Home » Five Critical Azure Security Best Practices for Effective Risk Management » Azure Security Defaults: A Comprehensive Guide to Key Settings and Policies
Azure Security Defaults: A Comprehensive Guide to Key Settings and Policies
Learn about the effectiveness of Azure Security Defaults and how they should be supplemented with custom conditional access policies for robust security measures.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Cloud infrastructure and services can be very complex, and Microsoft’s naming schemes often add to this complexity. You are probably familiar with at least one of the following terms: Azure Active Directory, AAD, Azure AD, or Microsoft Entra ID. The good thing is they usually refer to the same set of services and features used to authenticate users and services inside the Microsoft public cloud infrastructure.
One of the features inside Entra ID, and the main topic of today, is Azure Security Defaults. Although it may sound like a general term, Azure Security Defaults is actually a feature built into Azure Entra ID (formerly known as Azure AD). As the name would suggest, Azure Security Defaults is a set of security settings that are enabled by default on every Azure tenant.
Overview of key Azure Security Defaults settings and concepts
| Azure Security Defaults setting/concept | Explanation |
|---|---|
| Multi-factor authentication for users | Requires regular users of the Azure portal to register for MFA. MFA will be required occasionally to access resources. |
| Multi-factor authentication for administrators | Mandates MFA for all administrator accounts every time they sign in. |
| Blocking legacy authentication | Disables older, less secure authentication protocols that don’t utilize MFA, preventing attackers from exploiting vulnerabilities in outdated methods. |
| Protecting privileged activities | Requires MFA for any activities that require elevated permissions, such as accessing sensitive data, changing system configurations, or managing user accounts. |
| Securing Microsoft 365 users | Enabling security defaults to secure Microsoft 365 users access their accounts, especially email. |
| Securing third-party solutions | Secure third-party applications and services that connect to your Azure environment. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Enabling and disabling Azure Security Defaults in the Azure portal
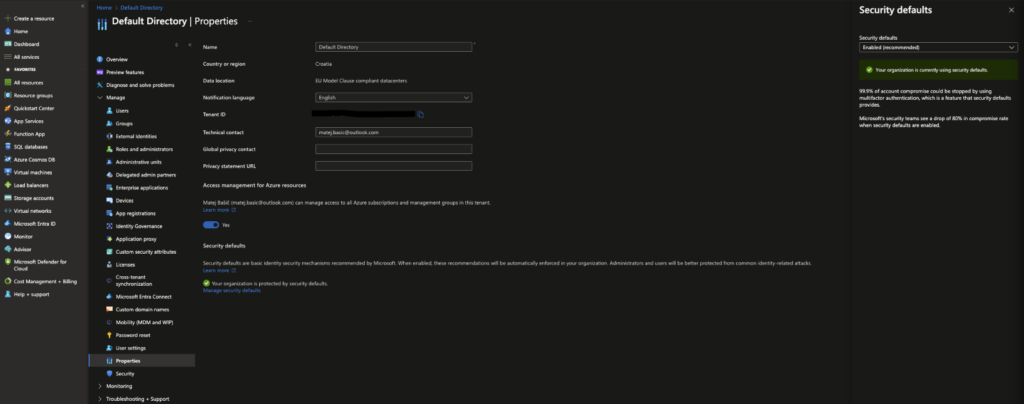
Let’s get the most important part out of the way first. How do you turn Azure Security Defaults on and off?
On the Azure portal, in the left pane, look for Microsoft Entra ID. The Active Directory menu opens. From there, expand the Manage dropdown menu and look for Properties. After opening Properties, you’ll notice the Manage security defaults option at the bottom, which you can use to enable and disable Azure Security Defaults.
If your tenant was created after January 2020, the setting is enabled by default.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Settings managed by Azure Security Defaults
Azure Security Defaults have certain ramifications that you should be aware of at all times because enabling or disabling these security settings can affect critical parts of your infrastructure, such as emails or file sharing.
The most important setting that Azure Security Defaults will enable is registering all users for multi-factor authentication. When using multi-factor authentication with Microsoft services, you’re generally expected to use the Authenticator app, which can be found on both Google Play store and Apple store. Whether or not this is the best solution depends on the situation, but it is important to note that your users will require access to a smartphone to properly register for multi-factor authentication. One of the most popular alternatives to the Authenticator app is YubiKey, a simple token that is inserted into a USB port on your device that must be physically touched every time MFA is triggered.
The second setting managed by Azure Security Defaults is the requirement of MFA for all administrators. Although regular users will have to use MFA occasionally, administrators will have to use MFA all the time. It’s important to realize that most automation scripts may require some adjustment to make them work with MFA. A good solution for that would be to use a special service account or integrate automation scripts with Azure itself using an Automation account.
As already mentioned, regular users will have to use MFA when necessary. Now this is a pretty generic statement, so what does this mean in practice? Generally, Microsoft will keep track of the IPs from which you’re logging in to M365 services, times at which you’re logging in, for how long you keep your sessions open, what types of devices you’re using to access M365 services, etc. This information can be used to create a very robust prediction model that will be used to check whether your current login attempt differs from your usual usage and behavior patterns. If the model decides that your login attempt is unusual—for example, you’re trying to access the Azure portal from a Mac when you’ve only used Windows PCs until now—you can expect that you will be prompted for an MFA login.
Beyond MFA, enabling Azure Security Defaults will block legacy authentication protocols. Legacy authentication is another one of those generic terms, so it’s important to note that in terms of Azure, and M365 in general, this term refers to protocols such as IMAP, POP3, or SMTP. This is a significant change, and you should make sure that none of your clients use these protocols for authenticating with M365 and to enable modern authentication in your Outlook clients.
