Is Your Active Directory Disaster Recovery Reliable? Will Your AD Forest Recovery Work When You Need It?
Active Directory Forest Recovery: What Is It and Why Is It Important?
An Active Directory forest is a collection of domains that share a common schema and global catalog. AD forest recovery is a method to restore the AD forest to a working state in case of a disaster, such as hardware failure, malware/ransomware attacks, or natural disasters.
Having reliable Active Directory disaster recovery is essential to keeping business operations running smoothly from customers, to supply chain partners, to employees. A robust AD forest recovery plan should include procedures for restoring active directory domain controllers, managing replication, restoring AD objects and attributes, DNS server configuration settings, FSMO roles, group policy objects, and restoring AD-integrated services. In a recent study on Active Directory disaster recovery, we found:
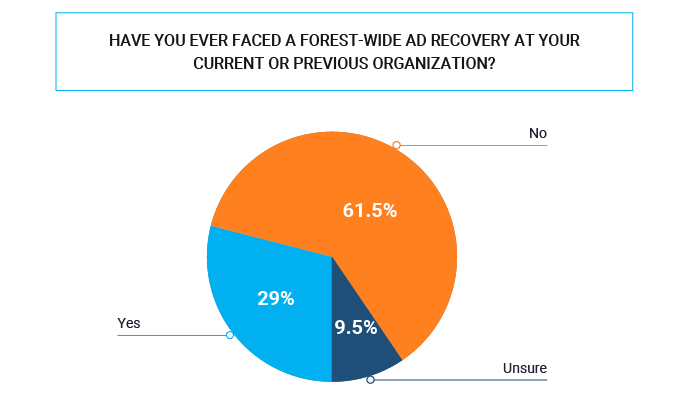
- 29% experienced a forest-wide AD recovery at their current or previous organization
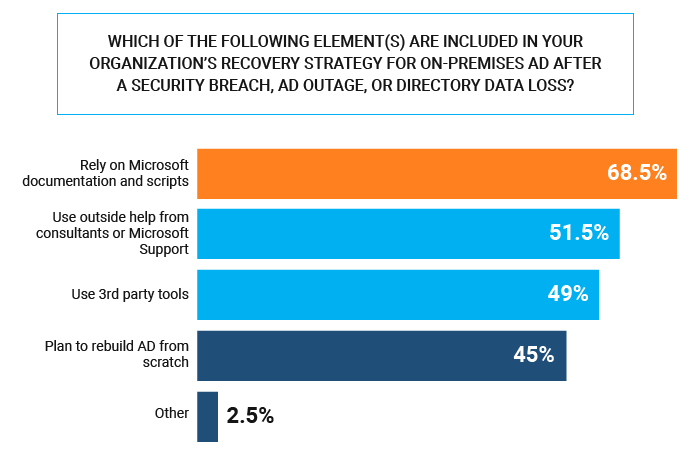
- 69% rely on Microsoft documentation and scripts
Can You Confidently Recover Your AD Forest?
Active Directory is the backbone for identity security and access for 90%+ of organizations globally. If it goes down, chaos ensues and costs skyrocket. Most are not confident with their current AD disaster recovery plan. How confident are you in your Active Directory forest recovery?
Here is an example from just a couple weeks ago: City of Oakland Declares State of Emergency After Ransomware Attack
Consider the following critical steps of developing and maintaining an AD disaster recovery plan, that you can be sure will work as intended, when needed:
- Documenting the recovery procedures (step 1, step 2, step 3, etc.)
- Identifying staff roles and responsibilities during the recovery process
- Ensuring the recovery procedures are consistent with the organization’s disaster recovery and business continuity plans
- Determining the approach to Active Directory forest recovery: traditional or instant
- Incorporating AD forest recovery products
- Regularly testing the disaster recovery plan
Challenges to Active Directory Forest Recovery
Lack of Testing
- Backups are often 12+ months old. Think about how many changes occur in a year.
Complexity
- Natively recovering AD, across on-prem AD, Azure AD, and Office 365, requires numerous steps with little guidance, making it immensely complex.
Limited Resources & Lack of Expertise
- Hybrid inherently adds complexity, making it time consuming and error prone. This is why 3rd party tools are necessary.
Traditional vs. Instant AD Forest Recovery
Traditional AD Forest Recovery:
Instant AD Forest Recovery:
Best Practices for Active Directory Disaster and Forest Recovery
- Test the recovery plan regularly to ensure it works as intended
- Know it will work when needed
- Automate recovery procedures whenever possible
- Automation = faster
- Incorporate Active Directory forest recovery products
- 3rd party = faster & less errors
- Evaluate multiple recovery products before selecting one
- Old way vs. new way
Cayosoft’s Instant Active Directory Forest Recovery
Reliable Active Directory forest recovery is critical for ensuring business continuity and protecting against data loss during ransomware or cybersecurity attacks. Cayosoft is the only vendor to offer Instant AD Forest Recovery. The technology is patent-pending and a game changer for recovery from disaster or attack. Read this case study highlighting a real-world example of why Gartner recommended Cayosoft over legacy AD recovery tool vendors Quest Software and Semperis.
Want to learn more about Cayosoft's patent-pending Instant AD forest recovery?
Learn more about Cayosoft Guardian Forest Recovery and check out this on-demand webinar to learn ways to protect and recover your hybrid AD environment quickly and efficiently after cyberattacks.