Most global businesses run hybrid AD environments, and following active directory security best practices is critical when combining on-premises and cloud services to secure both Active Directory (AD) and Microsoft Entra ID (formerly Azure AD). Both systems manage identity and access control, making them prime targets for attackers aiming to escalate privileges, extract data, and deploy ransomware. Recently, groups like Storm-0501 have been leveraging vulnerabilities in hybrid AD setups, expanding their campaigns to compromise both on-premises and cloud infrastructures.
In response to these growing threats targeting on-premises Active Directory, the National Security Agency (NSA), in collaboration with global cybersecurity agencies, has released critical guidance on Detecting and Mitigating Active Directory Compromises. This guide highlights the most common attack vectors being exploited and outlines active directory security best practices for securing and alerting on these threats. Let us explore key takeaways from the NSA’s guidance and how Cayosoft builds on these and extends to hybrid AD providing comprehensive real-time protection for AD and Entra ID.
NSA’s Guidance on Detecting and Mitigating AD Compromises
The NSA’s guidance focuses on 17 common attack techniques used to compromise on-premises Active Directory, providing strategies for detecting and mitigating these threats. As most businesses have integrated their on-premises AD with cloud-based services like Microsoft Entra ID, the risk of attack now spans both environments, making organizations more vulnerable than when using on-premises AD alone. By following Active Directory security best practices, businesses can mitigate the risks introduced by hybrid AD environments, which present attackers with a broader attack surface.
Real-World Attacks on AD and Entra ID: Mercury (Storm-1084) and Storm-0501
Mercury Attack
The Mercury attack group now tracked as Storm-1084, associated with Iran, has targeted hybrid environments by first compromising on-premises AD and then moving laterally to cloud services like Microsoft Entra ID. This operation was notably destructive, aiming not just for ransomware deployment but for complete disruption and destruction of resources.
In previous incidents, Mercury gained access through known vulnerabilities, which were then handed off to DEV-1084 to perform actions like data exfiltration, lateral movement across systems, and wiping out resources like virtual machines, storage accounts, and domain controllers.
Storm-0501
Recently, Storm-0501 has emerged as a significant threat to hybrid AD environments. This ransomware group initially gains access to on-premises AD by exploiting vulnerabilities in platforms like Zoho ManageEngine, Citrix NetScaler, and Adobe ColdFusion. After compromising the network, they move laterally to Microsoft Entra ID, where they create persistent backdoors by altering cloud configurations. Once inside, Storm-0501 uses Impacket and Cobalt Strike to steal credentials and deploy ransomware across both on-premises and cloud environments.
These real-world examples highlight the increasing sophistication of attackers targeting both AD and Entra ID, making it essential for organizations to adopt a comprehensive, real-time defense strategy for hybrid AD environments.
Common AD Attack Vectors
AD is often a target for attacks aimed at compromising user accounts and escalating privileges, which is why following active directory security best practices is essential to safeguard both on-premises and cloud-based systems. Some of the most common attack techniques outlined in the NSA’s guidance include:
- Kerberoasting: Attackers target service accounts with an SPN in AD by cracking their Ticket Granting Service (TGS) tickets, giving them access to sensitive accounts.
- DCSync: This technique exploits AD replication permissions, allowing attackers to steal password hashes from Domain Controllers.
- Password Spray: Attackers attempt to authenticate to multiple user objects using either a single password or multiple passwords until they successfully authenticate to a user object
Event Logs for Real-Time Detection in AD Environments
The NSA outlines specific event logs that should be monitored to detect suspicious activity within AD. For example:
- Event ID 4769, 4738, and 5136 (TGS ticket requests) are crucial for detecting Kerberoasting.
- Event ID 4662 highlights object changes and is critical for identifying DCSync attacks.
- Failed logon events (e.g., Event ID 4625) are key indicators of password spraying and brute-force attacks.
