Home » Five Critical Azure Security Best Practices for Effective Risk Management » Azure AD Entra ID: Mastering Key Concepts, Use Cases, and Best Practices
Azure AD Entra ID: Mastering Key Concepts, Use Cases, and Best Practices
Learn about Microsoft Entra ID, the cloud-based identity and access management solution for organizations using Azure Cloud or Microsoft 365, including key terminology, use cases, and security best practices.
Explore the chapters:
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Microsoft Entra ID is the latest name for a service that Microsoft has developed for many years. Specifically, Entra is Microsoft’s rebrand of the Azure Active Directory or Azure AD services. Microsoft Entra ID provides a cloud-based identity and access management (IAM) solution.
If your organization uses Azure Cloud or Microsoft 365, a Microsoft Entra tenant is created as part of these services. Entra ID integrates with Azure resources, Microsoft services like 365, and non-Microsoft applications to provide secure and seamless access for your users, applications, and devices.
This article will explore Microsoft Entra ID in detail, including key terminology, use cases, and a comprehensive guide to best practices that align with industry standards and Microsoft’s recommendations.
Summary of Key Azure AD Entra ID Concepts
The table below summarizes essential Azure AD Entra ID concepts that this article will explore in more detail.
| Concept | Description |
| Key terminology and features of Azure AD Entra ID | The different types of identity provided by Microsoft Entra ID support different use cases. Human identities support internal and external user sign-ins and single sign-on. Meanwhile, non-human identities can provide access to software and devices. Managed identities linked to Azure resources simplify credential management and avoid exposure. |
| Efficient management and administration | Automatic provisioning and dynamic groups can improve user management in Microsoft Entra ID. Third-party tools can supplement the functionality of the Microsoft Entra admin center and help avoid your organization needing to develop and maintain custom scripts. |
| Business continuity and disaster planning | Recoverability is a shared responsibility between the customer and Microsoft. Only users, Microsoft 365 groups, and application identity objects are soft deleted, meaning you can recover them within 30 days. Other objects are hard deleted and you must restore them from a backup. Microsoft Entra Exporter and other third-party tools can back up your Microsoft Entra ID configuration. |
| Security best practices | Identity has evolved to become the primary perimeter for security. By following a zero-trust security strategy, you can ensure the highest level of data protection. Microsoft Entra ID, with its centralized identity management, change monitoring and access review, and threat detection, helps your organization align with the zero-trust model, providing a robust security framework that you can trust. |
Key Terminology and Features of Azure AD Entra ID
Let’s begin by defining some key terminology used throughout the article. The primary purpose of Microsoft Entra ID is to provide authentication and authorization to users, applications, and devices to enable them to access internal and external resources. A resource could be an Azure Blob Storage Account, a SaaS application, or a Microsoft 365 document.
Rebranding to Microsoft Entra ID
On August 15th, Microsoft renamed Azure Active Directory (Azure AD) to Microsoft Entra ID. Microsoft replaced the names Azure Active Directory, Azure AD, and AAD with Microsoft Entra ID. This change was purely a rebrand, and all existing deployments, configurations, and integrations continued functioning as before.
Tenant and Directory
We often use the terms Microsoft Entra tenant and Microsoft Entra directory synonymously. Strictly, the directory is a database or catalog of the identities and resources associated with a Microsoft Entra tenant. A tenant is a dedicated and isolated instance of Azure AD that an organization receives. It provides functionality like signing in a user and issuing tokens. When creating your tenant, choose a location based on your data residency requirements because it cannot be changed later.
Types of Identity
Microsoft Entra ID defines two identities: human and machine/non-human. The table below provides examples of human and machine identities and further divides them into internal vs. external identities. Being an internal identity means that the identity is present in your organization’s Microsoft Entra directory, whereas an external Microsoft Entra tenant will authenticate an external identity in your directory.
| Human Identities | Machine Identities | |
| Internal | Employees | Workload Identities – applications, service principals, and managed identities. Devices – desktops, IoT, mobile phones |
| External | Partners Customer Vendors Consultants | External devices |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Use Cases for Microsoft Entra ID
The different identities supported by Microsoft Entra ID provide for various use cases.
