Home » Implementing Zero Trust Security with Microsoft Entra » Implementing Microsoft Entra Private Access: A Step-by-Step Guide
Implementing Microsoft Entra Private Access: A Step-by-Step Guide
Learn how Microsoft Entra Private Access leverages Zero Trust Network Access (ZTNA) principles to provide secure and seamless access to an organization's private resources from anywhere, replacing traditional VPNs.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Securing sensitive information while enabling seamless user experience is a challenging balancing act facing modern organizations. Traditional network access methods such as VPNs cannot meet the dynamic needs of today’s work environments as they are often inefficient and struggle to keep up with modern security threats.
Zero Trust Network Access (ZTNA) solutions are emerging as a solution to this problem and enabling network security to address the challenges of highly dynamic and distributed environments. Entra Private Access is Microsoft’s popular network security solution that leverages ZTNA principles and can often replace legacy virtual private network (VPN) implementations.
This article will explore Microsoft Entra Private Access in detail, including features, use cases, licensing, and configuration.
Summary of key Microsoft Entra Private Access concepts
The table below summarizes key concepts related to Microsoft Entra Private Access.
Concept | Description |
Zero Trust Network Access (ZTNA) | A security model that does not implicitly trust users or devices even if they are in an internal network and enforces verification for each access request. |
Virtual Private Network (VPN) | A network solution that creates a secure and encrypted tunnel to a remote private over the internet. |
Microsoft’s Security Service Edge (SSE) | It is a cloud-based identity-centric security solution comprising Microsoft Entra Internet Access, Microsoft Entra Private Access, and Microsoft Defender for Cloud Apps. |
Global Secure Access | Microsoft’s SSE solution delivers secure and seamless access to an organization’s private resources to anyone from anywhere. |
Quick Access app | A Private Access configuration method for quickly setting up access to private resources without a VPN. |
Global Secure Access app | It is another Private Access configuration method used to set up per-app access controls. |
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is a security framework based on the same principle as Zero Trust: Never Trust, Always Verify. A ZTNA solution enforces continuous verification, i.e., authentication and authorization, and enforces strict access controls regardless of whether the access request is from inside or outside the (organizational) network. It does not assume that private or internal networks are, by default, safe.
ZTNA aims to minimize security risks and reduce security breaches due to unauthorized access by continuously verifying user identity and device health.
Introduction to Microsoft's Security Service Edge (SSE) and Global Secure Access
Microsoft’s Security Service Edge (SSE) is a network security category that focuses on providing an identity-aware cloud-based network perimeter for the modern workforce. The SSE solution includes Global Secure Access, an identity-centric security solution that converges network, identity, and endpoint access controls to secure apps, data, and resources from any location, device, or identity.