These event logs are a great starting point for monitoring and alerting on AD attacks. However, in a hybrid AD environment, it is essential to monitor logs from both on-premises and cloud systems, which can complicate the process and make it harder for teams to respond quickly to potential threats. Relying solely on event logs has its limitations—they can be delayed, missed, or lost amid legitimate activity, making it challenging to detect critical incidents in real time.
Mitigation Strategies for Active Directory
To address these threats, the NSA’s guidance recommends several key mitigation strategies:
- Reduce Privileged Access: Attackers often escalate privileges, so limiting the number of highly privileged accounts in both AD and Entra ID is critical.
- Enable Multi-Factor Authentication (MFA): Implement MFA across both AD and Entra ID to make it harder for attackers to use stolen credentials.
- Use gMSAs (Group Managed Service Accounts): In line with active directory security best practices, using gMSAs in AD ensures automatic password rotation, making it difficult for attackers to compromise service accounts.
- Audit Privileged Changes: Regular auditing of privileged account activities helps identify suspicious behavior before attackers gain a foothold
Common Attack Vectors in Microsoft Entra ID
While the NSA’s guidance focuses on Active Directory, it’s essential to extend active directory security best practices to Microsoft Entra ID to prevent lateral movement and attacks on cloud services. The most common Entra ID attack vectors include:
- Security Tokens: Attackers steal security tokens (such as OAuth tokens) from compromised accounts to bypass password authentication and MFA, gaining direct access to cloud resources. This Pass-The-Token (PTT) attack can go undetected as attackers bypass credential-based defenses.
- Illicit Consent Grant: In Illicit Consent Grant attacks, users are tricked into granting OAuth permissions to malicious apps. Once the app is authorized, it can access sensitive data like emails and files, gaining persistent access that’s difficult to revoke without administrative action.
- Dangerous Entra ID App Permissions: Misconfigured OAuth permissions can allow attackers to escalate privileges or access sensitive data within Entra ID. Regular reviews of app permissions help prevent lateral movement within cloud environments by unauthorized actors.
- Cross-Tenant Attacks: Attackers can exploit trust relationships between different Entra ID tenants to move laterally and gain access to resources in other organizations. Guest accounts or federated identity setups are often targeted, especially in multi-tenant environments.
Event Logs for Real-Time Detection in Entra ID Environments
Key Entra ID event logs for monitoring include:
- Sign-in logs: Tracks successful and failed login attempts to detect unauthorized access.
- Audit logs: Logs administrative changes such as policy updates, role assignments, and app consents.
- Risky sign-ins and users: Identifies risky sign-ins, indicating potential phishing attempts or credential theft.
Mitigation Strategies for Entra ID
To secure Entra ID, the following strategies are critical:
- Conditional Access Policies: Enforce policies based on user risk, location, and device compliance.
- OAuth Permissions Review: Regularly audit OAuth app permissions to prevent overexposure.
- Privileged Identity Management (PIM): Limit and manage privileged access to sensitive cloud resources.
- Continuous Access Evaluation (CAE): Enable CAE to monitor and terminate risky sessions in real time(NSA Blog).
How Cayosoft Enhances Active Directory and Entra ID Security in Hybrid Environments
How Cayosoft Enhances Active Directory and Entra ID Security in Hybrid Environments
While the NSA’s guidance provides valuable insights into event-based monitoring and mitigation strategies, modern threats require real-time monitoring, automation, and a unified approach across both AD and Entra ID. That is where Cayosoft excels—providing real-time, direct protection across hybrid environments.
Here’s how Cayosoft enhances security for both AD and Entra ID:
Real-Time Monitoring of AD and Entra ID Directly—No Waiting for Event Logs
Cayosoft Guardian provides real-time monitoring of both on-premises AD and Microsoft Entra ID, allowing organizations to detect and respond to threats instantly. Whether it is unauthorized changes in AD or suspicious access attempts in Entra ID, Cayosoft ensures that security teams are alerted immediately.
