Explore the Importance of an Active Directory Recovery Plan
Understanding the Stakes of an Unprotected Active Directory
Active Directory Outage Impacts
Recent surveys have indicated:
- 90% use Active Directory as their primary authentication & authorization engine
- 79% have experienced a recent forest-wide outage
- 43% will take more than a day to recover their AD forest
- 90% are required to rebuild or have clean servers available to begin recovery
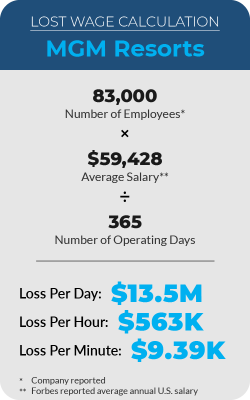
These survey results reveal an underlying problem with the potential for devastating impacts. A great example is the recent MGM cyberattack. Reports estimated the attack to cost over $100 million for the 10-day outage. Does this amount correctly reflect all of the costs associated with the outage?
With a bit of math, we can do a simple estimate of their loss from employee lost wages — potentially losing 13.5 million dollars per day. This only includes labor costs and doesn’t represent impacts to customers and suppliers, like loss of sales or damage to reputation. Considering all those factors, how much was MGM really losing per day? Last year, Veeam released a report where IT leaders estimated downtime costing $88,000 per hour.
When Active Directory is down, every minute matters! However, there are numerous scenarios that can prolong the recovery process. In your current Active Directory disaster recovery plan, are you required to rebuild servers from scratch or configure clean servers at the time of the attack? This can add extra time, stress, and potential complications to recovery. Considering the far-reaching impacts of outages, increasing cyberattacks, and costly downtime, is AD forest recovery that takes more than a day a viable option?
Hear from those who have experienced an Active Directory outage: Watch Video
Read our Active Directory Management Tools guide to learn about managing Active Directory with native and third-party tools.
Building a Robust Recovery Strategy
Backup Location
Clear Recovery Steps
When Active Directory issues arise, a clear plan can make all the difference:
- First, have a plan for common issues. If a Domain Controller goes down, what’s the first step? Craft action plans for frequent problems.
- Second, keep your plans updated. As your system and environment change, so should your recovery steps. Regularly review and update them.
- Third, practice makes perfect. Hold routine drills to familiarize your team with the plans. This ensures quicker, more confident responses in real situations.
- Last but not least, easy-to-find guides. Ensure that your team can quickly locate and refer to these plans, especially during emergencies.
Learn why Active Directory forest recovery is crucial to business continuity: View Infographic
RTO & RPO Compliance
Communication is Key
Understanding Network Topology
Incorporating Automation for Efficient Recovery
Get Proactive With Your AD Disaster Recovery with Cayosoft
With features like one-click immediate recovery, clean restore, advanced automation, and virtual labs, Cayosoft Guardian Forest Recovery was designed to do it all, very quickly, in a single solution.
FAQs
Our IT team is already stretched thin. How time consuming is it to create and maintain an Active Directory disaster recovery plan?
Developing a plan takes an initial investment of time and resources, but it’s a worthwhile endeavor. Leveraging tools that automate key steps like backups, testing, and even the recovery process itself can significantly reduce the ongoing burden on your team. It’s crucial to not only create but also maintain and regularly test the disaster recovery plan. The IT environment and organizational needs are constantly changing, and a plan that is not updated and tested may not be effective when most needed. Regular testing helps identify gaps and ensures the plan evolves in tandem with the infrastructure it is designed to protect. Testing is essential for ensuring that the plan will function correctly during an actual disaster. This investment acts as a safeguard against the much greater potential costs of prolonged downtime and recovery in the event of a real disaster.
What are some common scenarios that require an Active Directory disaster recovery plan?
Various events can require an Active Directory disaster recovery plan: these include ransomware attacks targeting AD, malicious insiders deliberately sabotaging the system, critical hardware failures on domain controllers, accidental misconfigurations or deletions made by admins, or natural disasters that compromise on-site infrastructure.
Our company has several branch offices spread across different locations. How does an Active Directory disaster recovery plan factor in this type of distributed environment?
A robust Active Directory disaster recovery plan must consider this complexity. It’s essential to have backup domain controllers in each location, potentially with replication schedules adjusted to prioritize critical data. Your plan should outline how to restore communication and functionality between sites in the event of an issue that impacts a primary data center. Cayosoft Guardian can augment the disaster recovery plan by allowing companies to get Active Directory back up and running swiftly in the cloud. Cayosoft Guardian ensures that there is a clean, active, and updated version of AD available to be synchronized from, streamlining the recovery process and reducing the immediate burden on IT resources of organizations.