Global Secure Access is built on Zero Trust principles and includes two products, Microsoft Entra Internet Access and Microsoft Entra Private Access, and is the unifying product term used by Microsoft. We will be focusing on Microsoft Entra Private Access in this article.
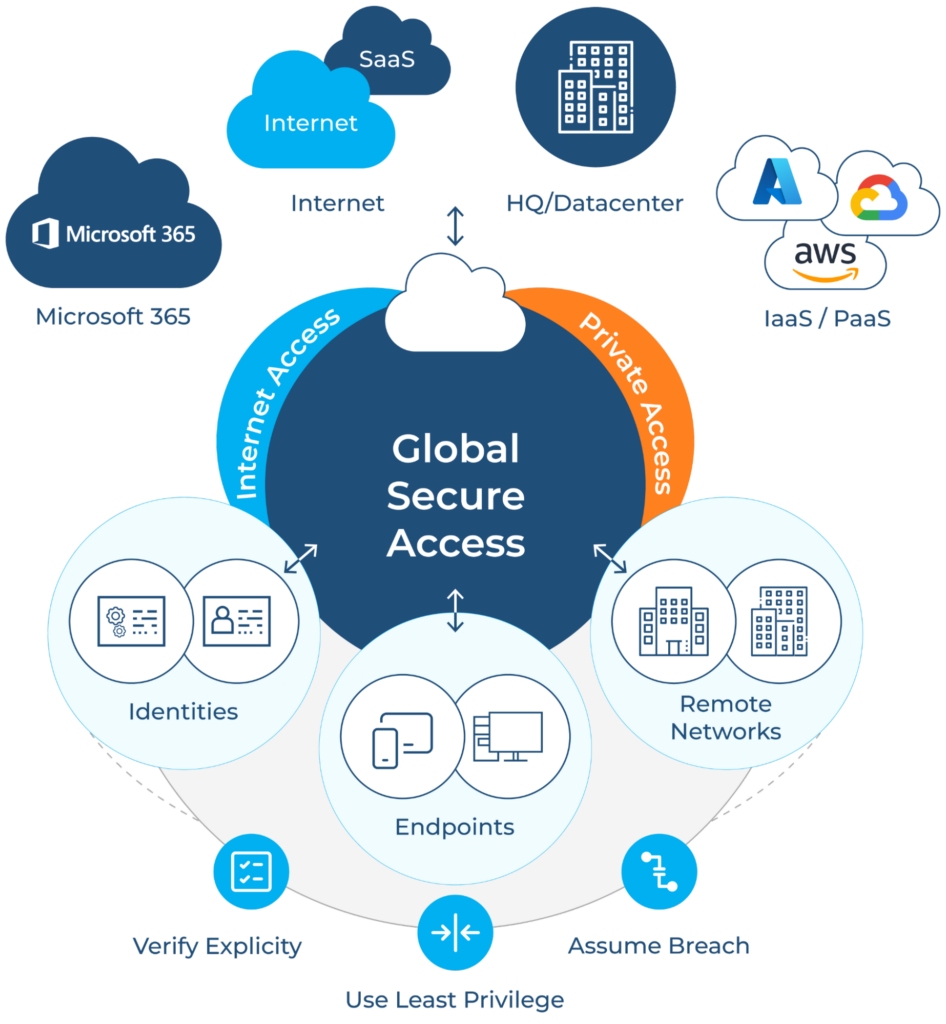
A logical overview of Global Secure Access. (Source)
Microsoft Entra Private Access
Entra Private Access is a cloud-based, no-VPN ZTNA solution that securely connects users and devices with private applications and resources. Private Access enables secure access to an organization’s private resources without a VPN. Users can be located anywhere, and the applications and data they want to access can be in any cloud or non-cloud environment.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Features
- Quick Access– Microsoft Entra Private Access has a Quick Access feature that enables Zero Trust access to IP addresses / FQDNs without needing a traditional VPN solution.
- Granular access controls- Per-app access for fine-grained control over access privileges.
- Conditional Access and SSO– Microsoft Entra Private Access supports Conditional Access and Single Sign-On (SSO) for private applications.
- Private resource segmentation– Teams can implement segmented access to private applications and resources.
- Application Discovery– This feature is currently in preview and enables visibility into private application usage.
Use cases
- Remote work– Organizations can allow remote workers, customers, and business partners secure access to private resources without requiring a VPN.
- SSO for multiple applications- Teams can provide single sign-on (SSO) capabilities for seamless access to multiple private applications.
- Conditional access implementations- Additionally, organizations can implement conditional access and enforce multi-factor authentication (MFA) when users access private resources.
- Modernize access controls for legacy apps- Private Access allows you to implement modern access controls to legacy applications.
Licensing
Microsoft Entra Private Access requires at least a Microsoft Entra ID P1 or Microsoft Entra ID P2 license as a prerequisite. You can then purchase a license for Private Access as a standalone product or purchase Microsoft Entra Suite, which includes Private Access and a host of other products related to identity protection, governance, and identity verification solutions.
Refer to the licensing page for the latest prices and information:
Cayosoft Guardian for Private Access
Cayosoft Guardian complements Microsoft Entra Private Access by providing threat detection, monitoring, and recovery solutions. Importantly, it continuously monitors changes and allows you to recover unwanted changes or deletions. For example, the configuration organizations use to create a private access environment relies heavily on conditional access policies. If these policies are accidentally deleted, they cannot be recovered natively from Microsoft Entra. Craysoft Guardian solves this problem and enables users to restore policies in the case of accidental deletions or unwanted changes.
Architecture
Organizations can use Microsoft Entra Private Access for ZTNA in two ways: Quick Access app and Per-app Access (also called Global Secure Access Apps)
Quick access
Quick Access is the fastest way to get started with Private Access. You simply add Fully Qualified Domain Names (FQDNs) or IP addresses to secure, along with port information if necessary. Access to these endpoints is always securely tunneled.