This is especially crucial in hybrid environments, where attackers often target vulnerabilities in AD to move laterally into cloud systems via Entra ID.
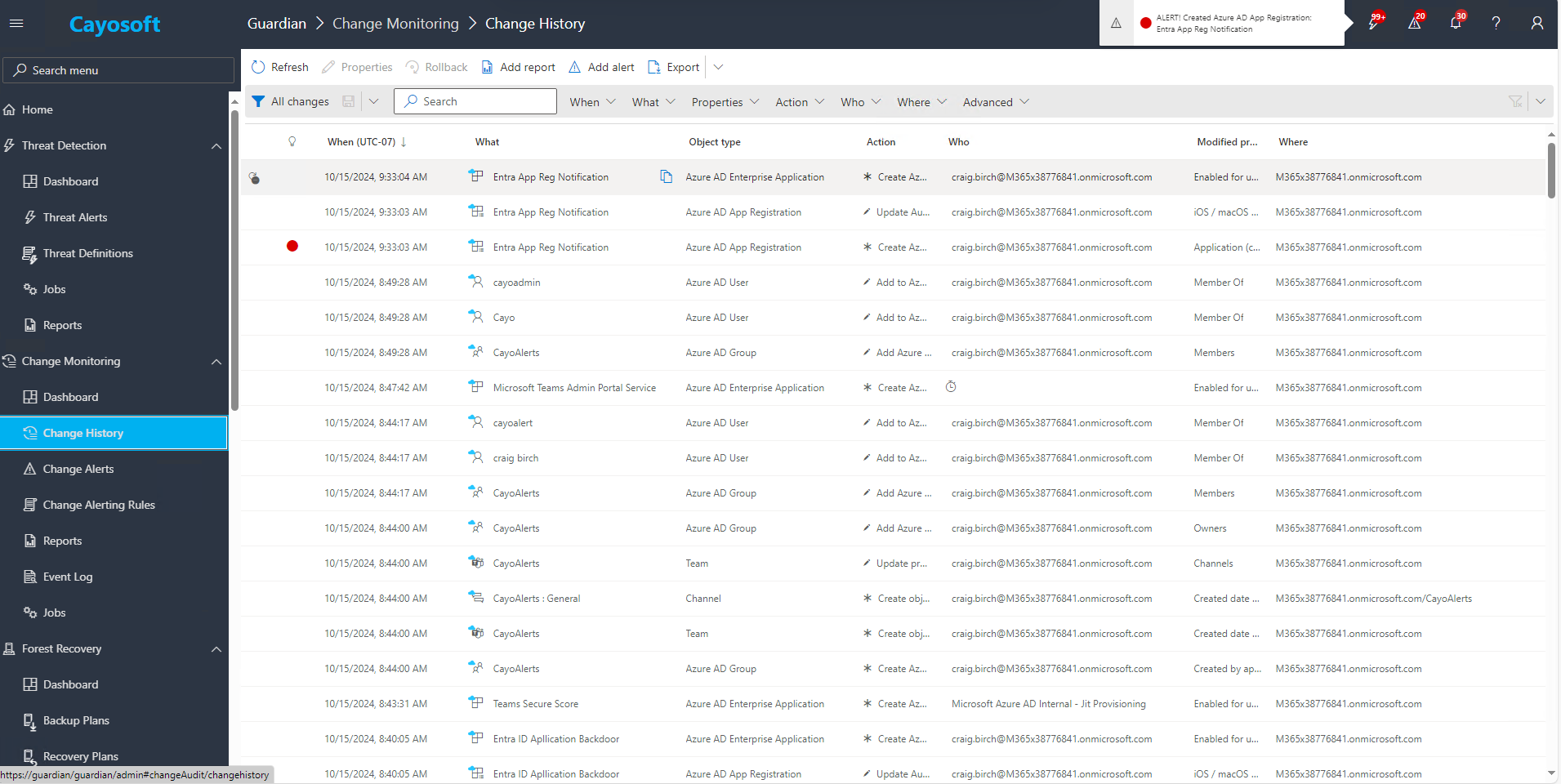
Automated Alerts Based on Real-Time AD and Entra ID Changes
With Cayosoft Guardian, security teams can set up automated alerts for real-time changes in AD and Entra ID, such as the creation of new privileged accounts, unauthorized password resets, changes to Entra ID Applications, and conditional access policies. These alerts ensure that no potential threat goes undetected.
