Home » Active Directory Management Tools: Must-Have Features » Active Directory Security
Active Directory Security
Learn about the essential best practices for securing Active Directory to protect against sophisticated cyber threats, like Pass-the-Hash and Golden Ticket attacks, through secure configuration, monitoring, and industry-standard administrative practices.
Explore the chapters:
- Active Directory Security
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
- Active Directory Security
- Active Directory Management Tools
- Active Directory Group Policy Management
- Active Directory Security
- Active Directory Management
- Active Directory Disaster Recovery
- Active Directory Auditing
- Active Directory Groups
- Disable Active Directory
- Active Directory Reporting
- Active Directory Backup
- Active Directory Forests
- Active Directory Monitoring
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Summary of Key Active Directory Security Best Practices
| Best Practice | Description |
| Have a Secure Configuration | Implement and enforce group policies for AD management. Deploy privileged access management (PAM) for strict oversight of privileged accounts. |
| Implement Monitoring and Auditing | Enhance your Active Directory security with real-time monitoring, detailed change logs for troubleshooting, and robust auditing tools for compliance and risk assessment. |
| Adhere to Industry-Standard Administrator Practices | Use role-based access control (RBAC) for permission alignment, adhere to the least privilege principle to minimize security risks, and utilize multi-factor authentication (MFA) for strengthened user authentication. |
Cyber Threats to Active Directory
Pass-the-Hash Attacks
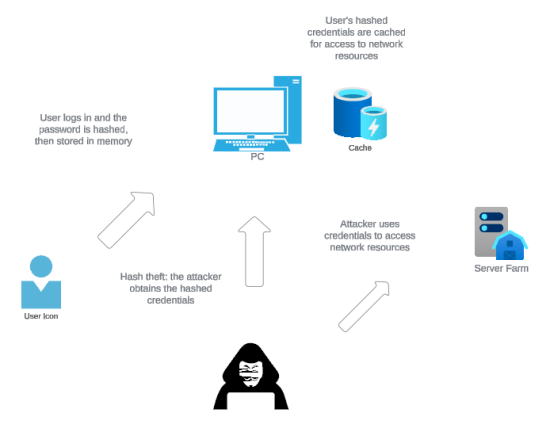
Pass-the-hash (PtH) attacks pose a threat to Active Directory due to their ability to exploit the authentication mechanism of Windows networks. By stealing NT LAN Manager (NTLM) hash values—which are stored hash functions rather than plaintext passwords—attackers can impersonate legitimate users without the need to decrypt or know the actual password. This form of credential theft enables attackers to gain unauthorized access and, potentially, escalate privileges within a network, often without triggering detection systems.
A PtH attack takes advantage of the fact that user credentials are typically cached as hash values within a system. When a user logs into a Windows account, the password is hashed, and the hash is stored in memory, allowing the user to access other network resources without re-entering the password. An attacker who successfully obtains these hash values can effectively “pass” them for authentication, traversing a network under the guise of a valid user account. This method bypasses the need for password cracking, making the attack more efficient.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Golden Ticket Attacks
Golden ticket attacks are advanced persistent threats (APTs) that exploit the Kerberos authentication protocol, which is integral to the security of AD environments. A golden ticket is a forged Kerberos Ticket Granting Ticket (TGT) that allows attackers to impersonate any AD user, bypassing Active Directory security to access resources across the network, and often maintain persistence within the system.
The attack begins when an adversary gains sufficient privileges to compromise a domain controller, thus breaching Active Directory security by accessing the AD database. The attacker can extract from the database the Kerberos key, known as the KRBTGT account hash, which is used to create golden tickets. These tickets can be repeatedly used for access until the KRBTGT account password is changed, and because they are trusted internally, they often go undetected for long periods.
