Home » Active Directory Management Tools: Must-Have Features » Key Considerations for an Effective Active Directory Backup Strategy
Key Considerations for an Effective Active Directory Backup Strategy
Learn about the importance of backing up Active Directory to ensure data consistency and protect against cyber threats, including best practices and key considerations for implementing an effective backup strategy.
Explore the chapters:
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
- Chapter
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Many Fortune 500 companies use Active Directory(AD) to manage and store crucial data related to network resources and user accounts. They depend on important AD features such as Group Policy, which allows for central operating system and application management, replication across domain controllers to ensure data consistency, and single sign-on capabilities to improve user experience.
However, because AD has comprehensive control over permissions and access to sensitive data, cyber attackers often target it. Attackers can exploit AD’s control mechanisms to infiltrate the network, assume privileged users’ identities, and conduct undetected operations. This can lead to significant disruptions and theft, highlighting the importance of securing AD against potential cyber threats. A robust Active Directory backup strategy is one of the best ways enterprises can mitigate risk.
This article will discuss the challenges and best practices related to Active Directory backup and restore, as well as security measures to protect against common AD risks.
Summary of key Active Directory backup best practices
The table below summarizes three fundamental Active Directory best practices this article will explore in more detail.
| Concept | Description |
|---|---|
| Configure schedule and retention policies for Active Directory backups | Set up a regular backup schedule and define retention policies to ensure data is consistently backed up and stored for the appropriate duration, minimizing data loss and ensuring compliance. |
| Verify Active Directory backups by performing a random restore | Regularly test backups by performing restoration to confirm that backup files are intact and can be successfully restored, ensuring data integrity and reliability in case of a disaster. |
| Document the steps required for backup and restore | Create detailed documentation outlining the procedures for backing up and restoring data, providing a clear guide for IT staff to follow in maintaining and recovering systems. |
Understanding Active Directory backup
Active Directory’s hierarchical structure, including forests, domains, and organizational units (OUs), alongside user and group objects, forms the backbone of efficient network management. Understanding this structure is crucial for implementing effective backup strategies and ensuring swift restoration and network security in case of data loss or disasters. Mastery of Active Directory’s schema allows administrators to organize directory information logically and manage access permissions efficiently. This structured approach supports decentralized management, aligns with organizational policies, and facilitates effective network administration, particularly in large organizations facing complex challenges.
What is Active Directory backup?
Active Directory backups differ from traditional data file backups, like those in object storage, due to AD’s unique structure. This structure demands that the backup covers multiple components and processes, including the database and system state files. The AD database holds a wide range of information related to the directory, such as user accounts, group policies, and organizational units (OUs). However, backing up AD does more than just preserve data. It protects the hierarchical structure and the complex relationships between directory objects. This highlights AD’s complexity and critical role in an organization’s IT infrastructure.
Reasons to Backup Active Directory
Backing up Active Directory (AD) is critical in ensuring business continuity, supporting disaster recovery, and complying with regulations. It enables organizations to recover swiftly from cyberattacks, natural disasters, or system failures, minimizing downtime. Backups safeguard against the accidental deletion of users or units and protect systems from corruption, ensuring smooth operations and stable system states. Additionally, these backups assist in meeting regulatory standards, preparing for audits, and supplying historical data for legal or forensic purposes. By regularly backing up AD, organizations ensure adherence to data retention policies, securing vital information.
Types of Active Directory backups
Traditionally, backing up Active Directory involves either a full server or a system state backup. Full server backup includes all the files on the machine, including Windows and application files. Because of its heavy nature, the backup process takes a lot of time and consumes a lot of storage. Similarly, doing a restoration would take a lot of time.
It’s important to note that these backups can inadvertently restore any malware present at the time of the backup. This risk might force you to use an older backup file that predates the malware, which may not be current enough to support a quick recovery.
The other type of backup is the system state backup that includes all the necessary files to restore Active Directory, including the raw database, DNS information, registry settings, SYSVOL folder, etc. This means that, similar to full server backups, restoring from a system state backup can also reintroduce malware present at the time of the backup. This may force you to use an older backup file that isn’t current enough to support a quick recovery. While a system state backup is lighter than full backup, it is more challenging, especially for an average user. The restoration process is complex and involves multiple steps.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Three common challenges with Active Directory backups
Backing up Active Directory presents unique challenges stemming from its complex nature and evolutionary path. Here are three reasons that highlight why backing up AD can be challenging.