Automated alerts help security teams act before attackers gain a foothold in either AD or Entra ID.
Efficient Privilege Management Across AD and Entra ID
Privilege management becomes even more critical in hybrid environments. Cayosoft Administrator helps organizations reduce their attack surface by automating privilege management across both AD and Entra ID. This includes automated account clean-up, removing stale accounts, and limiting over-provisioned access.
By streamlining privilege management in accordance with active directory security best practices, Cayosoft reduces the risk of attackers exploiting excessive privileges to gain control of on-premises or cloud-based resources.
Advanced Detection of Attack Paths in AD and Entra ID
Cayosoft Guardian provides advanced detection capabilities that go beyond common attack vectors, identifying lesser-known paths across both AD and Entra ID. This includes detecting misconfigurations in AD CS, analyzing legacy protocols, and monitoring suspicious activity in Entra ID that may go unnoticed by traditional security solutions.
With Cayosoft, organizations gain complete visibility into their hybrid environment, ensuring that no threat—no matter how obscure—goes unnoticed.
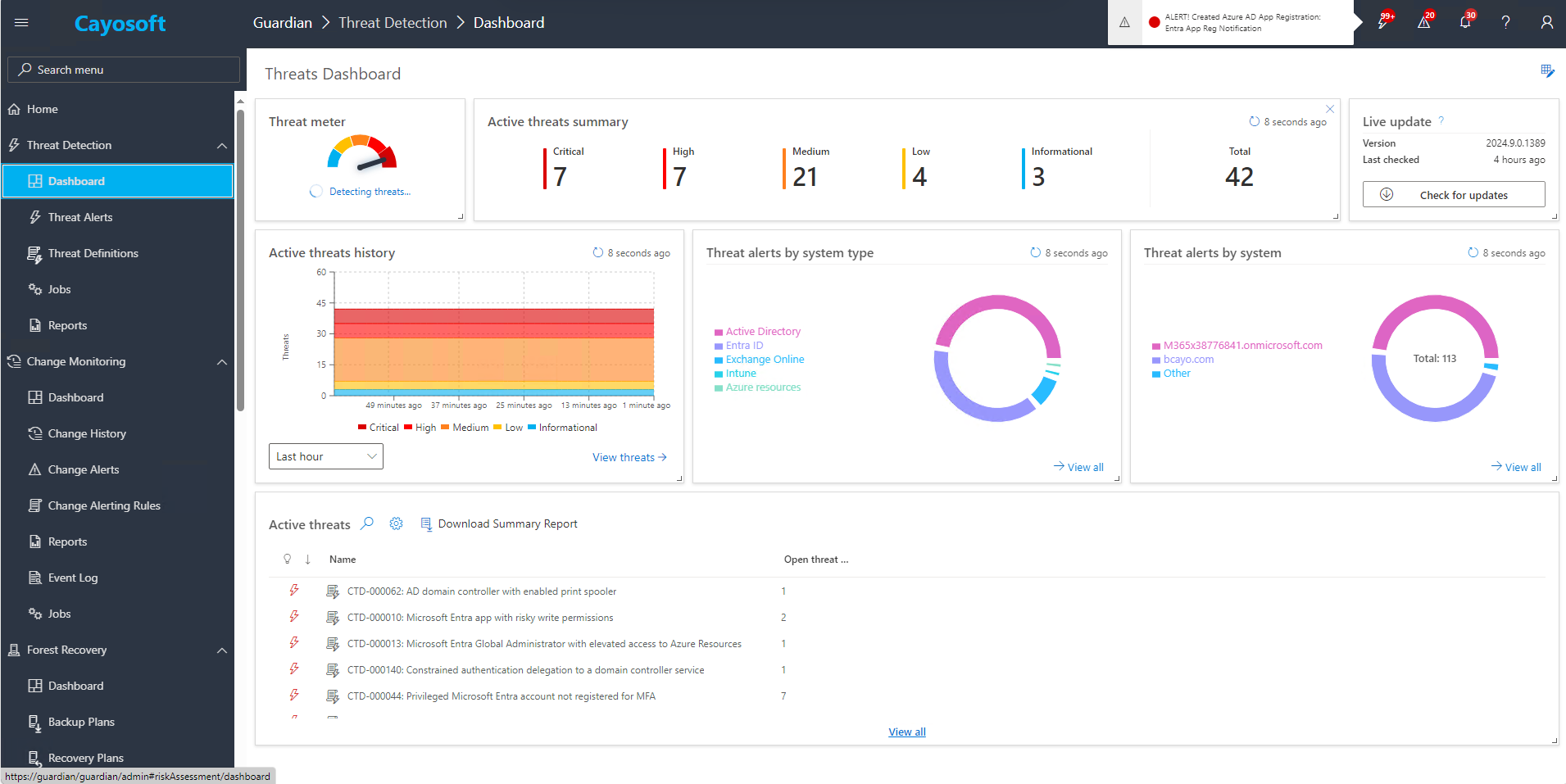
Hybrid Environment Protection: Real-Time and Comprehensive