Last, but definitely not least, enabling Azure Security Defaults will protect privileged activities. As you can probably guess, a privileged activity is every activity that manages Azure resources through Azure Resource Manager API. These include Azure portal, Microsoft Entra admin center, Azure powershell and Azure CLI. This setting means that administrators will be asked to perform MFA for their privileged activities.
Azure Security Defaults ramifications for Microsoft365/Office365 users
It’s better if administrators consider M365 and Azure as one vast and very complex public cloud system where most client-facing services are on the M365/O365 side while most administration tools are in the Azure Entra ID / Entra ID Admin center. After all, all authentication for Office365 is done through Entra ID.
Modifying Azure Security Defaults may impact M365 users, mainly their mailboxes. Ensure that your users are using email clients that are compatible with security settings enforced by Azure Security Defaults.
Watch demo video of Cayosoft’s hybrid user provisioning
Azure Security Defaults ramifications for third-party tools such as Cayosoft Guardian
Managing cloud and hybrid environments can become very complex very fast. Managing a hybrid Microsoft environment—including on-premises servers and services, Office365, and Azure public cloud—requires the administrator to use multiple complex dashboards, each made for a particular purpose. This workflow can lead to several very serious and impactful human errors in administration.
For this reason, companies often decide to use third-party tools to help them manage their Azure and Office365 infrastructure. An example of such a tool is Cayosoft Administrator, which allows users to easily manage their hybrid environments through a simple, unified dashboard.
It is crucial to check that such third-party tools will have the proper permissions to manage Azure resources through Azure Resource Manager API without interfering with Azure Security Defaults.
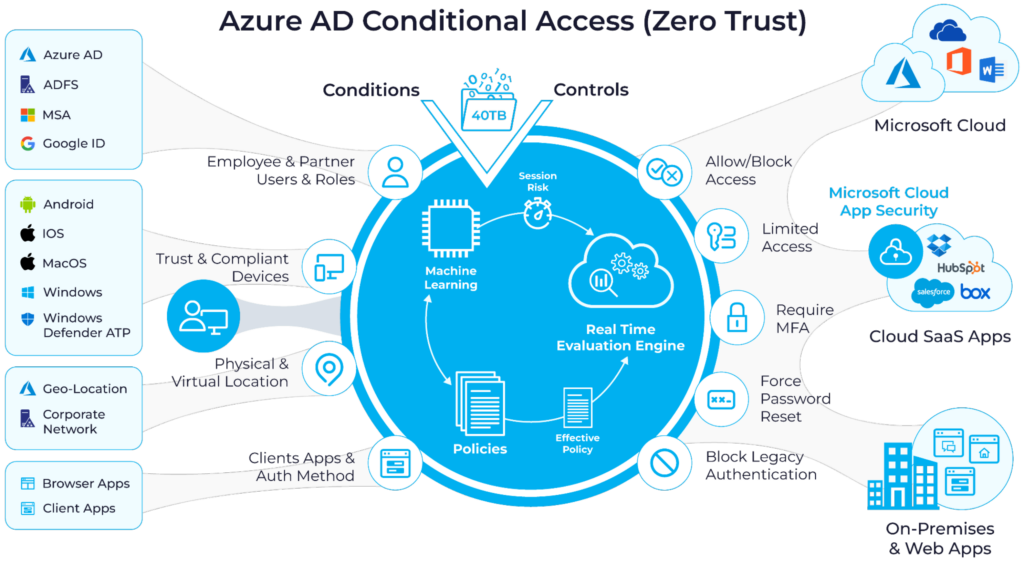
Advanced security methods: conditional access
Oftentimes, the lack of granularity that comes with Azure Security Defaults isn’t enough for administrators. For a more granular approach to managing security settings in Azure, we can use conditional access policies.
Conditional access policies can be overwhelming, as they are significantly more complex than Azure Security Defaults. For this reason, users often decide to manage conditional access policies using a third-party tool, such as Cayosoft Guardian.
Everyday management operations with conditional access policies can be cumbersome and not user-friendly. A great example of such action is modifying an existing policy. Whenever possible, in general, you never want to modify existing policies, instead creating new policies, but sometimes modifications cannot be avoided. This is a prime example of a scenario where using tools such as Cayosoft Guardian is ideal, as they can help you roll back Active Directory objects and attributes and conditional access policies that have been previously deleted or modified. Cayosoft Guardian can also help you identify modified policies as it monitors for any modifications made to Active Directory objects. Usage of this feature can be expanded even further as Cayosoft Guardian can notify you of modifications made in real time, enabling you to react to security breaches in a timely manner.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Audit logs are the cornerstone of a sound security strategy. They provide invaluable insights into user activities, system changes, and potential security threats, enabling organizations to maintain a strong security posture.
The five Entra ID (Azure AD) audit logs best practices in this article form the foundation of a comprehensive Azure audit logging strategy. The right technology can make a significant difference in how effectively and efficiently an organization can implement these practices. By leveraging Cayosoft’s solutions, organizations can more easily implement and maintain the best practices we’ve discussed, significantly enhancing their security posture and simplifying compliance efforts.
Whether you’re looking to improve your current audit logging processes or implementing a comprehensive strategy from scratch, Cayosoft’s solutions can provide the tools and support you need to succeed.
Take the next step and contact Cayosoft today for a personalized demo, and discover how our solutions can elevate your organization’s security and compliance efforts.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content