Internal human identities provide the most common use case, where IT administrators control which users can access specific resources – for example, granting users access to Microsoft services (like Microsoft 365), Azure Storage accounts, or third-party SaaS applications.
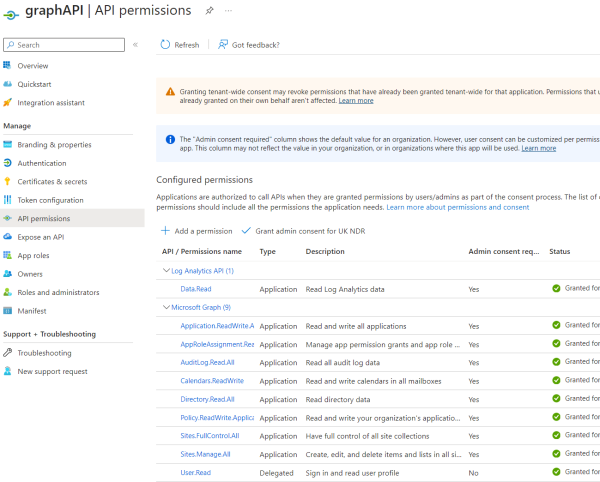
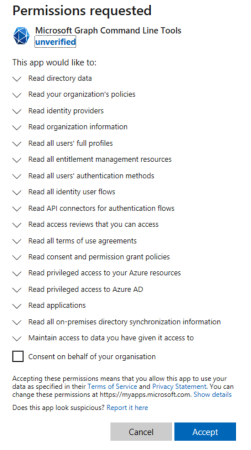
Your software requires a workload identity to identify itself. Let’s say you are developing a script that needs to authenticate with an Azure resource or using an Infrastructure as a code framework to create a resource in Azure. You would register an application in App Registrations to provide the necessary permissions. Then, you can assign API permissions to the application. The image below shows an example where an application called graphAPI has been assigned Microsoft Graph permissions. Under Certificates & secrets, you create a client secret to enable the script to authenticate itself with Entra ID.
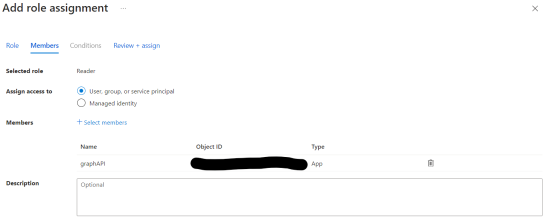
Your Microsoft Entra ID instance creates a service principal for the application, which can be assigned to Azure resources within your tenant to control what the application can access. For example, the graphAPI application is assigned the Reader role to access an Azure storage account, as shown in the image below.
There is a particular type of service principal called a managed identity. A managed identity is a specific type of service principal linked to an Azure resource. There are two types of managed identities:
- System assigned – the identity is linked to a single Azure resource.
- User assigned – a standalone Azure resource that can link to multiple Azure resources.
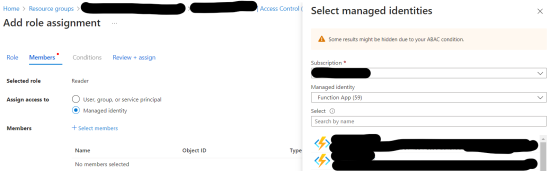
The advantage of a managed identity is that the credentials are automatically managed and are unknown to everyone. For example, an application running on Azure Functions may need to access Azure Storage to read and process data. Instead of using credentials like Access Keys within the Azure function, a managed identity can provide an identity to the Azure function. The image below gives an Azure Function App the Reader role to an Azure Storage account.
Groups
Groups provide shared access needs to several identities. Instead of assigning access rights individually to each user, create a group with the required permissions and add users to it. There are two types of Microsoft Entra ID groups: security and Microsoft 365.
| Security group | Microsoft 365 group |
| You create security groups to enable users, devices, service principals, and other groups to share the same security permission set. | You use a Microsoft 365 or distribution group to manage collaboration needs, including accessing a shared mailbox, calendar, or SharePoint site. |
License types
The table below briefly summarizes the various Microsoft Entra ID license types and their main features.