AD environment complexity
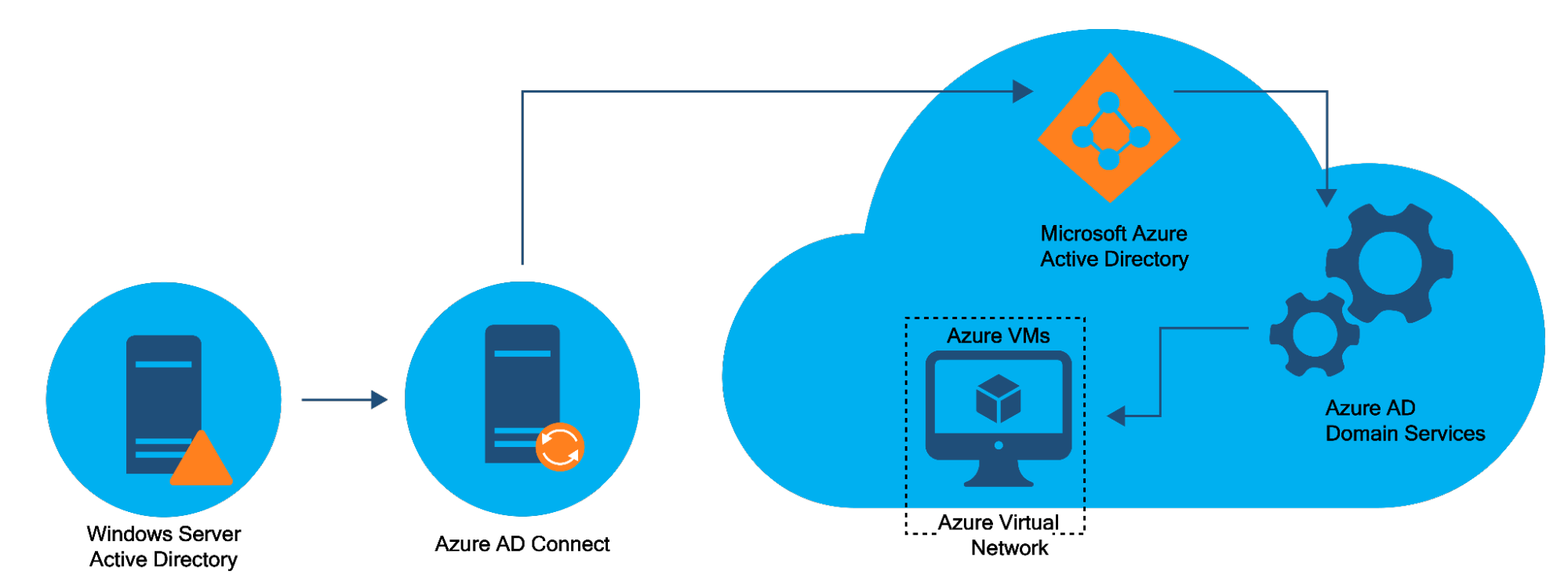
Over time, IT infrastructure has evolved and become increasingly complex. Nowadays, companies are not limited to maintaining their presence solely in their data centers; instead, they have expanded into the cloud. Depending on their specific needs, some companies operate entirely in the cloud, while others maintain hybrid environments. This evolution also extends to Active Directory.
Microsoft now offers Azure Active Directory, an online version of Active Directory hosted on the MS Azure cloud, responding to the growing trend of companies adopting work-from-home policies and managing remote sites.
Additionally, some environments are hybrid, incorporating a local Active Directory on-premises and synchronizing data with Azure Active Directory in the cloud. While this hybrid approach ensures unified identities across all applications and facilitates single sign-on, streamlining access, and security management, it also introduces complexity by introducing additional components like AD Connect which are responsible for synchronizing both environments to ensure seamless integration and consistent user experiences. If AD Connect stops working, synchronization issues will arise, causing both environments to be in different states and leading to a poor user experience.
