Home » Active Directory Management Tools: Must-Have Features » Active Directory Group Policy Management
Active Directory Group Policy Management
Learn 9 essential best practices to effectively manage group policy and maintain security and efficiency in your environments, with insights from Cayosoft, a leading AD administration software company.
Explore the chapters:
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Group policy is essential for Active Directory (AD) administrators seeking to manage user and computer configurations. However, implementing effective group policy requires more than just a basic understanding. When properly utilized, group policy brings a host of advantages. The best practices below apply to AD administrators looking to keep their environments stable, secure, and efficient. This article will explore best practices with examples, explaining how to implement them while incorporating insights from Cayosoft, a industry-leading Active Directory administration software. Below is a list of topics we will cover.
| Best Practice | Description |
| Begin with Default Policies | Do not modify the default domain policies unless necessary. Create new policies for custom settings. |
| Use Descriptive Names | Give organizational units (OUs)and Group Policy Objects (GPOs) descriptive names that reflect their purpose. |
| Have a Recovery Plan | Take a backup of all GPOs to maintain stability and consistency in an environment. |
| Limit Root Domain GPOs | GPOs shouldn’t be linked to the root-level domain, because these will apply to all users and computers. Instead, use the OU root level. |
| Organize OU Structure | Having an efficient OU structure makes it easier to manage group policies. |
| Do Not Disable GPOs | Unlink a GPO instead of disabling it. |
| Simplify GPOs | Create smaller policies instead of applying too many settings to one GPO. |
| Test Before Deploying | Before applying group policies to a production environment, always test changes in test environments. |
| Keep Track of All Changes | Enabling auditing to track changes in group policies is a crucial step in ensuring security and compliance. |
Group Policy Best Practices
These nine best practices are critical steps administrators can take to make environments secure and efficient.
Begin with Default Policies
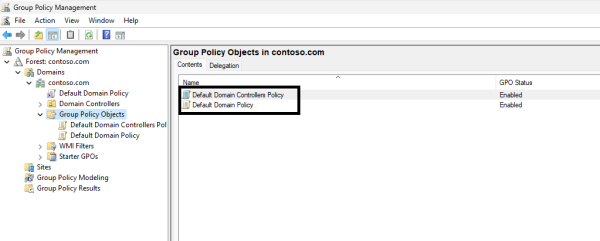
There are two default policies in Active Directory: the default domain policy and the default domain controllers policy. These two policies should be left unchanged, even though it may be tempting to put domain-wide settings here. Altering these default policies might disrupt the consistent state of your AD environment.
New policies containing custom rules, like password policies and domain account lockout policies, should be created. The two policies shown below, the default domain policy and the default domain controllers policy, serve as the foundation of your AD infrastructure. They contain a range of settings that enforce domain security and ensure proper domain functionality.
Use Descriptive Names
Giving objects descriptive names provides immediate insight into their purpose and scope. When GPOs are well-named, administrators can quickly identify the policies they need to work with or troubleshoot. When the environment grows, GPOs will get more challenging to manage if they don’t have a naming standard.
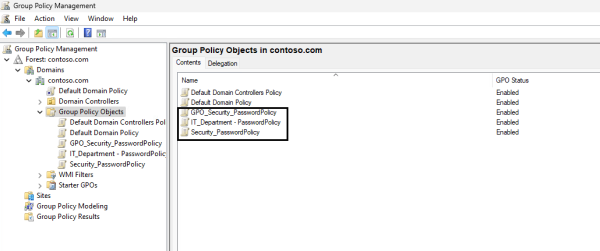
A few naming standards used in this document are:
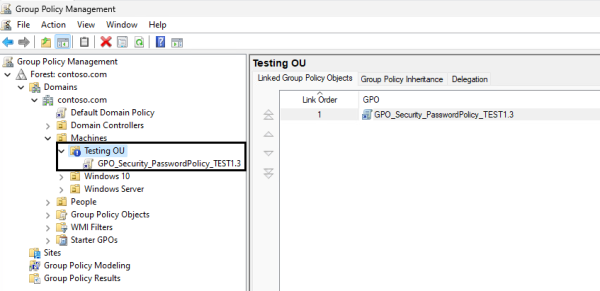
- Prefix-Based standard: GPO_Security_PasswordPolicy
- Descriptive standard: Security_PasswordPolicy
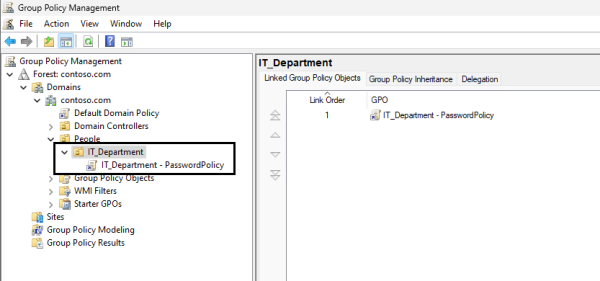
- Hierarchical standard: IT_Department – PasswordPolicy
To create new GPOs, follow the steps below.