| Product | Features |
| Microsoft Entra ID Free |
|
| Microsoft Entra ID P1 | The above plus,
|
| Microsoft Entra ID P2 | The above plus,
|
| Microsoft Entra ID Governance | Requires a P1 or P2 license
Provides an advanced set of identity governance capabilities like:
|
| Microsoft 365 | P1 is included with Microsoft 365 E3 for enterprise customers and Microsoft 365 Business Premium . P2 is included with Microsoft 365 E5 for enterprise customers |
| “Pay as you go” features | Based on monthly active users (MAU), e.g., Microsoft Entra External ID Based on resources, e.g., Microsoft Entra Permissions Management Based on workload identities, e.g., Microsoft Entra Workload ID Currently free, e.g., Microsoft Entra Verified ID |
The table shows the different Microsoft Entra ID licenses. (Source)
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Efficient Management and Administration
Microsoft Entra ID day-to-day administrative tasks will depend on the size of your organization and the types of identities that your organization is using. Day-to-day tasks may include:
- Adding, editing, and deleting user accounts
- Creating new groups
- Managing group membership
- Suspending user access
- Resetting forgotten passwords
- Unlocking accounts
- Renewing application credentials
- Update and remove group permissions
- Renewing expiring application credentials
Microsoft Entra Admin Center
The Microsoft Entra admin center (entra.microsoft.com) provides management and administration capabilities. For example, a new internal user can be created by:
- Browsing to Identity > Users > All Users
- Selecting New user
- Entering a User principal name and entering a Display Name
- Entering details for group and role assignments
- Selecting Create
Using the admin center is valuable for learning about Microsoft Entra ID’s features and functionality. However, using the admin center in a larger organization may require multiple Microsoft Entra ID administrations to remain efficient. Automatic provisioning, dynamic groups, and third-party tools can automate repeatable Microsoft Entra ID management and administration tasks.
Automatic Provisioning
Automatic provisioning can benefit Microsoft Entra ID administrators in two main areas: human resources-driven and application provisioning.
When you add a new employee to your HR system, Microsoft Entra ID can automatically create the user in your directory.
Enabling automatic provisioning keeps Microsoft Entra ID in sync with HR changes made to an employee:
- Employee attributes will be consistent with the underlying HR system.
- Changes in the HR system, such as line manager or location, will automatically be reflected in Microsoft Entra ID.
- If an employee leaves, their user account can be automatically disabled.
Microsoft Entra natively supports many popular SaaS apps and human resources systems and provides generic support for apps that implement the SCIM 2.0 standard. Application provisioning automatically creates user identities and roles in SaaS applications like Dropbox or Salesforce.
Automatic Provisioning
Automatic provisioning can benefit Microsoft Entra ID administrators in two main areas: human resources-driven and application provisioning.
When you add a new employee to your HR system, Microsoft Entra ID can automatically create the user in your directory.
Enabling automatic provisioning keeps Microsoft Entra ID in sync with HR changes made to an employee:
- Employee attributes will be consistent with the underlying HR system.
- Changes in the HR system, such as line manager or location, will automatically be reflected in Microsoft Entra ID.
- If an employee leaves, their user account can be automatically disabled.
Microsoft Entra natively supports many popular SaaS apps and human resources systems and provides generic support for apps that implement the SCIM 2.0 standard. Application provisioning automatically creates user identities and roles in SaaS applications like Dropbox or Salesforce.
Dynamic Group Membership
Attribute-based rules automatically enable users to be added or removed from Microsoft Entra ID groups. Administrators can create dynamic membership rules for both security and Microsoft 365 groups. For example, group membership may depend on the department or country where an employee is based. If an employee changes department or country, they are automatically removed from one group and added as a member to another group.
Third-Party Tools
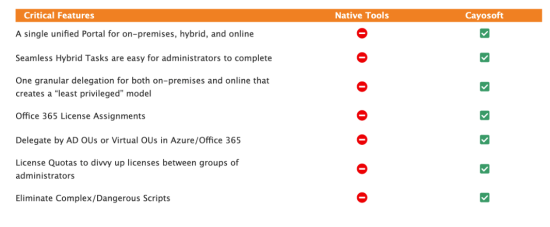
Third-party tools, like Cayosoft Administrator, overcome several limitations with the Microsoft Entra admin center by simplifying management and administration tasks. Administrators can save time swapping between separate interfaces for on-premise and cloud users in hybrid environments. Managing all types of identity from a single portal will be a significant efficiency gain. Cayosoft Administrator simplifies the management of hybrid environments by providing a single, unified console from which to perform administrative tasks.