Frequent AD changes
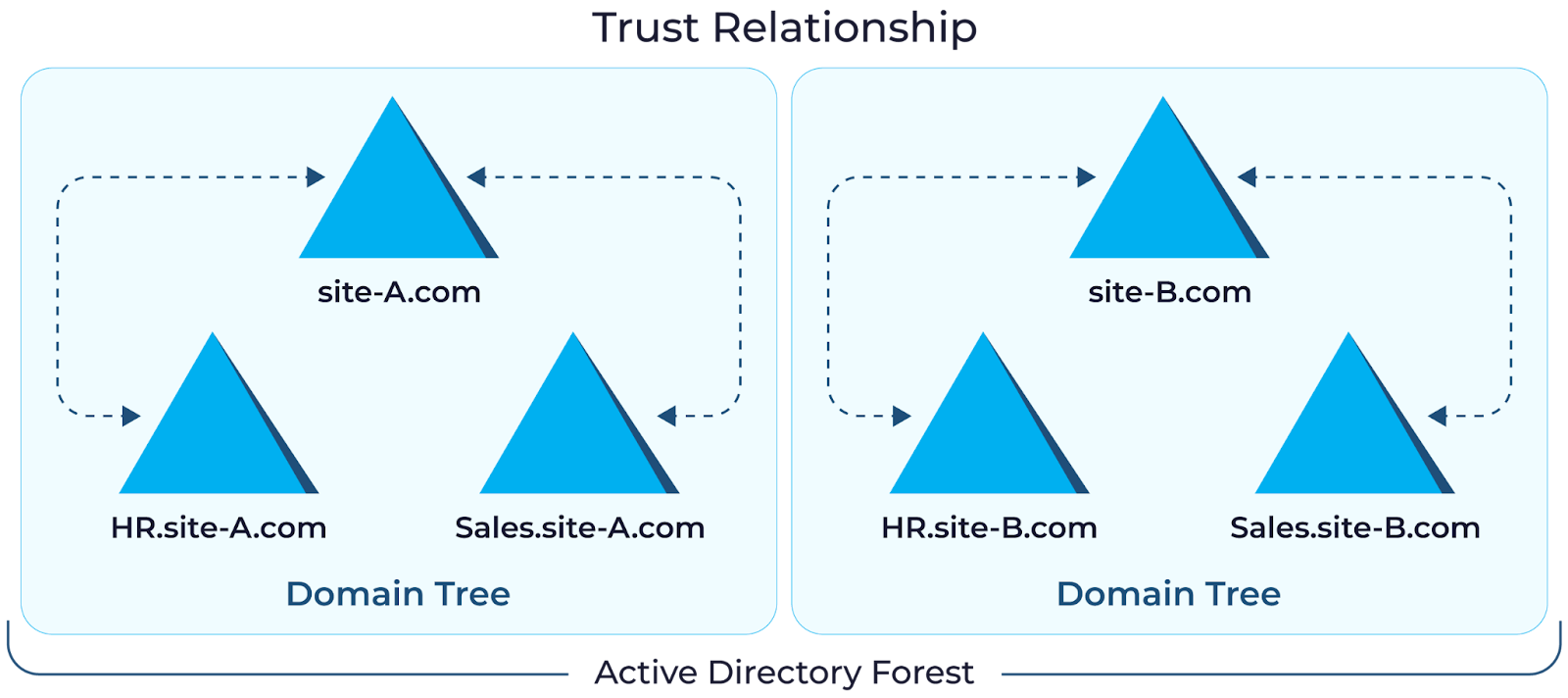
Active Directory data frequently changes. Companies regularly welcome new employees, bid farewell to departing ones, adjust user permissions, and create new group policies. These are day-to-day Active Directory operations that continuously change the state of data. Additionally, mergers and acquisitions (M&As) can create impactful changes in trust relationships between the new domains or forest changes to account for the convergence of the organizations. A change in security policies might emerge to ensure compliance with standards and regulations for the new business. Applications that rely on AD for authentication and authorization must be updated to recognize the new users and groups. Similarly SSO solutions may need to be reconfigured to allow seamless access for users from both the acquiring company and the acquired business.
Ensuring backups without impacting business continuity
Many companies today implement single sign-on (SSO) to enable the use of a single identity to authenticate across various business applications. This method not only simplifies the login process by reducing the need for multiple credentials but also emphasizes the vital importance of Active Directory (AD) in identity management.
However, if AD becomes unavailable for any reason, users cannot authenticate and access applications. This scenario becomes particularly challenging for companies with a global presence as they operate teams across different continents and time zones. As a result, IT administrators often struggle to find a clear maintenance window that avoids disrupting business operations.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Best practices for Active Directory backup and restore
Despite the challenges, adhering to the following best practices can ensure healthy AD backups.