Credential Harvesting
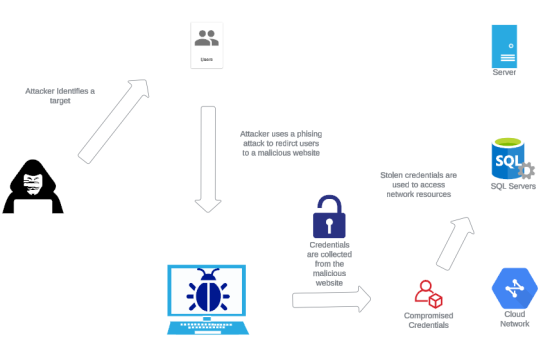
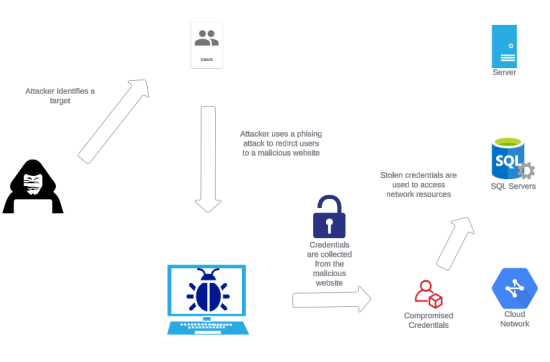
Credential harvesting is a critical threat vector where attackers gather credentials such as usernames and passwords from their targets, often as a preliminary step toward a more extensive attack. This practice encompasses various techniques, like phishing, keylogging, and exploiting system vulnerabilities. After harvesting credentials, the attacker can gain unauthorized access to systems, compromising Active Directory security to cause data breaches, install malware, or perpetuate fraud.
The ubiquity of credential harvesting is partly due to its effectiveness: People are often the weakest link in cybersecurity. Phishing remains one of the most common methods, where attackers fool users into providing login details through fake websites or deceptive emails. Malware such as keyloggers can covertly capture keystrokes, allowing attackers to gather credentials as users log into various systems.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Real-World Examples
Pass-the-Hash
According to this CloudStrike article, in April 2022, the ransomware-as-a-service platform “Hive” engaged in an elaborate attack, exploiting a technique known as pass-the-hash to target numerous clients of Microsoft Exchange Server. These clients spanned across various sectors, including energy, financial services, non-profits, and healthcare.
The attackers capitalized on a Microsoft Exchange Server vulnerability named ProxyShell. While Microsoft had already released a patch to address this ProxyShell issue, the delayed adoption of this update left many businesses vulnerable.
Through the ProxyShell vulnerability, the attackers were able to implant a nefarious web script that enabled them to execute malicious code on the affected Exchange servers. Once inside, the attackers utilized the pass-the-hash method, employing a tool called Mimikatz to extract the NTLM hash of user passwords. This granted them unauthorized control over the systems.
Following system infiltration, Hive conducted a systematic exploration of the network to understand its structure, harvested valuable data, and ultimately introduced ransomware to encrypt the data for extortion purposes.
Golden Ticket Attack
The infamous APT attack on the retail giant Target in 2013 is an instance where golden ticket tactics were exploited. After gaining initial entry through compromised third-party credentials, the attackers infiltrated Target’s network and eventually gained control of the domain controller. By generating a golden ticket, they were granted unhindered access to point-of-sale (POS) systems, leading to the extraction of around 40 million debit and credit card records. More information on the attack can be found here.
Credential Harvesting
A large-scale credential harvesting attack was seen in the LinkedIn breach in 2012 reported by TrendMicro, where attackers exploited a weak SHA-1 hashing algorithm to harvest passwords. Initially, 6.5 million hashed passwords were posted on a Russian hacker forum. By 2016, it was revealed that a total of 117 million credentials had been compromised in the same breach, making it one of the biggest credential-harvesting incidents at the time.
Watch a 12-minute product demo video of Cayosoft’s hybrid user provisioning
Active Directory Security Best Practices
Maintain a Secure Configuration
Group Policies and Account Policies
Privileged Access Management (PAM)
- Automating user creation, provisioning, and de-provisioning: Cayosoft Administrator streamlines user account management by automating the creation, maintenance, and decommissioning of AD accounts. This automation effectively eradicates delays or oversights in the management of account lifecycles, reducing the risk of security breaches associated with inactive or outdated user credentials.
- Password self-service portal: The Cayosoft Password Self-Service Portal permits users to perform password changes and resets without administrator intervention. By enabling users through safe, predefined processes, organizations can reduce support costs and improve user satisfaction while ensuring no compromise in security policies.
Implement Monitoring and Auditing
Monitoring and auditing are essential to ensuring adherence to regulatory compliance within Active Directory ecosystems. This strategy encompasses diligent log analysis, robust monitoring tools, and thorough security auditing practices.
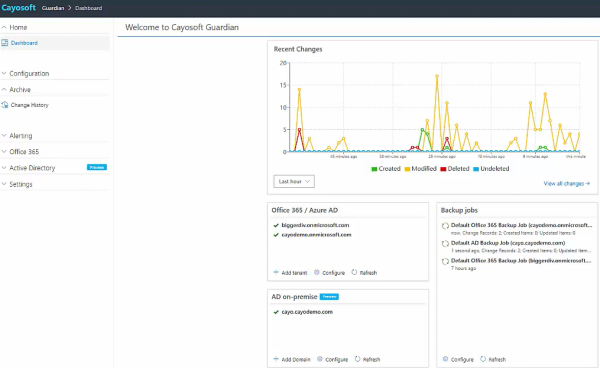
Cayosoft Guardian delivers real-time monitoring capabilities, offering organizations a powerful lens into their AD environments. It keeps track of all changes across AD infrastructures, providing administrators with detailed logs that are essential for diagnosing issues, tracing back unauthorized actions, and understanding the overall health of the AD space.