Many organizations develop custom scripts to automate Microsoft Entra ID tasks. However, maintaining custom scripts can make auditing harder. How will you track who ran the script or made changes to a script? In addition, keeping track of the service principals and credentials used by the scripts can be difficult and lead to over-permissive access to Microsoft Graph functionality to perform changes in Microsoft Entra ID.
Watch demo video of Cayosoft’s hybrid user provisioning
Business Continuity and Disaster Planning
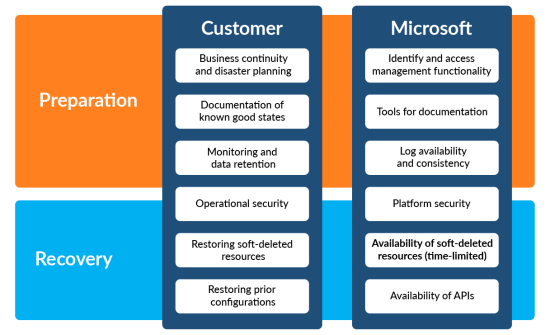
Shared Responsibility
Recoverability is a shared responsibility between Microsoft and your organization. You are responsible for ensuring that you have business continuity and disaster planning in place. You are also responsible for capturing known good states so that you can restore a previous Microsoft Entra ID configuration if necessary.
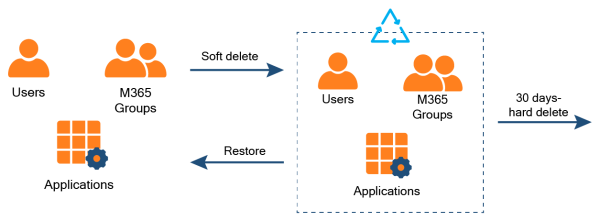
Deletions
Microsoft Entra ID has two types of deletions: soft and hard deletions. A soft deletion means a deleted item goes to the Microsoft Entra ID recycle bin, and you can restore it within 30 days. Only users, Microsoft 365 groups, and applications are soft deleted. Everything else, including security groups, is hard deleted and cannot be recovered from Microsoft Entra ID.
Similarly, the only way to recover from a misconfiguration is to record a known good state to restore your Microsoft Entra ID settings. The>Microsoft Entra Exporter is a PowerShell module that can export your Entra and Azure AD B2C configurations to JSON files.
Misconfigurations
The only way to recover from a misconfiguration is to have recorded a known good state from which to restore your Microsoft Entra ID settings. The Microsoft Entra Exporter is a PowerShell module that can export your Entra and Azure AD B2C configurations to JSON files. You can export your Entra configuration settings to local .json files as follows:
1. From an Administrator Windows PowerShell prompt:
> Install-Module EntraExporter Untrusted repository You are installing the modules from an untrusted repository. If you trust this repository, change its InstallationPolicy value by running the Set-PSRepository cmdlet. Are you sure you want to install the modules from 'PSGallery'?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): Y
2. Close this PowerShell because Administrator permissions are no longer required.
3. From a normal Windows PowerShell:
Connect-EntraExporter -TenantId '<tenant_id>'
4. After signing in and granting permission, you should see the following:
Welcome to Microsoft Graph!
Connected via delegated access using
Readme: https://aka.ms/graph/sdk/powershell
SDK Docs: https://aka.ms/graph/sdk/powershell/docs
API Docs: https://aka.ms/graph/docs
5. Make a directory to write the backup to:
> mkdir EntraBackup
6. Perform the export
> Export-Entra -Path '<backup_directory_path>' -All
7. The export will begin and produce an output like:
Entra Exporter is a simple tool that can only export data from Microsoft Entra ID; it cannot be used to restore data. However, it can be a helpful starting point for producing a regular output from Microsoft Entra ID for auditing or change control purposes.
Third-Party Tools
Even with the output from Entra Exporter, recovering a hard-deleted item or restoring a previous configuration will be time-consuming. It will either involve navigating the Microsoft Entra admin center or using the Microsoft APIs for recovery.