Configure schedule and retention policies for Active Directory backups
Organizational needs and compliance standards are crucial in shaping Active Directory backup and retention policies. Implementing the Grandfather-Father-Son (GFS) model for Active Directory backups includes daily, weekly, and monthly backup schedules, balances comprehensive backup coverage, and long-term data archiving. Factors such as storage capacity, Recovery Time Objective (RTO), and Recovery Point Objective (RPO) must be considered when configuring these policies. These considerations guide the development of a backup and retention strategy tailored to meet the organization’s requirements and resource constraints.
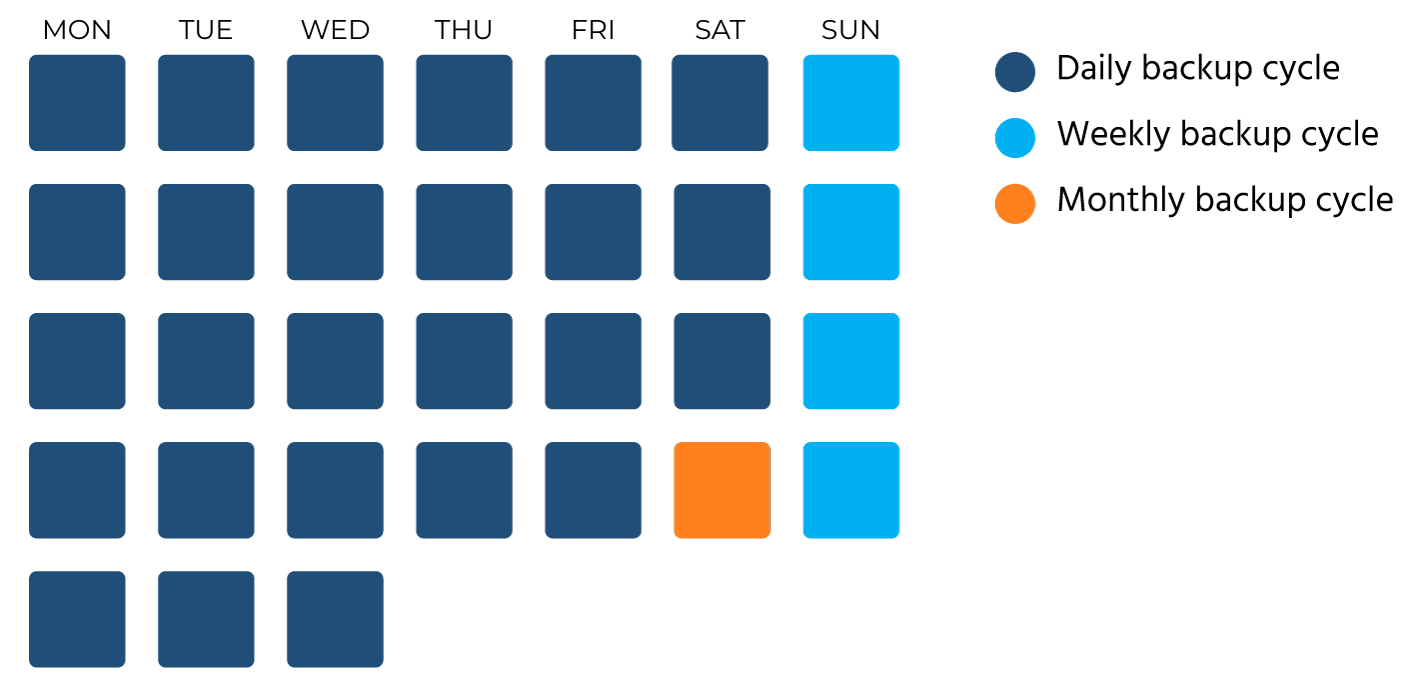
Verify Active Directory backups by performing a restore
Performing a restoration test to verify a backup is as critical as taking the backup. No one should find themselves in a situation where backups fail during an attempted restore. Simply trusting the success notification from backup software falls short of due diligence. By executing a restore, you validate the file’s integrity and confirm it holds the relevant data.
Document the steps required for backup and restore
As staff turnover occurs, experienced team members might depart, and new employees might join. Similarly, the backup administrator could be on leave, requiring someone else to assume their duties temporarily. In the worst-case scenarios, like a disaster, panic might compromise an individual’s ability to act effectively. A document clearly outlining all necessary backup and restoration steps becomes invaluable in these situations. This guide enables the quick and straightforward execution of backup and restore processes, ensuring continuity despite changes in personnel or emergencies.