- Open the Group Policy Management Console (GPMC)
- Expand the root level domain by clicking the dropdown arrow
- Right-click the “Group Policy Objects” OU
- Select “New”
- Enter a unique name
- Click “OK”
Below, you will find a few examples of conventional naming standards.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Have a Recovery Plan
Backing up GPOs is an integral part of maintaining continuity in your environment. Recovering from errors will be much quicker, and backups allow you to restore GPOs to a known functional state.
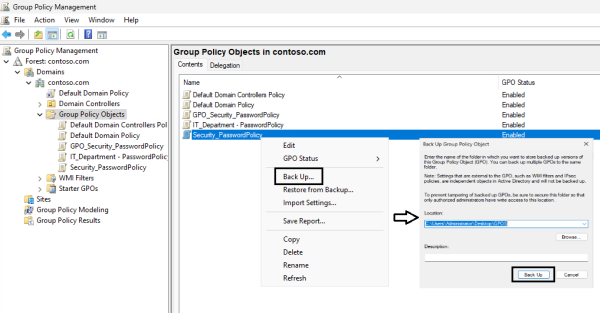
It is good practice to back up the default policies and critical GPOs before making changes. Below are the steps to manually back up a GPO object in GPMC.
- Open the GPMC
- Expand the root level domain by clicking the dropdown arrow
- Select the “Group Policy Objects” OU
- Right-click the GPO you would like to create a backup for
- Select “Back Up…”
- Browse to a desired location
- Click “Back Up…”
- Check confirmation windows and verify the backup was successful
- Click “OK” to exit the window
Backing up through the GPMC comes with its challenges. This method only permits the restoration of a full backup. There is no way to restore individual changes and retain the others.
This all-or-nothing approach can cause issues if, for example, multiple changes are made to a GPO, and there is a problem with one of the updates. AD administrators would have to restore a full, outdated backup, address the bug, and then redeploy all GPO changes again and retest.
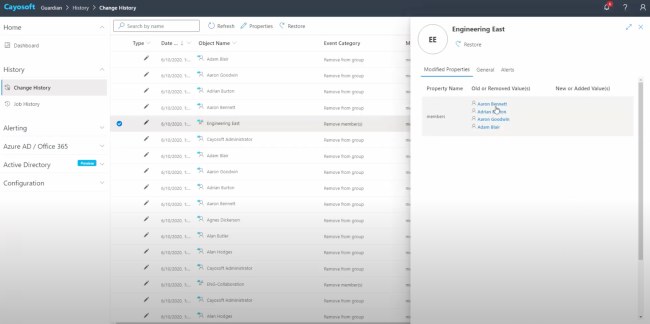
With Cayosoft Guardian, instant GPO and setting recovery allows administrators to rapidly recover from mistakes or malicious changes. Guardian is designed to enhance change visibility for on-premises, hybrid, and cloud services. Guardian monitors all directory changes, and administrators can quickly see, understand, and roll back mistakes or malicious changes across their entire hybrid Active Directory environment. Guardian can even automate rollback remediation of GPO changes made by unauthorized users.