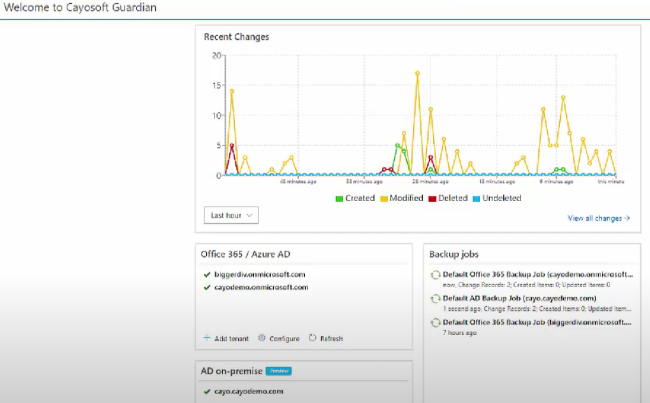
Tools like Cayosoft Guardian provide a more straightforward approach to recovery by capturing a granular change history of your Microsoft Entra ID tenant. With Cayosoft Guardian, soft and hard deleted items can be restored instantly, and rolling back your tenant to a previously known good state is a simple operation.
Security Best Practices
The advent of remote working and establishing hybrid cloud environments means you can’t assume everything is behind the corporate firewall. The focus has changed from network security to identity security, with the latter becoming the primary perimeter for security.
Follow a Zero-Trust Security Strategy
A zero-trust approach to security addresses modern work practices that do not have a traditional network edge. A zero-trust model includes the following security principles:
- Verify explicitly by using all available data points to authenticate and authorize. These can include the user’s location, the classification of the data accessed, and the time of day.
- Use the least privileged access to limit user access with just-in-time and just-enough access.
- Assume breach and minimize blast radius by partitioning sensitive data and resources. Use analytics to assess threats, like reviewing Microsoft Entra ID sign-in activity to spot anomalies.
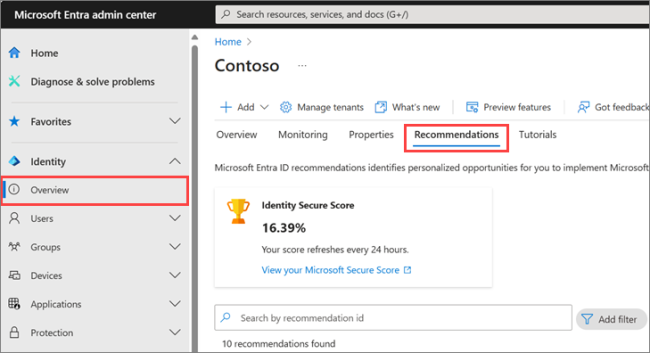
Your application developers can align with the zero-trust model by using Microsoft Entra ID-managed identities during their application development. NIST 800-207 is a vendor-neutral standard that can help align your organization with the Zero-Trust model. Microsoft also has further information on securing identity with Zero Trust and provides an identity secure score with recommendations to improve your security posture.
Centralize Identity Management
Maintaining a single Microsoft Entra directory will help establish a consistent and authoritative source of identities. Avoid using separate systems for on-premise and cloud-based users, as this can lead to inconsistencies and out-of-sync changes. Use Microsoft Entra Connect to synchronize your on-premises directory with your cloud directory.
Integrating your on-premise and cloud directories will give users a common identity when accessing cloud and on-premise resources. Your users will benefit from a single sign-on experience, and access controls, like MFA and conditional access, will be applied consistently to user identities.
Third-party tools like Cayosoft Administrator simplify centralized identity management by providing a single portal for managing all user accounts. Cayosoft Administrator will also ensure you follow best practices, such as not synchronizing accounts with Microsoft Entra ID that have high privileges in your Active Directory instance.
Change Monitoring and Access Reviews
Microsoft Entra ID provides three types of activity logs:
- Audit logs – show a history of changes to your tenant. For example, changes to applications, groups, and users are all captured.
- Sign-in logs – show the sign-in attempts of your users and client applications. They include sign-in errors and show both interactive (e.g., users) and non-interactive (e.g., applications) sign-ins.
- Provisioning logs – provide information about users provisioned in your tenant through a third-party service. For example, which users have been added to the Adobe application license?