The NSA’s guidance emphasizes the importance of event monitoring and privilege management in AD environments, but in hybrid systems that include Microsoft Entra ID, organizations need a more unified, real-time approach to security.
Cayosoft offers exactly that—by integrating real-time monitoring, automated alerts, and efficient privilege management across both AD and Entra ID, Cayosoft helps organizations secure their hybrid environments against common and advanced threats.
With Cayosoft, you can protect your hybrid infrastructure from end-to-end, ensuring that attackers cannot exploit your on-premises AD to breach your cloud-based resources via Entra ID.
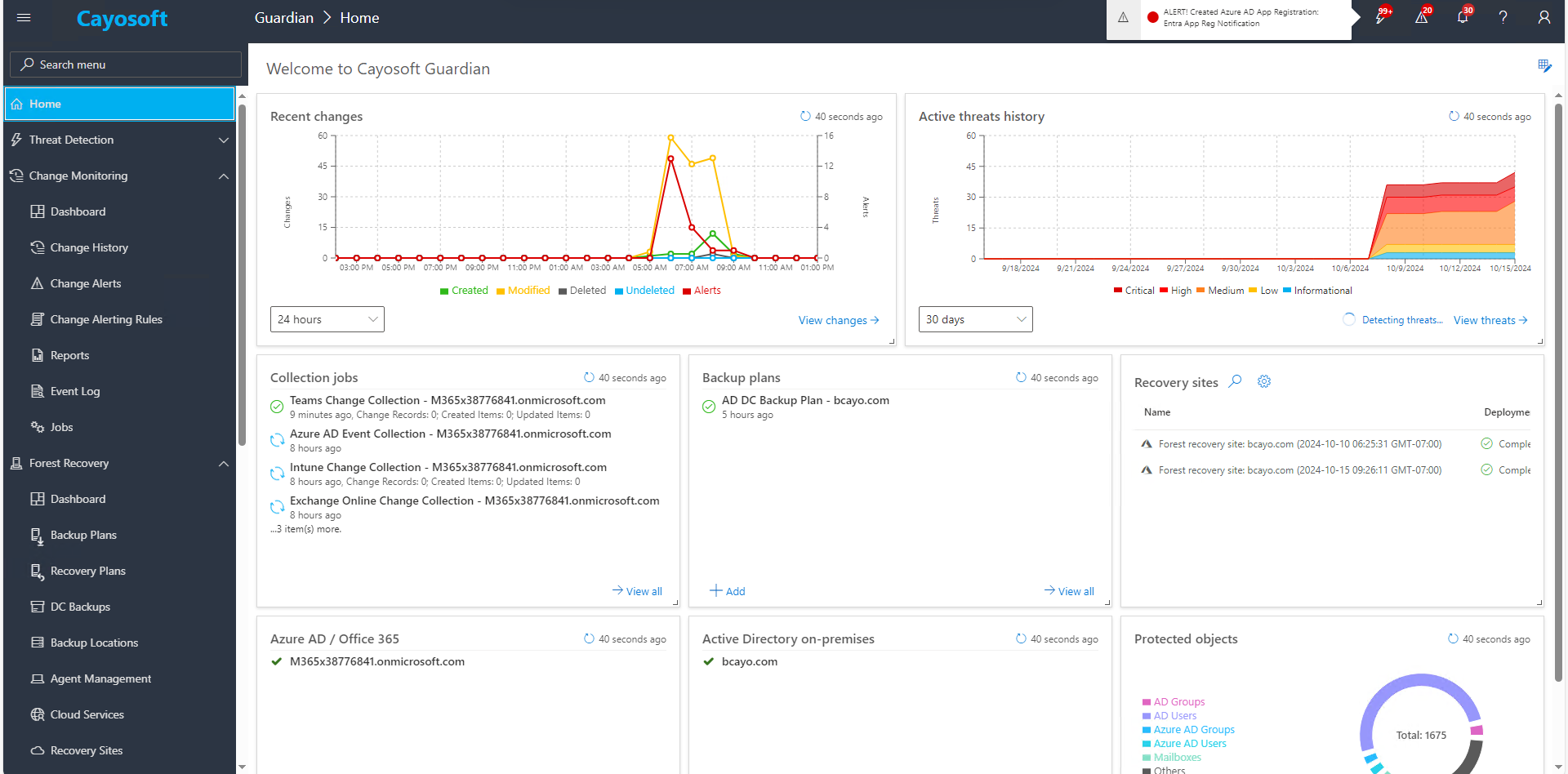
Schedule a demo of Cayosoft Administrator today and see how you can easily protect your Tier 0 and privileged service accounts.
FAQs
Traditional event log monitoring relies on logs that can be delayed or missed in the volume of normal activities. Cayosoft’s real-time monitoring offers immediate visibility into suspicious activity across both on-premises AD and Microsoft Entra ID, allowing for quicker detection and response without waiting for logs to process.
Hybrid AD environments combine on-premises and cloud systems, creating more opportunities for attackers to exploit over-privileged accounts. Cayosoft automates privilege management by auditing and adjusting account permissions, reducing attack surfaces and limiting what attackers can access if an account is compromised.
Cayosoft extends monitoring to cover cross-tenant configurations and guest account activities, identifying risks in federated identities and cross-tenant access. Automated alerts are triggered for suspicious activities between tenants, preventing lateral movement that could compromise multiple cloud environments.
Cayosoft enables ongoing auditing of OAuth app permissions within Microsoft Entra ID, ensuring that excessive or dangerous permissions are identified and managed effectively. This prevents malicious apps from gaining unauthorized access to sensitive data.
Key active directory security best practices include reducing privileged access, enabling multi-factor authentication (MFA), using Group Managed Service Accounts (gMSAs) to rotate passwords, auditing privileged changes regularly, and monitoring event logs in both on-premises AD and Microsoft Entra ID environments.
Cayosoft offers real-time monitoring, automated alerts, and advanced detection capabilities that align with active directory security best practices. It helps organizations protect hybrid environments, manage privileges efficiently, and detect attack paths across both AD and Entra ID.