For example, let’s say AD administrators made five changes to a GPO and identified an issue with one of the updates. Cayosoft Guardian would permit the restoration of the single GPO setting in question to its previous configuration, removing the defect until administrators can resolve the bug. The real-time backup taken by Guardian would include the four successful changes and the original GPO setting that was functional prior to the problematic update.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Limit Root Domain GPOs
The decision to limit GPOs at the root domain level is strategic and demands careful consideration. This practice involves restricting GPOs created at the domain’s root. Root domain GPOs apply to every user and object in the domain, which can lead to unintended consequences and make it harder to troubleshoot issues. Using granular controls and permissions at the root domain level is challenging. Cayosoft’s software, with its advanced management capabilities, enables you to assign policies granularly, reinforcing the notion that GPOs should be linked at the OU root level.
Granular controls, reduced complexity, and efficient troubleshooting are some of the advantages of limiting root domain GPOs. Managing policies and defining required settings is more straightforward with granular controls in place. Policies can target specific OUs, user groups, or computers, allowing for tailored configurations. As an organization grows, limiting root domain GPOs minimizes the number of GPOs that need to be managed at the highest level, leading to a simpler, more manageable environment. Troubleshooting becomes even easier.
Cayosoft Guardian can enforce change controls for additional GPO management and protection, restricting which users can make GPO updates. These restrictions can also be placed on individual GPOs, limiting who can make changes to organization-critical GPOs.
Organize OU Structure
Effective group policy management relies on an efficient OU structure. An organized OU structure simplifies management and enhances your environment’s security and overall efficiency. To maintain clarity, assign GPOs to OUs containing only the computers or users you want to target. This approach supports focused troubleshooting.
When it comes to policy inheritance, OUs play a crucial role. A logical OU structure ensures that policies applied at higher levels (parent OUs) are inherited by child OUs, providing consistency. An organized OU structure also facilitates scalability.
Do Not Disable GPOs
It is a fundamental best practice to avoid disabling GPOs whenever possible. Disabling GPOs can lead to unintended issues in your Active Directory environment. It can also make it harder to troubleshoot an existing issue because disabling a GPO will remove its settings from users and computers. When you disable a GPO, the ability to isolate and test is lost.
Additionally, GPOs could depend on other policies, so disabling a policy can have trickling effects. Unlinking a GPO is optimal if you no longer want those settings active. This approach allows for granular control of policy scope, and the GPO configuration will be retained and available for future use. It also simplifies troubleshooting by enabling an AD administrator to observe the effects and reapply the settings when needed.
Watch a 12-minute product demo video of Cayosoft’s hybrid user provisioning
Simplify GPOs
Simplifying GPOs is one of the most valuable strategies for group policy management. While creating highly detailed and specific GPOs for every possible configuration is tempting, doing so can lead to added system complexity, performance issues, and GPO management challenges. Too many settings can make it difficult to manage and troubleshoot. It’s easier to understand and fix GPOs when they are straightforward and focused. Simpler GPOs equate to better system performance, as complex GPOs can drastically increase log-in and startup times.
Each GPO should have a specific objective. It is best practice to configure only the essential settings applicable to the particular GPO. Configuring unrelated or unnecessary settings can make the GPO more complex and more challenging to discern from other GPOs.
Test Before Deploying
Administrators should always test GPOs thoroughly before deploying them to a production environment. Testing changes before deploying into production ensures policies work as intended and no new issues are introduced. Testing helps administrators identify conflicts when deploying new or modified policies, helps maintain a stable environment, and provides an opportunity to fine-tune based on the test results.
For organizations looking to move fast, particularly when making necessary compliance changes, Guardian strengthens a testing process even further by permitting any and all changes to be reverted instantly. Using Guardian’s change history functionality enables administrators to retain functional changes and revert problematic ones, allowing them to continue promoting functional compliance changes into production while they work to resolve the non-functional updates.
One way to test GPOs is by creating an OU and blocking inheritance. Blocking inheritance allows you to prevent the inheritance of GPOs from higher-level OUs or domains. You can then link only the GPOs you would like to test. Refer to the steps below to block inheritance.
- Locate the OU you would like to block inheritance on
- Right-click the OU
- Select “Block Inheritance”
- A blue circle with an exclamation point in the middle will appear to indicate inheritance is blocked.