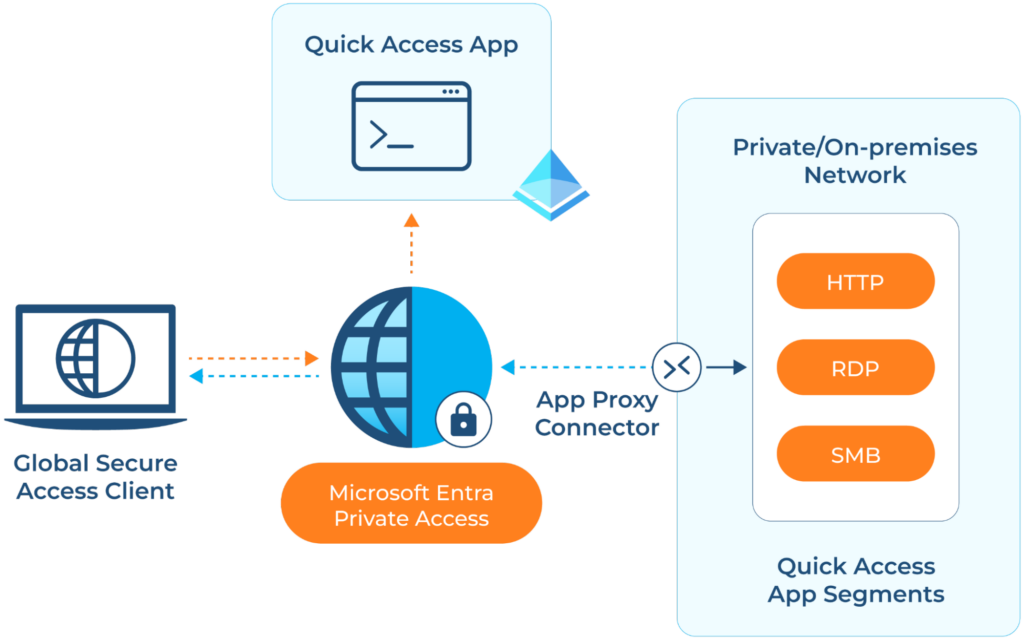
A logical overview of the Microsoft Entra Private Access Quick Access method. (Source)
Per-app access
Per-app access gives teams more fine-grained control over securing their private applications and resources. For example, you can have different access policies for different resources like database VMs and application VMs. Or separate conditional access policies for contract vs. permanent users.
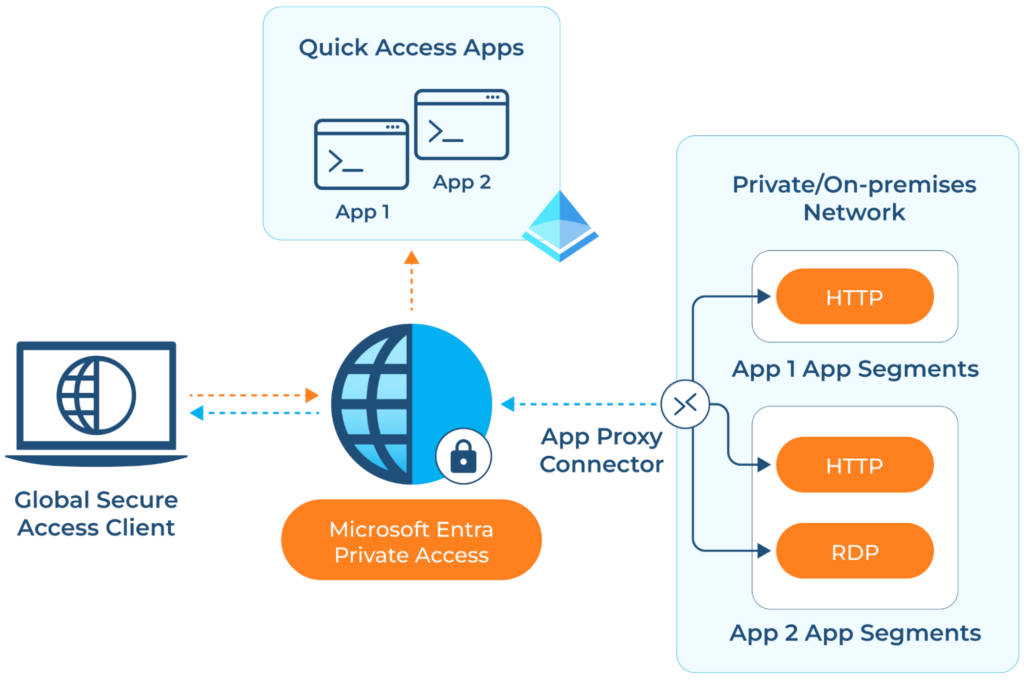
Per-app Access method (source)
Components
There are four essential components of Microsoft Entra Private Access architecture. They are:
- Private network connector: The Microsoft Entra private network connector is an agent that enables connectivity to the Private Access service (also called the application proxy service). It is installed on a Windows server on the same network as the on-premises private network or a virtual network in another cloud. It is one of the first things you do after activating Private Access.
- Connector groups: They allow you to group connectors for better control and also to simplify deployments. For example, you could group based on location or application type, such as production or development.
- Traffic forwarding profiles: Traffic profiles are used to evaluate incoming traffic and forward them to the correct applications and services. There are three traffic forwarding profiles that you can configure, they are: Microsoft traffic, Private Access, and Internet Access.
- Global Secure Access client: Administrators install/deploy the clients on the end-user devices. They are used to access private applications and resources using the forwarding profile created earlier, which is the Private Access profile. They are generally available for Windows and Android and in preview for macOS and iOS.
Private Access vs. Application Proxy
Microsoft Entra Application Proxy is a service that also enables secure access to private applications and is primarily used in on-premises setups. The table below summarizes the differences between Microsoft Entra Private Access and Application Proxy.