Cayosoft offers the following essential features for maintaining a secure AD environment. Together, these features enable organizations to actively manage their security postures, respond to incidents with informed precision, and uphold stringent standards of compliance within their AD operations.
Continuous Monitoring
Cayosoft Guardian provides around-the-clock surveillance to detect and alert on critical events or deviations, enabling rapid response to potential security incidents.
Comprehensive Logging
Detailed logs and contextual information about AD events offer insights into user activities, configuration adjustments, and access patterns. This data is pivotal for locating system vulnerabilities or identifying points of non-compliance.
The ability to perform extensive security audits is a key facet of Cayosoft solutions. With its robust reporting capabilities, Cayosoft Guardian aids in translating logged information into actionable intelligence.
Real-Time Reporting
Historical Auditing
Together, these features enable organizations to actively manage their security postures, respond to incidents with informed precision, and uphold stringent standards of compliance within their AD operations.
Adhere to Industry-Standard Administrator Practices
Effective administration practices form the cornerstone of AD security and operational efficiency. Implementing role-based access control (RBAC), adhering to the principle of least privilege, and enforcing multi-factor authentication (MFA) are vital practices that institutions adopt to secure their IT ecosystems. Cayosoft Administrator provides the tools necessary to seamlessly integrate these practices into the everyday management of AD and Azure AD environments.
By leveraging Cayosoft Administrator for RBAC, least privilege, and MFA, organizations can cultivate a secure, regulated, and efficient operational model that is resilient against both external and internal threats. These practices are described in more detail below.
Role-Based Access Control
Role-based access control (RBAC)RBAC is a method of regulating access to systems by assigning permissions to users based on their roles within an organization. Cayosoft Administrator allows you to create granular roles that align with the specific duties and responsibilities of different users within the enterprise. Cayosoft Administrator also streamlines the process of assigning and updating user permissions, ensuring that they are reflective of each individual’s current role, thereby optimizing the IT workforce’s productivity and mitigating insider threat risks.
Principle of Least Privilege
The principle of least privilege (PoLP) dictates that users be given the minimum levels of access—or permissions—needed to perform their job functions. Cayosoft Administrator aids in establishing and maintaining access policies that ensure that users have no more privilege than necessary, reducing the attack surface for potential security breaches. Permissions can be dynamically adjusted as roles shift within an organization, which is critical for maintaining a secure and adaptable IT environment.
Multi-factor authentication
Multi-factor authentication (MFA) adds an additional layer of security by requiring multiple methods of verification from users before granting access to a system. By integrating MFA protocols, Cayosoft Administrator provides a robust mechanism for validating user identities and preventing unauthorized access, which is a foundational requirement in today’s threat landscape.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Securing Active Directory is a critical task due to its significant role in managing network resources and user access. Combating threats like pass-the-hash attacks, golden ticket attacks, and credential harvesting requires a solid understanding of both the risks and robust defense mechanisms available.
The key to this defense is the adoption of best practices such as secure configurations, vigilant monitoring and auditing, and prudent administrative protocols. Tools like Cayosoft Guardian enhance an AD administrator’s ability to monitor AD environments in real-time, providing detailed logs for tracking changes and triggering alerts for potential security incidents. Through comprehensive reporting functions, organizations can conduct thorough security audits to maintain adherence to regulatory standards.
Effective administration is bolstered by Cayosoft Administrator, enabling precise role-based access control (RBAC), enforcing the principle of least privilege, and solidifying identity verification through multi-factor authentication (MFA). These practices are essential to limiting the attack surface, securing user credentials, and preventing unauthorized access.
Through careful planning and execution of these strategies, IT security professionals can safeguard Active Directory, turning it from a potential point of vulnerability into a stronghold of organizational security. As threats evolve, so too must the approaches to AD security, with organizations continuously refining their practices to stay ahead of malicious actors.
As we have highlighted in this article, utilizing the right tools and methodologies is crucial. Cayosoft’s suite provides a proactive framework for real-time monitoring, security auditing, and strict adherence to administrative best practices, all of which contribute to building a resilient AD infrastructure.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content