Keep Track of All Changes
By auditing group policy changes, monitoring and reviewing modifications made to GPOs is easier, aiding in the detection of unauthorized or unintended alterations. Auditing allows administrators to maintain configuration consistency, detect and respond to potential security threats, and decrease the time spent troubleshooting.
With auditing in place, it is easier to establish and enforce accountability for GPO modifications.
Auditing can be enabled by following the instructions below.
- Open the GPMC
- Locate the policy you’d like to edit, right-click, and select “Edit”
- Under “Computer Configuration,” select “Policies”
- Select “Windows Settings”
- Select “Security Settings”
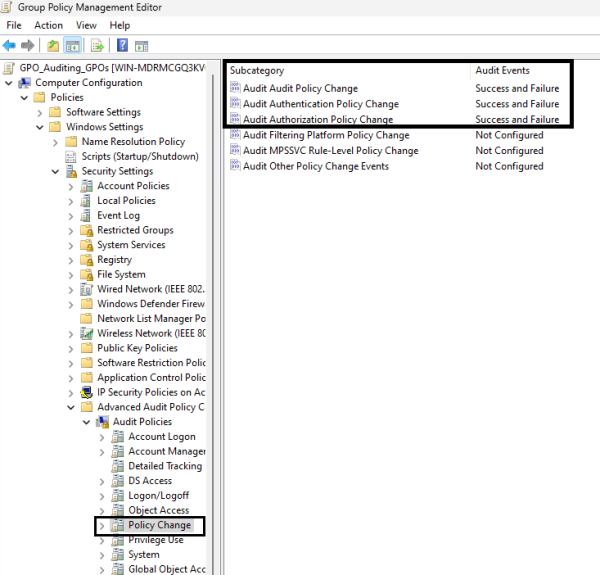
- Select “Advanced Audit Policy Configuration”
- Select “Audit Policies”
- Select “Policy Change”
- Enabled the following audit policies:
- “Audit Policy Change” (Success and Failure)
- “Audit Authentication Policy Change” (Success and Failure)
- “Audit Authorization Policy Change” (Success and Failure)
For additional auditing, you can enable Object-Level Auditing to monitor changes to GPO objects.
- Open Active Directory Users and Computers
- Click on “View” in the menu bar and enable “Advanced Features”
- Right-click the domain or OU where the GPOs are stored
- Go to the “Security” tab and click “Advanced”
- In the Auditing tab, click “Add” to create a new entry
- Specify the principal you want to audit for GPO changes
- Configure the type of access you want to audit
- Apply the changes and exit from the dialog screens
Auditing through the GPMC can prove cumbersome for large organizations or any organization with a sizable number of GPOs to manage.
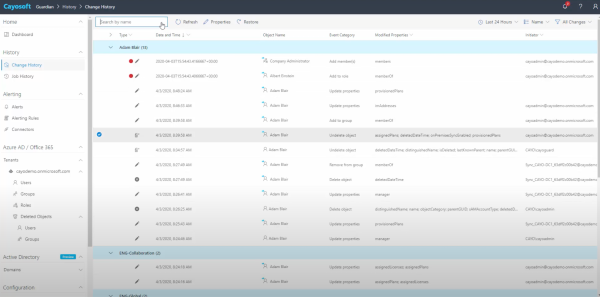
Cayosoft Guardian enables live change monitoring and real-time alerting across Active Directory, Azure AD, Office 365, and Entra ID. There is no need to manually manage auditing on an object-by-object basis, as Guardian will automatically track all AD changes without relying on native logs and provide a holistic view for administrators and auditors to review. If any updates need to be reverted, they can be done on an individual basis without affecting other parallel changes.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
GPOs are the backbone of configuration management in Windows, offering the flexibility to configure security policies and a multitude of settings. In this article, we covered nine best practices regarding group policy management. Integrating these principles into an organization establishes a robust framework for Group Policy Management, and an organization’s overall security posture is elevated.
With Cayosoft Guardian, administrators can easily manage their Active Directory and Microsoft Cloud instances. This product provides the security and control to manage, monitor, and recover environments in an instant. Guardian also decreases the time required to administer Active Directory, streamlines adherence to the best practices above, and allows administrators to focus on other essential efforts while moving at a quick pace.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content