Private Access | Application Proxy |
A key difference is that Private Access is based on the Zero Trust model. | Application proxy uses a simple, secure web gateway approach. |
It works on a wide range of use cases, such as IP address ranges, FQDNs, and supports ports and protocols. | It is primarily for web applications. |
Private access provides direct access to resources and applications. | Application proxy uses a redirect traffic method, similar to a reverse proxy. |
It uses a client called the network connector. | It does not use a client. |
Private access requires a license. | Application proxy does not need an additional license. |
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
How to configure Microsoft Entra Private Access using Quick Access
In this tutorial, we will set up Quick Access for a private subnet in an Azure VNET. At the end of these steps, you should be able to access a VM on the private subnet using its private IP from an end-user machine.
Here are the high-level steps involved:
- Acquire a trial of Private Access and activate Global Secure Access in the Microsoft Entra admin center.
- Configure a Windows VM on the same network with the Private Network connector.
- Configure Quick Access and enable traffic forwarding for the Private access profile.
- Install Global Secure Access client and test access.
Purchase a license or activate a trial
In this tutorial, we will activate a trial for Private Access.
1. Navigate to https://www.microsoft.com/en-in/security/business/identity-access/microsoft-entra-private-access and click Try for free. This will open a new page with a sign-up workflow.
2. Follow the prompts to sign in for a Microsoft Entra Private Access Trial. Close the window when the order is successfully placed.
Activating Global Secure Access
Private Access is part of Global Secure Access and all the setup and configurations related to it are performed under the Global Secure Access area in the Microsoft Entra admin center. Let’s activate Global Secure Access.
- Navigate to https://entra.microsoft.com/ and login if required.
- On the left navigation menu scroll down to see the Global Secure Access option, expand it and select Dashboard.
- Click the Activate button to begin.
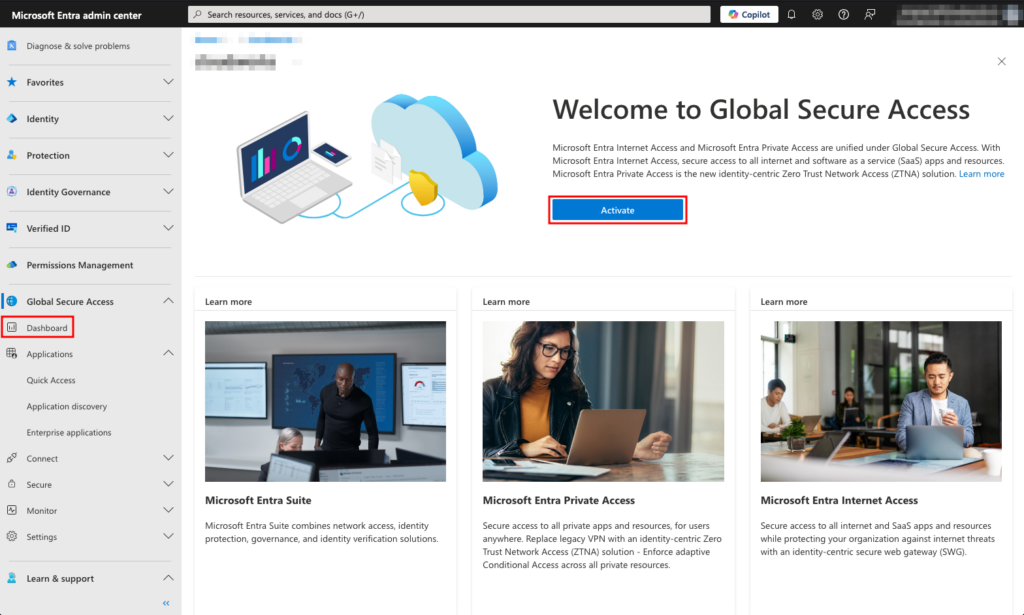
Access Global Secure Access in Microsoft Entra admin center
Install and configure the network connector
The next step is to install one or more Microsoft Entra private network connectors on your private network. This connector will allow outbound connections to the Global Secure Access service.
The following prerequisites must be in place before installing a connector:
- A server/VM running Windows Server 2012 R2 or later.
- .NET version v4.7.1 or above
- Transport Layer Security (TLS) 1.2 must be enabled on the server.
- Ports 80 and 443 must be open for outbound connections. In the case of an on-premises network with a firewall, you open these ports in the firewall settings.
- You must also allow access to various URLs. You should do this if you do not want to allow all outbound connections on port 80 and 443. The table below has the list.