Watch a demo video of Cayosoft’s hybrid user provisioning
Cayosoft for Active Directory Backup and Restore
With all the complexities mentioned, there should be an easy fix. That’s where Cayosoft Guardian comes in. It’s software designed to simplify security and recovery for organizations using Microsoft Active Directory (AD) and Azure Active Directory (Azure AD). Cayosoft Guardian combines threat detection, monitoring, and recovery into one simple unified console. This makes it extremely easy for administrators to keep track of changes to user accounts, permissions, and other necessary settings and respond quickly when needed.
Key features of Cayosoft Guardian
The table below summarizes four key features of Craysoft Guardian that can help enterprises improve their Active Directory backup strategy.
| Feature | Description | Example |
|---|---|---|
Instant recovery
| Recover from accidentally deleted objects or revert malicious changes to user accounts, group memberships, and settings. | Restore an admin account compromised by a phishing attack. |
Change monitoring
| Continuously monitor Active Directory and Azure AD for suspicious activity and receive real-time alerts. | Get notified about unauthorized attempts to create new user accounts in Active Directory. |
Historical records for hybrid changes
| View a complete history of changes made across the on-premise and cloud AD | Record changes made to Group Policy Object (GPO) settings, indicating who made the change and when it was made. |
| Threat detection | Automatically identify and rollback suspicious changes before potential exploitation.
| Identify and reverse unauthorized permission modifications to sensitive Active Directory objects automatically. |
Instant Forest Recovery
Traditional recovery methods, such as full backups and system state backups, often pose challenges. These methods require numerous steps, consume significant storage space, and result in lengthy recovery times (RTO). Consequently, restoring a system from the latest backup and returning to normal operations can be time-consuming.
Cayosoft Guardian Forest Recovery, with a patent-pending standby directory technology, is the breakthrough alternative to legacy forest recovery tools. It instantly recovers the entire AD forest simplifying the restore process. This tool is specifically designed to protect businesses from outages by ensuring instant forest recovery and maintaining business continuity. It simplifies the recovery process of Active Directory (AD) forests by streamlining the complex steps outlined in Microsoft’s technical guide, which typically involve over 35 steps. This efficiency significantly reduces the Recovery Time Objective (RTO), resulting in quicker recovery times and a smoother overall process.
An automated process runs every night to prepare the system for a quick restoration of the AD forest if needed. In the event of an outage, you can switch to the standby forest with just a few additional steps, completing the process in minutes. This ensures minimal disruption and provides a fully operational AD environment ready to support multiple domains or domain controllers.
Besides automating the recovery process, Cayosoft also offers advanced planning for backup and recovery. These plans specify how to restore essential components like domain controllers, DSRM passwords, FSMO roles, and DNS settings, ensuring a fast and accurate recovery. This acceleration minimizes downtime and its related costs.
Cayosoft Guardian focuses on data collection efficiency, keeping only essential data to quicken recovery. It allows for precisely restoring specific object attributes, such as group memberships and account settings, enabling granular and swift recovery from outages. Additionally, Cayosoft Guardian enables the setup of isolated virtual labs for testing. You can replicate your production AD forest in a secure, isolated environment, allowing for the testing of recovery procedures, compliance with regulations, and safe trials of changes to domains or forests. This preparation guarantees readiness for recovery, bolstering your defenses against potential disruptions and ensuring uninterrupted operation.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Business continuity and disaster planning should include your Microsoft Entra ID environment. Microsoft Entra ID has limited in-built recovery options for misconfigurations or hard-deleted objects. Cayosoft Guardian, through its unique patented technology, facilitates quick recovery by maintaining a ready-to-use backup version of the AD.
Cayosoft Guardian Forest Recovery safeguards your business from devastating Active Directory (AD) outages, whether caused by ransomware, cyberattacks, or data corruption. The platform provides a comprehensive, instant recovery solution for all Microsoft directories, encompassing on-premises AD, hybrid AD, and Azure AD.
Key features include:
- Granular recovery of AD objects and attributes
- Partition recovery
- Domain controller recovery
- Automated, instant full forest recovery
- Continuous change monitoring to detect and rollback unauthorized or accidental changes
To know more about how you can proactively prevent outages and quickly recover from attacks with Cayosoft, request a personalized demo here.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content