interact with AD or Entra ID environments. This ensures that scripts are scrutinized by multiple stakeholders for policy compliance, security vulnerabilities, and adherence to best practices. Also, consider using a code review tool to streamline the review process and ensure consistent feedback.
Leveraging Cayosoft for groups
As described above, native tools such as PowerShell in Active Directory and Microsoft Entra ID environments offer considerable flexibility and functionality, but they come with significant limitations in the complexity and manual effort required to perform routine administrative tasks, especially at scale. PowerShell scripts also lack the automation and centralized management capabilities needed to streamline group management across both AD and Entra ID environments seamlessly.
Cayosoft addresses the limitations of native tools by providing a unified platform for managing Active Directory, Entra ID, and hybrid groups.
Cayosoft’s lifecycle management features help organizations manage the entire lifecycle of groups, from creation to deletion, following best practices and compliance requirements. Its centralized management capabilities make it easier to manage groups across diverse identity platforms, including large-scale environments with numerous groups and users. The platform automates routine group management tasks such as group membership reviews, expiration, and cleanup, ensuring that groups are properly maintained and aligned with organizational policies throughout their lifecycle. In addition, Cayosoft’s robust auditing and reporting capabilities enable organizations to track administrative activities effectively, identify policy violations, and ensure compliance with regulatory requirements.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Effective management of groups across AD, Microsoft Entra ID, and hybrid environments requires careful consideration of native tool limitations and the adoption of solutions like Cayosoft. Native tools such as PowerShell offer powerful capabilities but lack automation, centralized management, and robust auditing features necessary for efficient group management at scale.
Cayosoft addresses these challenges by providing a comprehensive platform for managing groups across diverse identity platforms. Powerful automation features streamline group provisioning, modification, and deletion processes, reducing manual effort and minimizing the risk of errors. The platform’s centralized management capabilities enable organizations to enforce consistent policies, implement role-based access controls, and ensure compliance with regulatory requirements.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content