URL | Port/ | Description |
site.msappproxy.net, | 443/HTTPS | Communication between the connector and the Application Proxy cloud service |
crl3.digicert.com, crl4.digicert.com, ocsp.digicert.com, crl.microsoft.com, oneocsp.microsoft.com, | 80/HTTP | The connector uses these URLs to verify certificates. |
login.windows.net, secure.aadcdn.microsoftonline-p.com, site.microsoftonline.com, site.microsoftonline-p.com, site.msauth.net, site.msauthimages.net, site.msecnd.net, site.msftauth.net, site.msftauthimages.net, site.phonefactor.net, enterpriseregistration.windows.net, management.azure.com, policykeyservice.dc.ad.msft.net, ctldl.windowsupdate.com, and www.microsoft.com/pkiops | 443/HTTPS | The connector uses these URLs during the registration process. |
ctldl.windowsupdate.com, www.microsoft.com/pkiops | 80/HTTP | The connector uses these URLs during the registration process. |
List of URLs, Ports, and Protocols to open
- A user with an Application Administrator role.
- You must disable HTTP 2.0 on Windows Server versions 2019 and later. To do so, run the following PowerShell command and restart the server.
Set-ItemProperty 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp\' -Name EnableDefaultHTTP2 -Value 0
1. Navigate to Global Secure Access and select Connectors from the menu.
2. Next, click Download connector service and then click Accept terms and Download to download the connector. Move it to the Windows Server machine if needed.
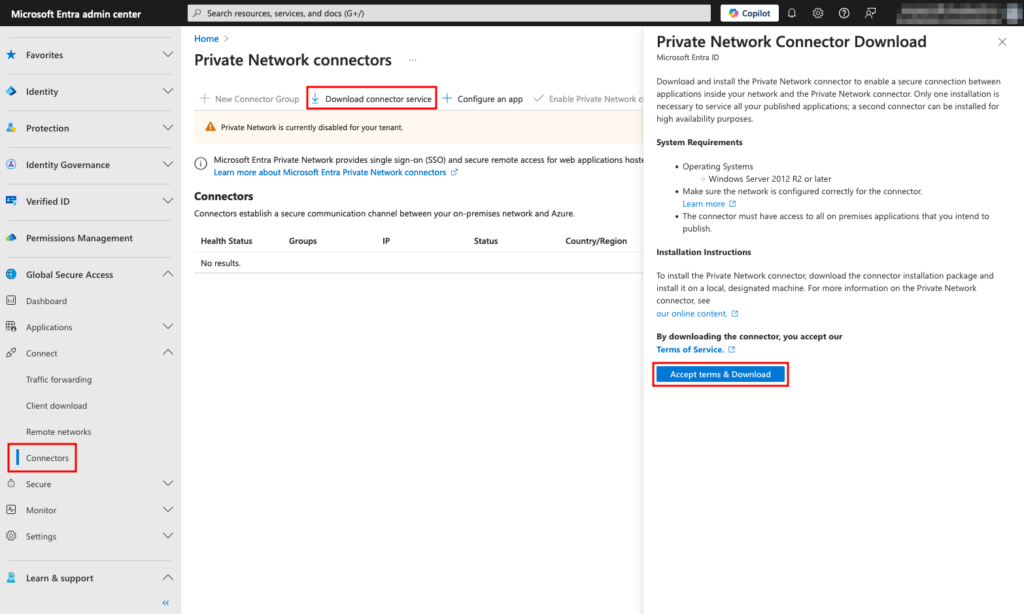
3. Double-click the MicrosoftEntraPrivateNetworkConnectorInstaller.exe file on the Windows Server to begin the installation process. When prompted, agree to the license terms and conditions and click Install.
4. You will be prompted to sign in to complete the connector registration with Microsoft Entra tenant. Use a credential that has Application Administrator permissions.
5. Finally, return to the Microsoft Entra admin center portal and refresh the Global Secure Access Connectors page. You should see an active connector listed.
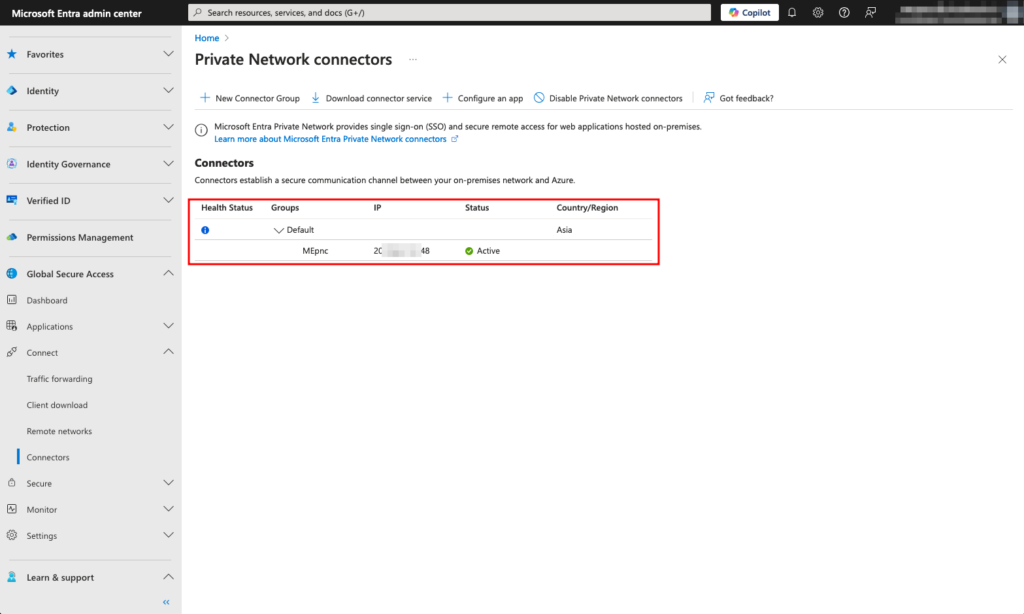
Status of installed connector
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Configure Quick Access
The next step in the configuration workflow is to configure Quick Access in the Global Secure Access area of Microsoft Entra.