A Microsoft Entra ID free license only retains audit and sign-in logs for seven days, and provisioning logs are unavailable. A Microsoft Entra ID P1 or P2 license will retain all logs for 30 days. Even with a P1 or P2 license, these default retention periods may not meet your security or industry compliance regulations. You can extend the retention period using any of the following methods:
- Integrating Entra logs with Azure Monitor Logs
- Sending logs to a Log Analytics Workspace
- Archiving Entra Logs to an Azure Storage Account
- Using a third-party tool like Cayosoft Administrator
Implement Threat Detection
“Microsoft Entra data shows attempted password attacks increased more than tenfold in 2023, from around 3 billion per month to over 30 billion.” 2023 Microsoft Digital Defense Report
The Microsoft Entra ID Protection dashboard monitors risks to your Microsoft Entra tenant, such as suspicious sign-in activity. Risk detection events are either captured in real-time or offline. Detections triggered in real-time take 5-10 minutes to appear in reports, and offline detections take up to 48 hours to appear in reports. Some risk detection events are labeled Premium detections and require a Microsoft Entra ID P2 license.
The Risky Users report provides a record of users whose accounts are at risk of compromise based on specific events, including:
- Activity from anonymous IP addresses
- Change of location
- Sign-ins from infected devices
Reviewing the risky users report can help your organization develop risk-based access policies. For example, Microsoft Entra Conditional Access enables you to enforce multi-factor authentication when the sign-in risk level is medium or high. The main benefit of these risk-based policies is they provide automatic risk remediation. If the at-risk user account completes MFA, Microsoft Entra ID will remediate the sign-in risk without an administrator intervening.
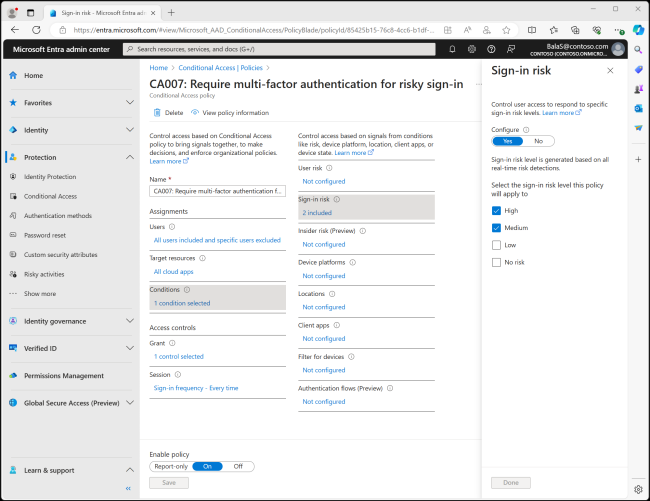
Third-party tools, like Cayosoft Guardian, further enhance threat detection, particularly in hybrid identity environments. For example, Cayosoft Guardian can discover malicious configuration changes to your Microsoft Entra ID environment and revert to a known good state. Cayosoft Guardian’s threat detection does not require extensive configuration and provides threat detection, monitoring, and recovery across on-premise AD, hybrid AD, Microsoft Entra ID, and Microsoft 365.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Last Thoughts on Azure AD Entra ID
Microsoft Entra ID is the new branding for Azure Active Directory. It provides a comprehensive cloud-based identity and access management (IAM) solution that supports a wide range of use cases, from traditional user management to applications and hardware. Entra ID simplifies your users’ experience with a single sign-on (SSO) feature and enhances their security with multi-factor authentication and conditional access policies.
As the number of identity objects in your directory grows, consider how automatically provisioning users and dynamically managing group membership can improve the efficiency of your Microsoft Entra ID administrators. Third-party tools like Cayosoft Administrator can provide a single portal for managing all identities from cloud and on-premise environments.
Business continuity and disaster planning should include your Microsoft Entra ID environment. Microsoft Entra ID has limited in-built recovery options for misconfigurations or hard-deleted objects. Cayosoft Guardian provides improved backup capabilities.
Consider identity to be your primary perimeter for security. Follow security best practices like the zero-trust model and regularly review changes to your Microsoft Entra ID environment, findings from user risk reports, and perform access reviews to ensure principles like least privilege are being followed. Wherever possible use managed identities with your Azure resources to simplify credential management.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content