1. Navigate to Quick Access, which will load the configuration blade.
2. Provide a Name for the configuration, and then click + Add Quick Access application segment to create one.
3. This will load another blade where you can set a destination type and its associated parameters, which will change based on the type. Here, it is set to the IP address range (CIDR). Click Apply and then Save. This creates an Enterprise application in Microsoft Enta ID.
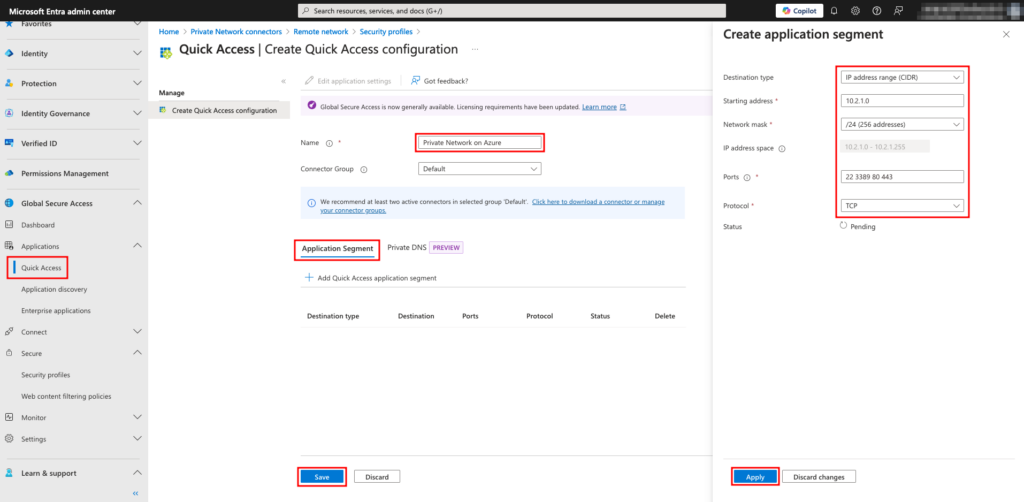
4. Next, you must add users (or groups) to this Quick Access app. Click the Edit application setting at the top to navigate to the enterprise application properties page.
5. Select Users and groups on the page and then click + Add user/group.
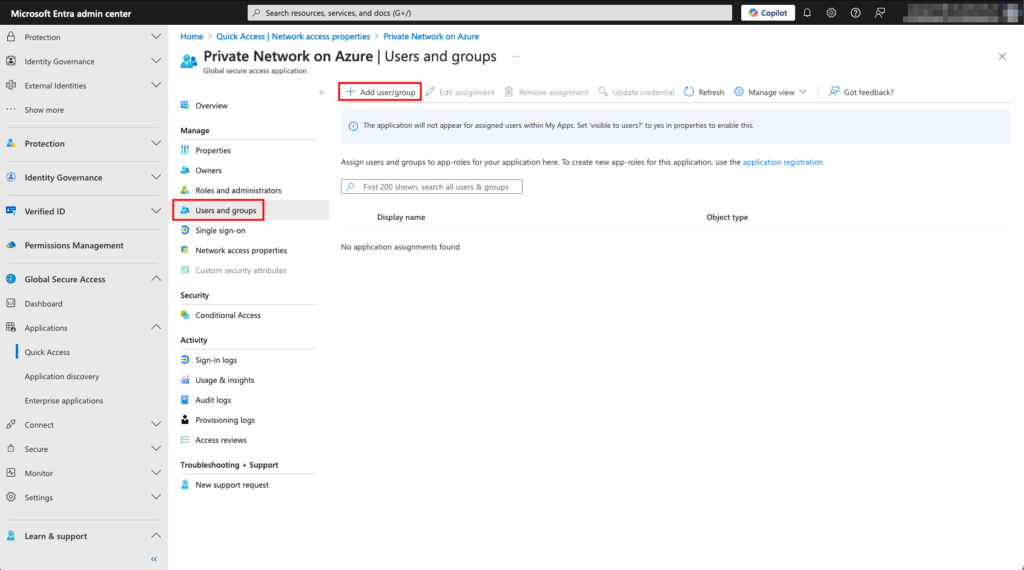
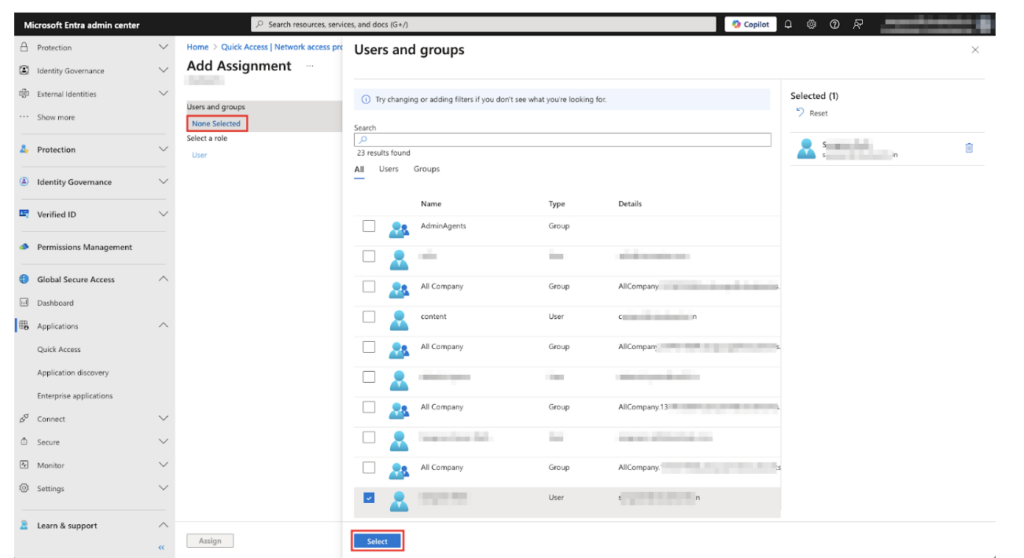
6. Click None Selected under Users and groups and then select the desired users. Click Select when done.
Enable traffic forwarding profile
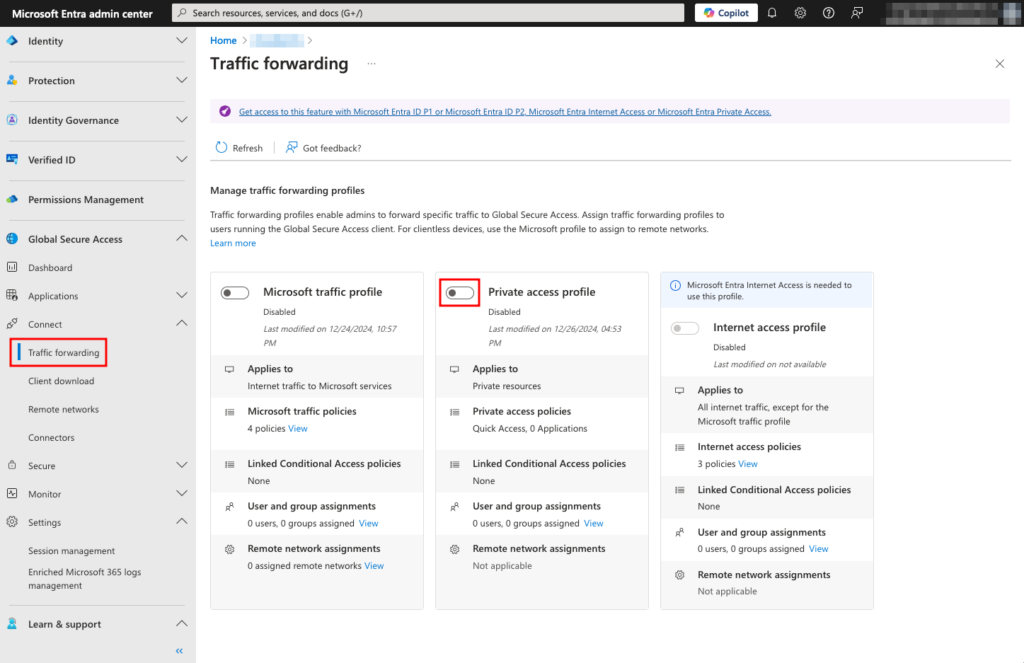
1. Navigate to Traffic forwarding in the Global Secure Access area and toggle the Private access profile. When prompted for confirmation, click OK.
NOTE: The toggle switch is activated only if you have a private access license.
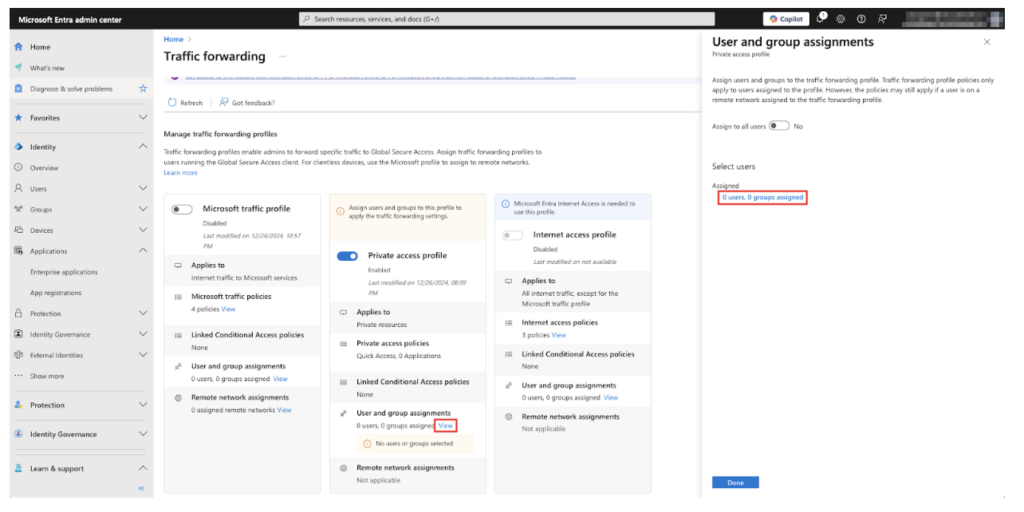
2. Next, you must assign the selected users and/or groups to the traffic forwarding profile. Click View under User and group assignments to do so. Then, use the link under Select users to add them. You can also assign this profile to all users.
Install Global Access secure client for end-user access
Finally, we will download and install the Global Access client on an end-user machine.
The following prerequisites must be met on the end-user machine:
- The Windows client must be Microsoft Entra or Microsoft Entra hybrid joined.
1. Navigate to the Client download section and click Download Client. In this example, we are downloading and installing the Windows client.
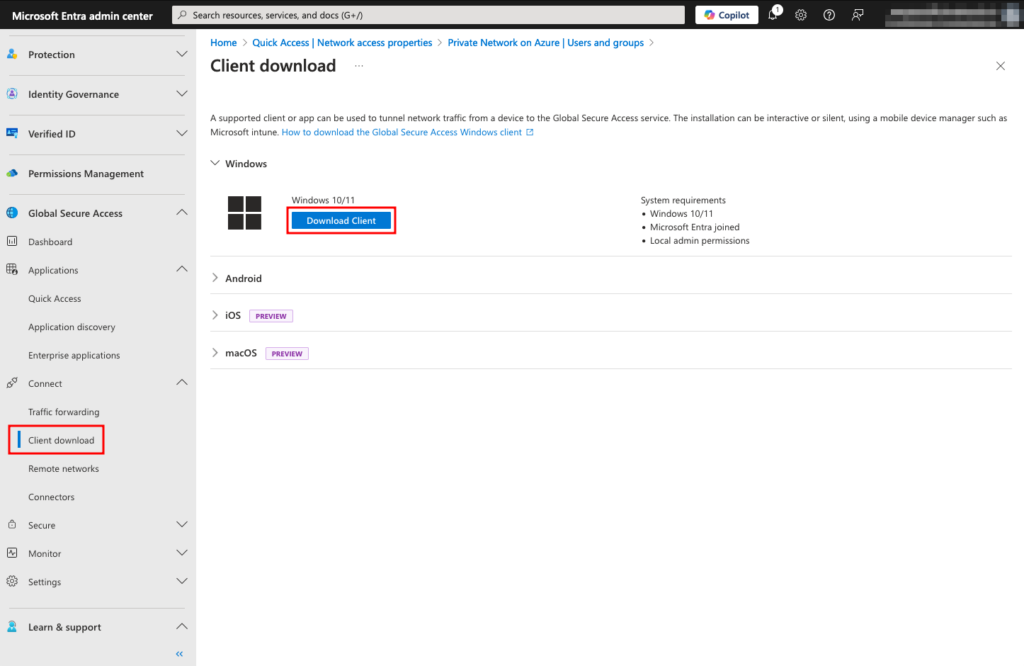
This will download a MicrosoftEntraPrivateNetworkConnectorInstaller.exe file.
2. Copy the file if needed and run the file to install the Global Secure Access client on an end-user machine. Once the client is installed, you will see the Global Secure Access client icon in the system tray.
A green check means that the Global Secure Access client is Connected.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Microsoft Entra Private Access provides a single-pane glass solution for clarity and control over identity permissions across multi-cloud environments. It provides visibility into the state of permissions through discovery, facilitates right-sizing through remediation, and provides continuous monitoring so organizations can adhere to compliance requirements such as the least privilege principle.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content